当前位置:网站首页>Oops, the system is under attack again
Oops, the system is under attack again
2020-11-08 08:54:00 【Total cost】
A few years ago , Our e-commerce platform encountered once CC attack ( A distributed network attack , More on that later ), At that time, the whole website was almost paralyzed . There was a lot of PC Web pages and APP The page does not open or continues to report errors , The order process is completely out of order .
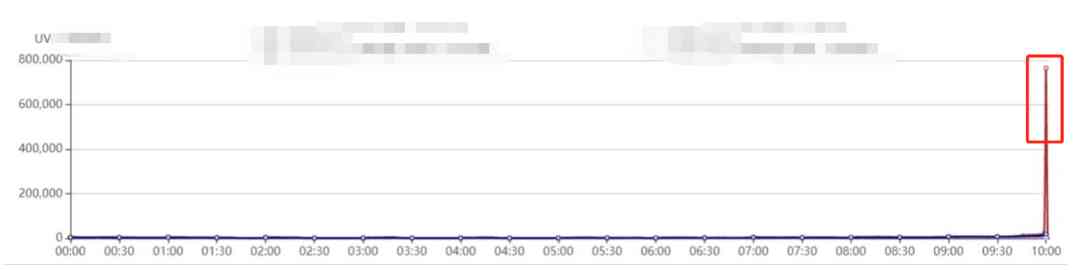
The above picture shows the monitoring of website traffic . We can see 10:00 when UV( Access users ) and client IP There's a sudden surge in numbers , Thousands of times more .
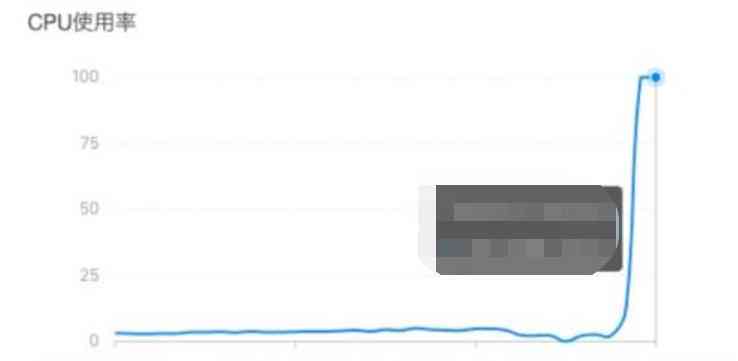
From the background monitoring ( Upper figure ),CPU The resources have been exhausted . because CPU Exhausted , The server is extremely slow , So I couldn't log in to the server at that time CPU Detailed usage , It can only be viewed according to the monitoring page CPU usage .
in addition , The export bandwidth is full . So during that time, many requests couldn't come in at all . What users see is a blank page , Request error, etc .
Through the analysis of , We found out that this attack was triggered by the launch of the limited launch of new products , It's a collection of wool . The attacker has launched a distributed network attack on a limited number of new products , The purpose is to seize Limited new products , Let's sell it at a high price in the market .
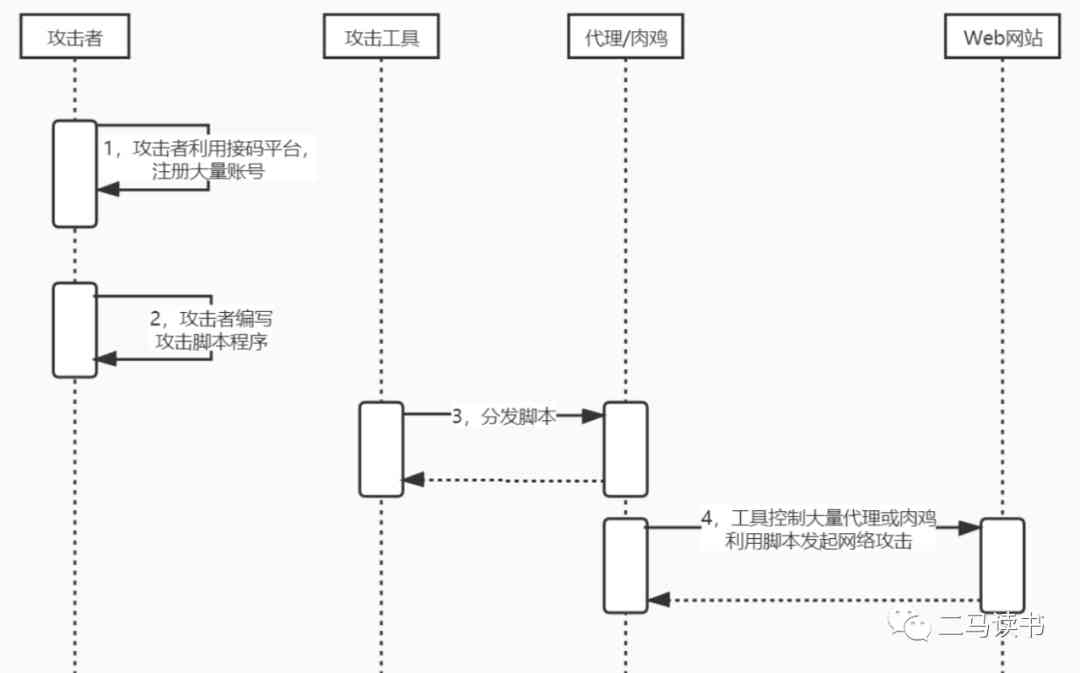
Attackers use the access platform ( Docking station , Generally speaking, it is the platform for receiving mobile phone verification code ) Register a large number of accounts in advance . Then prepare the script in advance , Use some attack tools ( There is a list of tools at the end of the article ) Distribute these scripts to a large number of agents or broilers , And through these agents and broilers to launch distributed attacks on the website . The attack steps are shown in the figure below :
Let's take a closer look at CC attack . understand CC Before we attack, let's clarify the following concepts .
Zombie hosts & Botnet
Botnet is a botnet virus , Computer equipment controlled by hackers . The computer device may be a terminal device , It can also be a cloud device , For example, a personal computer , mobile phone , Cloud hosts, etc . In general , Botnets have been manipulated and formed a botnet with other botnets . for example , A man illegally controls 10000 Computers , He can schedule this at the same time 10000 A computer launched a cyber attack , Then any one of them can be called a botnet , And this 10000 One computer makes up a botnet ( In fact, each computer is installed with a zombie client program ). Usually , A stolen computer is just one of the many botnets in the botnet , Zombies run silently in the background . It's hard for ordinary computer owners to notice that their systems have been “ Zombies ”, It's like a zombie without self-consciousness . The mobile computer you're using looks normal on the surface , It could also be a member of an infected zombie program .
chicken
Broiler refers to all those computer equipment controlled by others ( Computers and mobile phones, etc ), Whether it belongs to a botnet or not , Whether it is uniformly scheduled . Once the computer equipment is controlled by others , It's like meat on someone else's chopping board , People eat what they want , chicken ( machine ) One comes from this , Also known as the puppet machine . Of course, after installing the zombie on the broiler , It becomes a zombie host , That's what we call zombie computers , And become a member of the botnet .
DDos attack
DDos, Full name Distributed Denial of Service, Chinese means “ Distributed denial of service ”, It is to use a large number of legitimate distributed computer devices to target servers ( Website, etc ) Send a request , Causes the target server to CPU、 Memory 、 Bandwidth and other resources are exhausted , As a result, normal users cannot access the target server . Generally speaking, it is the use of network node resources , Such as :IDC The server 、 personal PC、 mobile phone 、 Smart devices 、 The printer 、 The camera and so on launch a large number of attack requests on the target , This leads to server congestion , And then they can't provide normal services to the outside world .

