当前位置:网站首页>How college students choose suitable computers
How college students choose suitable computers
2022-07-04 08:26:00 【Yisu cloud】
How college students choose the right computer
This article will explain in detail how college students choose suitable computers , Xiaobian thinks it's very practical , So share it for your reference , I hope you can gain something after reading this article .

One 、 General computer or Apple computer (WIN PC orMAC PC )
First of all, many people are Apple fans , And the shape of apple computer is also very beautiful . So many students think Apple computer should be the best . But in fact, when the computer chooses , It's not just about the brand , The important thing is to see the operating system of the computer .
Generally speaking, we divide computers into general computers and Apple computers , If you are professional , Is to choose WIN Version computer is still MAC PC . As we all know, most computers are Windows System , Although our systems may be different now , Yes, continue to use win7 Of , Have use win8 Of , And use win10 Systematic and so on , But it's basically all in Windows Under the series , In fact, most functional software is relatively general .
But the apple version uses Mac Version of the system , Therefore, many software installations are special installation packages , You need a special version to use . This brings about a problem , Many things you do on Apple computers may not be able to open or run on ordinary computers .
reminder : Here is a reminder , Because there are many computers in Colleges and universities , It's troublesome to update the whole generation , The cost is not low , So the computer configuration of general colleges and universities is not so high , And in addition to configuring several Apple computer rooms , Others are ordinary Windows System computer . Especially the computers configured in the classroom , All of them are Windows Version of the computer , This is likely to make some of our students' classroom presentations carefully prepared with Apple computers impossible to show . Therefore, you need to change the format and debug whether it can be opened in advance every time you make a report , Very trouble .
Overall speaking , In fact, for today's ordinary college students , I personally suggest not to buy one for the time being Mac Version of Apple Computer , Ordinary computers are more practical . And computers are also consumables , You can change another apple computer when you are about to graduate from college .
Two 、 College Students' computer configuration choices
Speaking of the configuration of College Students' computers , This is actually related to the major learned in the University . Generally, if you are not a professional with high requirements for computers , Similar processor 、 The graphics card 、 Memory and hard disk basically have no problem in learning and entertainment .
But if your major needs some special software , Including mapping 、 Video clips and so on , The requirements for computers are relatively higher . First, the memory should be larger , Processor intergenerational higher , The requirements of graphics card are also relatively high , At least a separate graphics card , The video memory is larger .
Of course, for some software operations like editing , Notebook computers are quite stuck anyway , If possible, it is better to configure desktop computers . But for students , Laptops are more convenient , Then the configuration needs to be more careful .
If you are a professional with high requirements for audio , Then the sound card configuration also needs to be considered .
Some students like playing games , Then the requirements for graphics cards are naturally higher . It is normal for college students to play games , As a leisure entertainment, there is no problem , But don't be too addicted , Delayed their own growth and progress .

About “ How college students choose the right computer ” This article is shared here , I hope the above contents can be of some help to you , So that you can learn more , If you think the article is good , Please share it for more people to see .
边栏推荐
- How to use MOS tube to realize the anti reverse connection circuit of power supply
- Moher College webmin unauthenticated remote code execution
- Moher College phpmailer remote command execution vulnerability tracing
- WordPress get_ Users() returns all users with comparison queries - PHP
- 【Go基础】1 - Go Go Go
- Three paradigms of database design
- DM8 database recovery based on point in time
- Need help resetting PHP counters - PHP
- Azure ad domain service (II) configure azure file share disk sharing for machines in the domain service
- C#,数值计算(Numerical Recipes in C#),线性代数方程的求解,Gauss-Jordan消去法,源代码
猜你喜欢
Unity text superscript square representation +text judge whether the text is empty
![[gurobi] establishment of simple model](/img/3f/d637406bca3888b939bead40b24337.png)
[gurobi] establishment of simple model

