当前位置:网站首页>Jumpserver高可用集群部署:(六)SSH代理模块koko部署并实现系统服务管理
Jumpserver高可用集群部署:(六)SSH代理模块koko部署并实现系统服务管理
2020-11-06 01:17:00 【dusthunter】
1、配置防火墙
firewall-cmd --permanent --add-rich-rule="rule family="ipv4" source address="10.255.200.1/30" port protocol="tcp" port="22222" accept"
firewall-cmd --permanent --add-rich-rule="rule family="ipv4" source address="10.255.200.1/30" port protocol="tcp" port="5000" accept"
firewall-cmd --reload
2、安装SSH代理koko模块
# 下载koko安装包并解压
cd /sas/jumpserver
wget https://github.com/jumpserver/koko/releases/download/v2.3.1/koko-v2.3.1-linux-amd64.tar.gz
tar -xf koko-v2.3.1-linux-amd64.tar.gz
mv koko-v2.3.1-linux-amd64 koko
cd koko
#该执行文件放入/usr/local/bin/,实现非绝对路径调用
mv kubectl /usr/local/bin/
#同样在koko目录下下载kubectl.tar.gz包
wget https://download.jumpserver.org/public/ kubectl.tar.gz
tar -xf kubectl.tar.gz
chmod 755 kubectl
mv kubectl /usr/local/bin/rawkubectl
rm -rf kubectl.tar.gz
3、修改koko配置文件
# 备份原始配置文件
cd /sas/jumpserver/koko
cp config_example.yml config.yml
# 修改koko配置文件,以下仅列出需修改的项目
vi config.yml
# Jumpserver项目的url, api请求注册会使用
CORE_HOST: https://10.255.200.5
# 修改BOOTSTRAP_TOKEN保持与jumpserver/config.yml中的一致
BOOTSTRAP_TOKEN:xxxxxxxxxxxxxxxx
# 修改日志级别
LOG_LEVEL: ERROR
# 会话共享使用的类型修改为redis
SHARE_ROOM_TYPE: redis
# 修改Redis配置,注意IP为浮动IP
REDIS_HOST: 10.255.200.4
REDIS_PORT: 6379
REDIS_PASSWORD: xxxxxxxx
REDIS_DB_ROOM: 6
4、编写systemd系统服务管理脚本
# 编写SSH代理模块koko启动脚本
vi /sas/jumpserver/tools/koko.service.sh
#!/bin/bash
cd /sas/jumpserver/koko/
case $1 in
start)
./koko -d
;;
stop)
./koko -s stop
;;
restart)
./koko -s stop && ./koko -d
;;
*)
;;
esac
# 编写SSH代理模块系统服务配置
vi /usr/lib/system/system/koko.service
[Unit]
Description=Jumpserver Koko Services
After=network.target remote-fs.target redis.service keepalived.service jumpserver.service
[Service]
Type=forking
ExecStart=/usr/bin/bash /sas/jumpserver/tools/koko.service.sh start
ExecReload=/usr/bin/bash /sas/jumpserver/tools/koko.service.sh restart
ExecStop=/usr/bin/bash /sas/jumpserver/tools/koko.service.sh stop
Restart=on-failure
RestartSec=5
[Install]
WantedBy=multi-user.target
5、https证书验证错误处理
tengine启用https后需在所有部署koko和guacamole的主机上导入安全证书,否则koko访问api接口时会报错,处理的方法是将相关的证书信息加入主机的证书信任列表中。
# 查看目标API服务的证书信息,此方法对其它https服务一样适用
openssl s_client -showcerts -connect 10.255.200.5:443
...