CC attack
CC attack (Challenge Collapsar). Its predecessor is Fatboy attack .Collapsar( Black holes ) Is a green alliance technology against DDOS product , It has high influence and reputation in the field of anti denial of service attacks . therefore , Hackers renamed the attack Challenge Collapsar, To challenge a black hole .
CC The attack was DDOS( Distributed denial of service ) A kind of , Is a common method of website attack , The attacker can access the victim through proxy server or broiler , Cause server memory or CPU When resources are exhausted or bandwidth resources are exhausted , Until the site is not accessible .
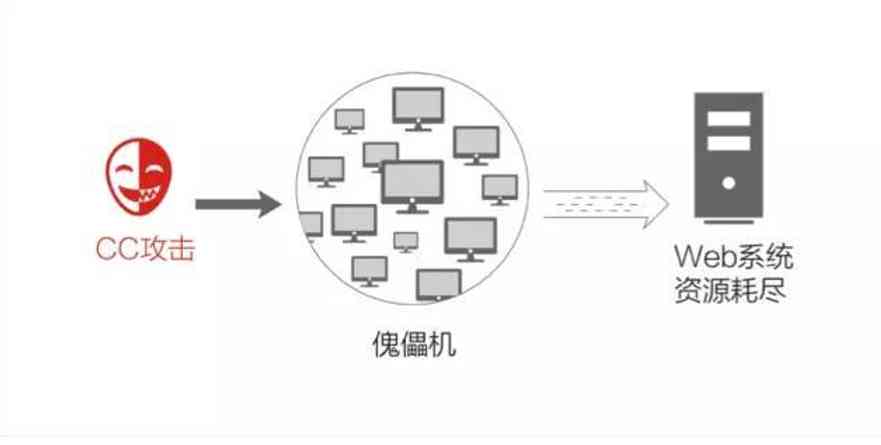
because CC The attack's access traffic comes from thousands of , Hundreds of thousands of , Even millions of computers , mobile phone , Virtual machine and other clients . It's almost the same as normal user access , These attack requests don't have obvious characteristics , It's hard to distinguish it from normal access , It's also very difficult to defend . In particular, using a botnet composed of broilers to launch attacks , There are tens of thousands of machines ( Many of these machines may be computers and mobile phones used by ordinary users ), This attack request is very similar to a normal user request , Defense is more difficult .
Slow attack --CC The variation of attack
The basic principle of slow attack is as follows : Open to any one HTTP Access to the HTTP The server , First, a connection is established , Specify a larger Content-length, And then contract at a very low rate , such as 1-10s Send a byte , Then keep the connection open . If the client continues to establish such a connection , Then the available connections on the server will be filled little by little , This leads to a denial of service .
HTTP The protocol is receiving request The request content is not verified before , So even if your Web No apps are available form Forms , This attack is just as effective .
Establish a large number of useless connections on the client side , And keep the cost of continuous contracting very low . In the actual experiment, a common PC The connections that can be made are in 3000 More than . This is for an ordinary Web The server , It's going to be a fatal blow . Not to mention the distributed attack combined with broilers .
Because it's easy to use , The cost is low , An obvious feature , Slow attack has become the research and utilization object of many attackers .
To this day , It has evolved into a variety of slow attacks , The typical ones are as follows :
Slow headers:Web Apply to deal with HTTP You have to receive everything before you ask HTTP Head , because HTTP The head contains some Web Important information that the application may use . Attackers take advantage of this , To launch a HTTP request , It's been sending HTTP Head , Consumes connection and memory resources of the server . Attack client and server establishment TCP After connection , Every time 10 Seconds before sending a message to the server HTTP Head , and Web The server didn't receive any more 2 A continuous \r\n when , Will think that the client did not send the header , And continue to wait for the client to send data .
Here's how to use slowhttptest Tool initiated slow header attack :
slowhttptest -H -c 1000 -l 300 -u http://192.168.2.16/test/
Mon May 21 02:03:49 2018:
slowhttptest version 1.7
- https://code.google.com/p/slowhttptest/ -
test type: SLOW HEADERS
number of connections: 1000
URL: http://192.168.2.16/test/
verb: GET
Content-Length header value: 4096
follow up data max size: 68
