当前位置:网站首页>Principles of BTC cryptography
Principles of BTC cryptography
2022-07-03 05:09:00 【Adobee Chen】
The premise is to master the basic skills of programming : Array 、 Linked list 、 Binary tree 、 hash function
Reference material : BitCoin and Cryptocurrency Technologies A Comprehensive Introduction、 Ethereum white paper 、 Yellow book 、 Source code 、Solidty file
Used in cryptography hash The function is called Cryptographic hash function, There are two important properties. One is called Collision resistance
for example x y ,H(x)=H(y) It's called hash collision ( Different inputs , The output is the same )
y ,H(x)=H(y) It's called hash collision ( Different inputs , The output is the same )
1. For cryptography hash Functions cannot be artificially made hash Collision
2. For cryptography hash The function is unidirectional , irreversible
For example
When one predicts the limit of the stock market tomorrow , It cannot be disclosed in advance . Because if this person may guide the direction of the rise and fall of the stock market ( Everyone heard him say which stock will rise tomorrow , Everyone buys that stock ), The best way is for him to write the forecast on a piece of paper , Give this piece of paper to the public trust institution .
Corresponding to the digital world , That's what this is x, Conduct hash(x). Wait until the opening tomorrow , To use this x Judge . because hash(x) It's irreversible , He cannot tamper with the result
边栏推荐
- cookie session jwt
- 2022-02-11 daily clock in: problem fine brush
- Yolov5 input (II) | CSDN creative punch in
- Notes | numpy-11 Array operation
- Esp32-c3 learning and testing WiFi (II. Wi Fi distribution - smart_config mode and BlueIf mode)
- The programmer resigned and was sentenced to 10 months for deleting the code. JD came home and said that it took 30000 to restore the database. Netizen: This is really a revenge
- Shuttle + alluxio accelerated memory shuffle take-off
- M1 Pro install redis
- Detailed explanation of the output end (head) of yolov5 | CSDN creation punch in
- Distinguish between releases and snapshots in nexus private library
猜你喜欢

Detailed explanation of yolov5 training own data set

On typescript and grammar
Source insight garbled code solution
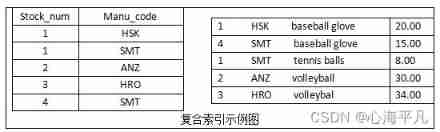
Gbase8s composite index (I)
Detailed explanation of the output end (head) of yolov5 | CSDN creation punch in

微服务常见面试题

【批处理DOS-CMD命令-汇总和小结】-CMD窗口的设置与操作命令-关闭cmd窗口、退出cmd环境(exit、exit /b、goto :eof)
appium1.22.x 版本後的 appium inspector 需單獨安裝

Appium 1.22. L'Inspecteur appium après la version X doit être installé séparément

Kept hot standby and haproxy
随机推荐
On typescript and grammar
1111 online map (30 points)
[set theory] relational power operation (relational power operation | examples of relational power operation | properties of relational power operation)
Shuttle + alluxio accelerated memory shuffle take-off
Online VR model display - 3D visual display solution
Review the configuration of vscode to develop golang
Chapter II program design of circular structure
Introduction to deep learning (II) -- univariate linear regression
[set theory] relation properties (reflexivity | reflexivity theorem | reflexivity | reflexivity theorem | example)
Source insight garbled code solution
SSM framework integration
Learning record of arouter principle
My first Smartphone
sql语句模糊查询遇到的问题
cookie session jwt
@RequestMapping
[Yu Yue education] basic reference materials of interchangeability and measurement technology of Zhongyuan Institute of Technology
M1 Pro install redis
[develop wechat applet local storage with uni app]
1119 pre- and post order traversals (30 points)