Linear algebra 1.1
Flask 常用组件
Moher college phpMyAdmin background file contains analysis traceability
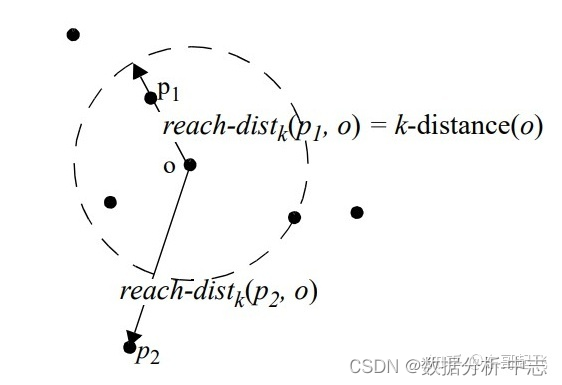
一文了解数据异常值检测方法
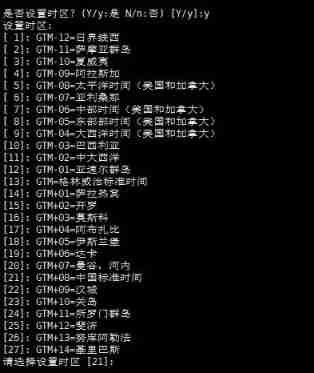
DM8 command line installation and database creation
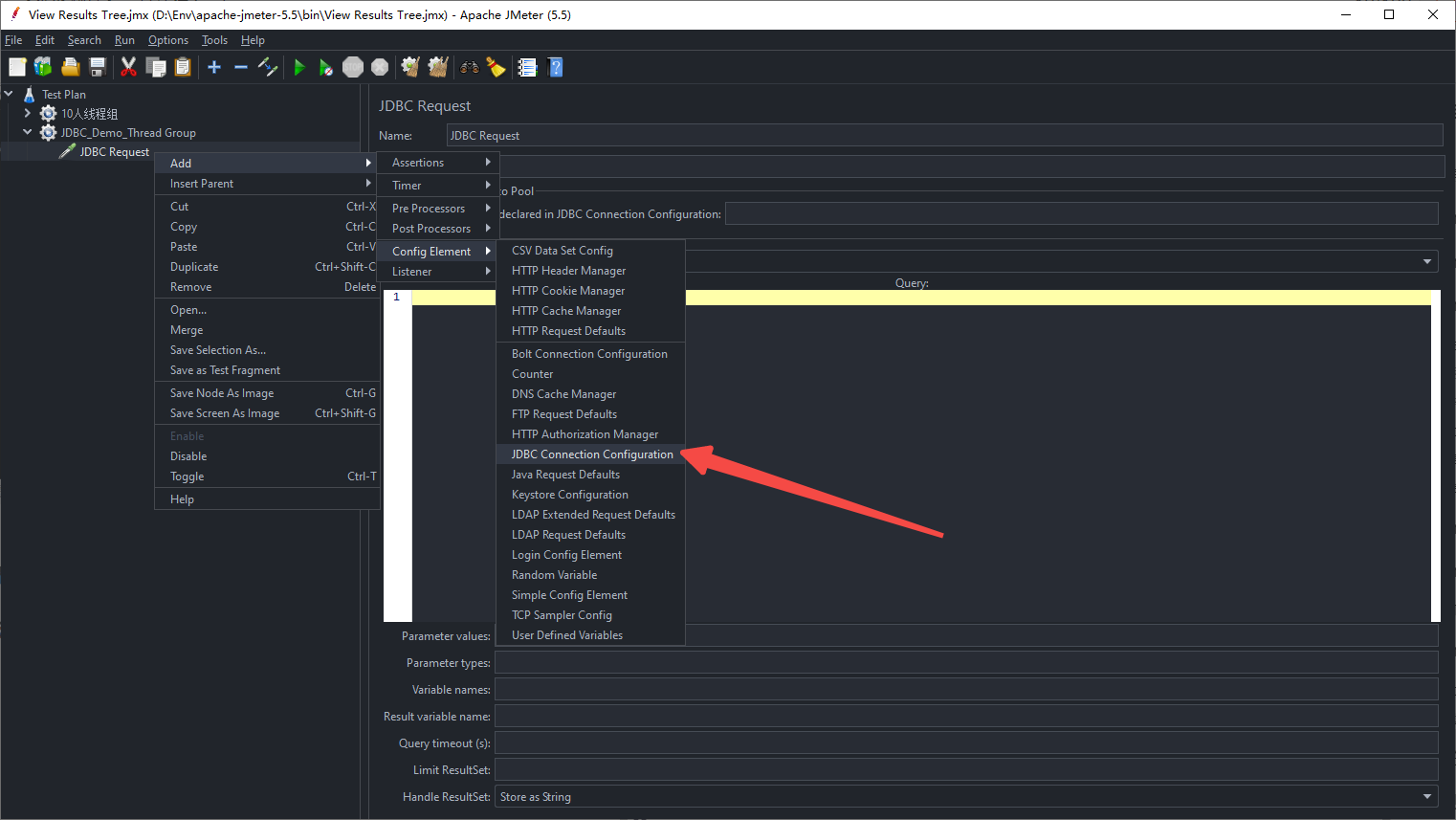
【性能測試】一文讀懂Jmeter
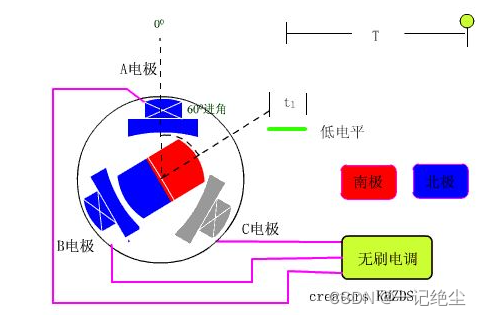
FOC控制
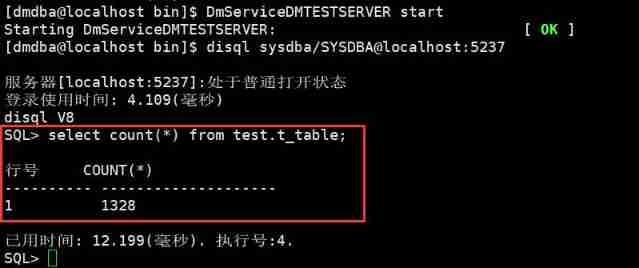
DM8 database recovery based on point in time
随机推荐
A single element in an ordered array
2022 tower crane driver examination and tower crane driver examination questions and analysis
Thesis learning -- time series similarity query method based on extreme point characteristics
Leetcode 146. LRU 缓存
Oracle stored procedures and functions
学习Nuxt.js
Leetcode 146. LRU cache
deno debugger
Display Chinese characters according to numbers
Add log file to slim frame - PHP
Linear algebra 1.1
How to get bytes containing null terminators from a string- c#
Wechat has new functions, and the test is started again
Moher College webmin unauthenticated remote code execution
Technology sharing | MySQL parallel DDL
Azure ad domain service (II) configure azure file share disk sharing for machines in the domain service
Snipaste convenient screenshot software, which can be copied on the screen
PHP converts seconds to timestamps - PHP
Flask 常用组件
Famous blackmail software stops operation and releases decryption keys. Most hospital IOT devices have security vulnerabilities | global network security hotspot on February 14