interval between follow up data: 10 seconds
connections per seconds: 50
probe connection timeout: 5 seconds
test duration: 300 seconds
using proxy: no proxy
Mon May 21 02:03:49 2018:
slow HTTP test status on 45th second:
initializing: 0
pending: 426
connected: 407
error: 0
closed: 167
service available: NO
Slowhttptest The request sent
GET /DVWA/ HTTP/1.1
Host: 192.168.2.16
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; Trident/4.0; SLCC2)
Referer: TESTING_PURPOSES_ONLY
X-aK1: sjqQ4Z
X-4: S
X-OWw: H
X-Dptasviz5: Q
...X-headers...
The number of server connections changes
# Before the client attacks , Number of server connections
root@server2:~# netstat -na|grep -i 80|wc -l
47
# In the process of the client launching the attack , Number of server connections
root@server2:~# netstat -na|grep -i 80|wc -l
461
root@server2:~# netstat -na|grep -i 80|wc -l
706
Slow body: The attacker sent a HTTP POST request , The requested Content-Length The head is worth a lot , bring Web The server or agent thinks the client is sending a lot of data . The server will remain connected and ready to receive data , But the attack client only sends a small amount of data at a time , Keep the connection alive , Consumes connection and memory resources of the server . Attack client and server establishment TCP After connection , Sent the complete HTTP Head ,POST Method with larger Content-Length, Then each 10s Send a random parameter . The server did not receive the corresponding Content-Length Of body, And continue to wait for the client to send data .
Slow read: The client establishes a connection with the server and sends HTTP request , The client sends the complete request to the server , And then keep this connection all the time , Read at a very low speed Response, For example, for a long time, the client does not read any data , By sending Zero Window To the server , Make the server think the client is busy , Read a byte until the connection is about to time out , To consume server connections and memory resources .
notes :TCP By sliding the window (Window) The concept of flow control . Imagine sending data at a high rate on the sending side and receiving it at a low rate on the receiving side , In order to ensure that the data is not lost , Flow control is clearly needed , Coordinate the working rhythm of both sides of communication . So called sliding window , Can be understood as the size of the buffer that the receiver can provide . seeing the name of a thing one thinks of its function ,Zero Window, Zero window , That is, when the sending speed of the sender is greater than the processing speed of the receiver , When the receiver's buffer is full , The sender will be informed of the current window size=0, The sender will immediately stop sending data .
Slow attack mainly uses thread-based( Based on threads ) Features of the server of the architecture , This server will open a thread for each new connection , It will wait to receive the complete HTTP The head will release the connection . such as Apache There will be a timeout to wait for this incomplete connection ( The default is 300s), But once the data from the client is received , This timeout will be reset . Because of this , Attackers can easily maintain a connection , Because the attacker only needs to send one character before the timeout , Then you can extend the timeout . The client only needs a few resources , You can open multiple connections , And then take up a lot of resources of the server .
