当前位置:网站首页>File upload Labs
File upload Labs
2022-07-02 08:27:00 【Defeat of Fujiwara Qianhua】
List of articles
Preface
upload-labs It's a use php language-written , Specifically collect penetration tests and CTF Various upload vulnerabilities encountered in the shooting range . It aims to help you have a comprehensive understanding of the upload vulnerability . At present, a total of 20 Turn off , Each level contains different upload methods
One 、 What is the file upload vulnerability ?
Web In the application , File uploading is a common functional requirement , For example, users upload member avatars
If the uploaded files are not verified and filtered , Attackers can upload malicious scripts , To achieve the purpose of an attack .
Two 、 Common upload detection rules
- client JS testing
- Server file extension detection ( Black and white list )
- Server side MIME Type detection (HTTP First line content-type Field )
- Server directory path detection ( testing path Sensitive keywords in parameters )
- Server file content detection ( Check file content )
3、 ... and 、 Bypass
The target contains vulnerability type classification
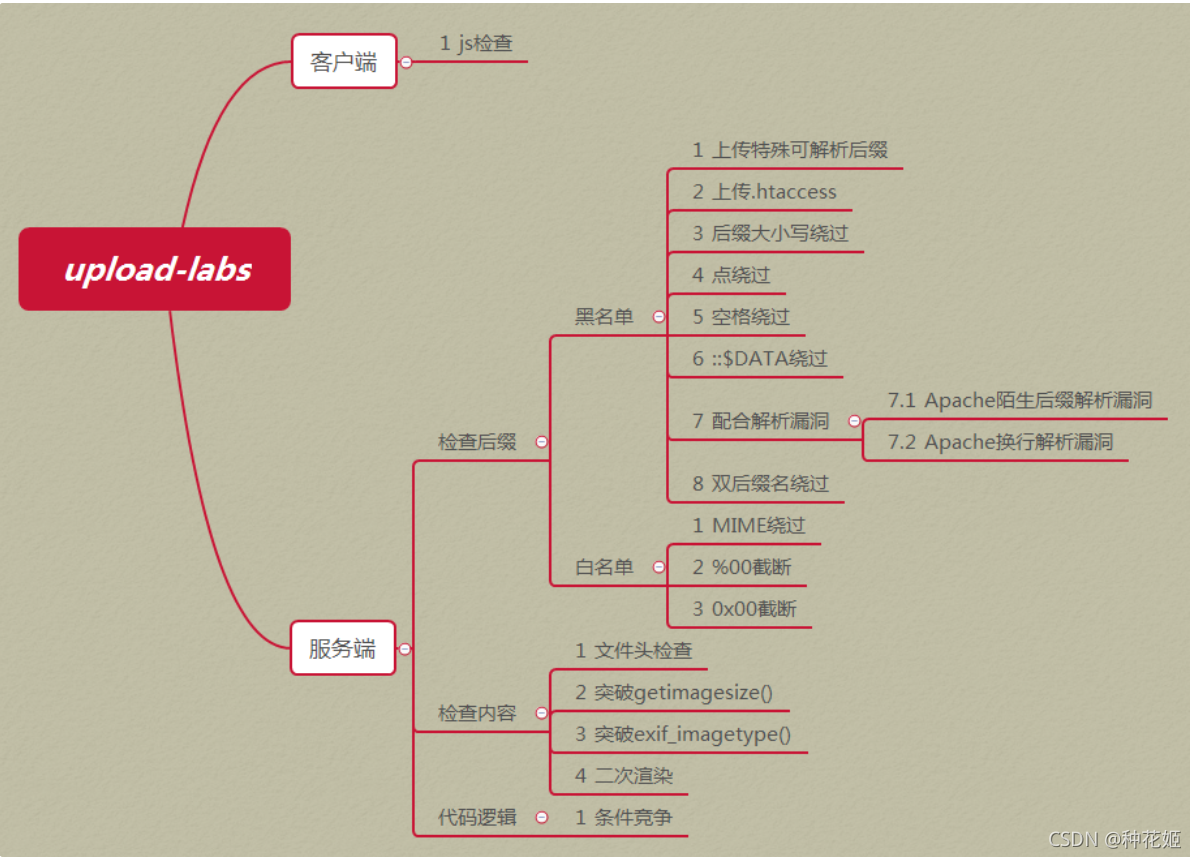
How to determine the type of upload vulnerability

