当前位置:网站首页>Honeypot attack and defense drill landing application scheme
Honeypot attack and defense drill landing application scheme
2022-07-02 08:30:00 【Chengdu knows Chuangyu】
2022 The actual combat drill of the year of attack and defense is imminent , Honey pot presents a copy for you in preparation for the war “ hardcore ” Sharing of landing application solutions , Help you clear your mind , Efficient “ Prepare for war ”.
Next , It will be combined with years of experience in network attack and defense , Summarize the attack path with the highest frequency launched by the attacker in the attack and defense drill scenario , For these potential problems , Formulate corresponding active defense strategies one by one , Respond effectively .
For information collection
Path analysis : Attackers usually take advantage of Information disclosure platform Such as GitHub、 Code cloud 、 Baidu SkyDrive 、 Internet portals such as cyberspace search engines , And try Use information to mine vulnerabilities .
Coping strategies :
1、 Build traps : By constructing Sensitive words 、 Non critical source code 、 System profile Such information honeypot system as a trap to attract attackers to visit .
2、 Drop bait : When delivering bait information , Consider using the browser ID The probability of success in traceability is higher , More bait can be delivered to the relevant information sharing platform .
Plant points for the system
Path analysis : The attacker obtains the target asset information or account information through information collection , Will choose to be familiar with the system Looking for weaknesses .
Coping strategies : Highly simulated key systems : Around the real business system simulation of the enterprise that the attacker focuses on during the attack and defense drill , The offline historical business system can be re launched into the honeypot system , Induce the attacker to stay .
Simulate customized high simulation scenarios : These domain name websites are maintained manually, such as adding interactive pages 、 Regularly publish group announcement information 、 Regular background login and management Build high simulation scenarios .
For intranet horizontal attacks
Path analysis : The attacker is supposed to pass 0day You can enter the intranet by other means , Due to the acquisition of The corresponding score of the defender's path is great , Path layout 、 Intranet horizontal attack is often a necessary attack process in attack and defense drills .
Coping strategies :
1、 Timely attack perception : Intranet Deploy as many perceptual honeypots as possible , It can be done by trunk The way to idle IP binding , To cover all areas of the intranet for attack awareness .
2、 Key points deploy honeypots : To prevent attackers from directly touching the real host or operation and maintenance terminal through the host access log , Some open ports on the host at the key node should be bound to the honeypot .
Sensitive information induces attacks : Can forge login domain credentials 、RDP Connection record 、 Operation and maintenance log 、 User folders 、 Browser browsing records and related sensitive information content to tempt attackers to attack .
For real-time attacks
Attack analysis : Attackers launch real-time attacks , The defender needs to block the attack 、 Record attack information 、 Analyze the attack path 、 Trace competitor information . These are not just data information that can be competent , It must rely on the attack perception of its own products 、 Ability to record , It also needs to expand its collaborative defense capabilities with security products 、 Combined with the traceability of security big data 、 Character portrait ability .
Coping strategies : Attack redirection
Network attack detection : Honeypot monitors whether the network environment has attack traffic in real time .
Attack stream redirection : The redirection of attack flow is introduced into the deployment of honeypot system , Realize the security isolation between attack activities and customer network environment , Ensure the security of customers' network environment .
Attack analysis
Applied analysis : Master the attack information of the attacker , And attack tools for attackers 、 route 、 After further analysis of intention, we can find our own system and defense vulnerabilities , Targeted leak detection and filling .
Coping strategies : Vulnerability simulation
Simulation scenario upgrade : Based on the largest and richest vulnerability knowledge base in China Seebug, Pass regularly POC Upgrade the simulation scene in the honeypot device .
Simulation vulnerability settings : Honeypot system can be injected with newer vulnerabilities 、 Simulation scenarios tailored to business services and application requirements , Lure the intruder to detect the honeypot and extend the residence time , Accurately capture high-risk hacker attacks , Protect customers' business systems .
Trace the source of the attack
Applied analysis : The biggest advantage of honeypot application in attack and defense drill scenarios is to take attack as defense , Traceability score .
Coping strategies : Attack real-time forensics
Get virtual identity : Obtain attack behavior data for classification and traceability , Realize deep traceability and reverse osmosis , Attackers including social media identities can be obtained IP、IM communication tools ID Wait for more personal information .
Related threat intelligence : Attackers often use VPN/ Proxy and other means to initiate access requests , Honeypot can obtain the attacker's truth through its integrated rich traceability plug-ins IP. Honeypot against every attack source IP Will create a unique fingerprint for marking , Even if the attacker tampers IP The attack behavior can also be analyzed through the effective correlation of fingerprints , And synchronize the information obtained at this stage to the safe brain 、 Tencent Threat Intelligence and other big data platforms , Build an accurate 、 Comprehensive Threat Intelligence .
Practical deployment skills
1、 Subregional deployment
Honeypots provide Locally aware honeypot and Cloud trap honeypot Two regional deployment methods , At the same time, it supports combined use .
Locally aware honeypot : Deployed in the enterprise intranet area and the core exchange area , Perceive and discover the attacker , And kick it out of the intranet area as soon as possible .
Cloud trap honeypot : Deployed in the public cloud area hosting the enterprise business system , By trapping honeypots 、 Collect attacker information by delivering bait and other means , Effectively track and trace the attacker , And real-time monitoring of Extranet domain name detection and scanning operations .
2、 System simulation application
Deploy the honeypot simulation system around the business application system that the attacker focuses on during the attack and defense drill and the real business system of the enterprise .

