当前位置:网站首页>Data reveal that the average cost is as high as $4.35 million in 2022, a record!
Data reveal that the average cost is as high as $4.35 million in 2022, a record!
2022-08-02 07:53:00 【Internet Security Research Institute】
The recently released "2022 Cost of Data Breach Report" shows that the scale and average cost of a global data breach in 2022 will hit a record high, with the average cost of a data breach as high as $4.35 million.
The 2022 Cost of a Data Breach Report is an in-depth analysis of real-world data breaches experienced by 550 organizations worldwide between March 2021 and March 2022.Analyzing data breach reports helps us understand how the current data breach affects us and what to do next.
The report summarizes the data security issues identified as follows:
1. The zero trust strategy needs to be taken seriously.80% of critical infrastructures do not implement a zero trust strategy, and 28% of data breaches in organizations that do not implement a zero trust program are related to ransomware or disruptive attacks.
2. Security technology can greatly reduce leakage costs.Organizations deploying AI and automated security technologies reduced breach costs by an average of $3.05 million, the most effective way to reduce breach costs observed.
3. Phishing attacks are the main means of hackers.Phishing and credential theft were the main reasons, resulting in an average breach cost of $4.91 million to victims.
4. The medical industry has become the hardest hit area.The healthcare industry is the industry with the highest data breach costs, with an average breach cost of $10.1 million in the healthcare industry in 2022.
5. Excessive trust in the supply chain.17% of breaches in critical infrastructure organizations are due to compromised business partners, underscoring the security risks posed by an environment of over-trust.
6. Paying the ransom does not reduce the cost of leakage.The total cost of breaches to businesses paying ransoms reached $812,000, above the average of $610,000.As a result, the total cost of a data breach is higher for businesses that choose to pay the ransom, and it also provides financial support for ransomware groups that could potentially expand their scale.
The persistence of global cyberattacks means that data breaches will have an ongoing "hard-to-eliminate impact" on businesses.The IBM report found that 83% of companies and institutions surveyed had experienced more than one data breach.At the same time, the after-effects of data breaches can also become apparent over time, with long-term effects on the victimized enterprise.Research data shows that nearly 50% of data breach costs are incurred more than a year after a data breach occurs.
Traditional security policies can protect an organization's network security and data security.However, sophisticated attackers have turned to attack vectors that organizations did not expect.They started targeting aspects that security teams often overlooked.For example, employees on social media platforms or for a collaboration tool - email.
Email is one of the most neglected aspects of business management.Email is the preferred method for hackers to gain initial access and infiltrate.
So, protecting email is protecting corporate data.
边栏推荐
- 自然语言处理 文本预处理(下)(张量表示、文本数据分析、文本特征处理等)
- Azure Synapse Analytics上创建用户并赋予权限
- 59:第五章:开发admin管理服务:12:MongoDB的使用场景;(非核心数据,数据量比较大的非核心数据,人脸照片等隐私的小文件;)
- MySQL-Multiversion Concurrency Control
- MySQL批量更新
- View port number occupancy
- View zombie processes
- MySQL-执行流程+缓存+存储引擎
- 【机器学习】实验2布置:基于回归分析的大学综合得分预测
- CollectionUtil:一个函数式风格的集合工具
猜你喜欢

【ROS基础】map、odom、base_link、laser 的理解 及其 tf 树的理解

以训辅教,以战促学 | 新版攻防世界平台正式上线运营!

