当前位置:网站首页>Answer to the first stage of the assignment of "information security management and evaluation" of the higher vocational group of the 2018 Jiangsu Vocational College skills competition
Answer to the first stage of the assignment of "information security management and evaluation" of the higher vocational group of the 2018 Jiangsu Vocational College skills competition
2022-07-07 06:48:00 【Wangzai sec】
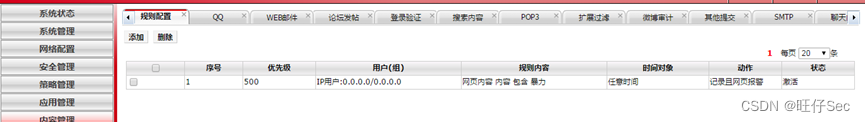
1. According to the network topology diagram , according to IP Address planning table , Yes WAF The name of .(20 branch )
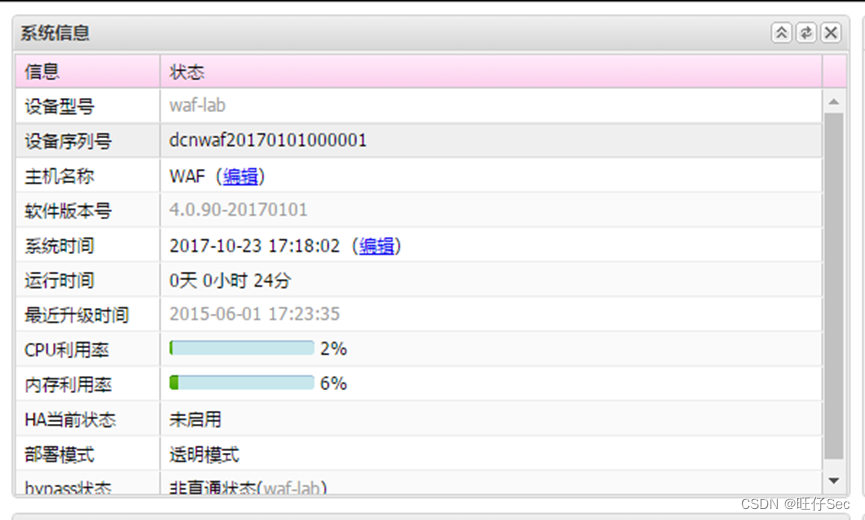
2. According to the network topology diagram , according to IP Address planning table , Yes DCRS The name of 、 Each interface IP Address configuration , stay DCRS Create the corresponding... On the switch VLAN, And classify the corresponding interface into VLAN.(56 branch , Yes, one button 5 branch , Until it's done )
DCRS#sh run
hostname DCRS (5 branch )
vlan 1-2;10;20;30;66 (5 branch )
!
Interface Ethernet1/0/1
!
Interface Ethernet1/0/2
switchport access vlan 2 (5 branch )
!
Interface Ethernet1/0/3
switchport access vlan 10 (5 branch )
!
Interface Ethernet1/0/4
switchport access vlan 20 (5 branch )
!
Interface Ethernet1/0/5
switchport access vlan 30 (5 branch )
!
Interface Ethernet1/0/6
switchport access vlan 66 (5 branch )
!
interface Vlan1
ip address 192.168.1.254 255.255.255.0 (5 branch )
!
interface Vlan2
ip address 192.168.2.1 255.255.255.0 (5 branch )
!
interface Vlan10
ip address 192.168.10.254 255.255.255.0 (5 branch )
!
interface Vlan20
ip address 192.168.20.254 255.255.255.0 (5 branch )
!
interface Vlan30
ip address 192.168.30.254 255.255.255.0 (5 branch )
!
interface Vlan66
ip address 192.168.66.254 255.255.255.0
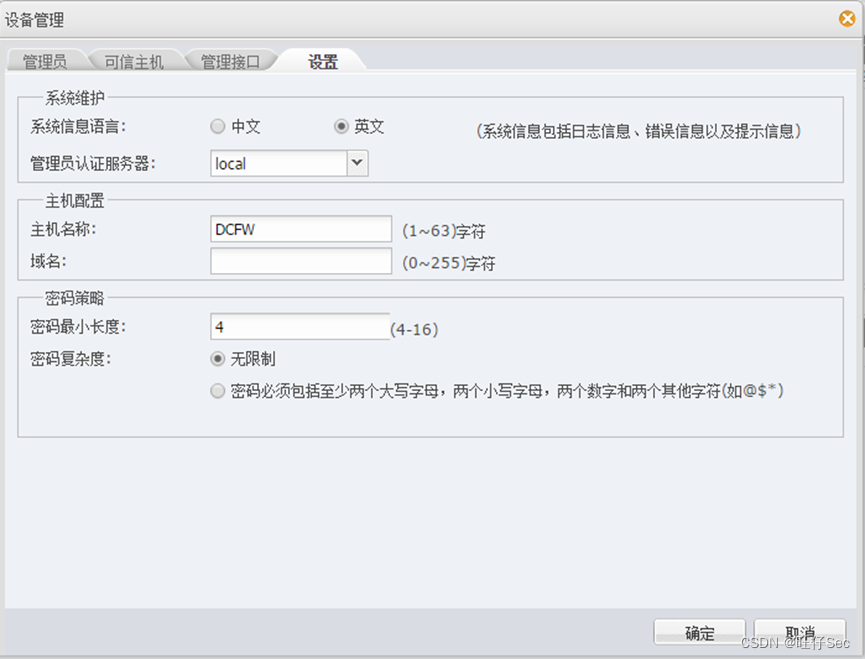
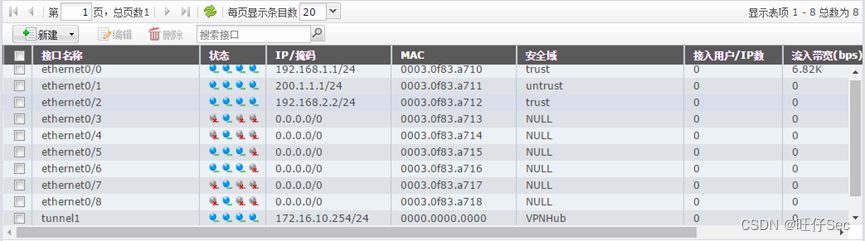
3. According to the network topology diagram , according to IP Address planning table , Yes DCFW The name of 、 Each interface IP Address configuration .(20 branch , Deduct every mistake 7 branch )
4. According to the network topology diagram , according to IP Address planning table , stay DCWS Create the corresponding VLAN, And classify the corresponding interface into VLAN, Yes DCWS Management of IP Address configuration .(26 branch , Deduct every mistake 4 branch )
DCWS#sh run
hostname DCWS (4 branch )
vlan 1;66 (4 branch )
!