3、 Network environment requirements
Honeypot management website opens the designated port , For administrators SSH Log in to the system for management 、 Page access uses 、 Probe and one-way encrypted channel of Management Center .

Honeypot probe : To ensure better perception , It is recommended not to restrict the port of the probe website .
4、 Deploy and implement the overall process

5、“ Sweetness ” Add plans
Honeypot in order to improve the construction of protective capacity 、 Control in advance , Achieve the purpose of making the honeypot more highly simulated and tempting attackers , Yes, honey pot “ Sweetness ” Relevant plans have been formulated .

Offensive and defensive confrontation itself is an asymmetric technological game , Blindly carry out passive defense , Even if the defense measures are continuously improved , It often only increases resource input and cost , It doesn't have a better effect , Instead, it always bears the risk of system and information being destroyed and stolen .
Honeypot landing application scheme for pure dry goods , You can contact Xiaobian to get ~
边栏推荐
- When a custom exception encounters reflection
- Using C language to realize MySQL true paging
- OpenCV3 6.3 用滤波器进行缩减像素采样
- Matlab数学建模工具
- Global and Chinese markets for conventional rubber track 2022-2028: Research Report on technology, participants, trends, market size and share
- Learning C
- Longest isometric subsequence
- 力扣每日一题刷题总结:字符串篇(持续更新)
- Constant pointer and pointer constant
- How to back up the configuration before the idea when reinstalling the idea
猜你喜欢

