当前位置:网站首页>What is web penetration testing_ Infiltration practice
What is web penetration testing_ Infiltration practice
2022-07-06 23:59:00 【Java architects must see】
Learn a whole set of web Penetration test experiment is very helpful for future testing , So I write down the realization in the learning environment , Provide experience in testing the entire website .
Purpose : (1) Learn how hackers invade websites through vulnerabilities , And obtain server permissions ; (2) Learn the whole process of penetration testing principle : Hackers exploit the injection vulnerability of the website , Then get the administrator account and password to go into the background , Through database backup , Get webshell; Then the hacker logs in shell, adopt 2003 The right of the server exp Take down the permissions of the server .
1. Check website security
Enter the test website http://192.168.1.3 Interface
Looking for loopholes , Let's scan with software first , Then find the link to test , Open in browser http://192.168.1.3/see.asp?ID=461&titleID=86 This link
Add ‘ , Page error reporting
It can be seen from the above figure that the database error interface is directly prompted , Judge that there may be injection vulnerabilities . We type in the browser http://192.168.1.3/see.asp?ID=461&titleID=86 and 1=
Let's enter in the browser http://192.168.1.3/see.asp?ID=461&titleID=86 and 1=2
Return to error page , Enter at the end of the link and 1=1 and and 1=2 Returning to the page is different , From this we can judge the existence of this site SQL Inject holes .
2. Use the tool to activate the successful tutorial administrator user 、 password
Open it D Injection tool
Put the existing injection point URL Copy to D In the injection tool , Choose the one on the left SQL Injection detection , Click detection , At the bottom of the database, we will be prompted about the type of database
Click the detection table segment , It is to detect all table names in the database
We click admin surface , Then click the detection field
choice password and admin Field , Then click the detection content , If the field content is exposed, the user name and password of the successful tutorial will be activated
3. Use the tool to activate the successful tutorial MD5 password
The password we got is MD5 Encrypted , We go through MD5 Activate the success tutorial software to activate the success tutorial
thus , We get the account password of the website administrator as linhai 123456
4. Log in to the website management background
We use software to detect the background of website management , Open Yujian background scanning tool
Put the website URL http://192.168.1.3 Input in the tool , Click to start scanning
Through the scanning results , We guess that the background login URL by http://192.168.1.3/admin/Login.asp
Use the administrator account to activate the successful tutorial linhai And password 123456 Successfully logged into the background
5. Get the website webshell
We enter the website management background , We need to get webshell, In this example, open system management first , Choose article management , Open the upload map
We upload directly asp Try the Trojan horse
We changed the suffix of the Trojan horse to mm.jpg
After successful upload , Right click photo properties , Take a look at the location of its upload and record it ,http://192.168.1.3/admin/Upfiles/201873091139.jpg
After we upload successfully , Because what you upload is pictures , It cannot be parsed into Trojan script , It happens that our website has the function of backing up the database , We can backup data , Rename the script file , Enable it to be executed as a Trojan script . We click data management on the left , Choose backup / Recover database
In the backup database , After the database path , Fill in the address of the picture we just uploaded :../admin/Upfiles/201873091139.jpg; Fill in after the backup database path ../db/1.aspx. The purpose of this is to upload our jpg Suffix Trojan horse , Back up as aspx file , Make our Trojan horse run normally .
After we click backup , visit http://192.168.1.3/db/1.aspx It's our Trojan horse address , The password of the Trojan horse is 77169, thus , We got the website webshell
6. Get the server permissions
Get into webshell after , We need to implement dos Command to add an administrator . Click on webshell The upper command line , Enter the execute command mode
Trying to perform whoami command , Check our permissions
We found that network service jurisdiction , You cannot directly add an administrator account under this permission , When we add accounts , Echo is blank , Prove that we can't add users
Click port scan , Then click Scan , Found the system open 43958 port , namely server-u service
Click on SU Raise the right , stay cmdshell Enter command in net user aaa 123456 /add, Then click execute
stay cmdshell Enter command in net localgroup administrators aaa /add, Then click execute
stay cmdshell Enter command in net user, Then click execute , see aaa Whether the user is successfully added
stay cmdshell Enter command in net user aaa, Then click execute , see aaa The user belongs to administrators User group
Click Start -> function ->mstsc->192.168.1.3-> Enter account aaa And password 123456, Click login
That's the end of today's article , Thank you for reading ,Java Architects must see I wish you a promotion and a raise , Good luck every year .