LeetCode 2360. 图中的最长环
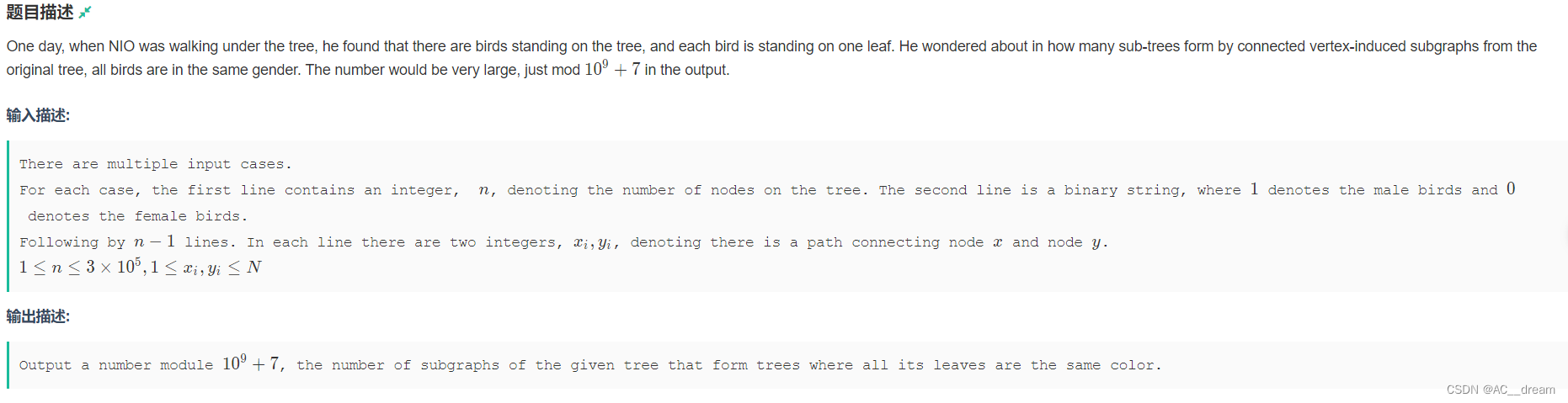
(2022牛客多校五)D-Birds in the tree(树形DP)
![The best interests of buying and selling stocks with handling fees [What is missing in the definition of DP status?]](/img/14/cd6ed7452230571db2e027f61dbdba.png)
The best interests of buying and selling stocks with handling fees [What is missing in the definition of DP status?]

在VMware上安装Metasploitable2

主流定时任务解决方案全横评

MySQL-数据库事务详解

Gradle系列——Gradle插件(基于Gradle文档7.5)day3-2
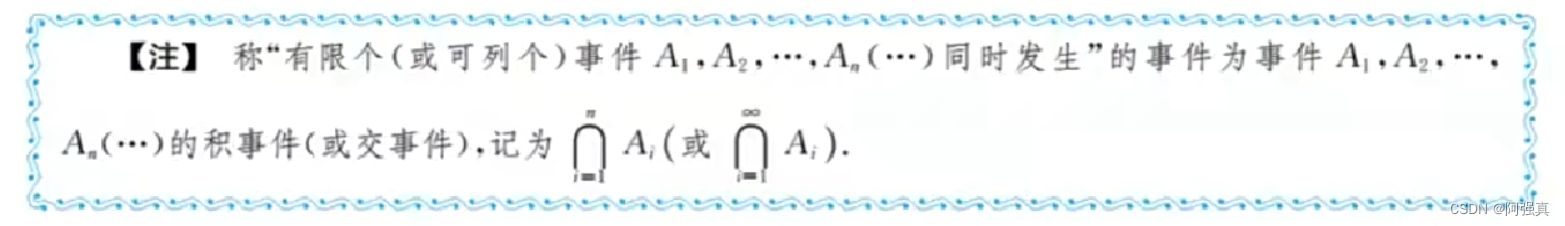
概率论与数理统计
随机推荐
【故障诊断分析】基于matlab FFT轴承故障诊断【含Matlab源码 2001期】
Enterprise training and reproduction guidebook - training and reasoning of the OpenPose model based on Huawei ModelArts platform, realizing the recognition of two behaviors of climbing and climbing ov
【杂】pip换国内源教程及国内源地址
MySQL-Multiversion Concurrency Control
The best interests of buying and selling stocks with handling fees [What is missing in the definition of DP status?]
MySQL-慢查询日志
Gradle系列——Gradle插件(基于Gradle文档7.5)day3-2
【CV】OpenVINO安装教程
入门opencv,欢笑快乐每一天
查看僵尸进程
OC-NSDictionary
请教一下,Flink SQL ,JDBC sink 入 mysql 库,想要搞一个自增主键,要怎么写
OC-Category
雷达人体存在感应器方案,智能物联网感知技术,实时感应人体存在
【请教】SQL语句按列1去重来计算列2之和
spark 读取本地文件
MySQL-数据库设计规范
【CNN回归预测】基于matlab卷积神经网络CNN数据回归预测【含Matlab源码 2003期】
初探形式化方法基本原理
LeetCode 2360. The longest cycle in a graph