Apache、httpd All use thread-based framework , Very vulnerable to slow attacks . And the other one event-based( Based on events ) Architecture server , such as nginx and lighttpd But not vulnerable to slow attacks .
How to defend against slow attacks ?
If the request exceeds the configured timeout or the transfer rate is below the minimum rate , Then it could be a slow attack . Can be configured to receive from the client HTTP Head and HTTP body Time out and minimum rate of , To avoid a long wait for a connection .
Count the number of messages periodically . One TCP Connect ,HTTP In the requested message , There are problems with too many messages or too few messages , If the number of messages in a cycle is very small , Then it could be a slow attack , You can ban it IP; If the number of messages in a cycle is very large , Then it could be a CC attack .
The most commonly used slow attack tools are :Slowhttptest and Slowloris.
CC etc. DDos The defense against an attack is as follows :
Press IP Current limiting
We can at the gateway layer (Apache,Nginx,Zuul etc. ), Yes IP Current limiting , Limit the number of interface accesses by minute level and second level dimension . When the number of visits exceeds the specified threshold, other requests are discarded . For those with too much traffic IP, Put it on the blacklist , Limit access to . The interception of malicious requests is pre processed to the gateway layer , Avoid a large number of malicious requests to the back-end service , Great pressure on Service .
Group deployment , According to the user flow limit
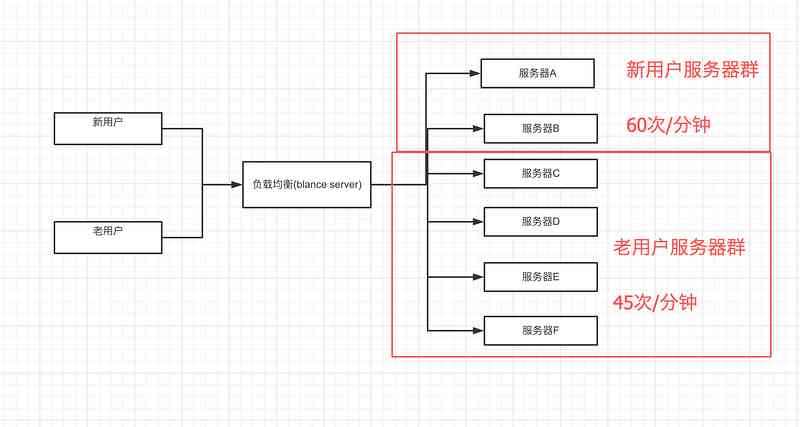
New and old users can be routed to different server groups . If new users suddenly soar , It's likely that there are a lot of registered accounts of broilers , These new user requests can be routed to a dedicated new user server group , Ensure that the server group where the old user is located will not be affected . After that, find out the abnormal users for blocking and blocking . You can also press USERID Limit the user's current , For example, the maximum number of requests per minute for new users is 60 Time / minute , Old users are 45 Time / minute . It can avoid sending a large number of requests to the back end in a short time .
Change the access port
In many cases ,Web Server adopt 80 The port provides external services , The attacker also attacks the corresponding port of the target site . After finding out that they were attacked , You can temporarily change the port to respond to an attack . But it's just a temporary strategy , An attacker with a little knowledge of the network will quickly discover the new interface , After changing the attack script, you can launch a new round of attack .
Buy advanced defense IP service
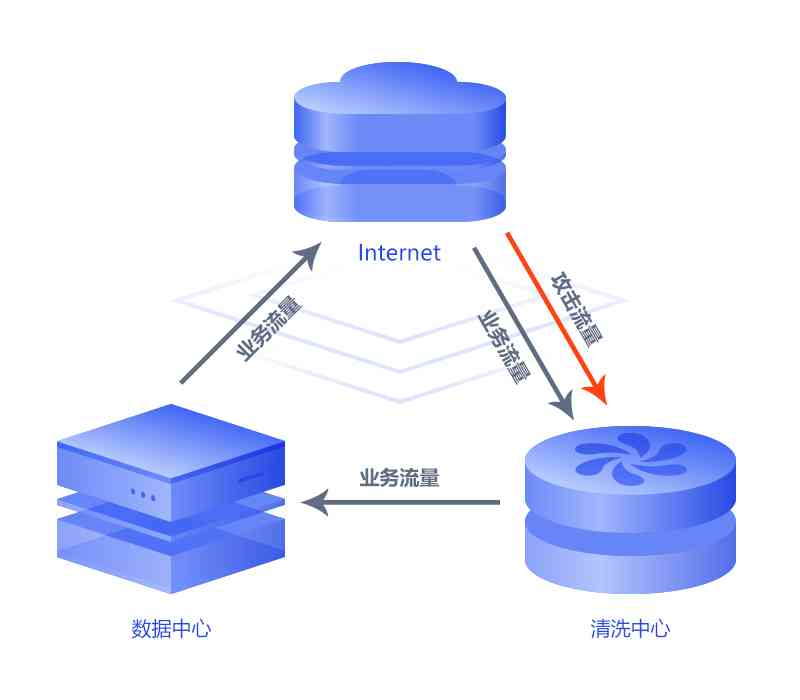
High imitation IP Service is the ultimate resistance D Plan . Companies can configure DDoS High prevention IP service , The domain name resolution of their own website points to the advanced defense IP, And configure the origin station IP. All public network traffic goes through advanced defense IP service , In high defense IP After cleaning and filtering, the normal traffic is forwarded to the source station IP, To ensure that the source station IP Stable access . in addition , High prevention IP Services tend to have huge bandwidth , General CC It's almost impossible for an attack to exhaust advanced defense IP The bandwidth resource of the service . High prevention IP The defense effect is very good , But the price is also more expensive . That's how we did it , Emergency procurement of advanced defense IP, And fast access to our website .

