当前位置:网站首页>When kubernetes encounters confidential computing, see how Alibaba protects the data in the container! (Internet disk link attached)
When kubernetes encounters confidential computing, see how Alibaba protects the data in the container! (Internet disk link attached)
2020-11-08 11:01:00 【Programmer interview】
Today I share with you the internal information of Alibaba , When Kubernetes Encounter secret Computing , How does Ali protect the data in the container ! Pull down at the end of the text to get the link to the network disk
- Introduction to confidential Computing
1.1 Application container security status 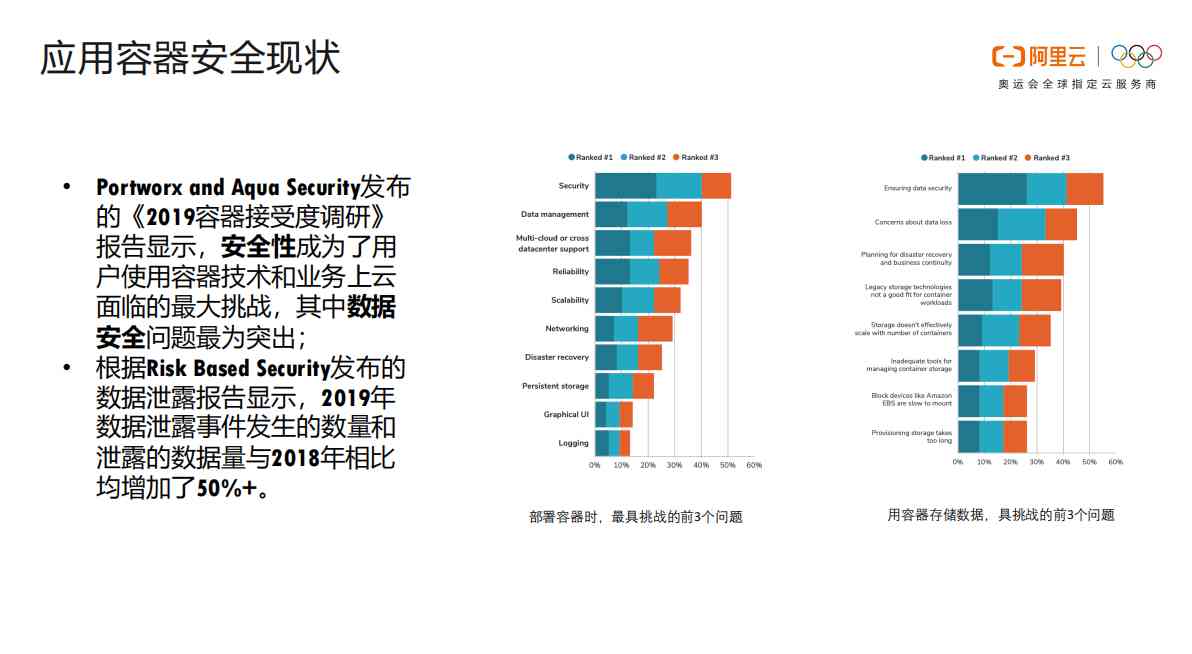
1.2 The age of secret computing is coming 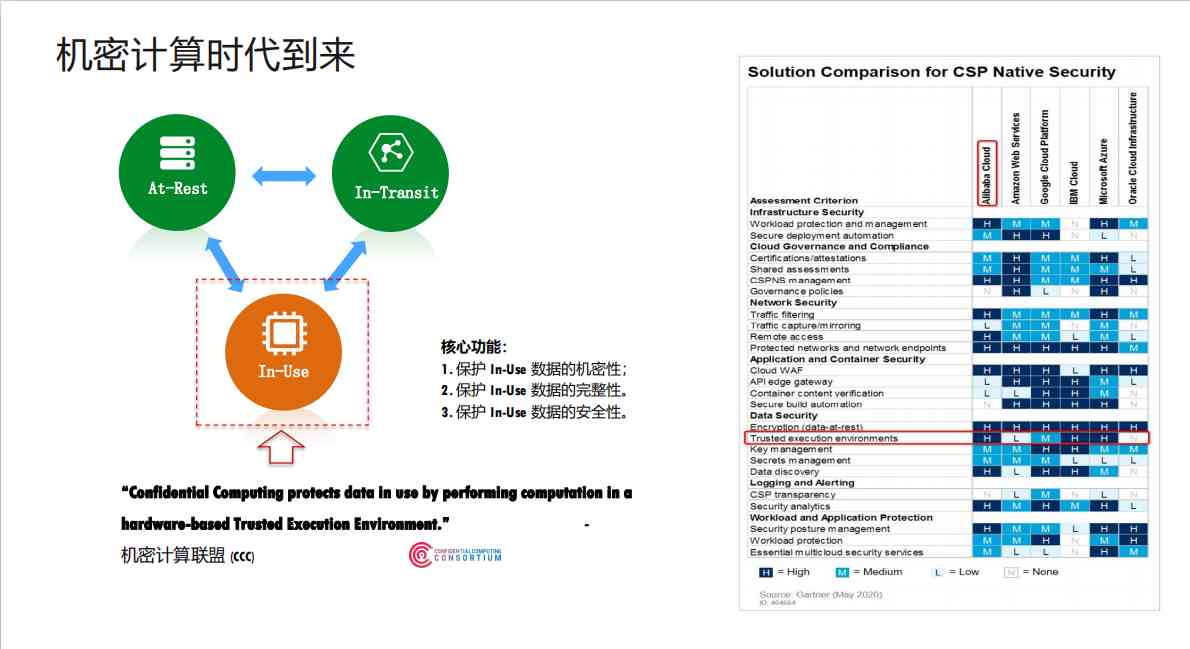
1.3 Computing confidential business scenarios 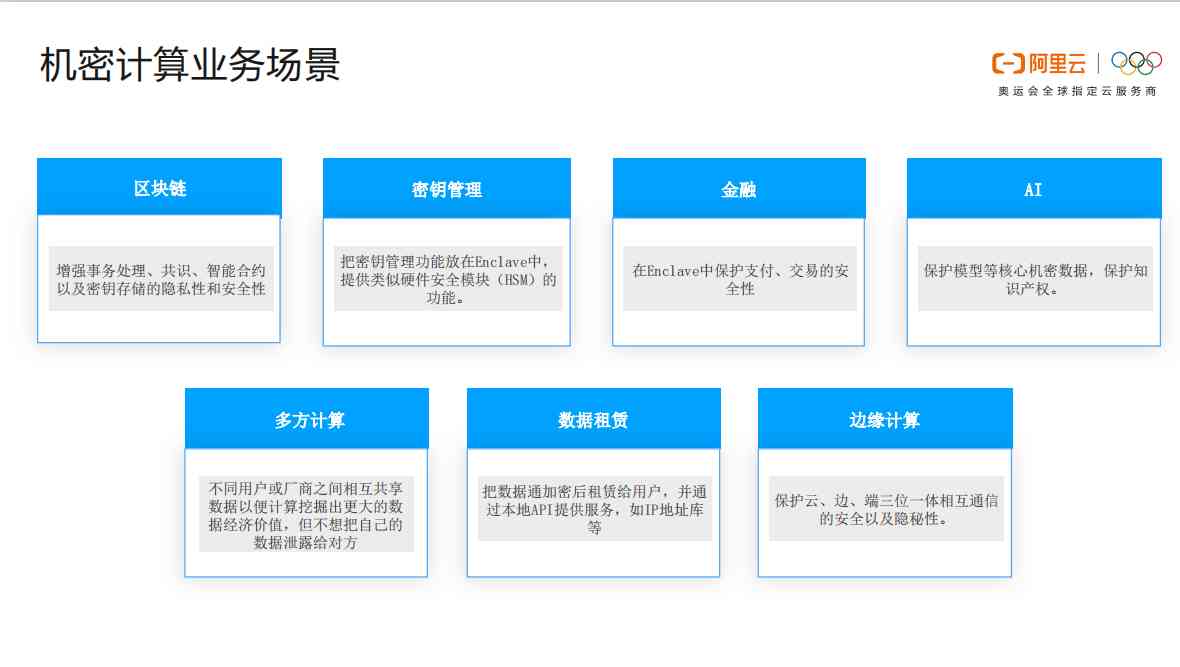
1.4 The difference between secure containers and secret Computing 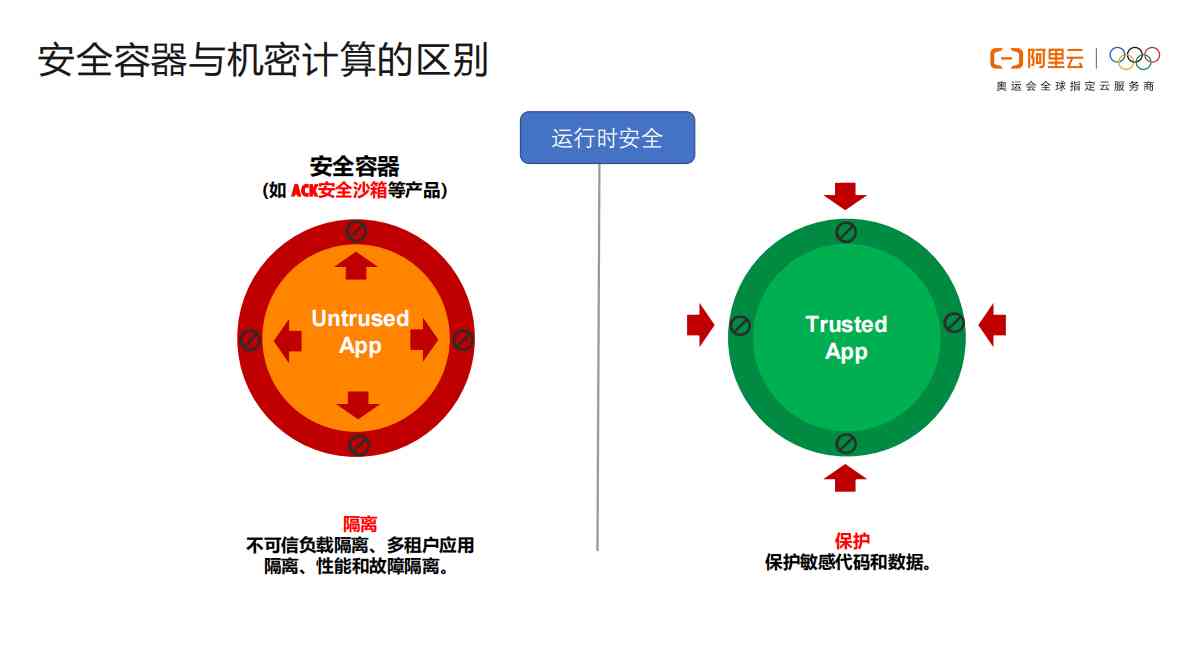
1.5 TEE Hardware platform 
1.6 Intel SGX There are smaller ones TCB(Trusted Computing Base) 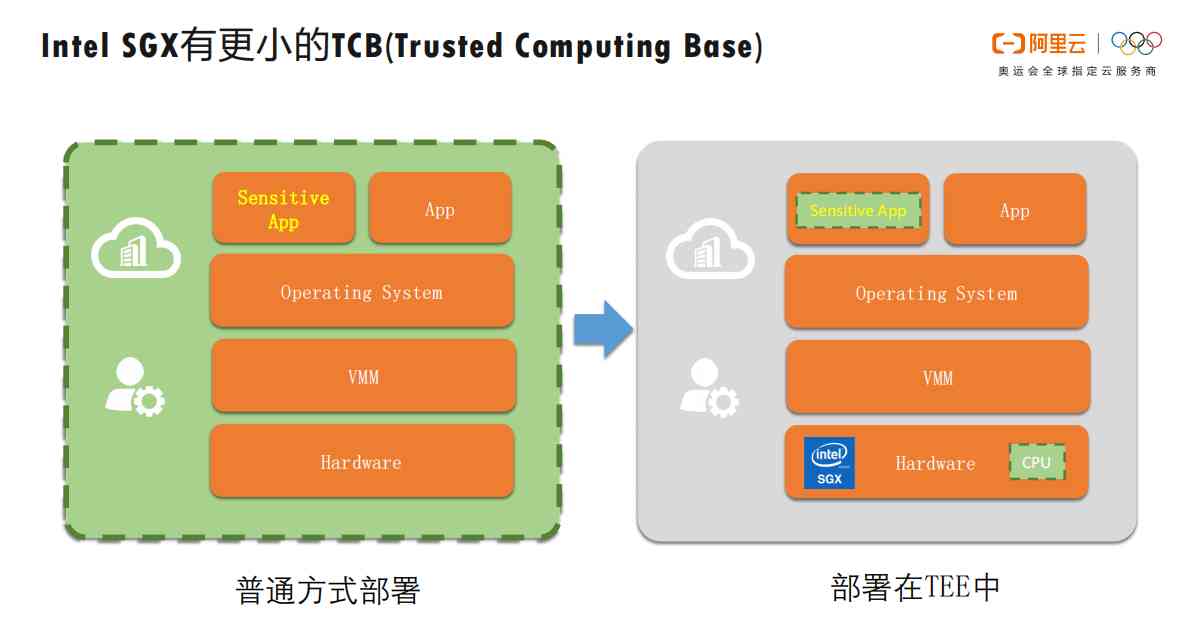
1.7 be based on Intel SGX Trusted application development and use process of 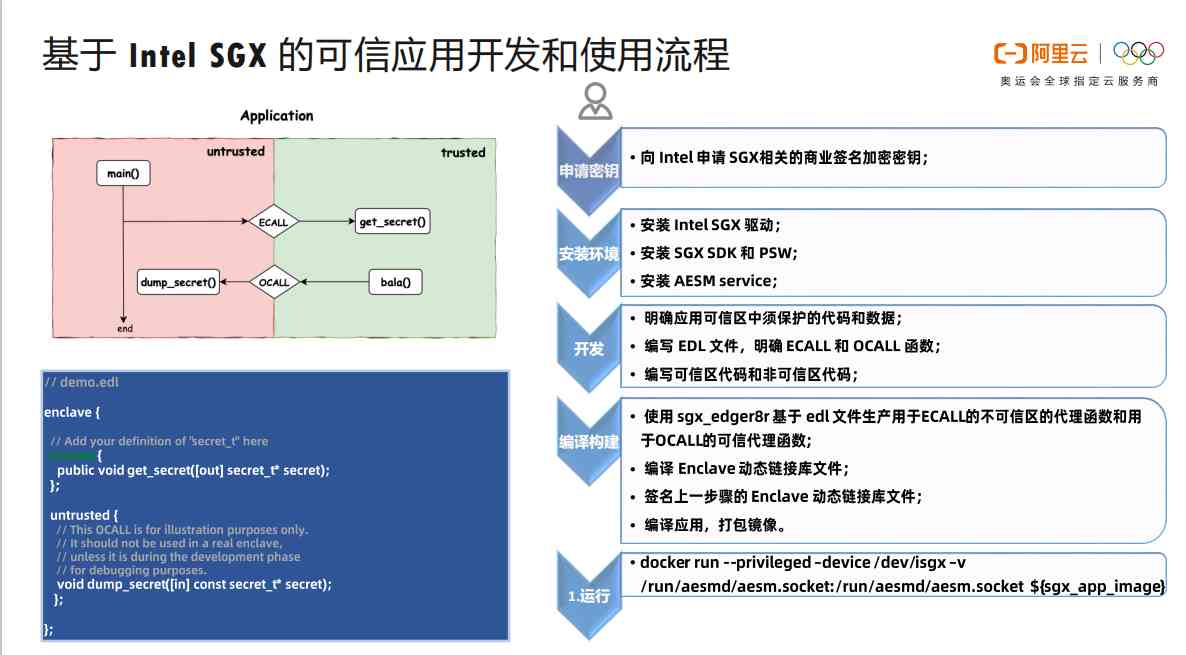
