当前位置:网站首页>1、 Go knowledge check and remedy + practical course notes youth training camp notes
1、 Go knowledge check and remedy + practical course notes youth training camp notes
2022-07-07 07:24:00 【A low-key horse】
Go Knowledge checking and filling + Practical course notes | Youth Camp notes
This is my participation 「 The third youth training camp - Back end field 」 The third part of note creation activities 1 Notes
It is divided into simple basic grammar to check and fill gaps and notes of the final practical project
Check for defects and make up for omissions :
Map:
map The assignment of is completely unordered , It has nothing to do with the content and order of insertion
Structure :
Pass in the structure pointer as a parameter in the method , It can be modified , In some cases, the overhead of copying structures can be avoided
string library :
a := "hello"
fmt.Println(strings.Contains(a, "ll")) // true
fmt.Println(strings.Count(a, "l")) // 2
fmt.Println(strings.HasPrefix(a, "he")) // true
fmt.Println(strings.HasSuffix(a, "llo")) // true
fmt.Println(strings.Index(a, "ll")) // 2
fmt.Println(strings.Join([]string{
"he", "llo"}, "-")) // he-llo
fmt.Println(strings.Repeat(a, 2)) // hellohello
fmt.Println(strings.Replace(a, "e", "E", -1)) // hEllo
fmt.Println(strings.Split("a-b-c", "-")) // [a b c]
fmt.Println(strings.ToLower(a)) // hello
fmt.Println(strings.ToUpper(a)) // HELLO
fmt package :
+v: Print out more details
fmt.Printf("p=%+v\n", p) // p={x:1 y:2}
#v: Print out more detailed content
fmt.Printf("p=%#v\n", p) // p=main.point{x:1, y:2}
JSON:
Serialize to a string :
a := userInfo{
Name: "wang", Age: 18, Hobby: []string{
"Golang", "TypeScript"}}
buf, err := json.Marshal(a)
if err != nil {
panic(err)
}
fmt.Println(buf) // [123 34 78 97...]
fmt.Println(string(buf)) // {"Name":"wang","age":18,"Hobby":["Golang","TypeScript"]}
Deserialize back to structure :
var b userInfo
err = json.Unmarshal(buf, &b)
if err != nil {
panic(err)
}
fmt.Printf("%#v\n", b) // main.userInfo{Name:"wang", Age:18, Hobby:[]string{"Golang", "TypeScript"}}
Get the timestamp :
now := time.Now()
fmt.Println(now.Unix()) // 1648738080
Type conversion :
This method always forgets
// String to number
n2, _ := strconv.Atoi("123")
// 123
// The number is converted to a string
strconv.Itoa(n2)
// "123"
rand random number
The corresponding random number seed is generated by the timestamp generated by the time the project is started each time :
maxNum := 100
rand.Seed(time.Now().UnixNano())
secretNumber := rand.Intn(maxNum)
The client parses the response
Convert a string into a stream
Because if you pass in a stream instead of a string , Prevent if the parameter file is large , It will waste a lot of time
client := &http.Client{
}
var data = strings.NewReader(`{"trans_type":"en2zh","source":"good"}`)
Add a blog you wrote before (golang Of Panic)
You can put panic Understand as a kind of try catch
Used only to catch fatal errors , It should not be used to report common errors : For example, when something should not happen happens , We should call panic( An array 、 Null pointer exception, etc )
When an exception occurs and is panic When capturing , The program will break , And then execute defer
stay go Language design , The function gets a multiple return value , Although very miscellaneous , Use... Every time if err != nil
however , Really catch exceptions and throw , It has to be used panic
The sample code
Practice notes :
SOCKS5 proxy server
SOCKS5 The protocol is a clear text transmission protocol , The purpose is to open a hole in the firewall , Let the authorized users have the ability to access the resources through a single port
Activation effect :
After starting the program ,
- Mode one : Configure and use this proxy in the browser , At this point, we open the web page , Proxy server logs , It will print out the domain name of the website you visit or IP, This shows that our network traffic is through this proxy server .
- Mode two : Test our proxy server on the command line . We can use
cur-soci5 + Proxy address , Followed by an accessible URL, If the proxy server works properly , that curt The command will return normally .
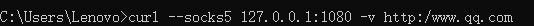
socks5 How the protocol works
Normal browser to visit a website , If you don't go through the proxy server , Will first establish with each other's website TCP Connect , Then shake hands three times . After shaking hands HTTP request , Then the service returns HTTP Respond to .
If you set up a proxy server , The process will become more complicated . The first is the browser and socks5 The agent establishes TCP Connect ,socks5 The agent then establishes with the real server TCP Connect . It can be divided into four stages , handshake phase 、 Authentication phase 、 Request stage 、relay Stage .
The first handshake stage , Liuziqi will socks5 Agent sends request , The content of the request package includes the version number of a protocol , There are also supported authentication types , socks5 Will choose an authentication method , Back to the browser . If you return 00 That means you don't need certification , If other types are returned, the authentication process will begin .