Interface Ethernet1/0/16
switchport access vlan 66 (4 branch )
interface Vlan66 (4 branch )
ip address 192.168.66.253 255.255.255.0
!
interface Vlan110(4 branch )
ip address 192.168.110.254 255.255.255.0
!
interface Vlan111(4 branch )
ip address 192.168.111.254 255.255.255.0
!
interface Vlan222(4 branch )
ip address 192.168.222.254 255.255.255.0
!
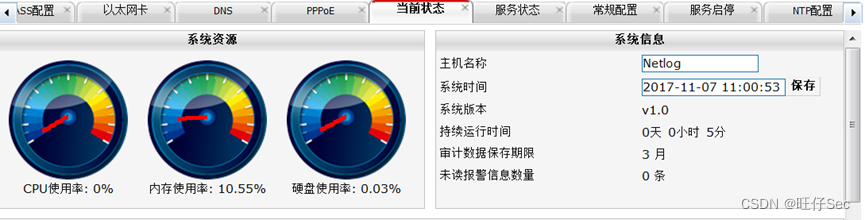
5. According to the network topology diagram , according to IP Address planning table , Yes DCBI The name of 、 Each interface IP Address configuration .(20 branch , Deduct every mistake 10 branch )
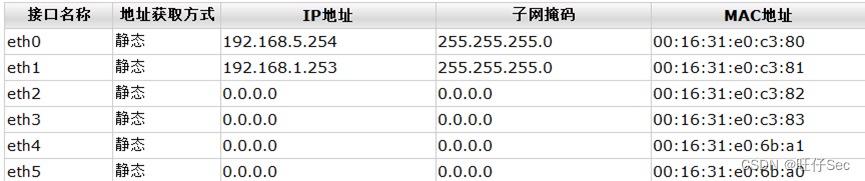
6. The internal network adopts static routing to realize the interconnection of the whole network .(18 branch )
Switch : (8 branch )
ip route 0.0.0.0/0 192.168.2.2
ip route 192.168.110.0/24 192.168.66.253
ip route 192.168.111.0/24 192.168.66.253
ip route 192.168.222.0/24 192.168.66.253
!
AC:
ip route 0.0.0.0 0.0.0.0 192.168.66.254 (4 branch )
A firewall : (8 branch )
WAF part
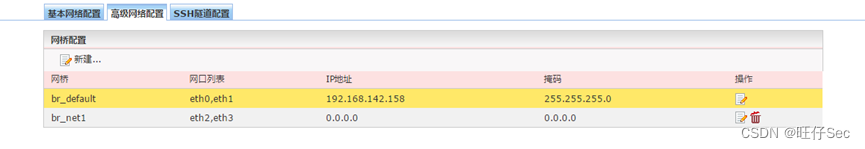
- To configure WAF In transparent mode , Complete the interface bridging according to the meaning of the question ;(6 branch )
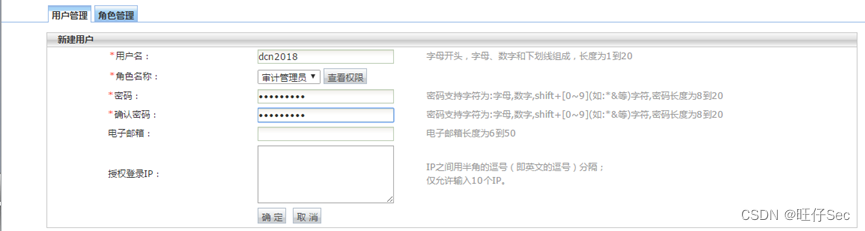
- Create an audit administrator account , user name :dcn2018, password :201810dcn(6 branch )
- To configure WAF When a malicious scanning website is found , take HTTP Redirect to http://www.dcn.com/alarm.html, Warn the attacker ;(12 branch , Scanning protection 4 branch , action 4 branch , Redirect URL 4 branch )
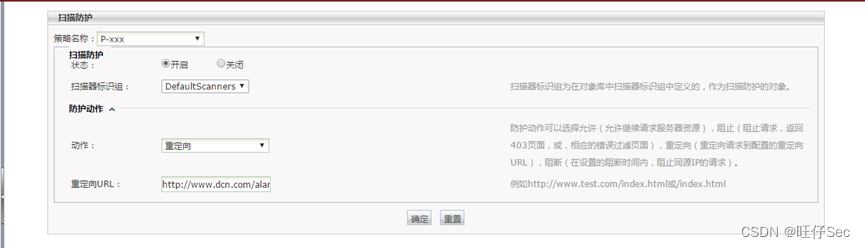
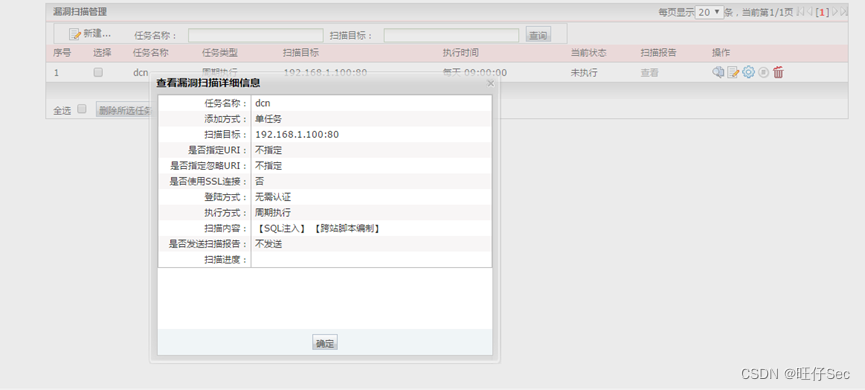
- New vulnerability scanning task dcn, Every day 9:00 scanning 192.168.1.100:80,SQL Inject , Cross site scripting ;(12 branch , The name of the task 4 branch , Scan target 4 branch , Scan content 4 branch )
DCWS part
- DCWS To configure VLAN110 To manage VLAN, AP Register dynamically to AC,AC management IP by 192.168.110.254; data VLAN by 111 and 222,vlan222 Related to SSID DCN, Issue network segments respectively 192.168.111.0/24,192.168.222.0/24, Gateway is the last available IP,DNS:8.8.8.8, The gateway needs to be excluded , The address is 2 God ;(22 branch , Deduct every mistake 2 branch , Until it's done )
service dhcp(2 branch )
!