- InclavareContainers Protect sensitive applications and data
2.1 Inclavare Containers The goal and value of 
2.2 Inclavare Containers framework 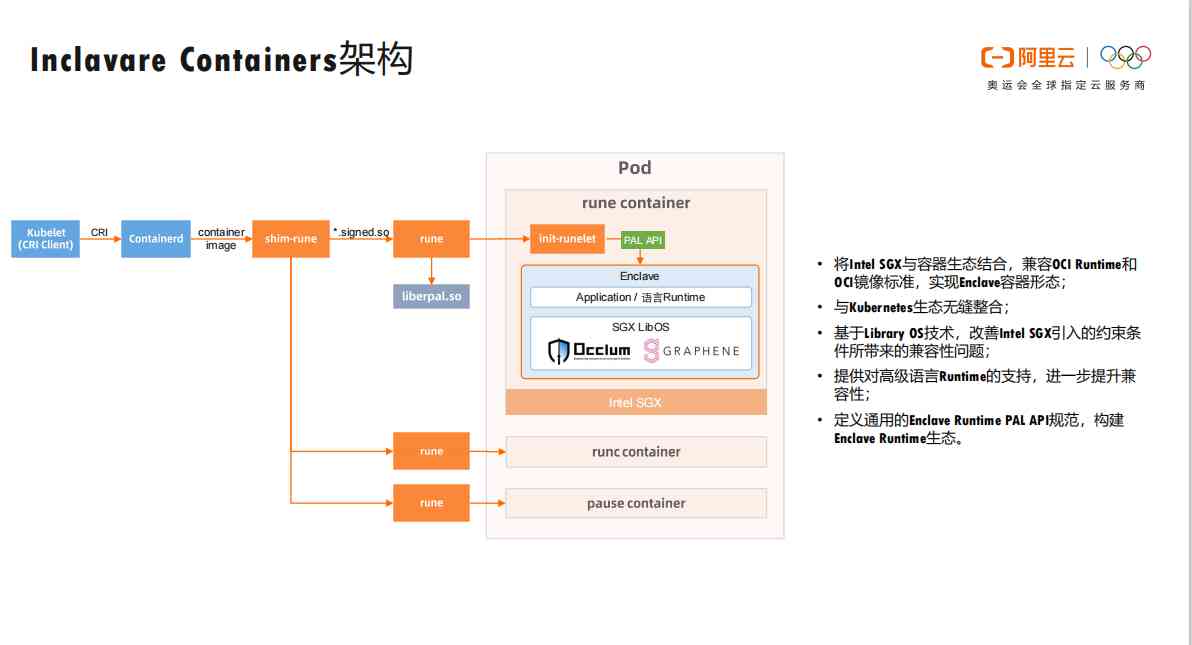
2.3 shim-rune Workflow 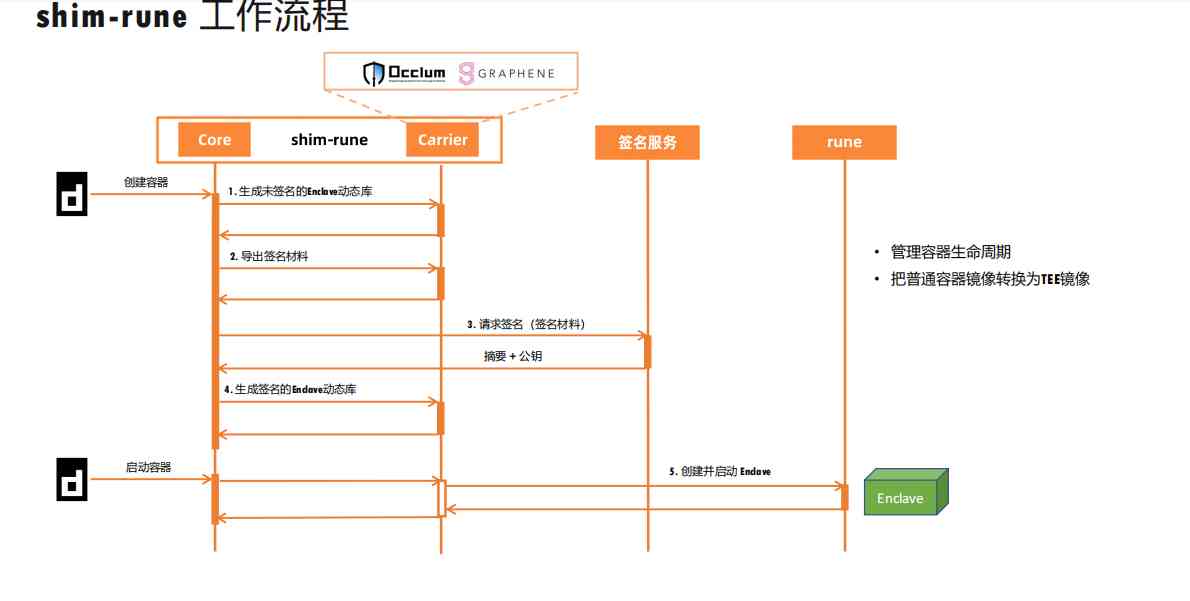
2.4 Client side signature and server side signature 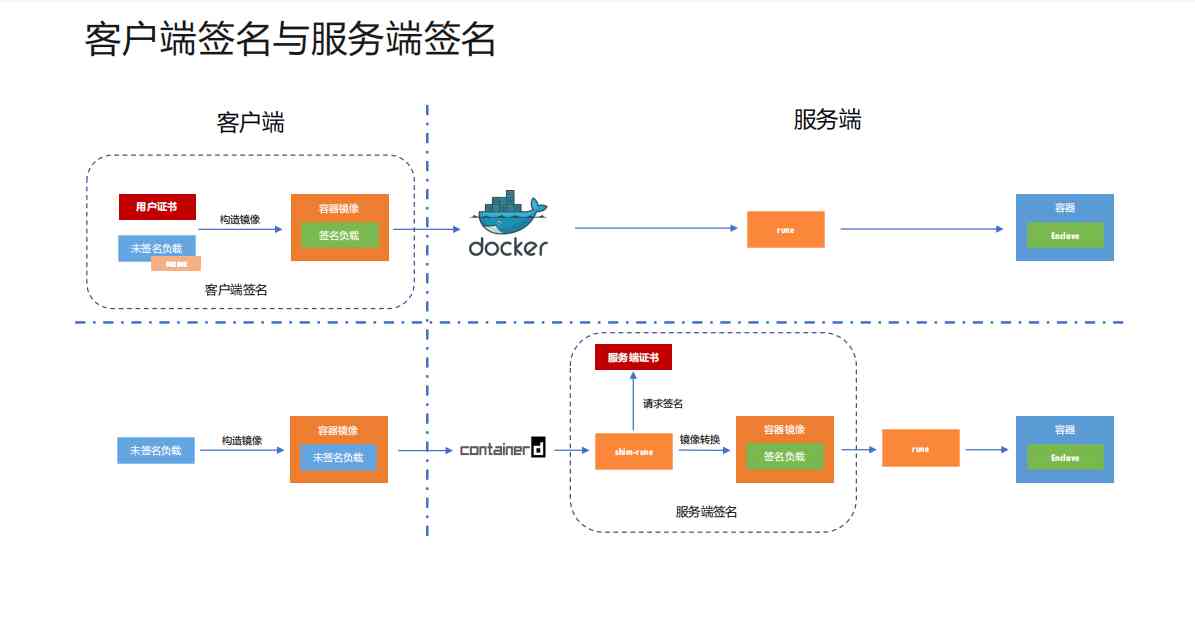
2.5 Multi team cooperation 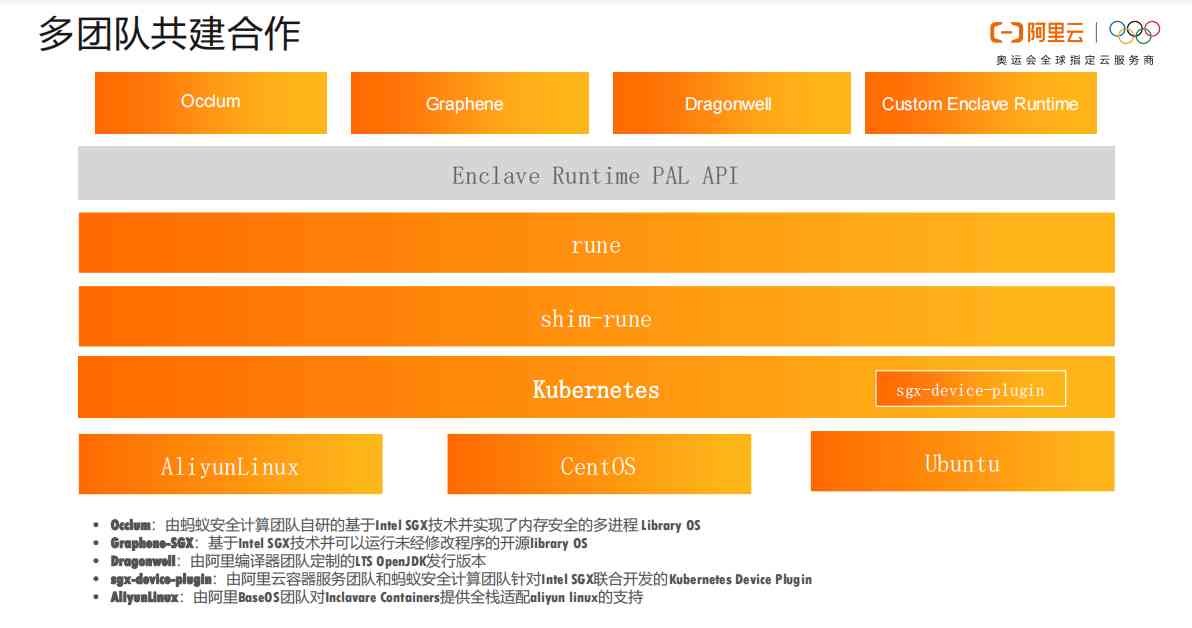
2.6 Inclavare Containers Open source project 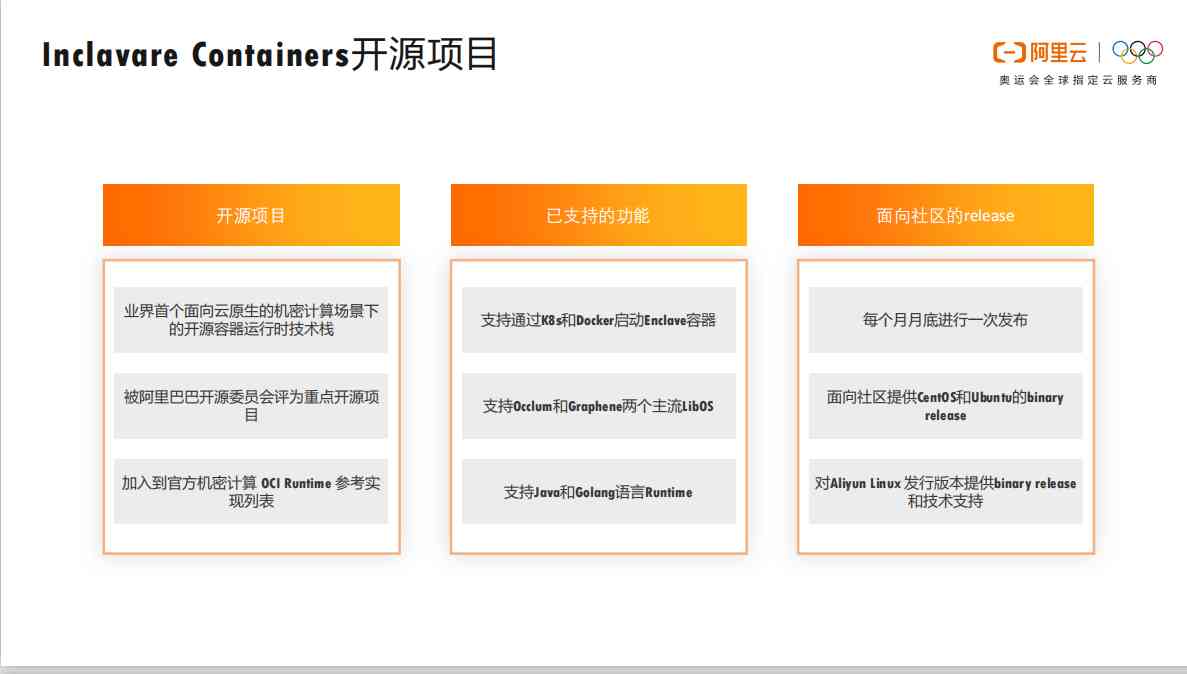
