当前位置:网站首页>Awk from entry to penetration (6) regular matching
Awk from entry to penetration (6) regular matching
2022-07-04 08:46:00 【Wonderful binary】
awk Of pattern In addition to using simple conditional expressions , You can also use regular expressions .
AWK Regular expressions can be processed easily and efficiently . A large number of complex tasks can be solved by extremely simple regular expressions . Everyone who is proficient in the command line knows the real power of regular expressions .
This chapter will focus on the use of standard regular expressions .awk The regularity of is basically the same as that of ordinary regularity , But in awk You need to use two regular expressions in / wrap up .
spot (Dot)
Dot character (.) You can match all characters except the end of line character . For example, the stool below can match fin, fun, fan wait .
$ echo -e "cat\nbat\nfun\nfin\nfan" | awk '/f.n/'
Executing the above command can get the following results :
fun
fin
fan
OK, let's start
Line start (^) Match the beginning of a line . The following example will output all the characters as strings The The first line .
$ echo -e "This\nThat\nThere\nTheir\nthese" | awk '/^The/'
You can get the following result by executing the above command :
There
Their
End of line
Line end ($) Match the end of a line . In the following example, all characters will be output n The ending line :
$ echo -e "knife\nknow\nfun\nfin\nfan\nnine" | awk '/n$/'
You can get the following result by executing the above command :
Ca
fin
fan
Match character set
Matching character sets are used to match sets ( Denoted by square brackets ) A character in . In the following example , matching Call And Tall It doesn't match Ball.
$ echo -e "Call\nTall\nBall" | awk '/[CT]all/'
You can get the following result by executing the above command :
Call
Tall
Exclusion set
Regular matching excludes characters from the set . In the following example, only Ball.
$ echo -e "Call\nTall\nBall" | awk '/[^CT]all/'
You can get the following result by executing the above command :
Ball
or
A vertical bar (|) Allow regular expressions to implement logic or operations . The following example will output Ball And Call .
$ echo -e "Call\nTall\nBall\nSmall\nShall" | awk '/Call|Ball/'
You can get the following result by executing the above command :
Call
Ball
Once at most
The symbol ( ?) The preceding character does not appear or appears once . The following example matches Colour And Color. Use ? bring u Becomes an optional character .
$ echo -e "Colour\nColor" | awk '/Colou?r/'
You can get the following result by executing the above command :
Colour
Color
Zero or more times
The symbol (*) Allow the character before it to appear multiple times or not . The following example will match ca,cat, catt wait .
$ echo -e "ca\ncat\ncatt" | awk '/cat*/'
You can get the following result by executing the above command :
ca
cat
catt
One or more times
The symbol (+) Make the character before it appear one or more times . The following example will match a 2 Or multiple consecutive 2.
$ echo -e "111\n22\n123\n234\n456\n222" | awk '/2+/'
You can get the following result by executing the above command :
22
123
234
222
grouping
Brackets are used for grouping and characters | Used to provide a variety of options . The following regular expression will match all that contain Apple Juice or Aplle Cake The line of .
$ echo -e "Apple Juice\nApple Pie\nApple Tart\nApple Cake" | awk '/Apple (Juice|Cake)/'
You can get the following result by executing the above command :
Apple Juice
Apple Cake
Multiple expressions can use && perhaps , come together , The meaning of and :
awk ‘/^ Start time date /,/^ End time date /’ nginx.log
such as , Query time period 2021-03-24 10:12:12 To 2021-09-24 10:12:12,
It can be used awk ‘/^2021-03-24 10:12:*/,/^2021-09-24 10:12:*/’ nginx.log Inquire about .
