当前位置:网站首页>2、 Concurrent and test notes youth training camp notes
2、 Concurrent and test notes youth training camp notes
2022-07-07 07:24:00 【A low-key horse】
Concurrent 、 Unit test course notes | Youth Camp notes
This is my participation 「 The third youth training camp - Back end field 」 The third part of note creation activities 1 Notes
Concurrent
Concurrency and parallelism
Concurrent : In a nuclear CPU Run in
parallel : In multi-core CPU Run in
Coroutines and threads
- coroutines : User mode lightweight threads ,KB Level
- Threads : Kernel mode , It can run multiple Synergetics ,MB Level
Co process communication
channel( Is it synchronized -> The efficiency of consumption and production varies )

Lock( Concurrent security )
sync Under bag Mutex, Locking ensures concurrency security
WaitGroup
Method :
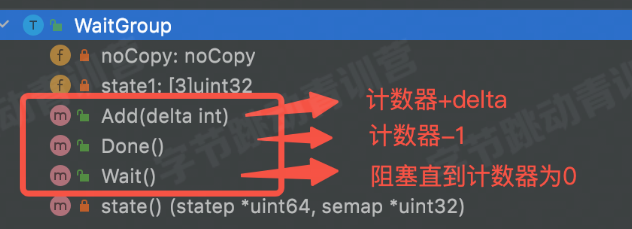
structure :
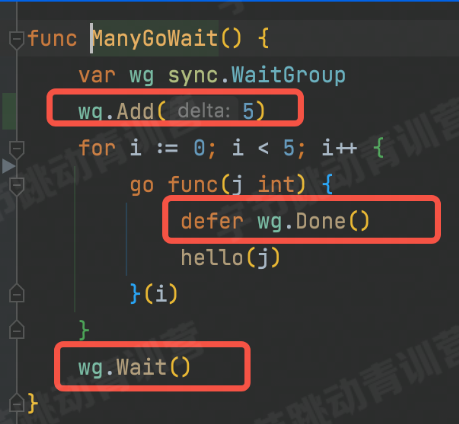
test
unit testing
The rules
assert( Example :assert.Equal() Method , Quickly compare and judge the test results )
coverage (
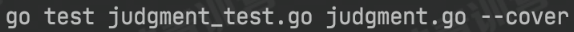 )<===“–cover”
)<===“–cover”rely on ((mock Mechanism ) idempotent 、 Stable ==》 Pile driving )
idempotent : Every test run should produce the same results as before
Mockey Patch The scope of Runtime, Pass... At run time Go Of unsafe package , Replace the address of the function in memory with the address of the runtime function . Jump the implementation of the function or method to be driven .
The benchmark
Test the performance and CPU Loss of
ps: perform rand It takes a long time , because rand In order to ensure global randomness and concurrency security , Holds a global lock , Therefore, it is recommended to use a high-performance random number method fastrand, At the expense of certain sequence consistency .
Add
The difference between the two forms of login
One 、Cookie and Session
This is generally used for authentication when interacting with the client .
Two 、JWT+Token
No need to rely on some storage , Generally, the backend decrypts directly .
It usually lies in the server 、http If you interact , Use JWT+token
Message queuing application scenario
The main problem to be solved is isolation
Use scenarios : The two methods , If it's a strong dependence , It cannot be achieved in this way
If it is non strong dependency , Method A Is to release a message 、 event , Method B It is to receive and consume this event for asynchronous processing , In this case, use message queuing , Can play a decoupling function
Strong dependence , It cannot be achieved in this way
If it is non strong dependency , Method A Is to release a message 、 event , Method B It is to receive and consume this event for asynchronous processing , In this case, use message queuing , Can play a decoupling function
边栏推荐
- Cloud backup project
- . Net core accesses uncommon static file types (MIME types)
- Multithreading and high concurrency (9) -- other synchronization components of AQS (semaphore, reentrantreadwritelock, exchanger)
- 深度学习花书+机器学习西瓜书电子版我找到了
- AVL树的实现
- 组件的嵌套和拆分
- Composition API 前提
- Bindingexception exception (error reporting) processing
- Advanced practice of C language (high level) pointer
- 普通测试年薪15w,测试开发年薪30w+,二者差距在哪?
