当前位置:网站首页>Face recognition: attack types and anti spoofing techniques
Face recognition: attack types and anti spoofing techniques
2020-11-08 07:14:00 【Artificial intelligence meets pioneer】
author |Trung Anh Dang compile |Flin source |towardsdatascience
Thanks to the rapid development of computer science and electronic technology , Now , In terms of market share , Face recognition is becoming the second largest biometric authentication method in the world after fingerprint .
Every day , More and more manufacturers are adding face recognition to their products , Apple, for example, uses face recognition technology , Banks use eKYC The solution goes through the induction process .
The main purpose of face recognition research is to improve the performance of verification and recognition tasks , On the contrary , In the past, there is little research on the security vulnerability of face recognition system , Until recent years , People are beginning to focus on different types of face recognition attacks , It includes testing whether a biometric comes from a living person or a photograph .
Two kinds of attacks used on face recognition systems
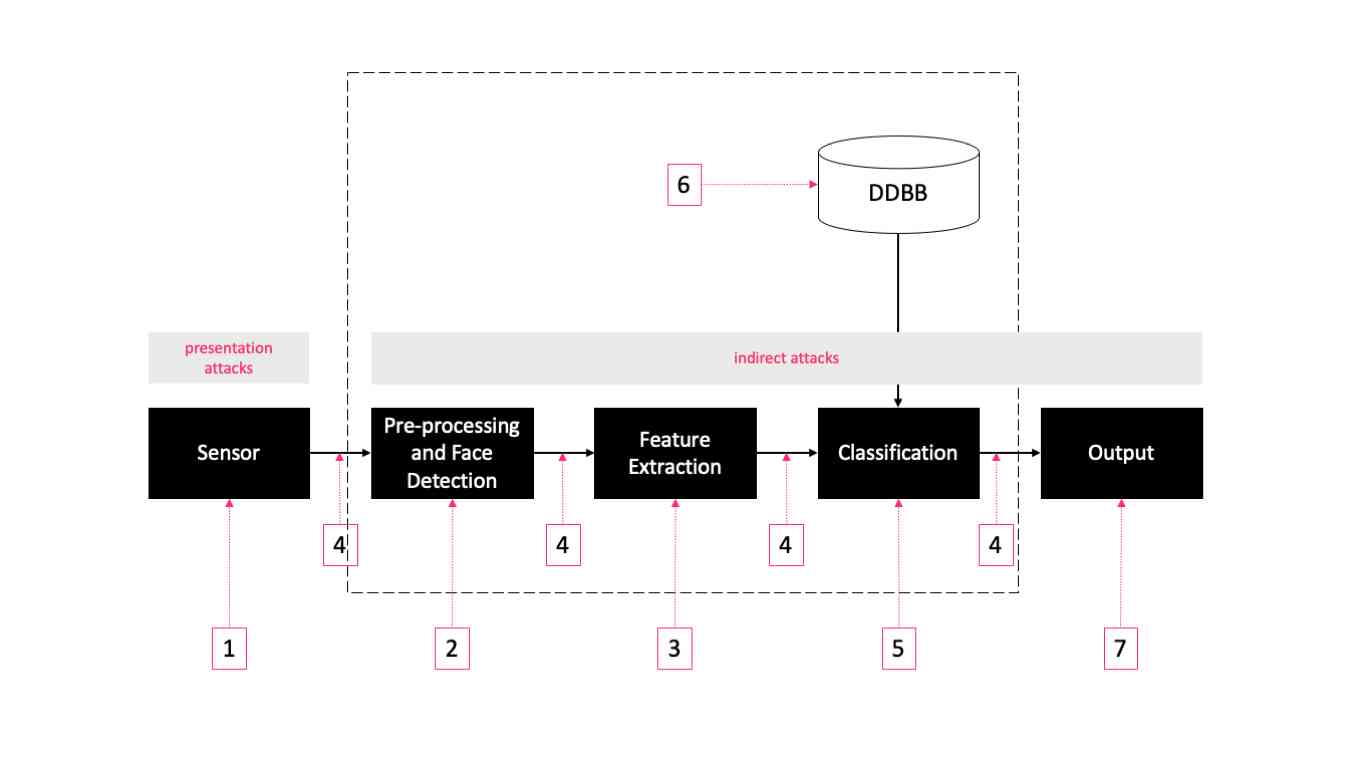
As shown in the figure above , There are seven modules and points that can be targeted , They fall into two types : Demonstrate attacks and indirect attacks .
Demonstrate the attack
Demonstrate the attack at the sensor level (1) Conduct , You don't have to access the system .
