当前位置:网站首页>misc ez_ usb
misc ez_ usb
2022-07-07 07:43:00 【[mzq]】
ez_usb
wireshark Open file
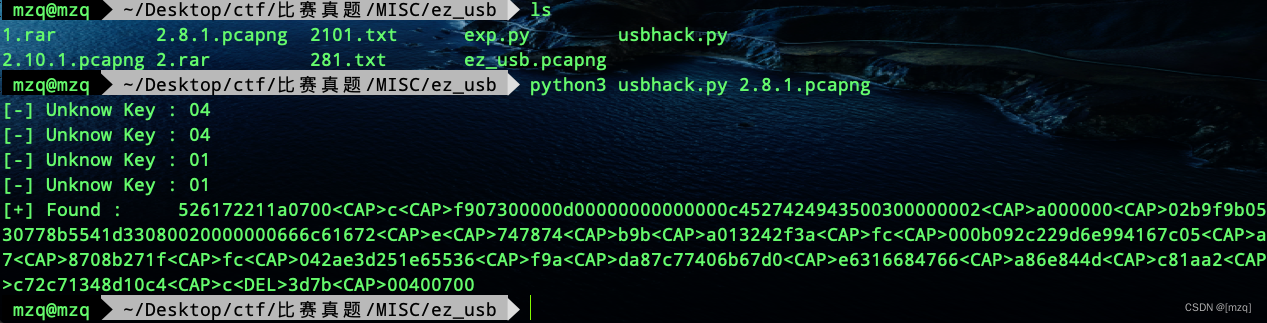
Found to be usb Traffic , The length is 8 Is keyboard traffic ,usbhack Extract the data , Found that the failure , go back to wireshark It is found that there are two versions of traffic .
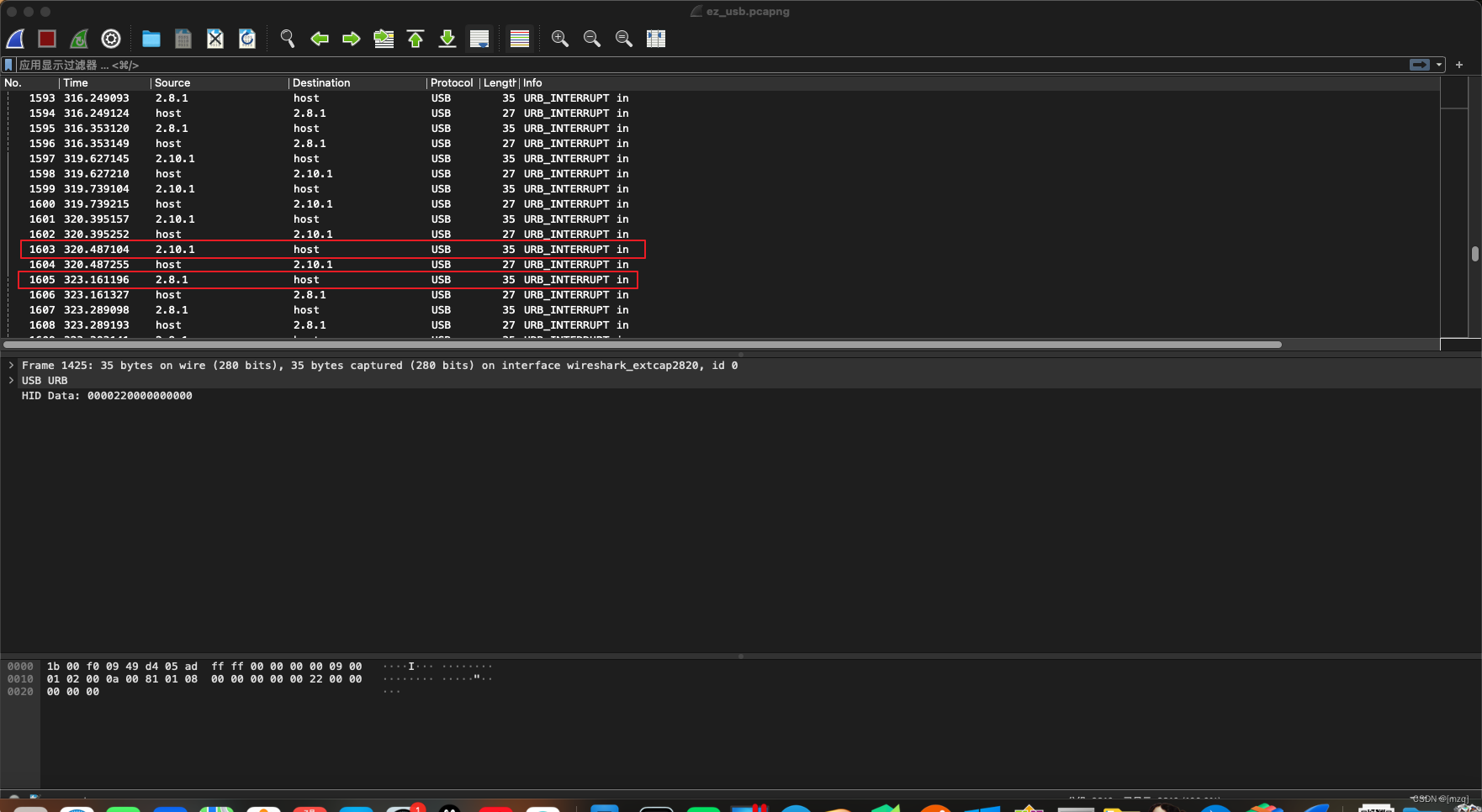
wireshark usb.src == “2.8.1” and usb.src == “2.10.1” Export specific groups
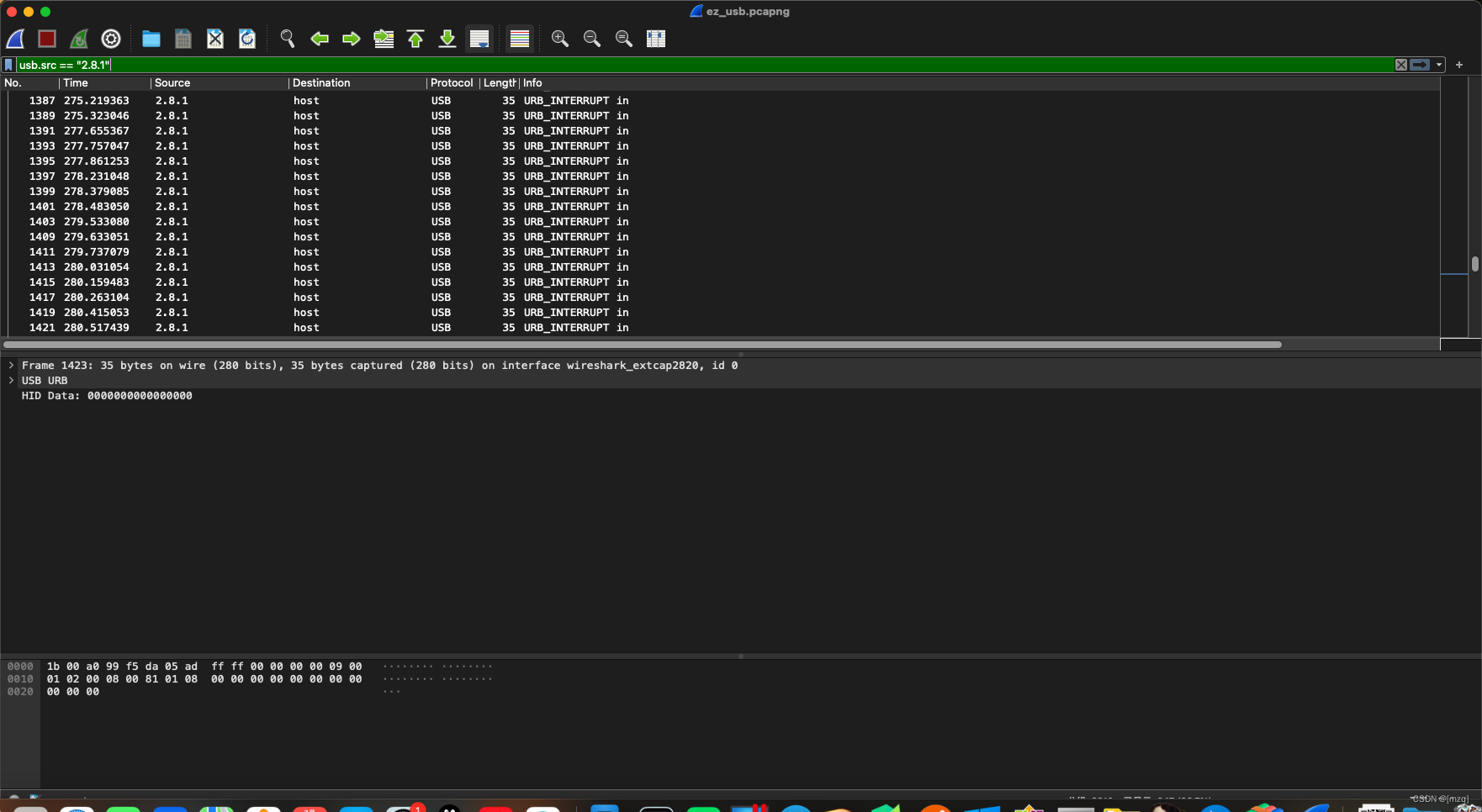
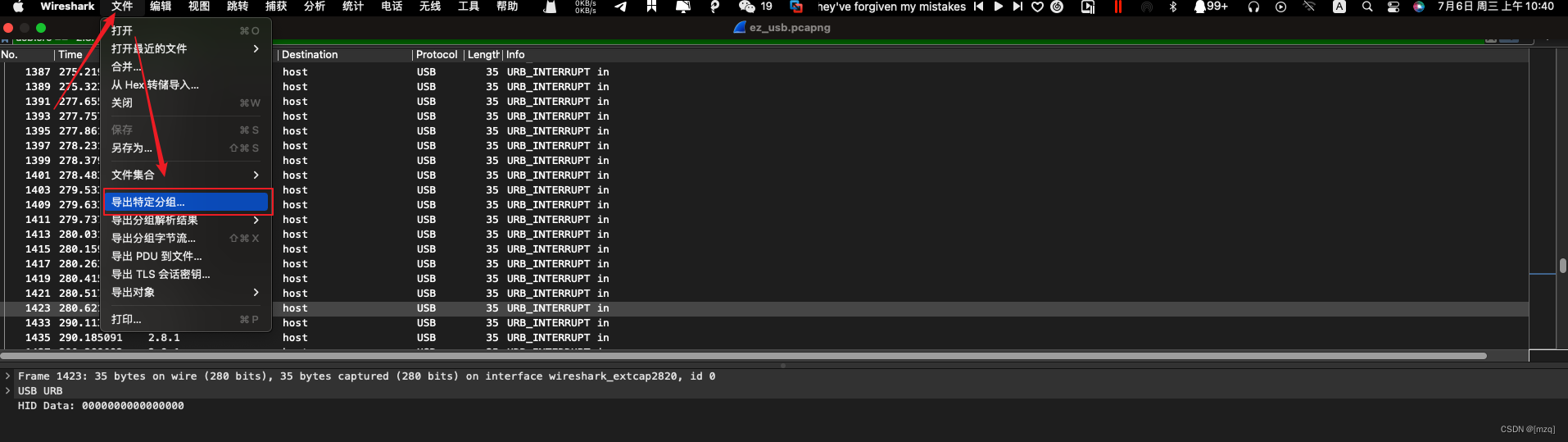
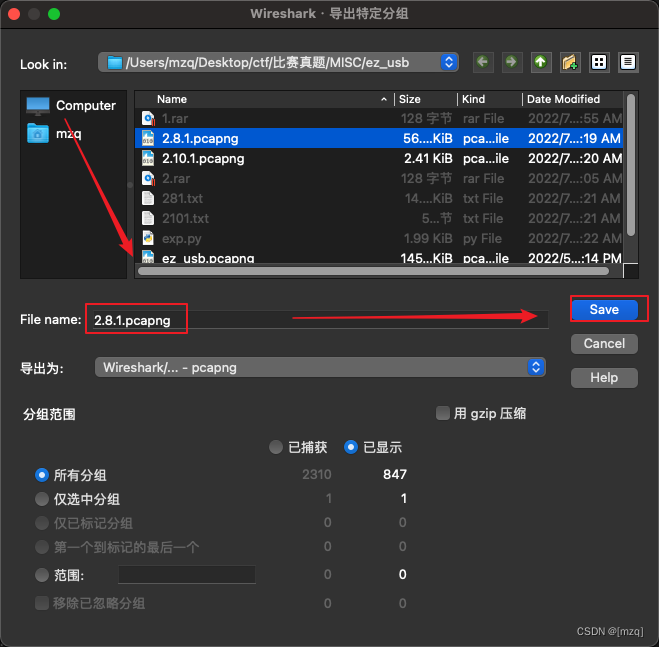
The two flows are derived as various pcapng file
Use UsbKeyboardDataHacker Directly analyze the content
UsbKeyboardDataHacker
#!/usr/bin/env python
import sys
import os
DataFileName = "usb.dat"
presses = []
normalKeys = {
"04":"a", "05":"b", "06":"c", "07":"d", "08":"e", "09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j", "0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o", "13":"p", "14":"q", "15":"r", "16":"s", "17":"t", "18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y", "1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