猜你喜欢
Composition API premise
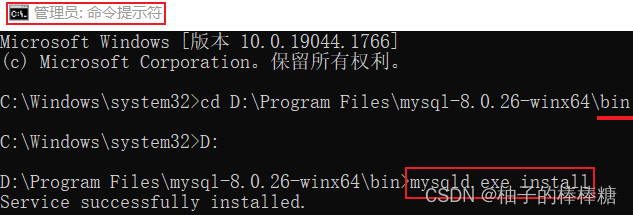
MySQL service is missing from computer service
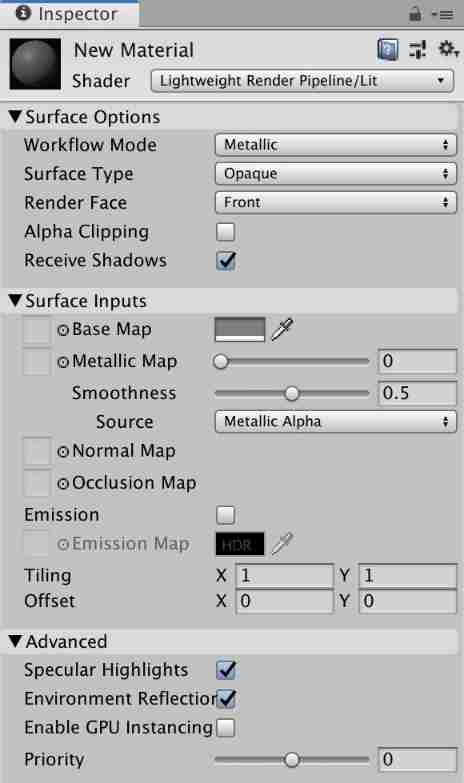
URP - shaders and materials - light shader lit
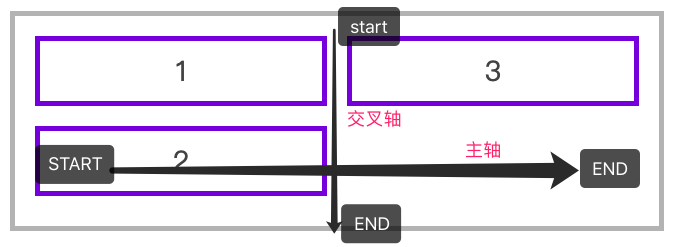
Flexible layout (II)
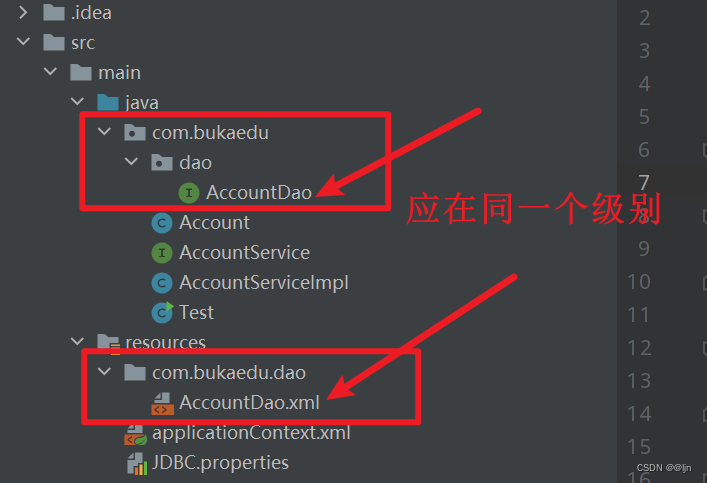
Bindingexception exception (error reporting) processing
sql中对集合进行非空校验
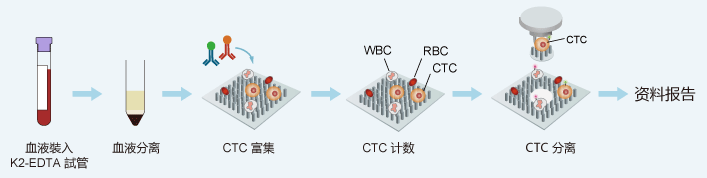
Circulating tumor cells - here comes abnova's solution
![How to model and simulate the target robot [mathematical / control significance]](/img/bd/79f6338751b6773859435c54430ec3.png)
How to model and simulate the target robot [mathematical / control significance]
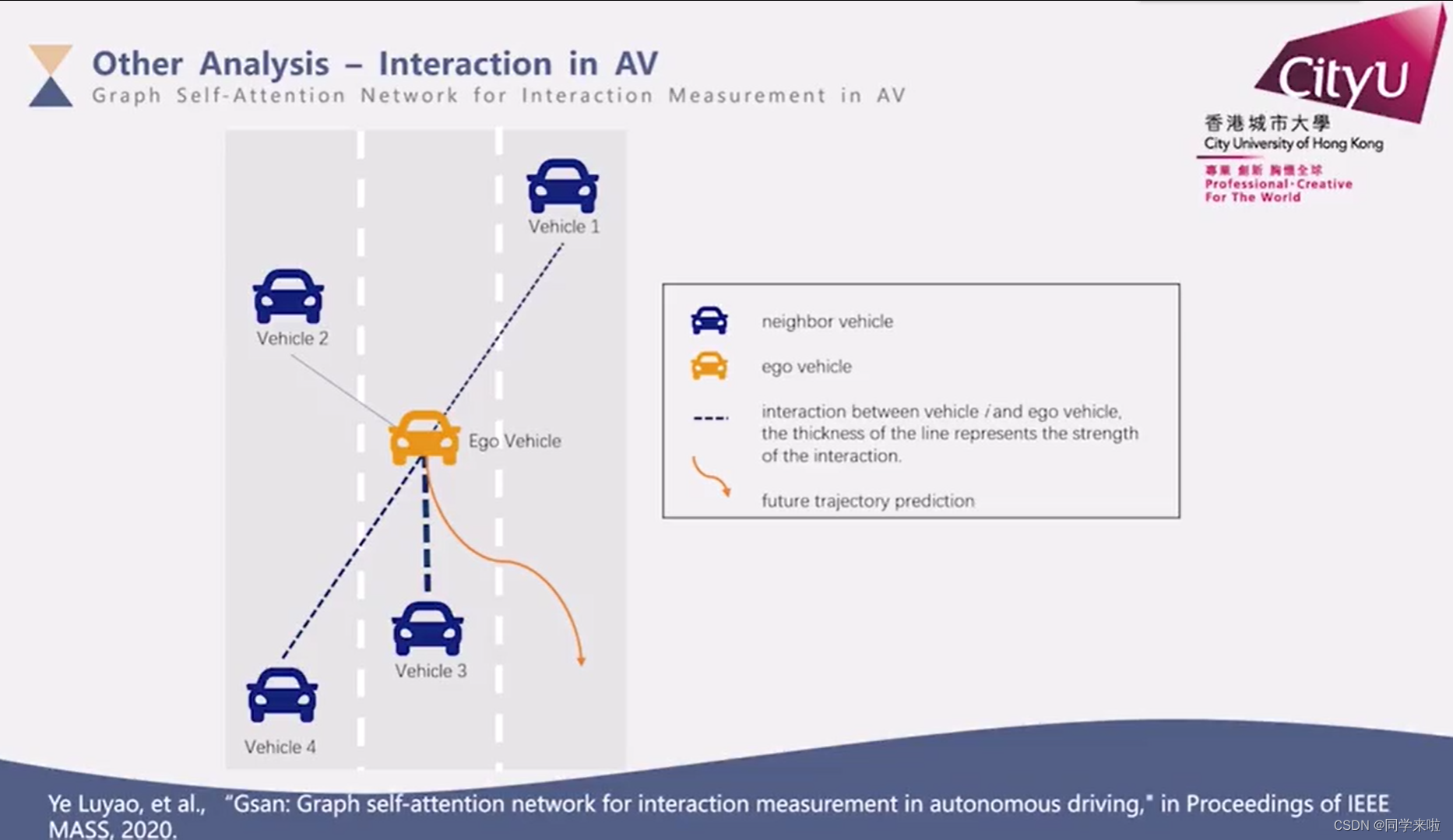
Academic report series (VI) - autonomous driving on the journey to full autonomy
Example of Pushlet using handle of Pushlet
随机推荐
2018 Jiangsu Vocational College skills competition vocational group "information security management and evaluation" competition assignment
. Net 5 fluentftp connection FTP failure problem: this operation is only allowed using a successfully authenticated context
Tumor immunotherapy research prosci Lag3 antibody solution
Music | cat and mouse -- classic not only plot
异步组件和Suspense(真实开发中)
【Liunx】进程控制和父子进程
Differences between H5 architecture and native architecture
[Luogu p1971] rabbit and egg game (bipartite game)
The currently released SKU (sales specification) information contains words that are suspected to have nothing to do with baby
Convolutional neural network -- understanding of pooling
Circulating tumor cells - here comes abnova's solution
Sqlmap tutorial (IV) practical skills three: bypass the firewall
记一个并发规则验证实现
[explanation of JDBC and internal classes]
"Xiaodeng in operation and maintenance" meets the compliance requirements of gdpr
After the promotion, sales volume and flow are both. Is it really easy to relax?
JS small exercise
A slow SQL drags the whole system down
弹性布局(一)
About binary cannot express decimals accurately