ip dhcp excluded-address 192.168.111.254
ip dhcp excluded-address 192.168.222.254(2 branch )
!
ip dhcp pool 110
network-address 192.168.110.0 255.255.255.0
option 43 hex 0104C0A86EFE
option 60 ascii udhcp1.18.2(2 branch )
!
ip dhcp pool 111
network-address 192.168.111.0 255.255.255.0
default-router 192.168.111.254
lease 2 0 0
dns-server 8.8.8.8(2 branch )
!
ip dhcp pool 222
network-address 192.168.222.0 255.255.255.0
default-router 192.168.222.254
lease 2 0 0
dns-server 8.8.8.8(2 branch )
!
interface Vlan66
ip address 192.168.66.253 255.255.255.0(2 branch )
!
interface Vlan110
ip address 192.168.110.254 255.255.255.0(2 branch )
!
interface Vlan111
ip address 192.168.111.254 255.255.255.0(2 branch )
!
interface Vlan222
ip address 192.168.222.254 255.255.255.0(2 branch )
!
ip route 0.0.0.0/0 192.168.66.254 (2 branch )
!
Interface Ethernet1/0/15 (2 branch )
switchport mode trunk
switchport trunk native vlan 110
!
Interface Ethernet1/0/16 (2 branch )
switchport access vlan 66
wireless
no auto-ip-assign
enable
ap authentication none
static-ip 192.168.110.254(2 branch )
network 1 (2 branch )
ssid GUEST
vlan 111
network 2 (2 branch )
ssid DCN
vlan 222
ap profile 1
name Default
hwtype 29( or 59)(2 branch )
radio 1
vap 1
enable (2 branch )
radio 2
vap 1
enable (2 branch )
- To configure 2.4G Work under frequency band , Use 802.11g agreement ;(8 branch )
wireless
ap profile 1
ap escape (4 branch )
radio 1
mode g (4 branch )
- Set up SSID GUEST, The encryption mode is wpa-personal, The password is :11111111,VLAN111(12 branch , Deduct every mistake 3 branch , Until it's done )
network 1
security mode wpa-personal(3 branch )
ssid GUEST(3 branch )
vlan 111(3 branch )
wpa key xxxxxx(3 branch )
- GUEST Flow control network , The upside 1M, The downside 2M And turn on user isolation . (12 branch , Deduct every mistake 3 branch )
network 2
client-qos enable(3 branch )
client-qos bandwidth-limit down 2048(3 branch )
client-qos bandwidth-limit up 1024(3 branch )
station-isolation (3 branch )
- Through configuration, it is avoided that there are many access terminals and a large number of weak terminals , Avoid high-speed clients from being blocked by low-speed clients “ Drag on ”, Let the low-speed client not lose transmission for a long time ;(6 branch )
ap profile 1
radio 1
schedule-mode preferred (3 branch )
radio 2
schedule-mode preferred (3 branch )
Router part
- Configure the default route , Enable intranet users to access Internet;( 2 branch )
ip route 0.0.0.0/0 192.168.2.2
- Will connect DCFW Two way traffic is mirrored to Netlog To monitor and analyze ;(6 branch )
monitor session 1 source interface Ethernet1/0/2 tx(2 branch )
monitor session 1 source interface Ethernet1/0/2 rx(2 branch )
monitor session 1 destination interface Ethernet1/0/1(2 branch )
- Turn on the anti-jamming device ARP Scanning function , Port received... In unit time ARP More than 50 It's considered an attack ,DOWN Drop this port ;(4 branch )
anti-arpscan enable(2 branch )
anti-arpscan port-based threshold 50(2 branch )
- At the company headquarters DCRS Configure port loop detection on (Loopback Detection), Prevent from vlan20 Single port loop under interface , The detection time interval when there is a loop is configured as 30 second , The detection interval when there is no loop is 10 second ; (4 branch )
Interface Ethernet1/0/4
switchport access vlan 20
loopback-detection specified-vlan 20 (2 branch )
loopback-detection control block
!
loopback-detection interval-time 30 10 (2 branch )
- To control access to the network PC, Need to exchange Eth1/0/10 Mouth open DOT1X authentication , Configure authentication server ,IP The address is 192.168.2.100,radius key yes dcn2018;; (10 branch )
radius-server key 0 dcn2018(2 branch )
radius-server authentication host 192.168.2.100(2 branch )
aaa enable(2 branch )
!
dot1x enable (2 branch )
!
Interface Ethernet1/0/10 (2 branch )
dot1x enable
dot1x port-method portbased
!
- Switch on remote management , Use SSH The method account number is group number , The password for 123456.(4 branch )
ssh-server enable (2 branch )
username 5( Group number ) privilege 15 password 0 123456 (2 branch )
- VLAN20 Users use dynamic acquisition IP Address ,DHCP The server AC On the configuration .(4 branch )
service dhcp (2 branch )
ip forward-protocol udp bootps
interface Vlan20
ip address 192.168.20.254 255.255.255.0
ip helper-address 192.168.66.253 (2 branch )
- Configure... On the switch , Only allowed in vlan30 Users access the wireless management segment during working hours IP.(6 branch )
Firewall enable
!
time-range time2 (2 branch )
periodic weekdays 00:00:00 to 09:00:00
periodic weekdays 18:00:00 to 23:59:59
periodic weekend 00:00:00 to 23:59:59
!
ip access-list extended acl (2 branch )
deny ip 192.168.30.0 0.0.0.255 192.168.110.0 0.0.0.255 time-range time2
permit ip any-source any-destination
exit
!
