当前位置:网站首页>[attack and defense world | WP] cat
[attack and defense world | WP] cat
2022-07-04 08:31:00 【ethanyi9】
【 Attack and defend the world | WP】CAT
The problem solving steps
analysis
Open the page to see 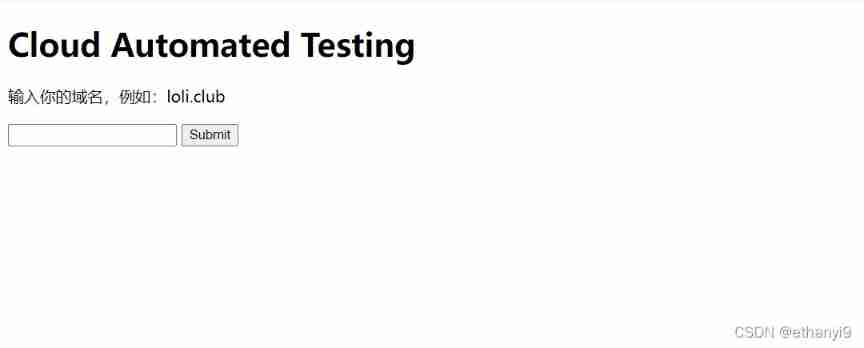
Input url Found no response , And input 127.0.0.1 This kind of ip After the address , Echo occurred
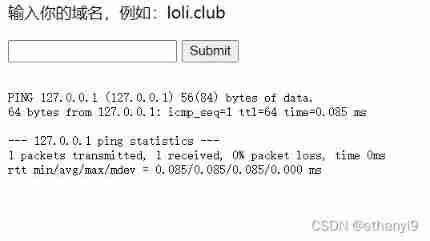
Find out url You can enter values directly , Let's try wide byte input , That is input %80, The error reporting interface appears 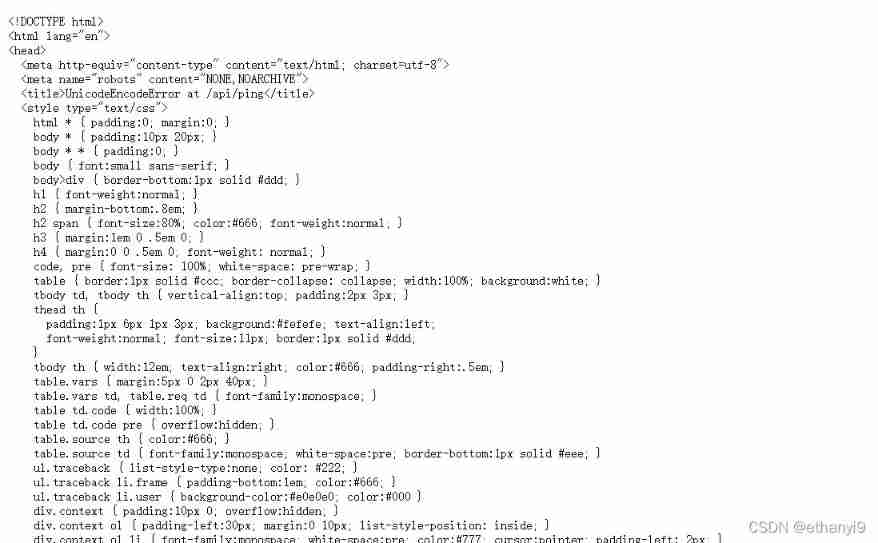
Replace the error reporting interface with html, Found to be Django Error reporting interface
The bosses say yes django The code is set to gbk Caused wide characters to be incorrectly encoded ( More than the ascii Code range ).