( The certification process :
First step , The browser will send a package to the proxy server , This package has three fields ; First field :version, That is, the protocol version number , Fixed is 5; Second field :methods, Number of certified methods ; Third field : Every method The coding ,0 Representatives don't need certification ,2 On behalf of user name and password authentication
here , The proxy server also needs to return a response, The return package includes two fields , One is version One is method, That is, the authentication method we selected , At present, we are only ready to implement the method without authentication , That is to say 0)
The third stage is the request stage , After authentication, the browser will towards socks5 Initiate request . The main information includes version number , Type of request , Generally, it's mainly connection request , Represents hope socks5 The server goes to a domain name or a IP Address a port to establish TCP Connect , After the proxy server receives the response , It will establish a connection with the back-end server , Then return the response .
The fourth stage is relay Stage , At this time, the browser will send a normal sending request , Then after the proxy server receives the request , It will directly convert the request to the real server . Then if the real server returns a response , The response will also be sent to the proxy server , The proxy server doesn't care about the details of sending traffic , It can be HTTP Traffic , It could be something else TCP Traffic .
Establish connection with back-end server , Then return the response .
The fourth stage is relay Stage , At this time, the browser will send a normal sending request , Then after the proxy server receives the request , It will directly convert the request to the real server . Then if the real server returns a response , The response will also be sent to the proxy server , The proxy server doesn't care about the details of sending traffic , It can be HTTP Traffic , It could be something else TCP Traffic .
边栏推荐
- C language (high-level) data storage + Practice
- Composition API premise
- Wechat applet full stack development practice Chapter 3 Introduction and use of APIs commonly used in wechat applet development -- 3.10 tabbar component (I) how to open and use the default tabbar comp
- Fullgc problem analysis and solution summary
- A slow SQL drags the whole system down
- 計算機服務中缺失MySQL服務
- freeswitch拨打分机号源代码跟踪
- LC interview question 02.07 Linked list intersection & lc142 Circular linked list II
- Reflection (II)
- 抽丝剥茧C语言(高阶)指针的进阶
猜你喜欢
Fast quantitative, abbkine protein quantitative kit BCA method is coming!
Esxi attaching mobile (Mechanical) hard disk detailed tutorial
Summary of customer value model (RFM) technology for data analysis
计算机服务中缺失MySQL服务
Lm11 reconstruction of K-line and construction of timing trading strategy
Kuboard can't send email and nail alarm problem is solved
main函数在import语句中的特殊行为
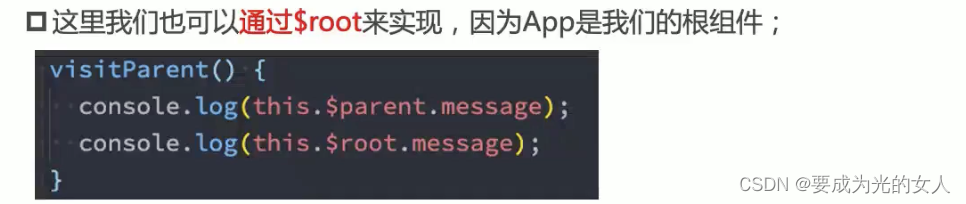
$parent (get parent component) and $root (get root component)

MySQL service is missing from computer service
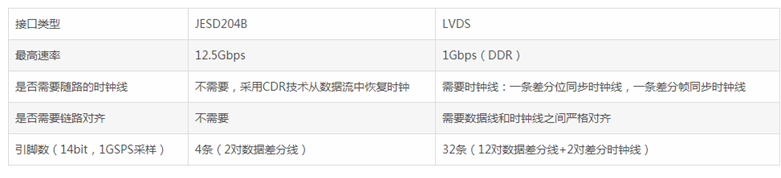
FPGA course: application scenario of jesd204b (dry goods sharing)
随机推荐
Esxi attaching mobile (Mechanical) hard disk detailed tutorial
Paranoid unqualified company
子组件传递给父组件
Test of transform parameters of impdp
Pass parent component to child component: props
Example of Pushlet using handle of Pushlet
Convolutional neural network -- understanding of pooling
toRefs API 与 toRef Api
Answer to the second stage of the assignment of "information security management and evaluation" of the higher vocational group of the 2018 Jiangsu Vocational College skills competition
Kuboard can't send email and nail alarm problem is solved
Pass child component to parent component
Advantages of using net core / why
Four goals for the construction of intelligent safety risk management and control platform for hazardous chemical enterprises in Chemical Industry Park
URP - shaders and materials - light shader lit
The currently released SKU (sales specification) information contains words that are suspected to have nothing to do with baby
FPGA course: application scenario of jesd204b (dry goods sharing)
Mobx knowledge point collection case (quick start)
【云原生】内存数据库如何发挥内存优势
ROS2规划系统plansys2简单的例子
Composition API 前提