Demonstration attacks are related to purely biometric vulnerabilities . In these attacks , The intruder uses some kind of artifact , for example , Photo , Mask , Synthetic fingerprint or printed iris image , Or trying to mimic the behavior of real users ( For example, gait , Signature ) Fraudulent access to biometric systems .
because “ Biometrics are no secret ”, The attacker is aware of this reality , That is, it exposed a lot of biological characteristics data , It shows people's faces , eyes , Voice and behavior , So they use these information resources to try to trick the face recognition system with the following example .
-
The attacker uses the photo of the user to be impersonated .
-
They use user videos to mimic .
-
Hackers can build and use the 3D Model , for example , Super realistic mask
We use anti spoofing techniques to prevent these attacks .
Indirect attack
It can be in the database , Indirect attack on matched communication channels, etc (2-7). In this type of attack , The attacker needs to access the inside of the system .
It can be done through “ classic ” Technology related to network security ( Not with biometrics ) Related technology to prevent indirect attacks , So in this article we will not discuss .
Attack style
If you don't implement demo attack detection , Most of the latest facial biometric systems are vulnerable to simple attacks .
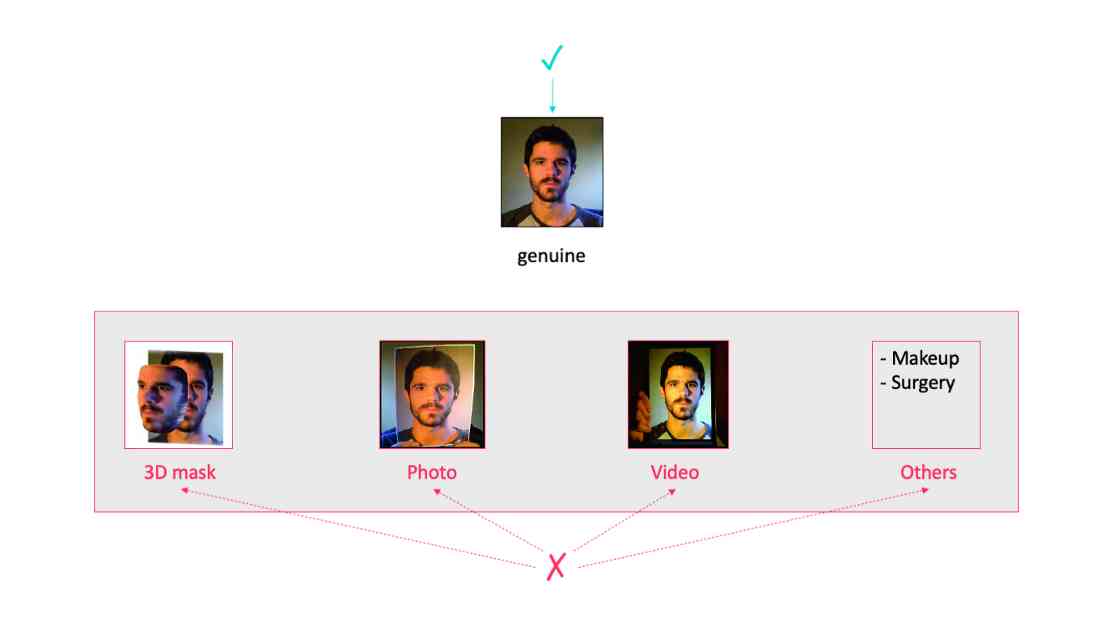
Usually , You can present a picture of the target person to the camera , Video or 3D Mask the face recognition system . Or make-up or plastic surgery . however , Due to the high exposure rate of high resolution digital camera 、 The cost is low , Using photos and videos is the most common type of attack .
-
Photo attack : Photo attacks include displaying photos of the attacked identity on the sensors of the face recognition system .
-
Video attack : An attacker can play a legitimate user's video on any device that copies the video , And then it's presented to the sensor / The camera .
-
3D Masked attack : In this type of attack , Attackers construct facial 3D Rebuild and present it to the sensor / The camera .
-
Other attacks : Make up , Operation
Anti spoofing technology
Because most face recognition systems are vulnerable to spoofing attacks . therefore , In order to design a secure face recognition system in real scenes , Start with the initial planning of the system , Anti spoofing technology should be the top priority .
Because facial recognition systems try to distinguish real users , Therefore, there is no need to determine whether the biometric sample provided to the sensor is true or false . We can achieve them in four different ways .
sensor
We use sensors to detect real-time features in the signal .
Special hardware
With dedicated hardware ( for example 3D The camera ) To detect signs of life , But it's not always possible to deploy .
Challenge response method
Use the challenge response method , The demonstration attack can be detected by asking the user to interact with the system in a specific way .
