当前位置:网站首页>Sword finger offer 14- I. cut rope
Sword finger offer 14- I. cut rope
2022-07-03 12:59:00 【Hiccup~~~~】
The finger of the sword Offer 14- I. Cut the rope
I'll give you a length of n The rope of , Please cut the rope to the whole length m paragraph (m、n Are integers. ,n>1 also m>1), The length of each rope is recorded as k[0],k[1]…k[m-1] . Excuse me, k[0]k[1]…*k[m-1] What's the maximum possible product ? for example , When the length of the rope is 8 when , We cut it into lengths of 2、3、3 Three paragraphs of , The maximum product we get here is 18.
Example 1:
Input : 2
Output : 1
explain : 2 = 1 + 1, 1 × 1 = 1
Example 2:
Input : 10
Output : 36
explain : 10 = 3 + 3 + 4, 3 × 3 × 4 = 36
Tips :
2 <= n <= 58
Ideas
Dynamic programming
Recurrence :a[i]=max(a[i], max( (i-j),a[i-j] ) * max( j,a[j] ));
- max( Previous value , Current updated value )
- Current updated value =[i-j] The maximum value of the range * [0-j] Maximum range
Code
class Solution {
public:
int cuttingRope(int n) {
vector<int> a(60);
a[0]=0;
a[1]=1;
for(int i=2;i<=n;i++){
for(int j=1;j<i;j++){
a[i]=max(a[i],max( (i-j),a[i-j] )*max( j,a[j] ));
}
// printf("%d--%d\n",i,a[i]);
}
return a[n];
}
};
边栏推荐
- C graphical tutorial (Fourth Edition)_ Chapter 13 entrustment: what is entrustment? P238
- 2022-02-09 survey of incluxdb cluster
- GaN图腾柱无桥 Boost PFC(单相)七-PFC占空比前馈
- Tensorflow binary installation & Failure
- 【判断题】【简答题】【数据库原理】
- [ArcGIS user defined script tool] vector file generates expanded rectangular face elements
- 解决 System has not been booted with systemd as init system (PID 1). Can‘t operate.
- Differences between initial, inherit, unset, revert and all
- Define a list, store n integers, and calculate the length, maximum value, minimum value and average value of the list
- Harmonic current detection based on synchronous coordinate transformation
猜你喜欢
![[network counting] Chapter 3 data link layer (2) flow control and reliable transmission, stop waiting protocol, backward n frame protocol (GBN), selective retransmission protocol (SR)](/img/45/c2d7934b886d8090373ca9e6e23c97.gif)
[network counting] Chapter 3 data link layer (2) flow control and reliable transmission, stop waiting protocol, backward n frame protocol (GBN), selective retransmission protocol (SR)
【计网】第三章 数据链路层(2)流量控制与可靠传输、停止等待协议、后退N帧协议(GBN)、选择重传协议(SR)

Harmonic current detection based on synchronous coordinate transformation

4. 无线体内纳米网:电磁传播模型和传感器部署要点
Analysis of a music player Login Protocol

Application of ncnn neural network computing framework in orange school orangepi 3 lts development board
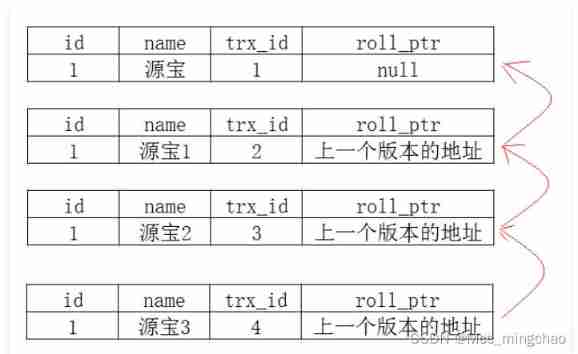
Deeply understand the mvcc mechanism of MySQL
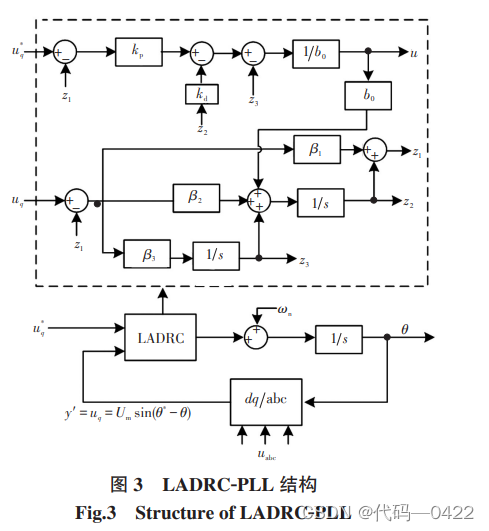
自抗扰控制器七-二阶 LADRC-PLL 结构设计