High prevention IP The service cleans the request in a variety of ways . such as , We will analyze the results based on big data , Forming various characteristics IP list . The attack tools are also identified according to the request characteristics .
Page static
Try to make the page static , Reduce access to back-end services . Static pages can take full advantage of the caching capabilities of client browsers and reverse proxies . It's ok CDN, use CDN Share most of the traffic . It can greatly reduce the probability of attack traffic reaching back-end services .
avoid IP leak
In order to reduce the DDos The possibility of attack , We need to hide the truth IP, This can make the attacker unable to find the target , So as to protect the website effectively . hide IP There are two main ways , utilize CDN Or advanced defense IP. Although many companies have access to CDN, But there's a lot to be aware of , If you don't pay attention, you will reveal the truth IP.
Try to avoid the real business host directly initiating external connection , Students who don't understand this sentence can think of the following scenes : User registration activation 、 You need to send an email to retrieve your password , If the business host goes directly through SMTP Way to send out email , Most of the time, email HEADER There will be truth in it IP.
Prevent secondary domain name IP leak . The main domain name is on CDN, If you manage the backstage admin The secondary domain name of has not passed through CDN, It can be easily resolved to the business host IP, It's also true IP. Email analysis MX, If it doesn't go through CDN, It will also reveal the truth IP.CDN If only domestic , You can use the foreign host PING Domain name to get real IP. There are a lot of things like that , To draw attention to .
notes :MX That's mail exchange records . Used to point the e-mail ending with the domain name to the corresponding mail server . For example, the email users use is domain name 163.com For the end , So in MX When you parse, you have to resolve to 163.com Corresponding server IP. If it doesn't go through CDN, It's easy to get the truth IP.
Finally, several distributed network attack tools are introduced :
LOIC:LOIC It's one that focuses on web Application's Dos/DDOS Attack tools , It can be used TCP Data packets 、UDP Data packets 、HTTP Request the target site to DDOS/DOS test , A bad person may take advantage of LOIC Building botnets .LOIC Yes, it is C# Written language , This is a C# Novice hands-on work , by GUI The interface attracted the use of little white people who did not know the truth . Because of the programming “ Intentionally or unintentionally ” Leave the BUG As a result, once the attack starts, the attack cannot be stopped before exiting the process , Potentially increases the attack effect . The main means of attack is to send a large amount of data in an infinite loop , There are no other features .LOIC The main interface of the program is as follows .
HULK:HULK It's a kind of web Denial of service attack tool for . It can be web A lot of single fake traffic is generated on the server , Can bypass the engine's cache , Therefore, it can directly attack the resource pool of the server .hulk What's special about : It's unique to every request , It can bypass the engine's cache and directly act on the server's load .
Darkddoser:Darkddoser Launched through botnets http attack , The graphic interface is as follows .
Slowhttptest:Slowhttptest Is a flexible configuration of the application layer attack tool , It can initiate things like slowloris、Slow http post、slow read、slow range Slow attack implemented by tools such as .
Zarp:Zarp Is to use Python Compiling 、 similar MSF A network attack testing framework for . The tools are modular in design , Set vulnerability scan 、 Sniffing 、DDoS Stress testing in one .Zarp The main interface is a CLI Driven graphical interface , Use a multi-layer menu , It's quite convenient to use .
At the end
In the game of attack and defense in the computer world , We as defenders , It's impossible to make the system impeccable , There are no security holes . What we can do is , Try to be comprehensive , Keep finding problems , Quickly fix known security issues . There is no absolutely safe system , There are no defenseless hackers . Only by constantly accumulating safety knowledge , Keeping the awareness of danger in times of safety can make us deal with cyber attacks calmly .
If you think the article is good , At the end of the article ???? It's back , Remember to give it to me 「 give the thumbs-up 」 and 「 Looking at 」 Oh ~
版权声明
本文为[Total cost]所创,转载请带上原文链接,感谢
边栏推荐
- Template linked list learning
- Cloud Alibabab笔记问世,全网详解仅此一份手慢无
- PCR and PTS calculation and inverse operation in TS stream
- 接口
- Solve the problem of rabbitmq message loss and repeated consumption
- Introduction to ucgui
- FORTRAN77从文件中读入若干数据并用heron迭代公式开方
- PerconaXtraDBCluster8.0 最详尽用法指南
- Swiper window width changes, page width height changes lead to automatic sliding solution
- NOIP 2012 提高组 复赛 第一天 第二题 国王游戏 game 数学推导 AC代码(高精度 低精度 乘 除 比较)+60代码(long long)+20分代码(全排列+深搜dfs)
猜你喜欢