-----BEGIN CERTIFICATE-----
MIIDizCCAnOgAwIBAgIUM4uh9rB+BGjNBBLssCLCMdP54fkwDQYJKoZIhvcNAQEL
BQAwSjELMAkGA1UEBhMCQ04xDjAMBgNVBAgMBUhVQkVJMQ4wDAYDVQQHDAVXVUhB
TjENMAsGA1UECgwESEJUVjEMMAoGA1UECwwDQ0pZMCAXDTIwMTAxNTA5Mjk1M1oY
DzIxMjAwOTIxMDkyOTUzWjBKMQswCQYDVQQGEwJDTjEOMAwGA1UECAwFSFVCRUkx
DjAMBgNVBAcMBVdVSEFOMQ0wCwYDVQQKDARIQlRWMQwwCgYDVQQLDANDSlkwggEi
MA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQC8elmgAtgkp3lrtVLGtan1ktQ9
+VxIofV88da9GL07lcPpMjJFqUpMngU7F+G4JUEntm/nxH9VypEp8QE+CMnRdYN0
WXnJczSC1bZDF48ya1HnZ+H6wTxfZpAf4ZCzrXHUyPWUyiHKaOAY54UVQkNLF54y
rEN7hNy5NPPPQf6fnYoN/q72VqDfwGNEtfO7k57Zqf94uh09nnqNjHhuW2ZdfzHG
3qWdwq9Kj7Q0IeQ9ufI/gd3yCfmej63HF3KLUbzzYgDHFZsAFmwTsmCoimhtlQK/
c5rQ4brGpTKl9Lg4R0d+/p7+FcBM76a/V/S42S6oyFYRaXaYnm3zrXttQ8VXAgMB
AAGjZzBlMAsGA1UdDwQEAwIF4DAdBgNVHSUEFjAUBggrBgEFBQcDAQYIKwYBBQUH
AwIwNwYDVR0RBDAwLoIUanVtcHNlcnZlci5oYnJ0di5vcmeHBAr/yAWHBAr/yAGH
BAr/yAKHBAr/yAMwDQYJKoZIhvcNAQELBQADggEBAFphglFfhEwxjEQ6jsqGaiwt
r8tse1E6dsiPYjQeHq6sYKaV2G2KxGHs1Mh66augFG37ljV0XVtkaFUyc6F+b00p
Z7CSZ17gI7QcycZpcxClf7I3/CXpS/NDdYQR/yir1reYmE01H50bw5tNVaHZWrL0
kUXOtsh68dSq0lwbbNEoPh7bFZV746ycC8vZHGZVCzgCit2IRQa4OPt8lV025JJr
UTy/ASDLVZuGRkAa7z0dA5CFas9QFu/ya938NJVVFoHzUy+SwpME5rBlX9kU3pin
nkNQ5Bl3C10bEQtetAmdTGHV384rj2ZnfRLXobXw21oXJRLfuQPLvYHC8H4dsRQ=
-----END CERTIFICATE-----
...
