当前位置:网站首页>Jarvis OJ shell traffic analysis
Jarvis OJ shell traffic analysis
2022-07-05 16:46:00 【[mzq]】
shell Flow analysis
Title Attachment : https://dn.jarvisoj.com/challengefiles/+_+.rar.977e2c637dc492fb9a7cf7595c852044
Use strings Find keywords ctf I found one of them python Encryption and decryption script
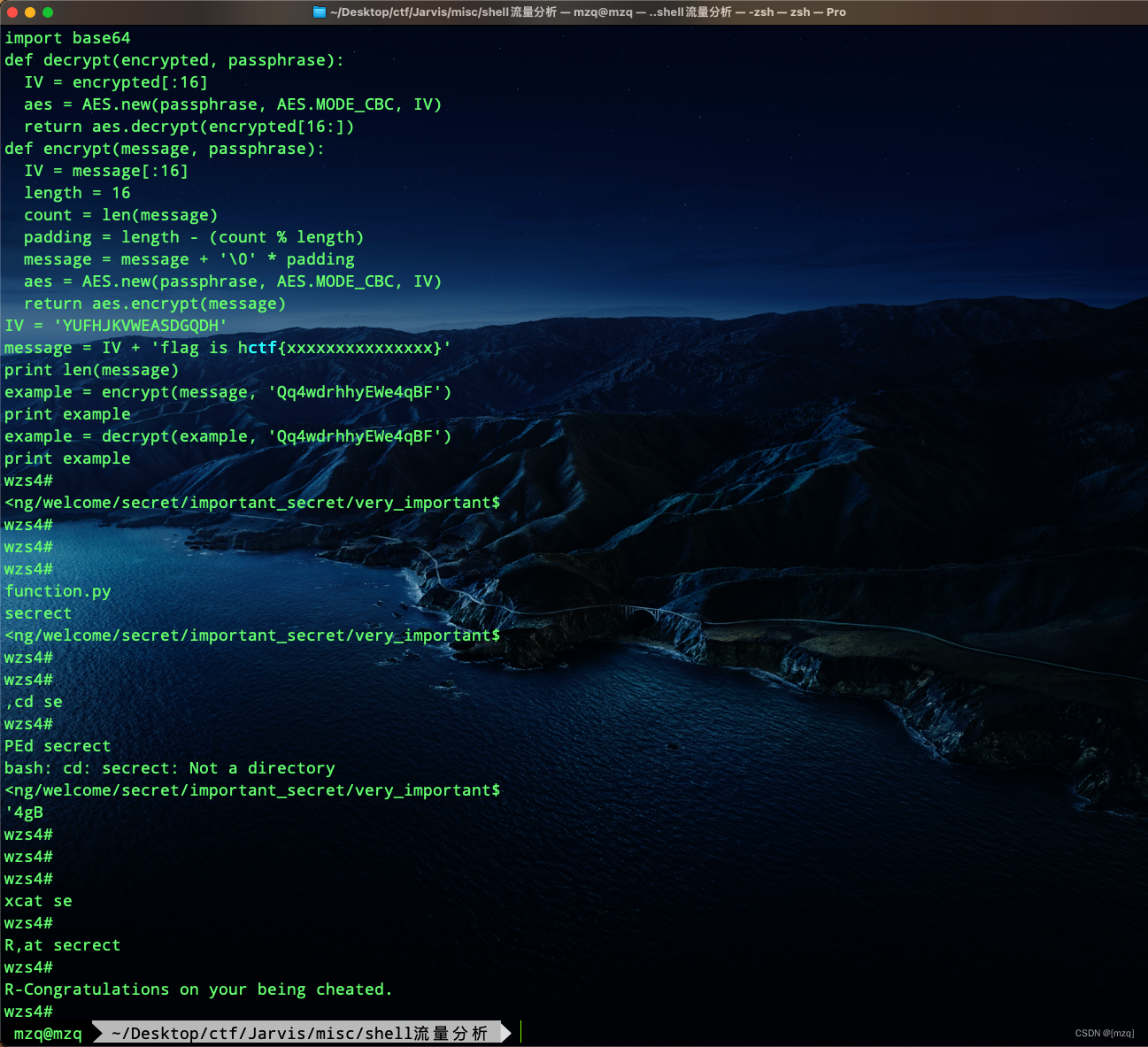
use wireshark analysis tcp There are encrypted and decrypted in the stream python2 Script
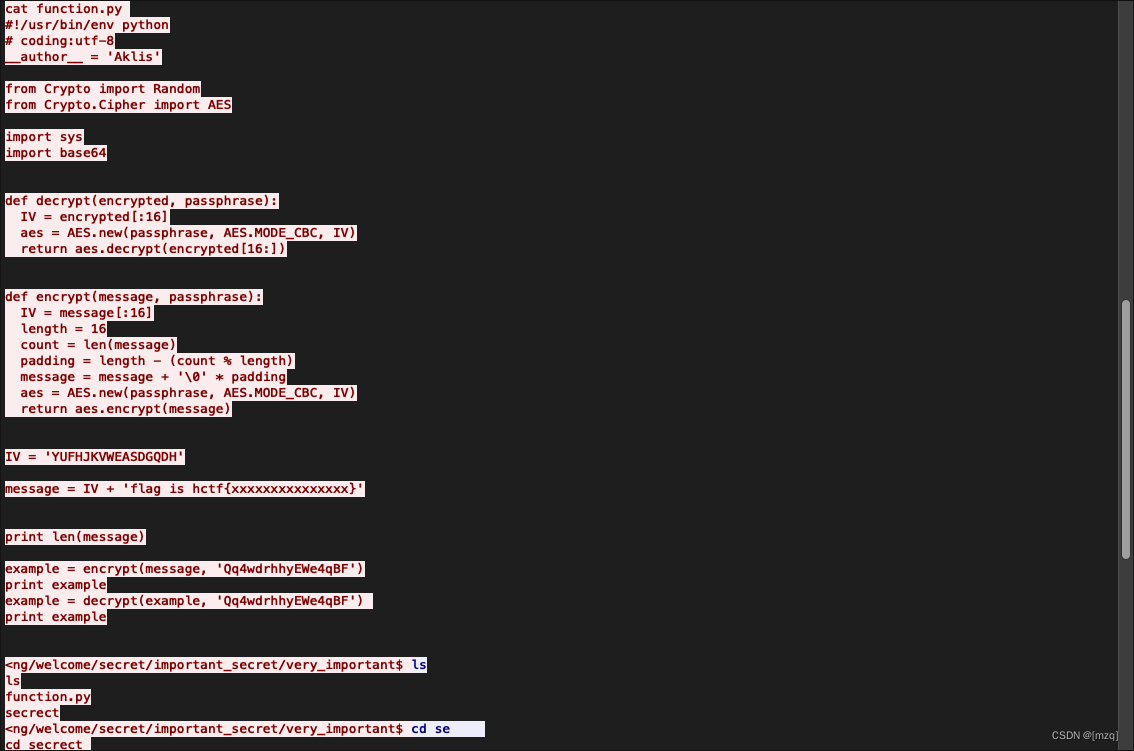
Also found a string base64 Encrypted string , Try to decrypt and get garbled code
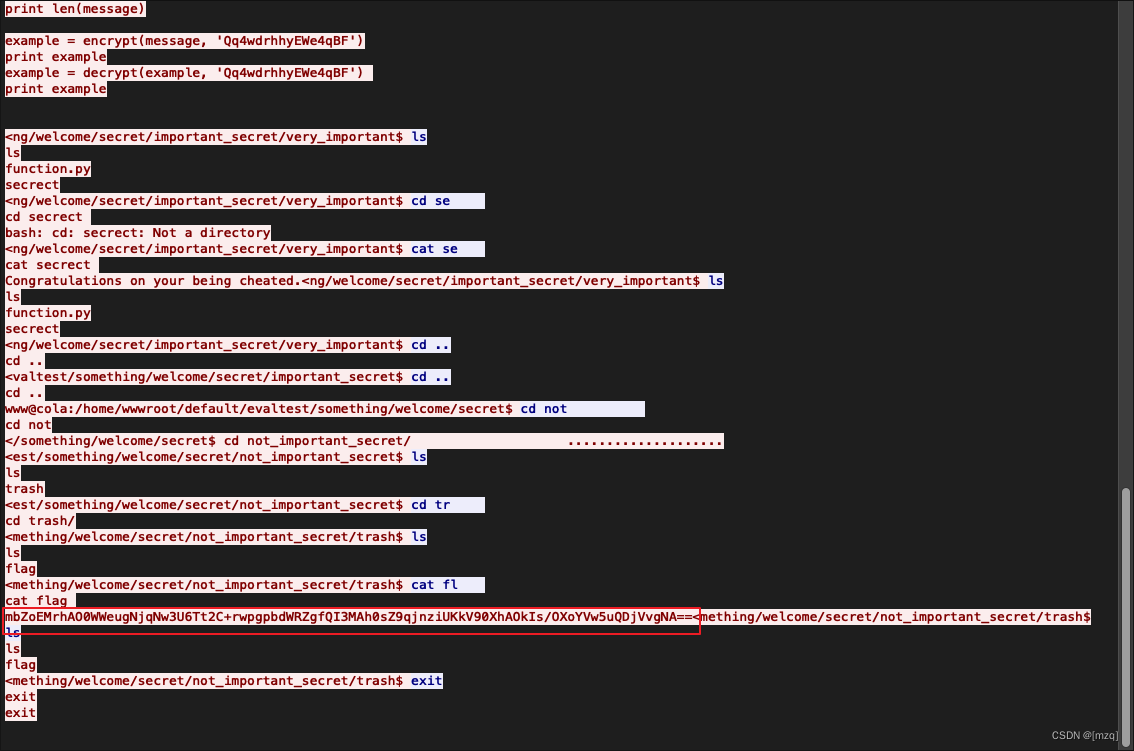
Guess after decryption python Script decryption
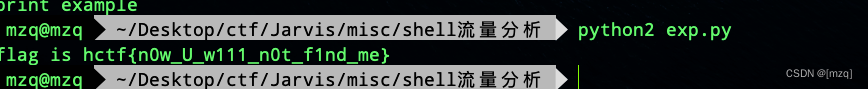
from Crypto import Random
from Crypto.Cipher import AES
import sys
import base64
def decrypt(encrypted, passphrase):
IV = encrypted[:16]
aes = AES.new(passphrase, AES.MODE_CBC, IV)
return aes.decrypt(encrypted[16:])
def encrypt(message, passphrase):
IV = message[:16]
length = 16
count = len(message)
padding = length - (count % length)
message = message + '\0' * padding
aes = AES.new(passphrase, AES.MODE_CBC, IV)
return aes.encrypt(message)
IV = 'YUFHJKVWEASDGQDH'
message = IV + 'flag is hctf{xxxxxxxxxxxxxxx}'