4", "22":"5", "23":"6","24":"7","25":"8","26":"9","27":"0","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"-","2e":"=","2f":"[","30":"]","31":"\\","32":"<NON>","33":";","34":"'","35":"<GA>","36":",","37":".","38":"/","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
shiftKeys = {
"04":"A", "05":"B", "06":"C", "07":"D", "08":"E", "09":"F", "0a":"G", "0b":"H", "0c":"I", "0d":"J", "0e":"K", "0f":"L", "10":"M", "11":"N", "12":"O", "13":"P", "14":"Q", "15":"R", "16":"S", "17":"T", "18":"U", "19":"V", "1a":"W", "1b":"X", "1c":"Y", "1d":"Z","1e":"!", "1f":"@", "20":"#", "21":"$", "22":"%", "23":"^","24":"&","25":"*","26":"(","27":")","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"_","2e":"+","2f":"{","30":"}","31":"|","32":"<NON>","33":"\"","34":":","35":"<GA>","36":"<","37":">","38":"?","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
def main():
# check argv
if len(sys.argv) != 2:
print("Usage : ")
print(" python UsbKeyboardHacker.py data.pcap")
print("Tips : ")
print(" To use this python script , you must install the tshark first.")
print(" You can use `sudo apt-get install tshark` to install it")
print("Author : ")
print(" WangYihang <[email protected]>")
print(" If you have any questions , please contact me by email.")
print(" Thank you for using.")
exit(1)
# get argv
pcapFilePath = sys.argv[1]
# get data of pcap
os.system("tshark -r %s -T fields -e usb.capdata 'usb.data_len == 8' > %s" % (pcapFilePath, DataFileName))
# read data
with open(DataFileName, "r") as f:
for line in f:
presses.append(line[0:-1])
# handle
result = ""
for press in presses:
if press == '':
continue
if ':' in press:
Bytes = press.split(":")
else:
Bytes = [press[i:i+2] for i in range(0, len(press), 2)]
if Bytes[0] == "00":
if Bytes[2] != "00" and normalKeys.get(Bytes[2]):
result += normalKeys[Bytes[2]]
elif int(Bytes[0],16) & 0b10 or int(Bytes[0],16) & 0b100000: # shift key is pressed.
if Bytes[2] != "00" and normalKeys.get(Bytes[2]):
result += shiftKeys[Bytes[2]]
else:
print("[-] Unknow Key : %s" % (Bytes[0]))
print("[+] Found : %s" % (result))
# clean the temp data
os.system("rm ./%s" % (DataFileName))
if __name__ == "__main__":