Interface Ethernet1/0/5 (2 branch )
switchport access vlan 30
ip access-group acl in
- For interception 、 Prevent illegal MAC Address and IP Address bound ARP Packet configuration is dynamic arp Detection function ,VLAN30 User network interface ARP The threshold is 50.(4 branch )
interface Vlan30
ip address 192.168.30.254 255.255.255.0
ip arp dynamic maximum 50
Firewall part
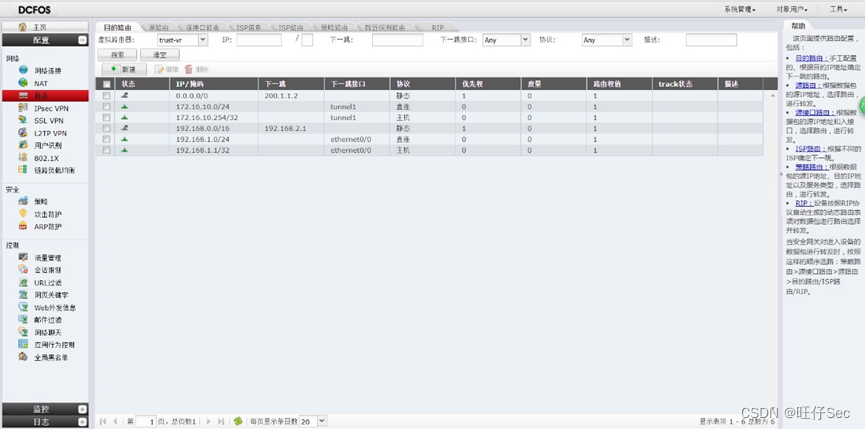
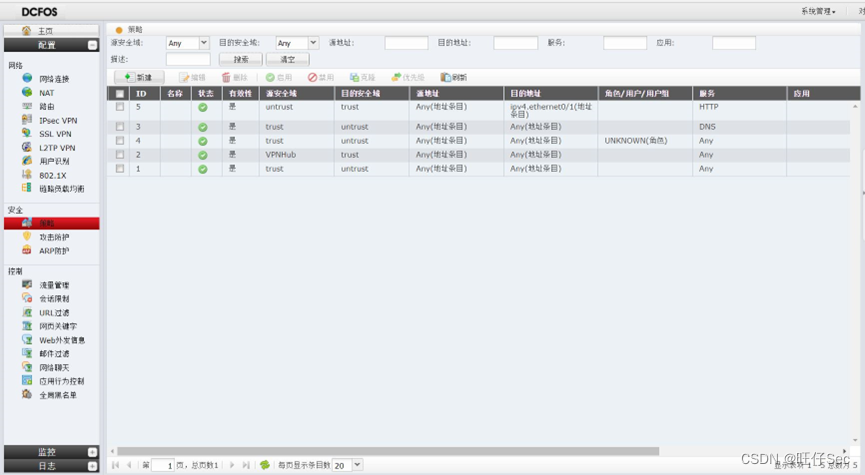
- In the head office DCFW Configure according to the meaning of the question Trust,Untruct,VPNhub Area , And configure the release strategy between regions ;(6 branch , Deduct every mistake 2 branch )
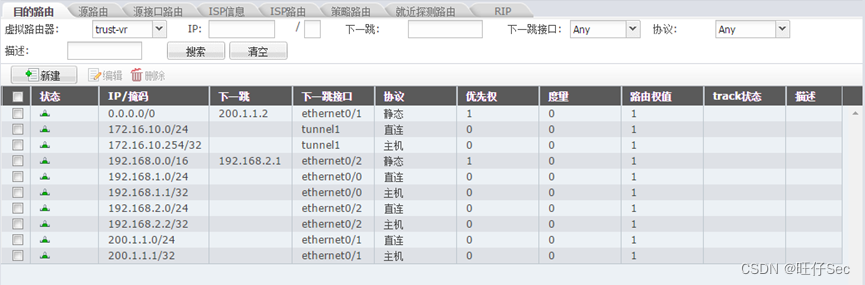
- Configure the routing , Leading to internet Configure the default route in the specified direction , Use the next hop IP by PC2, Configure static main class summary routes for internal routes ;(8 branch , Deduct every mistake 4 branch )
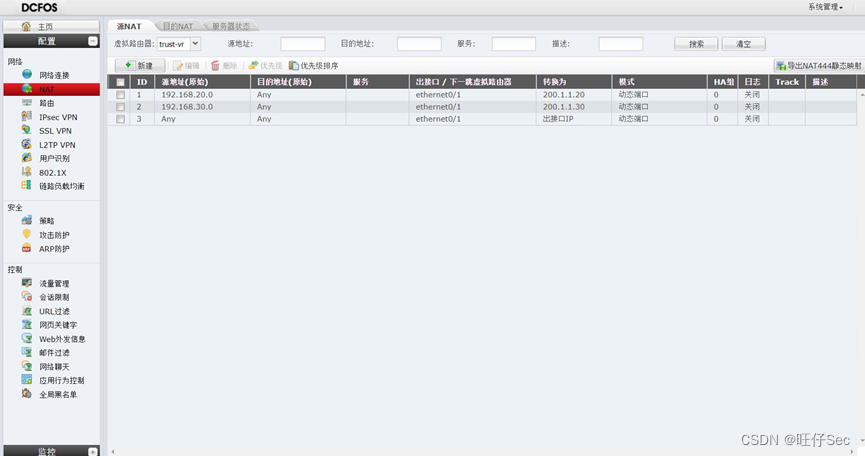