#print len(message)
#example = encrypt(message, 'Qq4wdrhhyEWe4qBF')
#print example
example = "mbZoEMrhAO0WWeugNjqNw3U6Tt2C+rwpgpbdWRZgfQI3MAh0sZ9qjnziUKkV90XhAOkIs/OXoYVw5uQDjVvgNA=="
example = base64.b64decode(example)
example = decrypt(example, 'Qq4wdrhhyEWe4qBF')
print example
flag is hctf{
n0w_U_w111_n0t_f1nd_me}
边栏推荐
- Clear restore the scene 31 years ago, volcanic engine ultra clear repair beyond classic concert
- 公司自用的国产API管理神器
- Desci: is decentralized science the new trend of Web3.0?
- Flet tutorial 12 stack overlapping to build a basic introduction to graphic and text mixing (tutorial includes source code)
- Apiccloud cloud debugging solution
- Binary tree related OJ problems
- PSPNet | 语义分割及场景分析
- Jarvis OJ Webshell分析
- 服务器的数据库连不上了2003,10060“Unknown error“【服务已起、防火墙已关、端口已开、netlent 端口不通】
- Apple 已弃用 NavigationView,使用 NavigationStack 和 NavigationSplitView 实现 SwiftUI 导航
猜你喜欢
![[brush questions] effective Sudoku](/img/5b/3064170bebd1ccbee68d6a85d23830.png)
[brush questions] effective Sudoku
怎样在电脑上设置路由器的WiFi密码

Jarvis OJ Flag
How to install MySQL
HiEngine:可媲美本地的云原生内存数据库引擎
Explain in detail the functions and underlying implementation logic of the groups sets statement in SQL
清晰还原31年前现场,火山引擎超清修复Beyond经典演唱会