main()
Find out
5261722yes rar The file header , Delete<CAP>c<DEL>And at the end of the filec, Then save as rar file

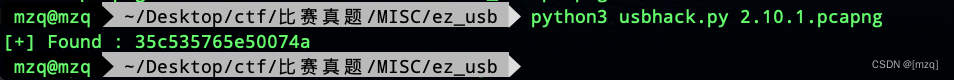
decompression rar Password required for file discovery , Extract another version of usb Traffic discovery password
35c535765e50074a
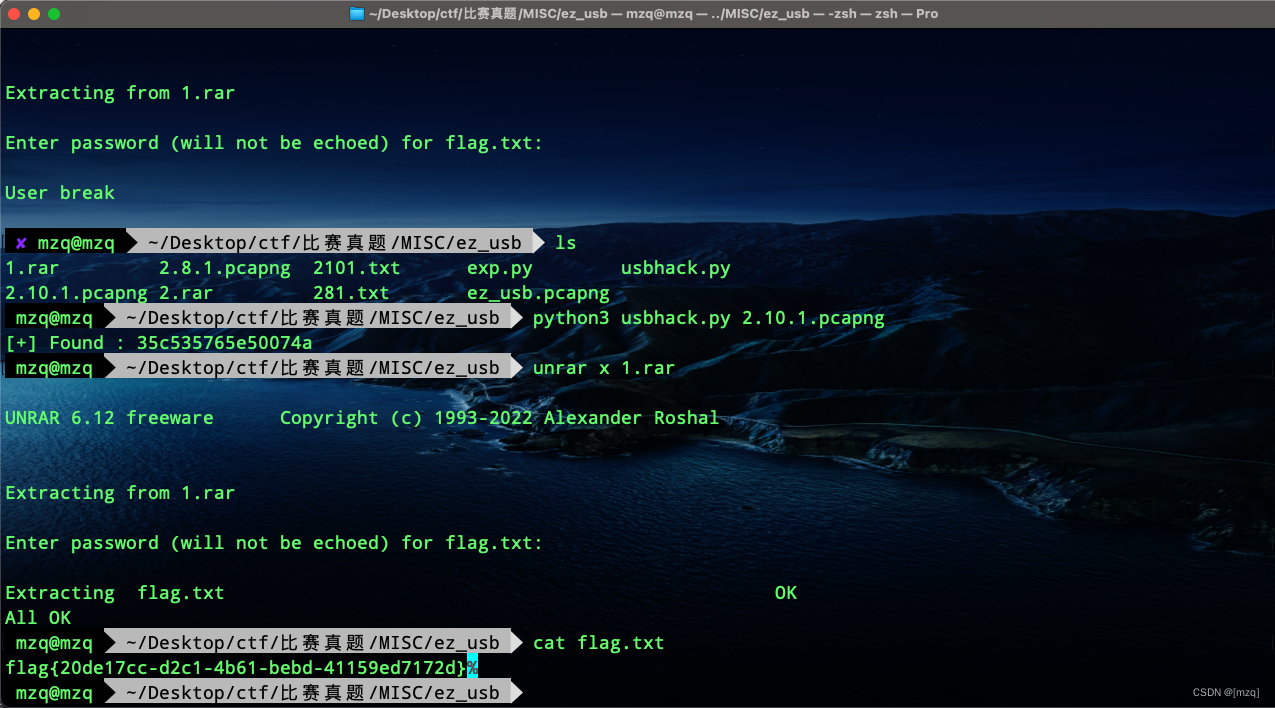
flag{
20de17cc-d2c1-4b61-bebd-41159ed7172d}
边栏推荐
- 1140_ SiCp learning notes_ Use Newton's method to solve the square root
- Convolutional neural network -- understanding of pooling
- Wx is used in wechat applet Showtoast() for interface interaction
- 解决could not find or load the Qt platform plugin “xcb“in ““.
- My ideal software tester development status
- IPv4 exercises
- Write CPU yourself -- Chapter 9 -- learning notes
- Gslx680 touch screen driver source code analysis (gslx680. C)
- JS get all date or time stamps between two time stamps
- Six methods of flattening arrays with JS
猜你喜欢
After 95, Alibaba P7 published the payroll: it's really fragrant to make up this
一、Go知识查缺补漏+实战课程笔记 | 青训营笔记
《动手学深度学习》(四) -- 卷积神经网络 CNN
【webrtc】m98 screen和window采集
English translation is too difficult? I wrote two translation scripts with crawler in a rage
图解GPT3的工作原理
四、高性能 Go 语言发行版优化与落地实践 青训营笔记
Redis data migration

Kbu1510-asemi power supply special 15A rectifier bridge kbu1510

misc ez_usb
随机推荐
Why is the row of SQL_ The ranking returned by number is 1
IO流 file
07_ Handout on the essence and practical skills of text measurement and geometric transformation
今日现货白银操作建议
Six methods of flattening arrays with JS
抽絲剝繭C語言(高階)數據的儲存+練習
numpy中dot函数使用与解析
English translation is too difficult? I wrote two translation scripts with crawler in a rage
Route jump in wechat applet
Detailed explanation of neo4j installation process
Music | cat and mouse -- classic not only plot
242. Bipartite graph determination
Build personal website based on flask
【云原生】内存数据库如何发挥内存优势
Redis data migration
After 95, Alibaba P7 published the payroll: it's really fragrant to make up this
解决:Could NOT find KF5 (missing: CoreAddons DBusAddons DocTools XmlGui)
面试官:你都了解哪些开发模型?
Simple example of ros2 planning system plansys2
Solve could not find or load the QT platform plugin "xcb" in "