- Configuration dynamics NAT, The correspondence is as follows :(9 branch , Deduct every mistake 3 branch )
VLAN20 The user map is 200.1.1.20;
VLAN30 The user map is 200.1.1.30;
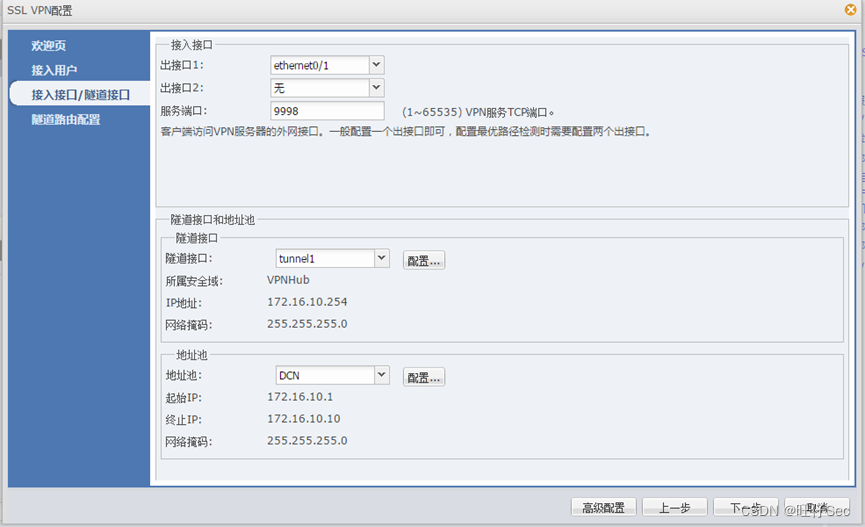
- The head office DCFW To configure SSLVPN, Build users dcn01, password dcn01, Connection required Internet PC2 You can dial in , The service port is 9998,SSLVPN See address table for address pool ; (8 branch , Deduct every mistake 4 branch , Until it's done )
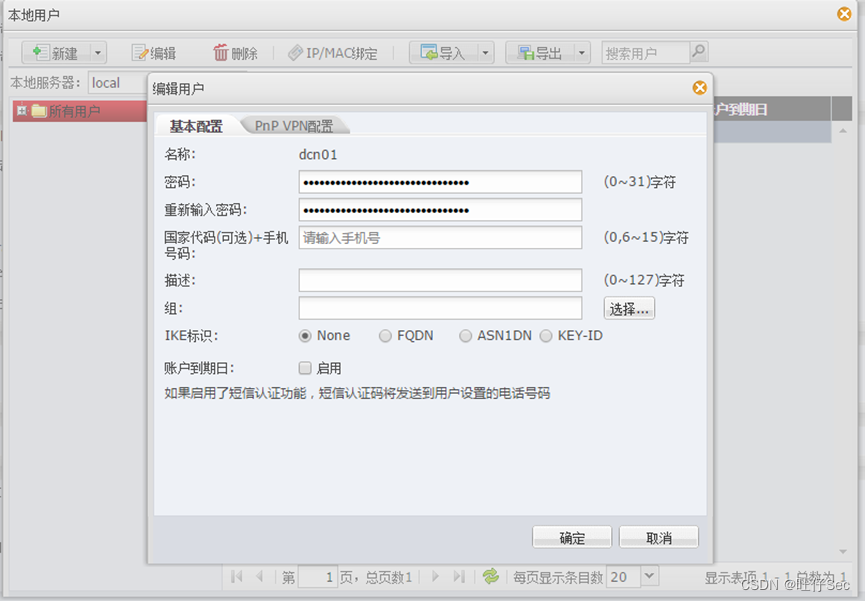
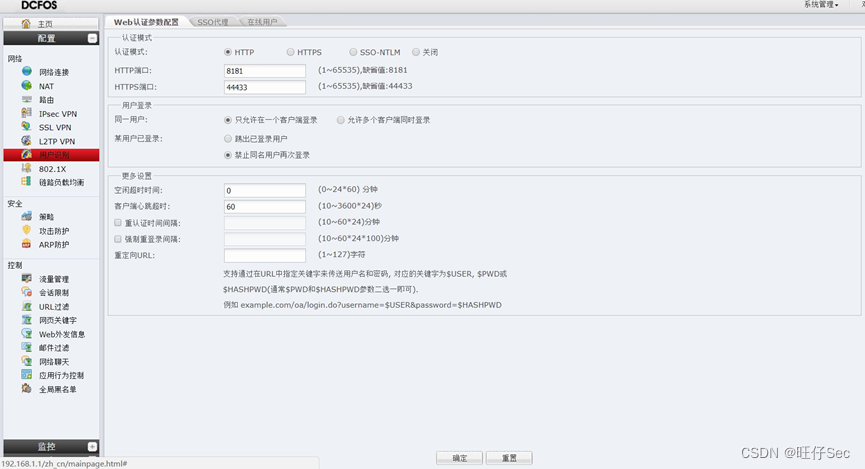
5、 Intranet wireless users need to pass real name authentication to access the Internet , Adopt export local certification , The account number is the group number , The password for 123.(8 branch , Deduct every mistake 4 branch , Until it's done )

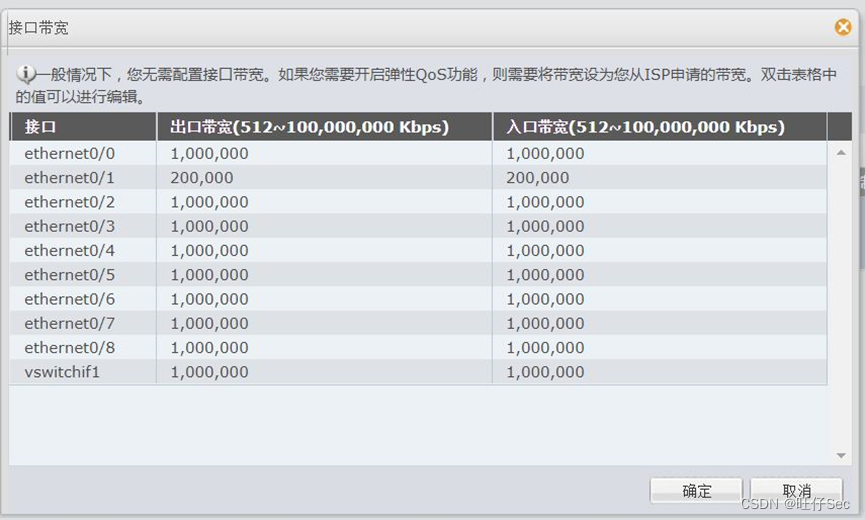
