当前位置:网站首页>Detailed explanation of @accessories annotation of Lombok plug-in
Detailed explanation of @accessories annotation of Lombok plug-in
2022-07-02 16:52:00 【Promise__ shallow】
About @Accessors
@Accessors Annotations are used to configure lombok How to generate and display getters and setters Methods [email protected] Annotations can be annotated on classes or attributes
@Accessors There are three properties
- fluent
- chain
- prefix
A detailed explanation of these three attributes
fluent
fluent For a Boolean value , If true Generated get/set There is no way set/get Prefix , The default is false
for example :
@Accessors(flunet = true)
public class MyClass {
@Getter
private int num;
}
- 1.
- 2.
- 3.
- 4.
- 5.
Generated get Method is num(), instead of getNum()
chain
chain For a Boolean value , If true Generated set Method returns this, by false Generated set The method is void type . The default is false, Except when fluent by true when ,chain The default is true.
This is more commonly used , because set Method returns this object , Commonly used to realize chain programming , Such as
user.setName(" Zhang San ").setAge(12).setHeight(175)
- 1.
prefix
prefix For a series of string type , You can specify a prefix , Generate get/set Method will remove the specified prefix
for example :
@Accessors(prefix = "m")
public class MyClass {
@Getter
private int mNum;
}
- 1.
- 2.
- 3.
- 4.
- 5.
Generated get Method is getNum(), instead of getMNum()
边栏推荐
- PCL least median square method fitting plane
- LeetCode 4. 寻找两个正序数组的中位数(hard)
- 易语言abcd排序
- C语言中sprintf()函数的用法
- 2322. 从树中删除边的最小分数(异或和&模拟)
- 历史上的今天:支付宝推出条码支付;分时系统之父诞生;世界上第一支电视广告...
- System Verilog implements priority arbiter
- [cloud native] briefly talk about the understanding of flume, a massive data collection component
- Leetcode1380: lucky numbers in matrix
- TCP拥塞控制详解 | 2. 背景
猜你喜欢
![[North Asia data recovery] data recovery case of raid crash caused by hard disk disconnection during data synchronization of hot spare disk of RAID5 disk array](/img/51/f9c1eed37794db8c8d0eefd60b9e3d.jpg)
[North Asia data recovery] data recovery case of raid crash caused by hard disk disconnection during data synchronization of hot spare disk of RAID5 disk array

七一献礼:易鲸捷 “百日会战”完美收官 贵阳银行数据库提前封板

分析超700万个研发需求发现,这8门编程语言才是行业最需要的!
渗透工具-内网权限维持-Cobalt strike
![John blasting appears using default input encoding: UTF-8 loaded 1 password hash (bcrypt [blowfish 32/64 x3])](/img/4c/ddf7f8085257d0eb8766dbec251345.png)
John blasting appears using default input encoding: UTF-8 loaded 1 password hash (bcrypt [blowfish 32/64 x3])
数字IC手撕代码--投票表决器

⌈ 2022 ⌋ how to use webp gracefully in projects
Where can I open computer administrator permissions

Digital IC hand tearing code -- voting device
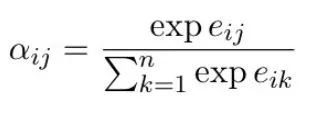
What is the difference between self attention mechanism and fully connected graph convolution network (GCN)?
随机推荐
System Verilog implements priority arbiter
学生选课系统(山东农业大学课程设计)
Yolov5 practice: teach object detection by hand
基于多元时间序列对高考预测分析案例
Interview summary of large factories
Yyds dry goods inventory has not revealed the artifact? Valentine's Day is coming. Please send her a special gift~
[error record] the connection of the flutter device shows loading (disconnect | delete the shuttle/bin/cache/lockfile file)
What is the difference between self attention mechanism and fully connected graph convolution network (GCN)?
DigiCert SSL证书支持中文域名申请吗?
Mathematical analysis_ Notes_ Chapter 5: univariate differential calculus
Global and Chinese market of jacquard looms 2022-2028: Research Report on technology, participants, trends, market size and share
Exploration and practice of integration of streaming and wholesale in jd.com
Data security industry series Salon (III) | data security industry standard system construction theme Salon
How to solve the failure of printer driver installation of computer equipment
Classic quotations
曆史上的今天:支付寶推出條碼支付;分時系統之父誕生;世界上第一支電視廣告...
MySQL port
图书管理系统(山东农业大学课程设计)
Yyds dry inventory company stipulates that all interfaces use post requests. Why?
unity Hub 登錄框變得很窄 無法登錄