# 将-----BEGIN CERTIFICATE-----到-----END CERTIFICATE-----中间的内容添加至/etc/pki/ca-trust/extracted/pem/tls-ca-bundle.pem 结尾
# 打开信任证书列表,使用SHIFT+G跳转到文件结尾,粘贴证书内容
vi /etc/pki/ca-trust/extracted/pem/tls-ca-bundle.pem
6、其它
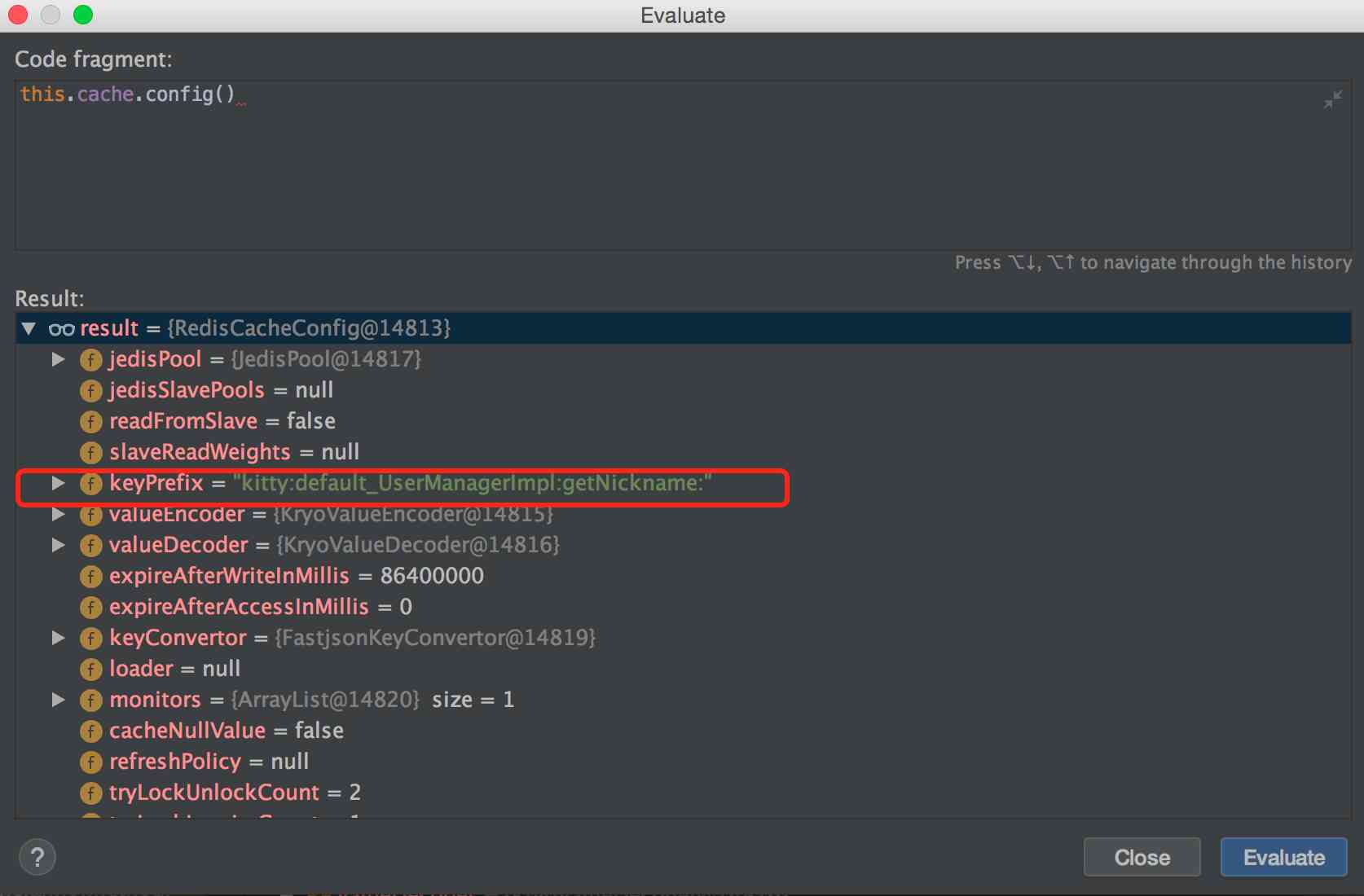
己注册过的koko实例因修改配置等原因需重新注册时,需要删除相关的accesskey
rm –rf /sas/jumpserver/koko/data/keys/.access_key
koko 日志文件路径:/sas/jumpserver/koko/data/logs
cat /sas/jumpserver/koko/data/logs/koko.log
版权声明
本文为[dusthunter]所创,转载请带上原文链接,感谢
https://blog.51cto.com/dusthunter/2547206
边栏推荐
- 企业数据库的选择通常由系统架构师主导决策 - thenewstack
- 对pandas 数据进行数据打乱并选取训练机与测试机集
- X Window System介紹
- 面经手册 · 第15篇《码农会锁,synchronized 解毒,剖析源码深度分析!》
- Asp.Net Core learning notes: Introduction
- 6.7 theme resolver theme style parser (in-depth analysis of SSM and project practice)
- JVM内存区域与垃圾回收
- mac 安装hanlp,以及win下安装与使用
- 面经手册 · 第14篇《volatile 怎么实现的内存可见?没有 volatile 一定不可见吗?》
- Gradient understanding decline
猜你喜欢
随机推荐
用Keras LSTM构建编码器-解码器模型
有关PDF417条码码制的结构介绍
Python3網路學習案例四:編寫Web Proxy
X Window System介紹
【新閣教育】窮學上位機系列——搭建STEP7模擬環境
mongodb(从0到1),11天mongodb初级到中级进阶秘籍
自然语言处理之分词、命名主体识别、词性、语法分析-stanfordcorenlp-NER(二)
高级 Vue 组件模式 (3)
为了省钱,我用1天时间把PHP学了!
【jmeter】實現介面關聯的兩種方式:正則表示式提取器和json提取器
JVM内存区域与垃圾回收
阿里CCO项目组面试的思考
连肝三个通宵,JVM77道高频面试题详细分析,就这?
Python machine learning algorithm: linear regression
普通算法面试已经Out啦!机器学习算法面试出炉 - kdnuggets
【C/C++ 1】Clion配置与运行C语言
一时技痒,撸了个动态线程池,源码放Github了
6.9.2 session flashmapmanager redirection management
Network programming NiO: Bio and NiO
Python + Appium 自動化操作微信入門看這一篇就夠了