- In order to make rational use of export bandwidth resources, it is necessary to limit the Internet bandwidth of internal users , On weekdays 8:00 To 18:00 Wired users upload online / The download bandwidth is 1000K/2000K, The total export bandwidth of the park network is 200M.(9 branch , Deduct every mistake 3 branch , Until it's done )
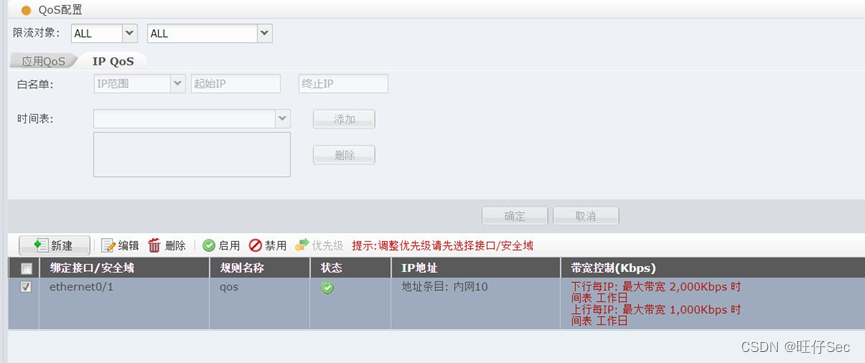
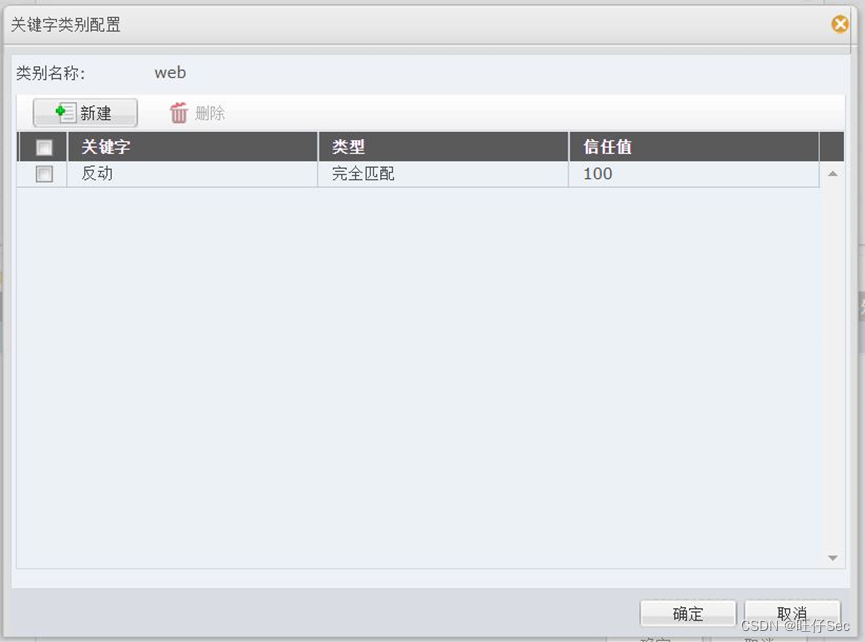
7、 In response to the net action of the network supervision office , It is required that wired users of the intranet web Control the outgoing content , It is forbidden to send keywords to web pages on the Internet “ reactionary ” And record relevant logs .(6 branch , Deduct every mistake 3 branch , Until it's done )
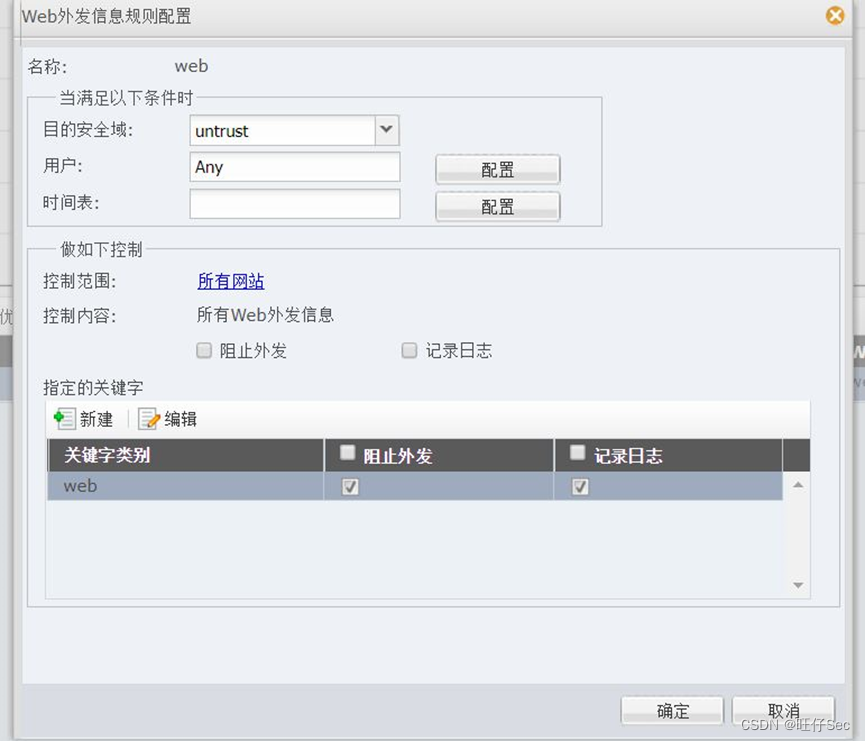

8、 Find the inside first VLAN20 and VLAN30 A large number of users are connected to the Internet , As a result, it is very slow for intranet users to open external web pages, and sometimes they can't open , It is required to make corresponding settings on the firewall , Control the problem .(6 branch , Deduct every mistake 3 branch , Until it's done )