2.7 Inclavare Containers Milepost 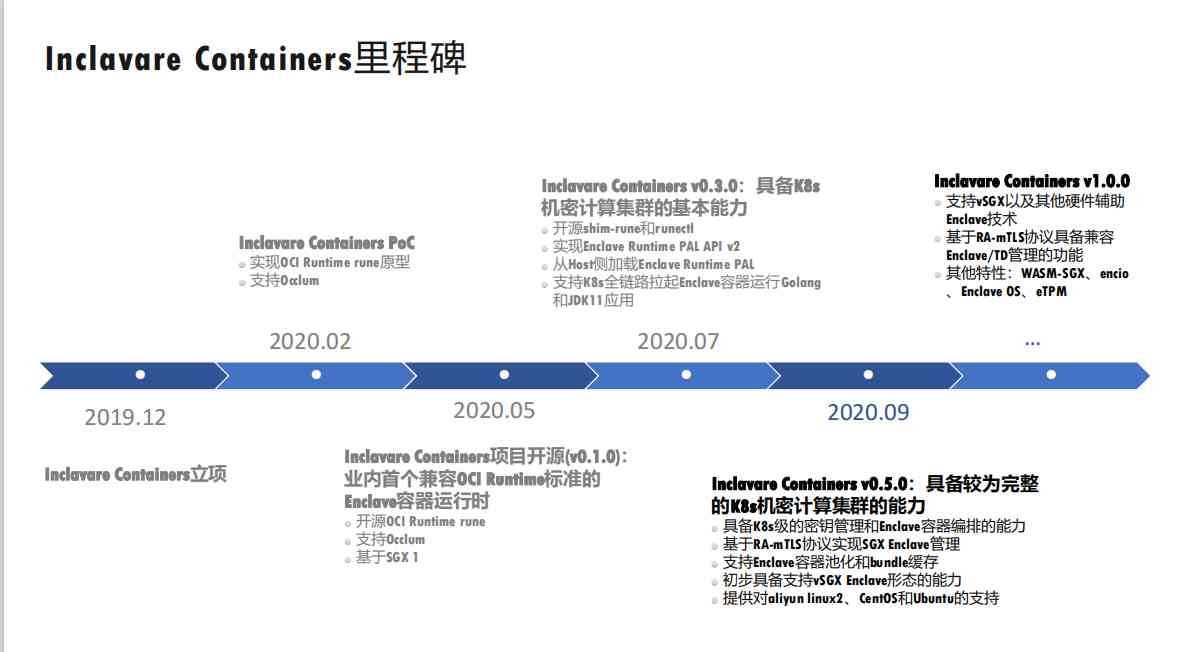
2.8 2020 Secret computing technology industry 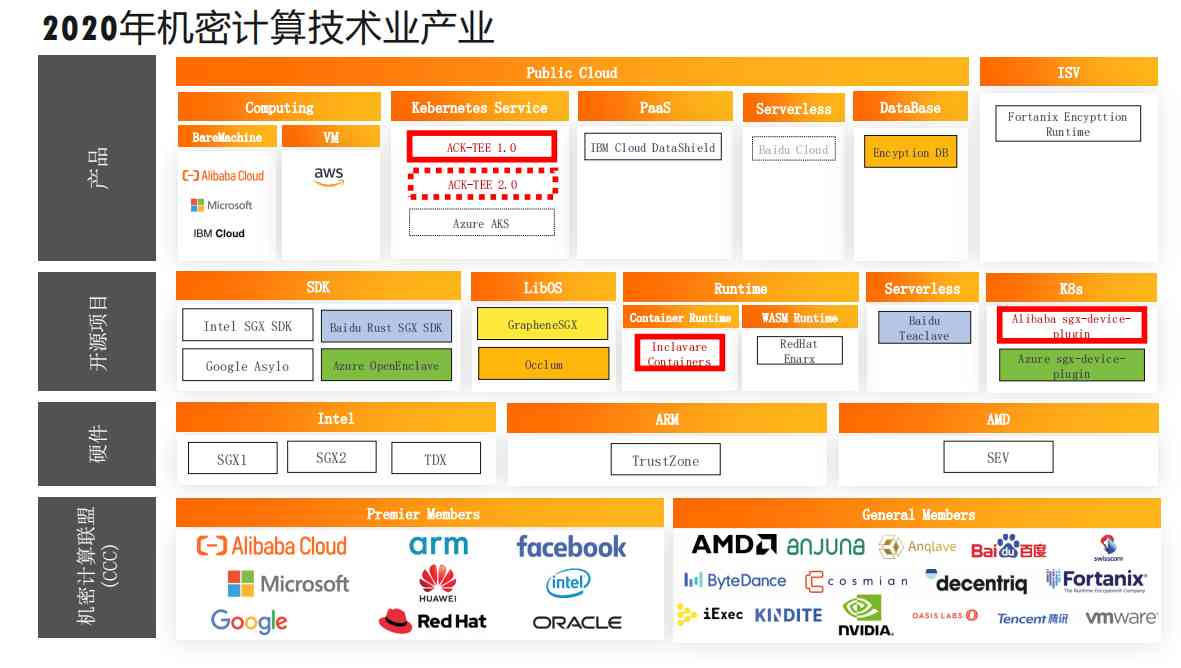
- ACK-TEE
3.1 ACK-TEE brief introduction 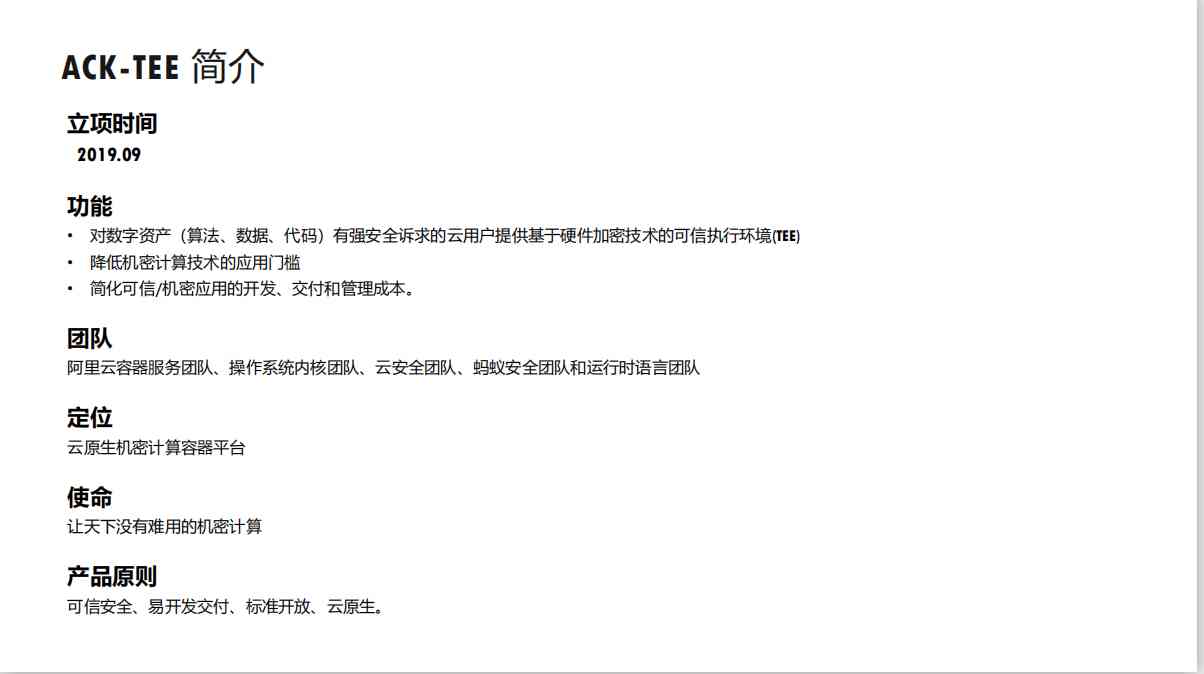
3.2 ACK-TEE 1.0 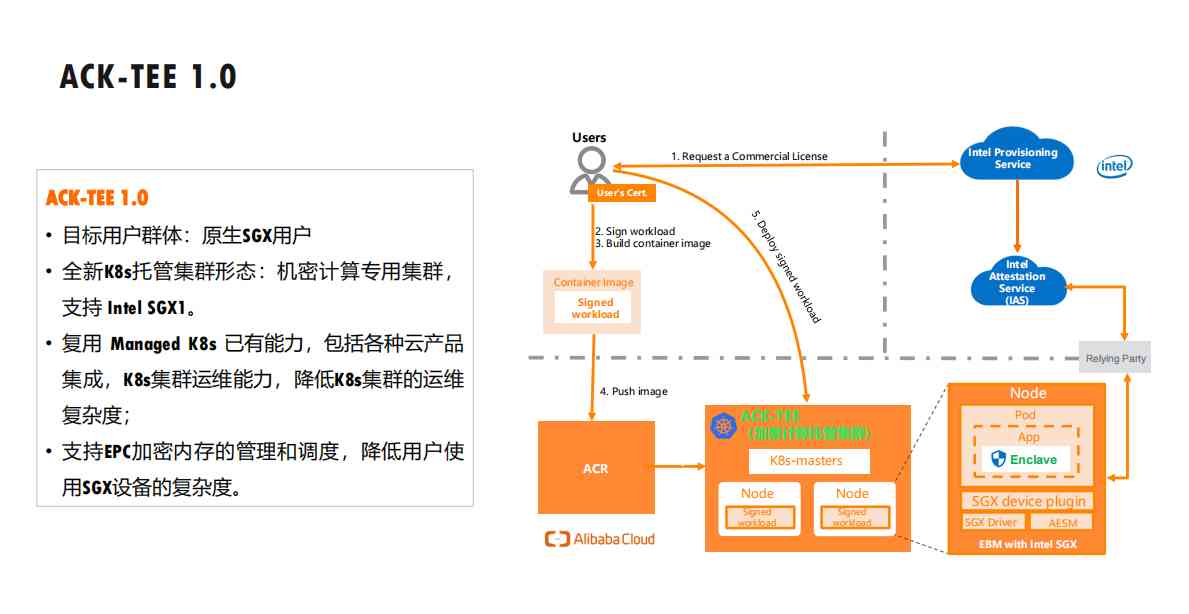
3.3 ACK-TEE 2.0 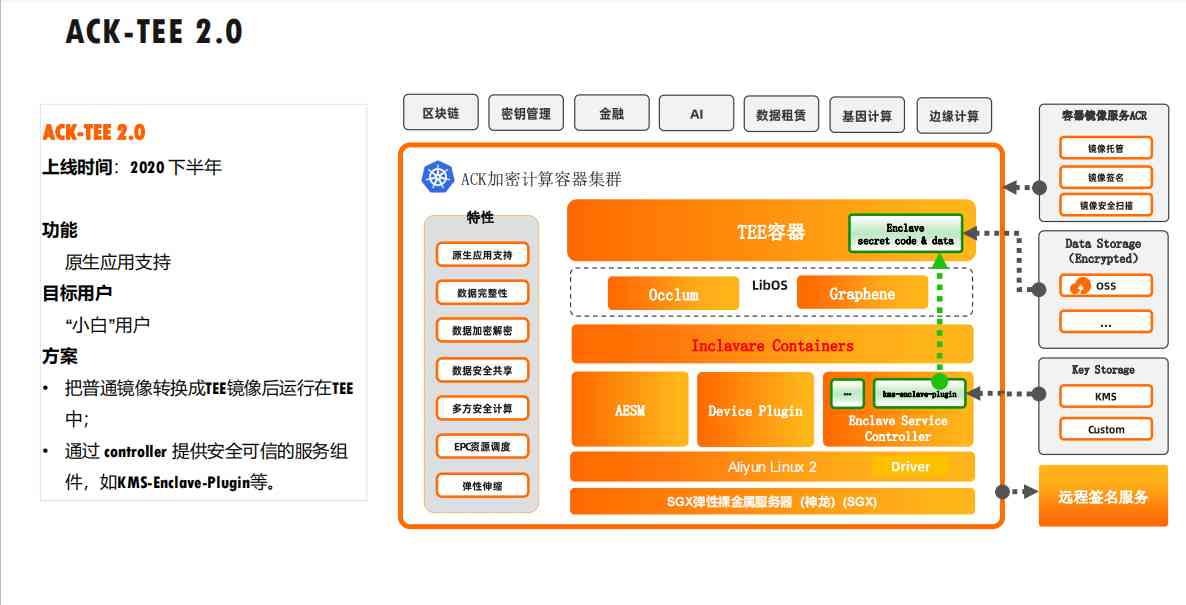
Click on the link to get the full document link :https://pan.baidu.com/s/112GDueQO4SRsXM7VpnDckQ Extraction code :ejaq
※ Part of the article comes from the Internet , If there is infringement, please contact to delete ; More articles and materials | Click on the text directly after ↓↓↓ 100GPython Self study Kit Alibaba cloud K8s Actual combat manual [ Alibaba cloud CDN Pit guide ]CDN ECS Operation and maintenance guide DevOps Practice Manual Hadoop Big data combat manual Knative Cloud native application development guide OSS Operation and maintenance manual White paper on cloud native architecture Zabbix Enterprise level distributed monitoring system source document 10G The interview questions of large factories are marked with
版权声明
本文为[Programmer interview]所创,转载请带上原文链接,感谢
边栏推荐
- Written interview questions: find the smallest positive integer missing
- 年轻一代 winner 的程序人生,改变世界的起点藏在身边
- YGC troubleshooting, let me rise again!
- 阿里教你深入浅出玩转物联网平台!(附网盘链接)
- 我们采访了阿里云云数据库SQL Server的产品经理,他说了解这四个问题就可以了...
- That's what software testing is all about?!
- YGC问题排查,又让我涨姿势了!
- Solve Safari browser download file name garbled problem
- Which is more worth starting with the difference between vivos7e and vivos7
- Basic concepts of computer network (5) basic principles of local area network
猜你喜欢
Flink's sink: a preliminary study
为 Docsify 自动生成 RSS 订阅

函数周期表丨筛选丨值丨SELECTEDVALUE - 知乎