-
smile
-
Sad or happy facial expressions
-
Head movements
Algorithm
Using the following recognition algorithm has the ability to resist attacks in essence .
Mirror feature projection : First , By depicting the mirror feature space corresponding to the real image , On this basis, we learn the projection of real data and false data . secondly , Training according to real projection SVM Model , And then use 3D Mask projection and print photo projection are used as anti deception models for detection simulation .
Deep feature fusion : Through in-depth study of the importance of face image color feature information for face detection , Using deep convolution neural networks ResNet and SENet The network structure of deep feature fusion is constructed , Effectively train the relevant face anti deception data .
Image quality assessment : The method is based on the combination of image quality metrics . The solution compares the original image with the processed image .
Deep learning : This method is based on multi input architecture , The architecture combines a pre trained convolutional neural network model with a local binary pattern descriptor .
Biometric authentication methods https://towardsdatascience.com/biometric-authentication-methods-61c96666883a
How to implement ?
We can use anti spoofing technology to build demonstration attack detection system (PAD), And integrate it with the face recognition system .

Using this method , The anti spoofing system makes the decision first , Only after it's confirmed that the samples came from living people , The face recognition system will process it .
Link to the original text :https://towardsdatascience.com/facial-recognition-types-of-attacks-and-anti-spoofing-techniques-9d732080f91e
Welcome to join us AI Blog station : http://panchuang.net/
sklearn Machine learning Chinese official documents : http://sklearn123.com/
Welcome to pay attention to pan Chuang blog resource summary station : http://docs.panchuang.net/
版权声明
本文为[Artificial intelligence meets pioneer]所创,转载请带上原文链接,感谢
边栏推荐
- scala 中 Future 的简单使用
- WPF personal summary on drawing
- swiper 窗口宽度变化,页面宽度高度变化 导致自动滑动 解决方案
- Windows subsystem Ubuntu installation
- Speed up your website with jsdelivr
- A compilation bug brought by vs2015 Update1 update [existing solutions]
- Unparseable date: 'mon Aug 15 11:24:39 CST 2016', time format conversion exception
- 哔哩哔哩常用api
- 双向LSTM在时间序列异常值检测的应用
- Solve the problem of rabbitmq message loss and repeated consumption
猜你喜欢
面部识别:攻击类型和反欺骗技术

Learn Scala if Else statement

Got timeout reading communication packets解决方法
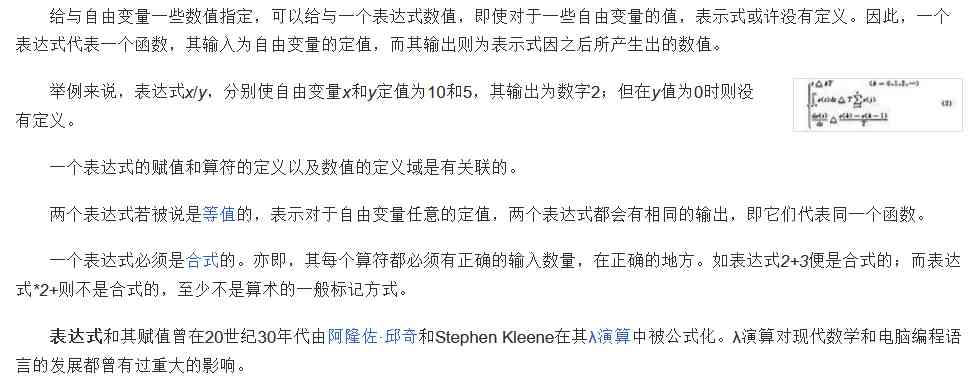
c# 表达式树(一)

Simple use of future in Scala
云计算之路-出海记:整一台 aws 免费云服务器

November 07, 2020: given an array of positive integers, the sum of two numbers equals N and must exist. How to find the two numbers with the smallest multiplication?