When a custom exception encounters reflection
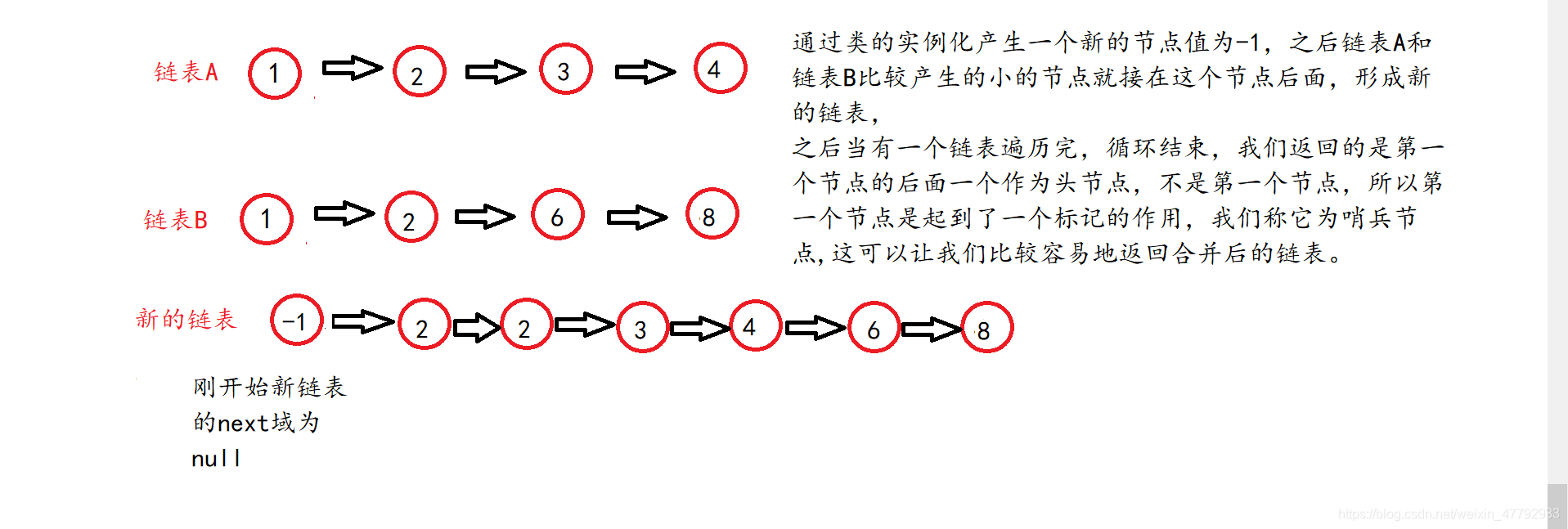
链表经典面试题(反转链表,中间节点,倒数第k个节点,合并分割链表,删除重复节点)
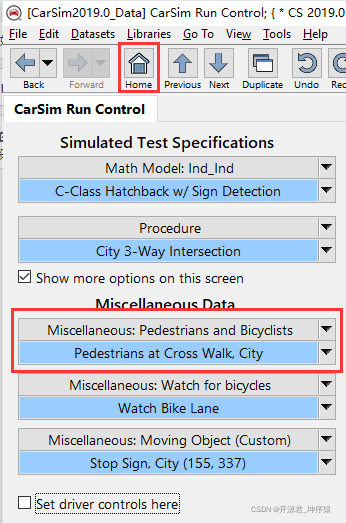
Carsim-問題Failed to start Solver: PATH_ID_OBJ(X) was set to Y; no corresponding value of XXXXX?
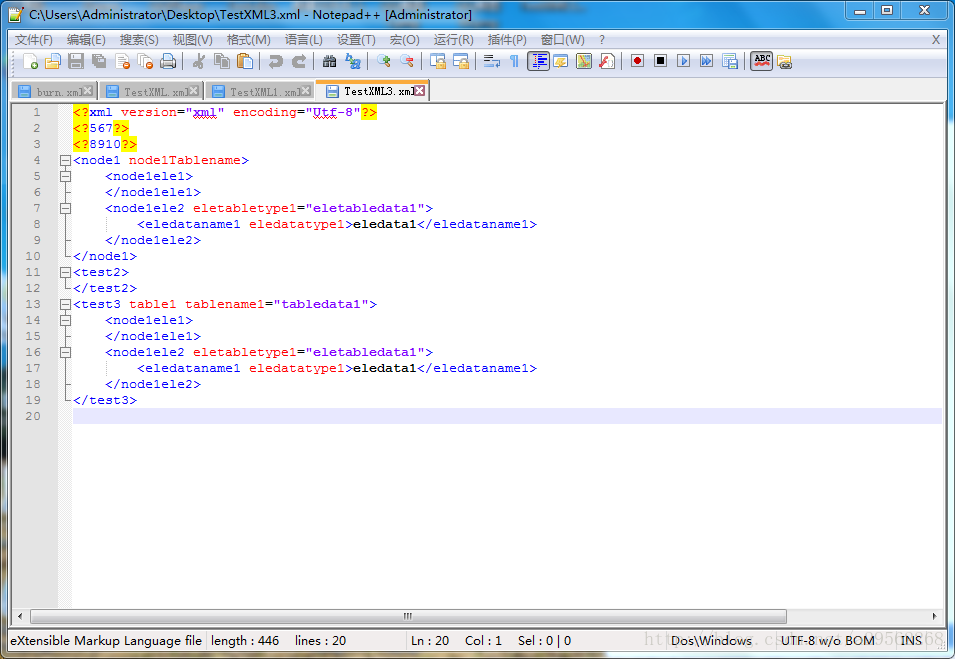
C language implements XML generation and parsing library (XML extension)