Fgagt: flow guided adaptive graph tracking

将“光头”识别为“足球”,AI 摄像头如何犯的错?

VC6 compatibility and open file crash resolution

Python3.9的7个特性

Ulab 1.0.0 release

5g + Ar out of the circle, China Mobile Migu becomes the whole process strategic partner of the 33rd China Film Golden Rooster Award

Qt混合Python开发技术:Python介绍、混合过程和Demo

vivoy73s和荣耀30青春版的区别
技术人员该如何接手一个复杂的系统?

Littlest jupyterhub| 02 using nbgitpuller to distribute shared files
随机推荐
M-end software product design considerations - Zhihu
Deeplight Technology Bluetooth protocol SRRC certification services
5G+AR出圈,中国移动咪咕成第33届中国电影金鸡奖全程战略合作伙伴
Improvement of rate limit for laravel8 update
Visual studio 2015 unresponsive / stopped working problem resolution
Qt混合Python开发技术:Python介绍、混合过程和Demo
Solve the problem of rabbitmq message loss and repeated consumption
Experience the latest version of erofs on Ubuntu
Face recognition: attack types and anti spoofing techniques
GET,POST,PUT,DELETE,OPTIONS用法与说明
VC6兼容性及打开文件崩溃问题解决
Is blazor ready to serve the enterprise?
Do you really understand the high concurrency?
C / C + + Programming Notes: what are the advantages of C compared with other programming languages?
VC6 compatibility and open file crash resolution
Mate 40系列发布 搭载华为运动健康服务带来健康数字生活
The most detailed usage guide for perconaxtradbcluster8.0
Littlest JupyterHub| 02 使用nbgitpuller分发共享文件
[summary series] technical system of Internet server: high performance database index
软件测试就是这么回事?!