ubuntu实时显示cpu、内存占用率
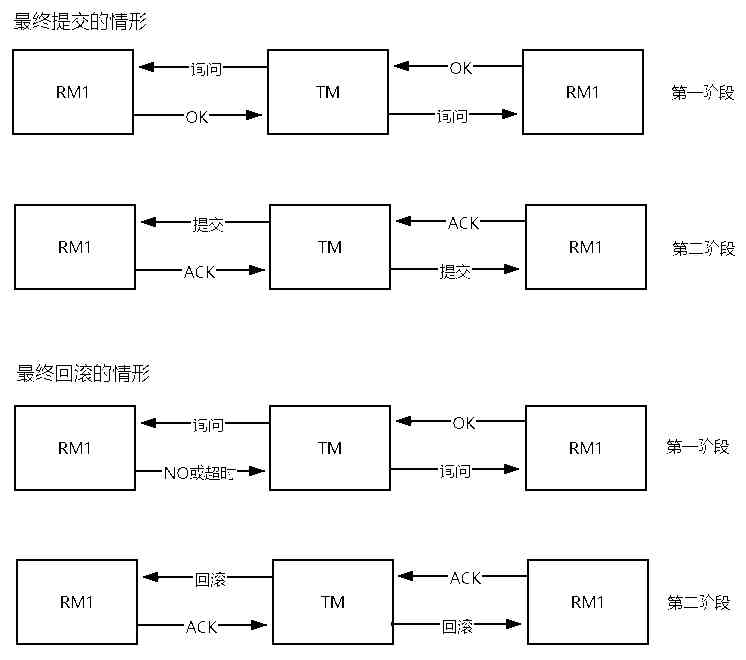
14000 word distributed transaction principle analysis, master all of them, are you afraid of being asked in the interview?
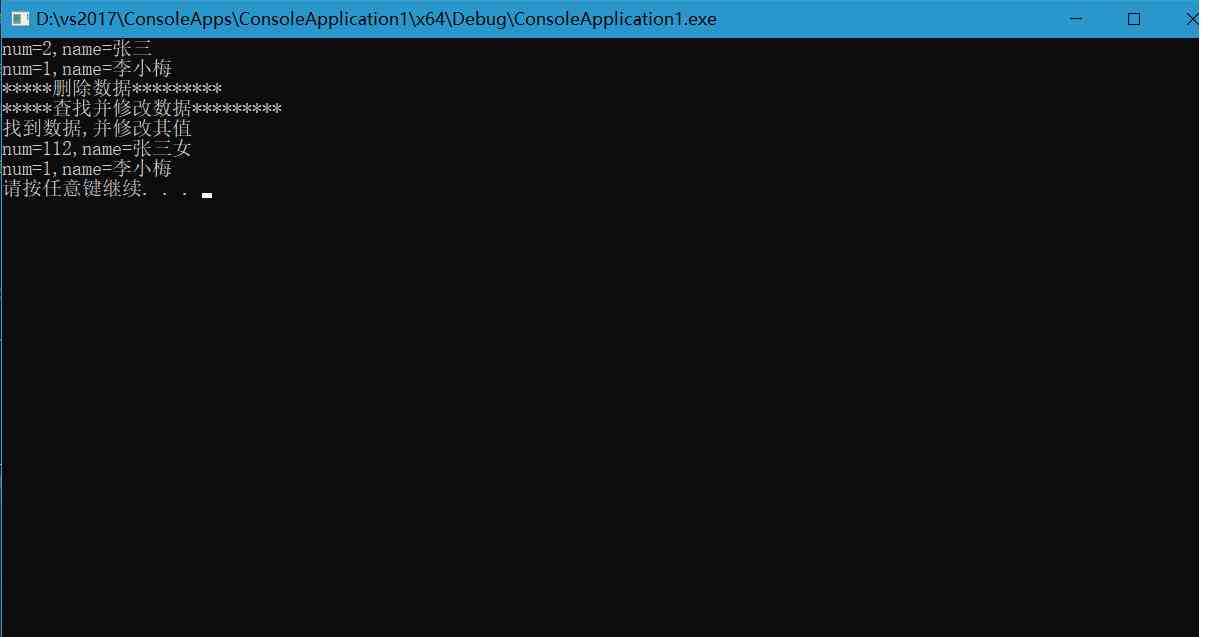
模板链表类学习
随机推荐
Blazor 准备好为企业服务了吗?
IOS learning note 2 [problems and solutions encountered during the installation and use of cocopods] [update 20160725]
A compilation bug brought by vs2015 Update1 update [existing solutions]
Bili Bili common API
Solve the problem of rabbitmq message loss and repeated consumption
Go之发送钉钉和邮箱
Basic operation of database
面部识别:攻击类型和反欺骗技术
Web Security (4) -- XSS attack
GET,POST,PUT,DELETE,OPTIONS用法与说明
麦格理银行借助DataStax Enterprise (DSE) 驱动数字化转型
Download, installation and configuration of Sogou input method in Ubuntu
Windows下子系统Ubuntu安装
个人短网址生成平台 自定义域名、开启防红、统计访问量
16. File transfer protocol, vsftpd service
Is blazor ready to serve the enterprise?
Distributed consensus mechanism
Data structure and sorting algorithm
Golang anonymous structure member, named structure member, inheritance, composition
CPP (4) boost installation and basic use for Mac