边栏推荐
- 短链的设计
- Rider离线使用Nuget包的方法
- I've been laid off, and I'll lose money for everything. The days when I once made a monthly salary of 20000 are not coming back
- Wasserstein Slim GAIN with Gradient Penalty(WSGAIN-GP)介绍及代码实现——基于生成对抗网络的缺失数据填补
- Unity color palette | color palette | stepless color change function
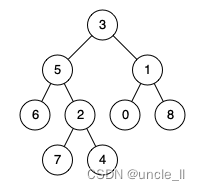
- leetcode:236. The nearest common ancestor of binary tree
- Oracle EMCC 13.5 environment in docker every minute
- Zero code and high return. How to use 40 sets of templates to meet 95% of the reporting needs in the work
- 1000字精选 —— 接口测试基础
- Pinia module division
猜你喜欢
rancher集成ldap,实现统一账号登录
Gradle知識概括
What is a responsive object? How to create a responsive object?
Matplotlib draws a histogram and adds values to the graph
leetcode:236. The nearest common ancestor of binary tree
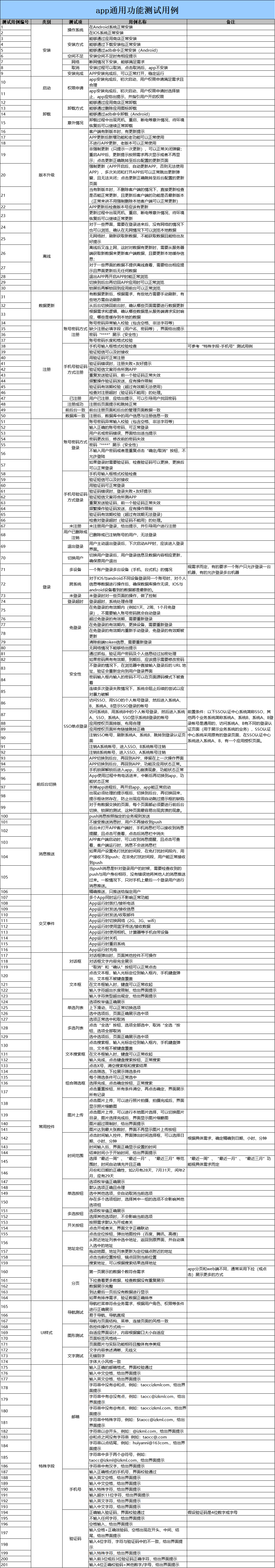
Cas d'essai fonctionnel universel de l'application
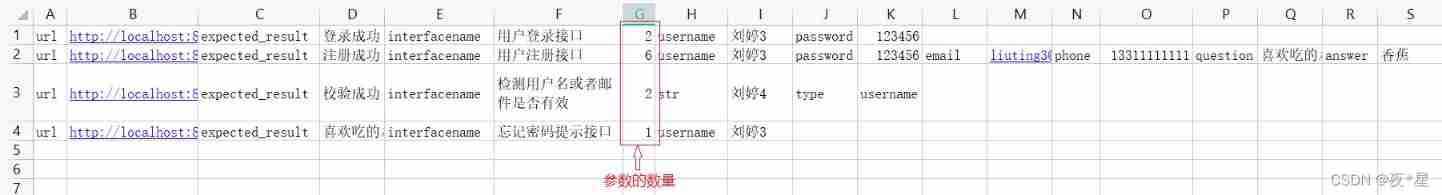
Interface joint debugging test script optimization v4.0
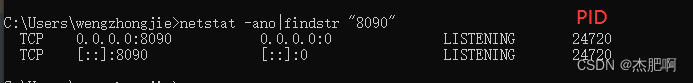
Close unregistering application XXX with Eureka with status down after Eureka client starts
内网穿透zerotier 外网(手机、电脑等)访问内网设备(树莓派、NAS、电脑等)

DAY SIX
随机推荐
GPIO简介
基于jsp+servlet+mysql框架的旅游管理系统【源码+数据库+报告】
谁说新消费品牌大溃败?背后有人赢麻了
leetcode:236. The nearest common ancestor of binary tree
web渗透测试是什么_渗透实战
Design a red envelope grabbing system
leetcode:236. 二叉树的最近公共祖先
PostgreSQL高可用之repmgr(1主2从+1witness)+Pgpool-II实现主从切换+读写分离
数据运营平台-数据采集[通俗易懂]
快讯 l Huobi Ventures与Genesis公链深入接洽中
There are only two TXT cells in the ArrayExpress database. Can you only download the sequencing run matrix from line to ENA?
How about the order management of okcc call center
DAY FOUR
【系统分析师之路】第七章 复盘系统设计(面向服务开发方法)
Unity 颜色板|调色板|无级变色功能
华为mate8电池价格_华为mate8换电池后充电巨慢
The largest single investment in the history of Dachen was IPO today
Asset security issues or constraints on the development of the encryption industry, risk control + compliance has become the key to breaking the platform
MATLIB从excel表中读取数据并画出函数图像
Supersocket 1.6 creates a simple socket server with message length in the header