高效能人士的七个习惯
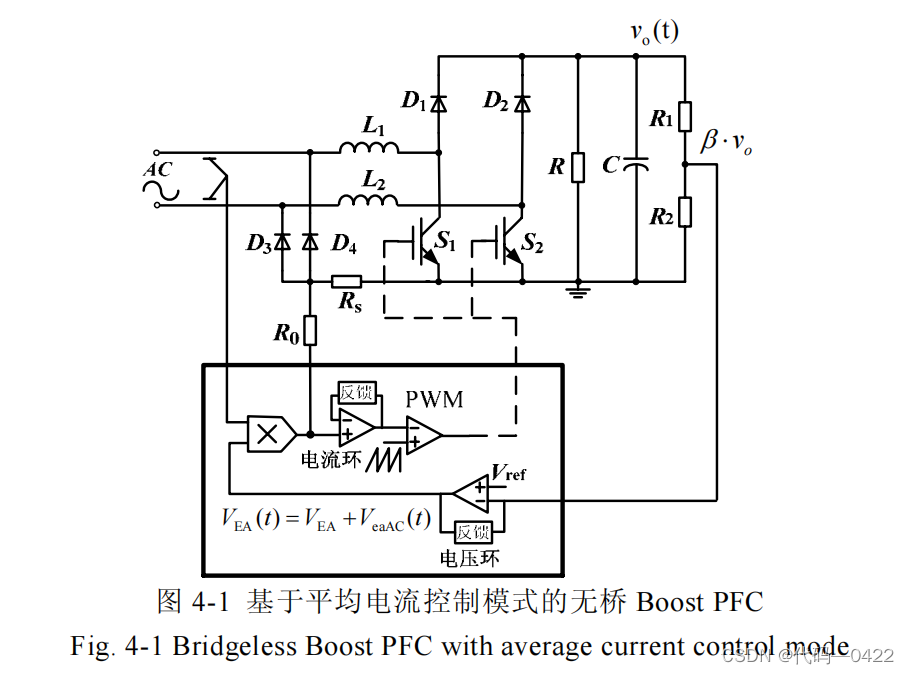
电压环对 PFC 系统性能影响分析
随机推荐
2022-01-27 redis cluster cluster proxy predixy analysis
【习题七】【数据库原理】
Pytext training times error: typeerror:__ init__ () got an unexpected keyword argument 'serialized_ options'
剑指 Offer 16. 数值的整数次方
Analysis of the influence of voltage loop on PFC system performance
剑指 Offer 14- II. 剪绳子 II
Drop down refresh conflicts with recyclerview sliding (swiperefreshlayout conflicts with recyclerview sliding)
alright alright alright
Differences and connections between final and static
有限状态机FSM
社交社区论坛APP超高颜值UI界面
Export the entire Oracle Database
Deeply understand the mvcc mechanism of MySQL
[ArcGIS user defined script tool] vector file generates expanded rectangular face elements
Keep learning swift
C graphical tutorial (Fourth Edition)_ Chapter 13 entrustment: what is entrustment? P238
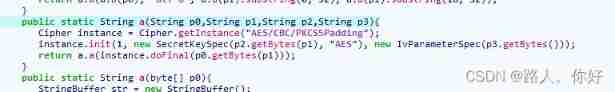
The foreground uses RSA asymmetric security to encrypt user information
初入职场,如何快速脱颖而出?
How to get user location in wechat applet?
2022-01-27 redis cluster technology research