The idea behind is to look at the prompt directly , I heard that there was a hint during the game 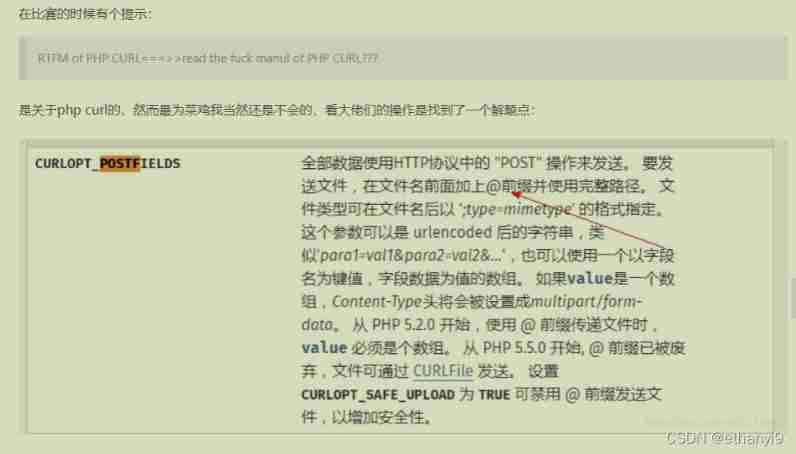
That is to say, it can be used @ And file path
Then we can only follow the train of thought , That is, first look at the previous error page database The path of ( There is no idea to find others here , Just look at the database first )
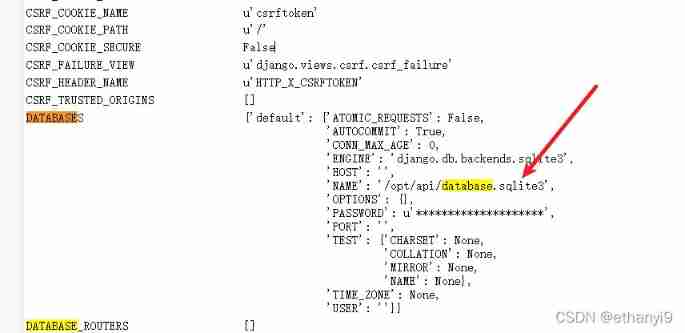
Then read the file , Input
@/opt/api/database.sqlite3

Learning knowledge
URL code
What is? URL code
url Coding is a coding format , It and utf-8 perhaps GBK The difference in coding is url Encoding is for characters other than alphanumeric , for instance :
- ASCII Character control code : character in range 00-1F Hexadecimal (0-31 Decimal system ) and 7F(127 Decimal system )
- Not ASCII Encoding format characters , such as GBK code 、utf-8 Code the Chinese character part of these two codes ( notes :GBK Chinese characters in the code are two bytes , stay url In the code, it is shaped like %B4%BA, and utf-8 It's three bytes , stay url In the code, it is shaped like %E6%98%A5)
边栏推荐
- [CV] Wu Enda machine learning course notes | Chapter 9
- How to use C language code to realize the addition and subtraction of complex numbers and output structure
- ZABBIX 5.0 monitoring client
- Learn nuxt js
- Leetcode 23. Merge K ascending linked lists
- WordPress get_ Users() returns all users with comparison queries - PHP
- 小程序容器技术与物联网 IoT 可以碰撞出什么样的火花
- Redis 哨兵机制
- 根据数字显示中文汉字
- How to use MOS tube to realize the anti reverse connection circuit of power supply
猜你喜欢
Manjaro install wechat
ctfshow web255 web 256 web257
Redis sentinel mechanism
Moher college phpMyAdmin background file contains analysis traceability
![[CV] Wu Enda machine learning course notes | Chapter 9](/img/de/41244904c8853b8bb694e05f430156.jpg)
[CV] Wu Enda machine learning course notes | Chapter 9
How to re enable local connection when the network of laptop is disabled
【性能测试】一文读懂Jmeter
运动【跑步 01】一个程序员的半马挑战:跑前准备+跑中调整+跑后恢复(经验分享)

How college students choose suitable computers
go-zero微服务实战系列(九、极致优化秒杀性能)
随机推荐
【Go基础】1 - Go Go Go
Famous blackmail software stops operation and releases decryption keys. Most hospital IOT devices have security vulnerabilities | global network security hotspot on February 14
Basic operations of databases and tables ----- view data tables
How to send pictures to the server in the form of file stream through the upload control of antd
Newh3c - routing protocol (RIP, OSPF)
Div hidden in IE 67 shows blank problem IE 8 is normal
zabbix 5.0监控客户端
@Role of requestparam annotation
Leetcode 23. 合并K个升序链表
std::is_ union,std::is_ class,std::integral_ constant
DM8 tablespace backup and recovery
Devops Practice Guide - reading notes (long text alarm)
The second session of the question swiping and punching activity -- solving the switching problem with recursion as the background (I)
小程序容器技术与物联网 IoT 可以碰撞出什么样的火花
FRP intranet penetration, reverse proxy
Sort by item from the list within the list - C #
A single element in an ordered array
Snipaste convenient screenshot software, which can be copied on the screen
deno debugger
DM8 command line installation and database creation