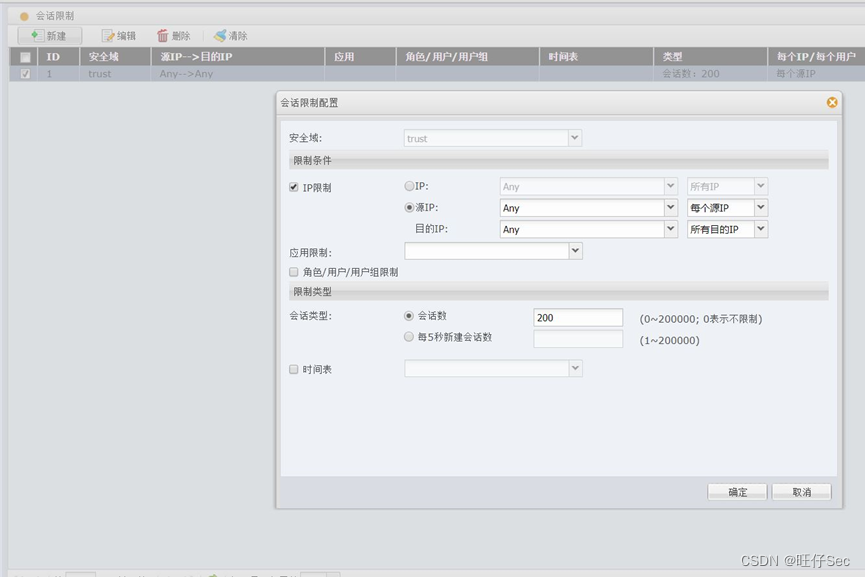
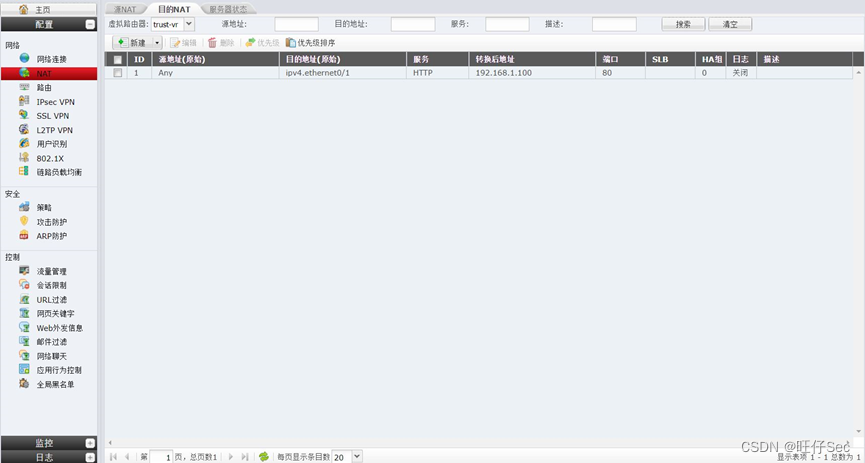
9、PC2 It can pass the address orientation of the external network port of the firewall DCST Of 80 port .(4 branch , Deduct every mistake 2 branch , Until it's done )

DCBI part
- At the company headquarters DCBI On the configuration , The equipment is deployed in bypass mode , Add administrator account dcn2018, password dcn2018;(12 branch )
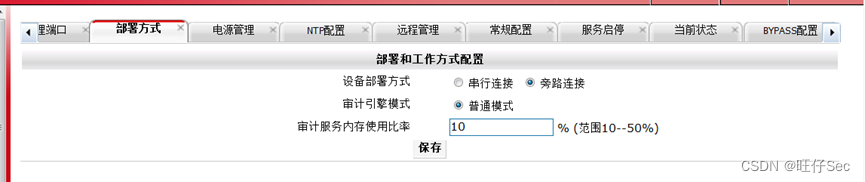
- Add content rule , For website access, the keywords include “ violence ” Of , Record and email alarm ;(12 branch )
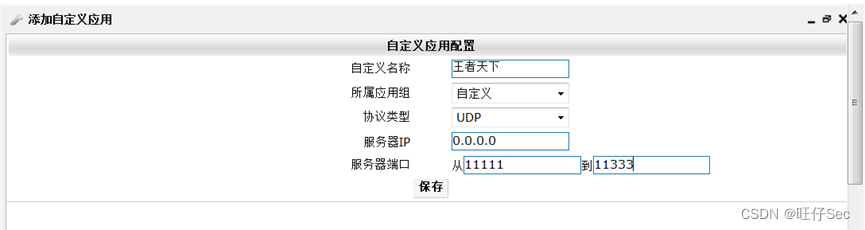
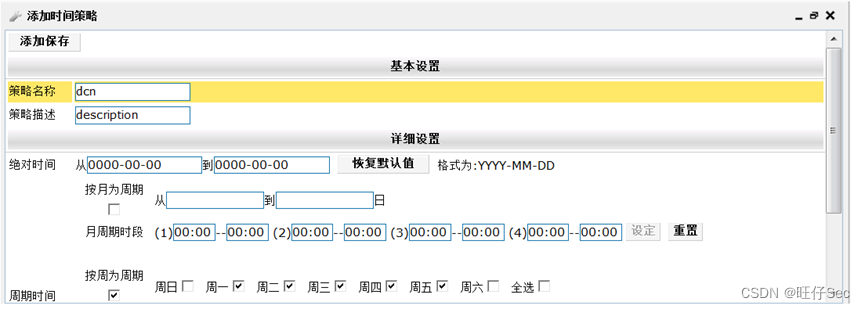
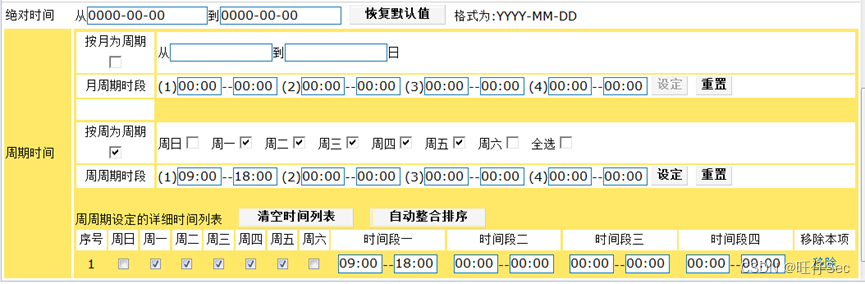
- DCBI Configure applications and application groups “ The king of the world ”,UDP Protocol port number range 11111-11333, From Monday to Friday 9:00-18:00 monitor LAN Of all users in “ The king of the world ” Access records ;(12 branch , Deduct every mistake 4 branch )
边栏推荐
- 服装门店如何盈利?