Fleet tutorial 09 basic introduction to navigationrail (tutorial includes source code)
Cs231n notes (bottom) - applicable to 0 Foundation
Win11 prompt: what if the software cannot be downloaded safely? Win11 cannot download software safely
随机推荐
PSPNet | 语义分割及场景分析
If you can't afford a real cat, you can use code to suck cats -unity particles to draw cats
Google Earth Engine(GEE)——Kernel核函数简单介绍以及灰度共生矩阵
sqlserver 做cdc 要对数据库性能有什么要求么
《21天精通TypeScript-3》-安装搭建TypeScript开发环境.md
The new version of effect editor is online! 3D rendering, labeling, and animation, this time an editor is enough
Data access - entityframework integration
Mongodb getting started Tutorial Part 04 mongodb client
[echart] resize lodash to realize chart adaptation when window is zoomed
践行自主可控3.0,真正开创中国人自己的开源事业
Single merchant v4.4 has the same original intention and strength!
[deep learning] [original] let yolov6-0.1.0 support the txt reading dataset mode of yolov5
Cartoon: what is blue-green deployment?
Benji Banas membership pass holders' second quarter reward activities update list
漫画:什么是服务熔断?
yarn 常用命令
Starkware: to build ZK "universe"
Jarvis OJ Webshell分析
数据湖(十四):Spark与Iceberg整合查询操作
Android 隐私沙盒开发者预览版 3: 隐私安全和个性化体验全都要