Introduction to mongodb foundation of distributed document storage database

Personal current technology stack

狗狗也能操作无人机!你没看错,不过这其实是架自动驾驶无人机 - 知乎

个人目前技术栈

i5 1135g7和i5 1035g1参数对比区别大吗? 哪个好

计算机网络基本概念(五)局域网基本原理

Win10 terminal + WSL 2 installation and configuration guide, exquisite development experience
随机推荐
仅用六种字符来完成Hello World,你能做到吗?
211考研失败后,熬夜了两个月拿下字节offer!【面经分享】
Is there a big difference between i5 1135g7 and i51035g1? Which is better?
阿里出品!视觉计算开发者系列手册(附网盘链接)
Recommend an economic science video, very valuable!
vivoY73s和vivoY70s的区别 vivoY73s和vivoY70s哪个值得入手
print( 'Hello,NumPy!' )
IQKeyboardManager 源代码看看
临近双11,恶补了两个月成功拿下大厂offer,跳槽到阿里巴巴
Win10 Terminal + WSL 2 安装配置指南,精致开发体验
游戏优化性能杂谈(十一) - 知乎
Tiktok live monitoring Api: random recommendation
Tidb performance competition 11.02-11.06
阿里教你深入浅出玩转物联网平台!(附网盘链接)
[data structure Python description] use hash table to manually implement a dictionary class based on Python interpreter
入门级!教你小程序开发不求人(附网盘链接)
我们采访了阿里云云数据库SQL Server的产品经理,他说了解这四个问题就可以了...
Where is the new target market? What is the anchored product? |Ten questions 2021 Chinese enterprise service
为 Docsify 自动生成 RSS 订阅
Px4 adds new applications