边栏推荐
- Ehrlich sieve + Euler sieve + interval sieve
- Internal learning
- awk从入门到入土(11)awk getline函数详解
- 微服务入门:Gateway网关
- MySQL relearn 1-centos install mysql5.7
- From scratch, use Jenkins to build and publish pipeline pipeline project
- FOC控制
- Flutter 集成 amap_flutter_location
- The basic syntax of mermaid in typera
- L1 regularization and L2 regularization
猜你喜欢
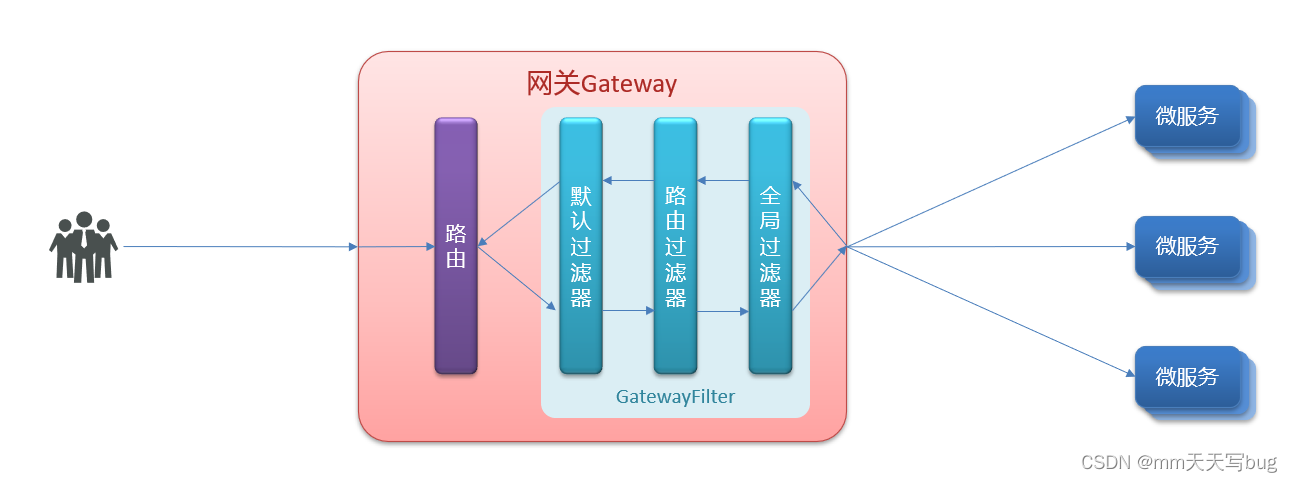
微服务入门:Gateway网关

Codeforces Round #803 (Div. 2)(A-D)
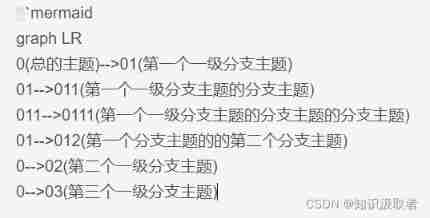
The basic syntax of mermaid in typera
Fault analysis | MySQL: unique key constraint failure
C, Numerical Recipes in C, solution of linear algebraic equations, Gauss Jordan elimination method, source code
Newh3c - routing protocol (RIP, OSPF)
manjaro安装微信
What if the wireless network connection of the laptop is unavailable
![Leetcode topic [array] -136- numbers that appear only once](/img/6d/f2e4b812e5dd872fbeb43732d6f27f.jpg)
Leetcode topic [array] -136- numbers that appear only once

4 small ways to make your Tiktok video clearer
随机推荐
A method for detecting outliers of data
Show server status on Web page (on or off) - PHP
How to choose solid state hard disk and mechanical hard disk in computer
awk从入土到入门(10)awk内置函数
Codeforces Round #803 (Div. 2)(A-D)
How can we make a monthly income of more than 10000? We media people with low income come and have a look
Take you to master the formatter of visual studio code
Educational Codeforces Round 119 (Rated for Div. 2)
C, Numerical Recipes in C, solution of linear algebraic equations, Gauss Jordan elimination method, source code
OpenFeign 服务接口调用
Question 49: how to quickly determine the impact of IO latency on MySQL performance
[error record] no matching function for call to 'cacheflush' cacheflush();)
From scratch, use Jenkins to build and publish pipeline pipeline project
FOC control
What if the wireless network connection of the laptop is unavailable
[BSP video tutorial] stm32h7 video tutorial phase 5: MDK topic, system introduction to MDK debugging, AC5, AC6 compilers, RTE development environment and the role of various configuration items (2022-
2022 electrician (intermediate) examination question bank and electrician (intermediate) examination questions and analysis
Educational Codeforces Round 115 (Rated for Div. 2)
Basic discipline formula and unit conversion
How to re enable local connection when the network of laptop is disabled