Four 、 The first 1 Turn off
- Upload a 1.php file , Page echo
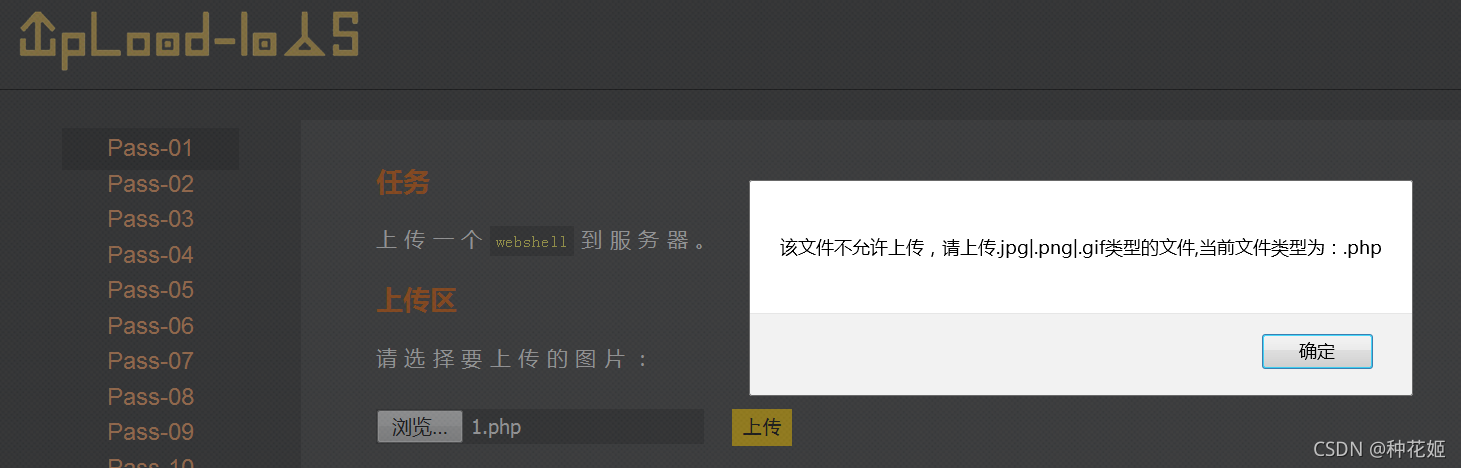
- Even if you can't pass the above “ Echo... Soon ” To judge , You can also try grabbing , You can't catch it , Check the source code of the page and you will find
function checkFile() {
var file = document.getElementsByName('upload_file')[0].value;
if (file == null || file == "") {
alert(" Please select the file to upload !");
return false;
}
// Define the types of files allowed to be uploaded
var allow_ext = ".jpg|.png|.gif";
// Extract the type of uploaded file
var ext_name = file.substring(file.lastIndexOf("."));
// Determine whether the type of uploaded file is allowed to be uploaded
if (allow_ext.indexOf(ext_name + "|") == -1) {
var errMsg = " The file is not allowed to upload , Please upload " + allow_ext + " Files of type , The current file type is :" + ext_name;
alert(errMsg);
return false;
}
}
- Just disable the script , You can bypass the detection
5、 ... and 、 The first 2 Turn off
- Upload an illegal file , The echo

- Can catch packets , The description is backend authentication . Ahead of 1.php Renamed 1.png Upload successful . There are many ways of back-end verification , Without source code , Only by experience black box test .

Revised MIME type , namely conten-type, Upload successful , And successfully resolved

边栏推荐
- Comparison between setTimeout and requestanimationframe (page refresh)
- 力扣方法总结:滑动窗口
- Use Wireshark to grab TCP three handshakes
- sqli-labs第8关(布尔盲注)
- Opencv3 6.3 reduced pixel sampling with filters
- Use of OpenCV 6.4 median filter
- VS Code配置问题
- STL速查手册
- One of the reasons for WCF update service reference error
- Carsim-问题Failed to start Solver: PATH_ID_OBJ(X) was set to Y; no corresponding value of XXXXX?
猜你喜欢

Data reverse attack under federated learning -- gradinversion
方法递归(斐波那契数列,青蛙跳台阶,汉诺塔问题)
Matlab mathematical modeling tool

Intelligent manufacturing solutions digital twin smart factory
C language implements XML generation and parsing library (XML extension)
Opencv3 6.3 reduced pixel sampling with filters

Simple implementation scheme of transcoding and streaming (I)

Fundamentals of music theory (brief introduction)
Vs code configuration problem

Animation synchronization of CarSim real-time simulation
随机推荐
Erase method in string
Use of opencv3 6.2 low pass filter
使用Matplotlib绘制图表初步
Global and Chinese market of snow sweepers 2022-2028: Research Report on technology, participants, trends, market size and share
SQL operation database syntax
Mutex
Global and Chinese markets for Salmonella typhi nucleic acid detection kits 2022-2028: Research Report on technology, participants, trends, market size and share
Longest isometric subsequence
用数字 5,5,5,1 ,进行四则运算,每个数字当且仅当用一次,要求运算结果值为 24
Causes of laptop jam
Global and Chinese market of medicine cabinet 2022-2028: Research Report on technology, participants, trends, market size and share
力扣每日一题刷题总结:栈与队列篇(持续更新)
ICMP协议
File upload and download performance test based on the locust framework
Short video with goods source code, double-click to zoom in when watching the video
What are the platforms for selling green label domain names? What is the green label domain name like?
Use Matplotlib to draw a preliminary chart
旋转链表(图解说明)
樂理基礎(簡述)
On November 24, we celebrate the "full moon"