- Installing redis and windows extension method under win system
- 【解决】Final app status- UNDEFINED, exitCode- 16
- 根据IP获取地市
- 大促过后,销量与流量兼具,是否真的高枕无忧?
- JWT 认证
- dolphinscheduler3.x本地启动
- Handling hardfault in RT thread
- How can I check the DOI number of a foreign document?
- C language (structure) defines a user structure with the following fields:
猜你喜欢
POI export to excel: set font, color, row height adaptation, column width adaptation, lock cells, merge cells

LM small programmable controller software (based on CoDeSys) Note 23: conversion of relative coordinates of servo motor operation (stepping motor) to absolute coordinates
Installing redis and windows extension method under win system

Programmers' daily | daily anecdotes
JESD204B时钟网络

项目实战 五 拟合直线 获得中线
企業如何進行數據治理?分享數據治理4個方面的經驗總結
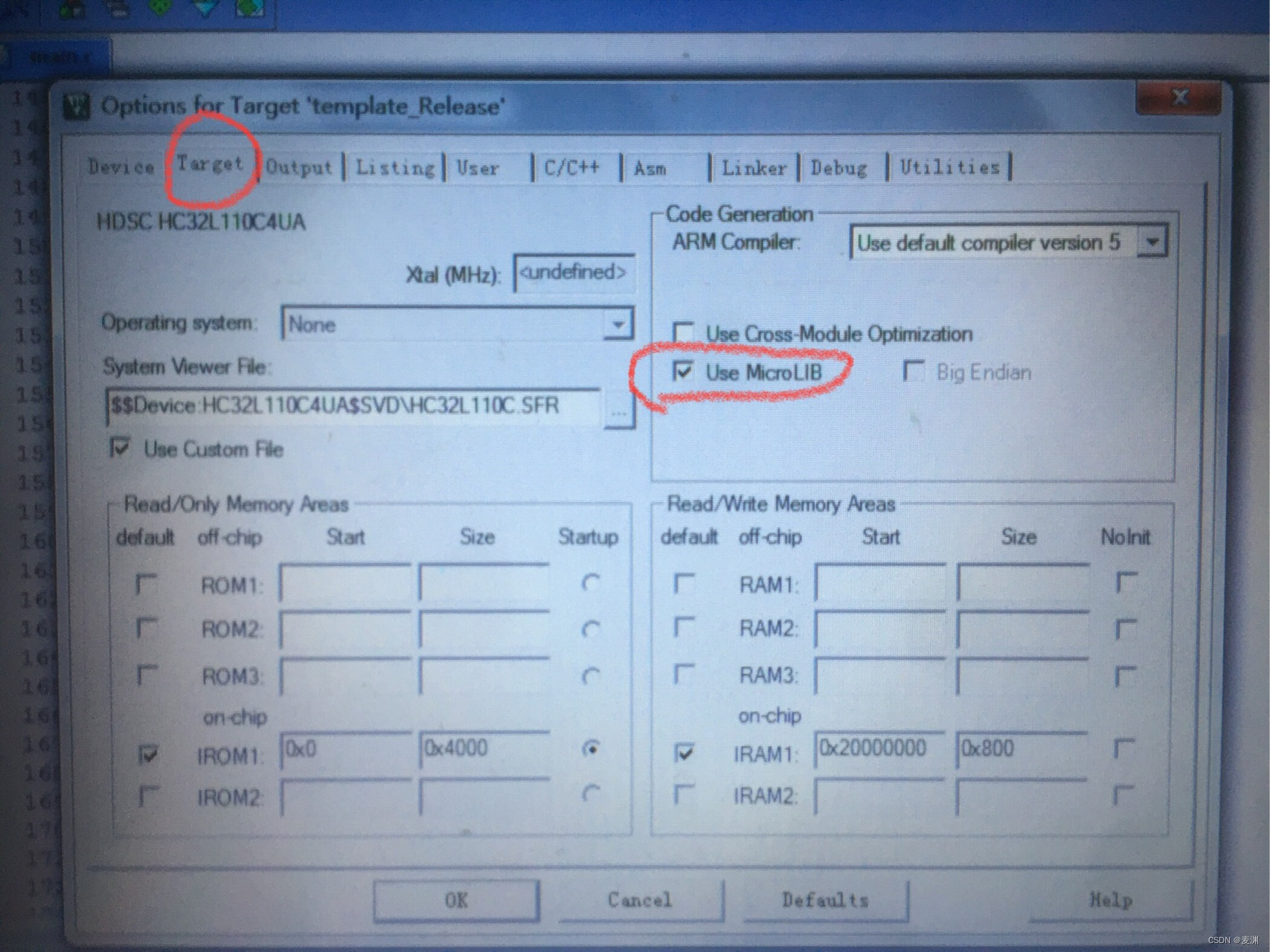
屏幕程序用串口无法调试情况
【从零开始】win10系统部署Yolov5详细过程(CPU,无GPU)

服装门店如何盈利?
随机推荐
Installing redis and windows extension method under win system
VIM mapping large K
C interview 24 (pointer) define a double array with 20 elements a
中英文说明书丨ProSci LAG-3 重组蛋白
品牌电商如何逆势增长?在这里预见未来!
Haqi projection Black Horse posture, avec seulement six mois de forte pénétration du marché des projecteurs de 1000 yuans!
ICML 2022 | 探索语言模型的最佳架构和训练方法
屏幕程序用串口无法调试情况
隐马尔科夫模型(HMM)学习笔记
from .onnxruntime_pybind11_state import * # noqa ddddocr运行报错
Abnova 免疫组化服务解决方案
网络基础 —— 报头、封装和解包
leetcode 509. Fibonacci Number(斐波那契数字)
基于JS的迷宫小游戏
Stack and queue-p78-8 [2011 unified examination true question]
Unable to debug screen program with serial port
What are the classic database questions in the interview?
ceres-solver和g2o性能比较
MySql用户权限
2022/07/04学习记录