Principes fondamentaux de la théorie musicale (brève introduction)

Smart agriculture solutions smart agriculture system development
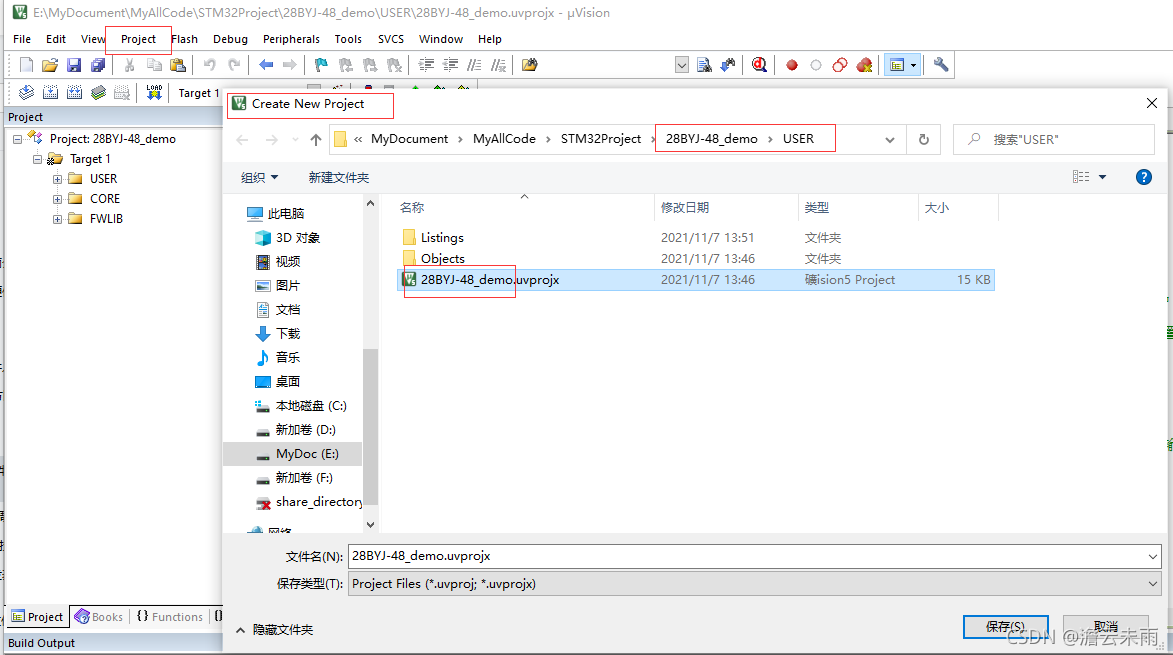
STM32 new project (refer to punctual atom)

Simple implementation scheme of transcoding and streaming (I)
Carla-ue4editor import Roadrunner map file (nanny level tutorial)
Use the kaggle training model and download your own training model
随机推荐
Carsim-问题Failed to start Solver: PATH_ID_OBJ(X) was set to Y; no corresponding value of XXXXX?
What is SQL injection
Matlab数学建模工具
2022 Heilongjiang latest food safety administrator simulation exam questions and answers
Comparable,Comparator,Clonable 接口使用剖析
2022 Heilongjiang latest construction eight members (materialman) simulated examination questions and answers
Routing foundation - dynamic routing
Principes fondamentaux de la théorie musicale (brève introduction)
Don't know mock test yet? An article to familiarize you with mock
How to apply for a secondary domain name?
Use of OpenCV 6.4 median filter
idea中注释代码取消代码的快捷键
Programming ape learning English - imperative programming
Force deduction method summary: double pointer
Method recursion (Fibonacci sequence, frog jumping steps, tower of Hanoi problem)
Common shortcut keys of Jupiter notebook (you can also view it by pressing h in command mode)
力扣方法总结:查找类
STL quick reference manual
Wang extracurricular words
OpenCV 6.4 中值滤波器的使用