当前位置:网站首页>Use Wireshark to grab TCP three handshakes
Use Wireshark to grab TCP three handshakes
2022-07-02 08:24:00 【Ischanged】
List of articles
wireshark Download and install
The software can be downloaded directly from the official website wireshark, Just choose the appropriate version of your computer .
But it's not recommended , The reason is that the visiting speed of foreign websites is too slow , When I was writing my blog, I went to the official download and couldn't download the installation package , Then I went to Sogou to download an installation package , Installation , Click Install Package all the way next Installation , I will explain separately what needs attention during installation .
Reading permission :
Check the following options , Some defaults are not checked :
TCP A brief introduction to the format of the Protocol segment
TCP, namely Transmission Control Protocol, Transmission control protocol . A man is his name , To carry out a detailed control of data transmission .
TCP The features of the agreement :
There is a connection
Byte stream oriented ( In data transmission engineering, one byte is the basic unit )
Reliable transmission ( After the sender sends data to the receiver , The sender responded , Tell the receiver that the data has been received )
full duplex ( Sending and receiving can send data at the same time , Data may also have been received )
TCP Protocol segment format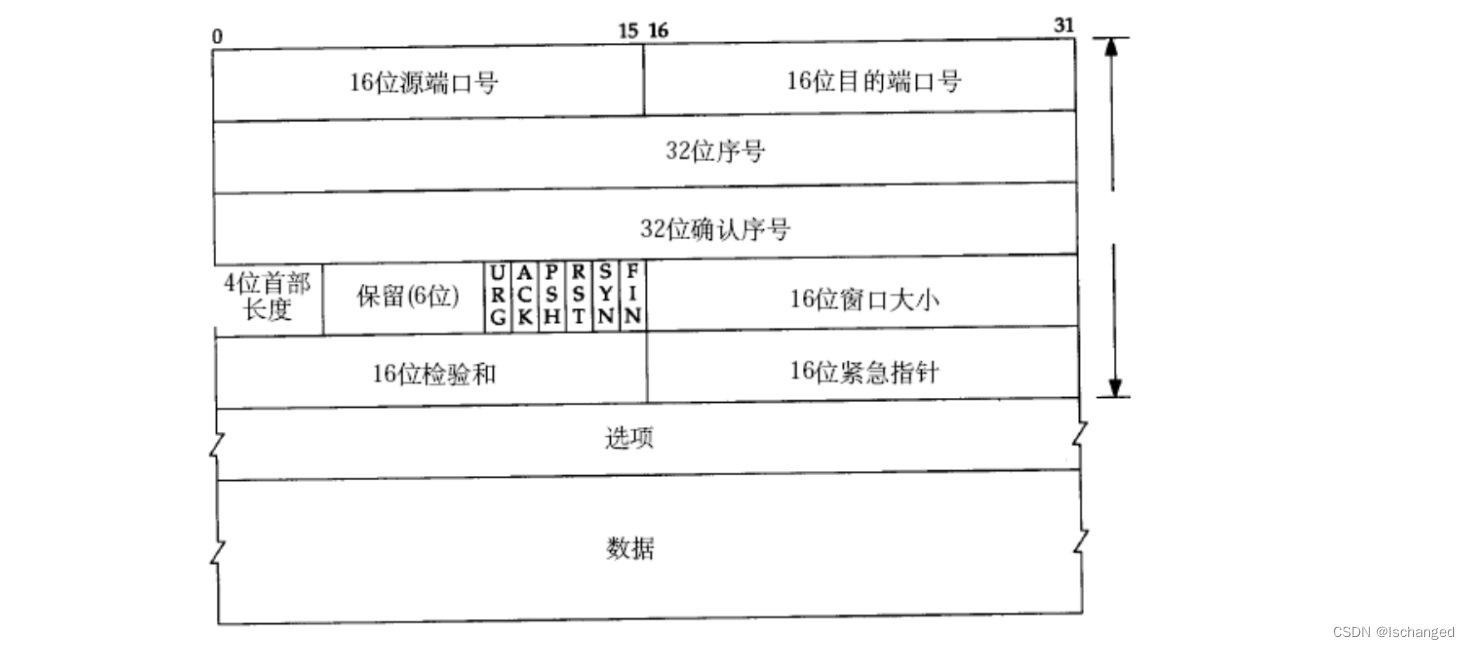
Source / Destination port number : Indicates which program of a host the data comes from , Which program of another host to go to .
32 Bit number , Number the data to be transmitted , Each byte corresponds to a sequence number , Accumulate in turn
32 Bit confirmation number , After receiving the data , Return an acknowledgement datagram , It contains a confirmation number , It means that the data receiver before the confirmation number has received ,TCP The serial number and confirmation serial number in the datagram are the guarantee TCP An important way of reliable transmission .
4 Bit head length , The unit is 4 Bytes , that TCP The maximum data size of the header is 60 Bytes .
Reserve a place for other purposes , Used after TCP Iterative update of the Protocol .
6 Bit flag bit :
URG: Is the emergency pointer valid
ACK: with ACK The identified datagram is called an acknowledgement segment
PSH: Prompt the receiving application to immediately start from TCP The buffer reads the data away
RST: The other side asked to reestablish the connection ; We carry RST The identified is called the reset message segment
SYN: Request to establish a connection ; We carry SYN The identified message is called a synchronous segment
FIN: Inform the other party , This end is closing , We call carrying FIN The marked is the end message segment
The six flag bits above are TCP The six bits in the header , By default 0, When used, it becomes 1 了 .
Other fields are not introduced in this blog .
Introduction to confirmation and response mechanism
TCP The core feature of the protocol is reliability , The core mechanism to ensure reliability is the confirmation response mechanism ,TCP Many mechanisms are used to ensure reliability and efficiency , There is a confirmation response , Over time retransmission , Connection management ( Three handshakes , Four waves ), The sliding window ( Ensure efficiency ) etc. . Now let's introduce the confirmation response, which is helpful to understand connection management .** Because the network transmission environment is complex and diverse , Lead to unreliability of data transmission , If it comes later, it is a case ,** Here's the picture : I sent them to my friend Xiao Ming respectively , Two datagrams , The meaning of arriving successively is completely different ,
What Xiao Ming wanted to express was , I invited him to drink milk tea ok, Get out of your homework , However, due to the complexity and diversity of the network environment , The datagram it sent to me was sent first and then to , It's caused , I invited him to drink milk tea and roll , do the homework ok, In this way, the meaning of both sending parties will change ,** So we can send datagrams , Just number each byte of each datagram , This number is called serial number , After receiving the data, the receiver sends a confirmation message segment , There is also a confirmation sequence number for the sender's sending sequence number in the confirmation message segment , Confirm the received data through this confirmation serial number , This confirmation number is also TCP A field in the header ,** In this way, this chaotic situation can be avoided .
I have already introduced tcp The basic unit of transmitted data is bytes , Instead of transmitting data one by one as I drew casually above .tcp Number each byte of data . The maximum range of numbers is 32 The maximum range represented by bits , As shown in the following figure, you can have a simple look 
The number range of the above datagram is from 1 Numbered starting , But not necessarily , You can also use other numbers for initial numbering .TCP The confirmation and response mechanism of is roughly shown in the figure below :
After the above simple understanding TCP After the relevant knowledge, we can grab the package .
Use wireshark Grab TCP Three handshakes of
First of all, we should be clear about the process of three handshakes , It's roughly as follows .
Click on WLAN Choose our network card , Our host communicates with other hosts through this network card , Grab the data through this network card TCP Three handshakes analysis .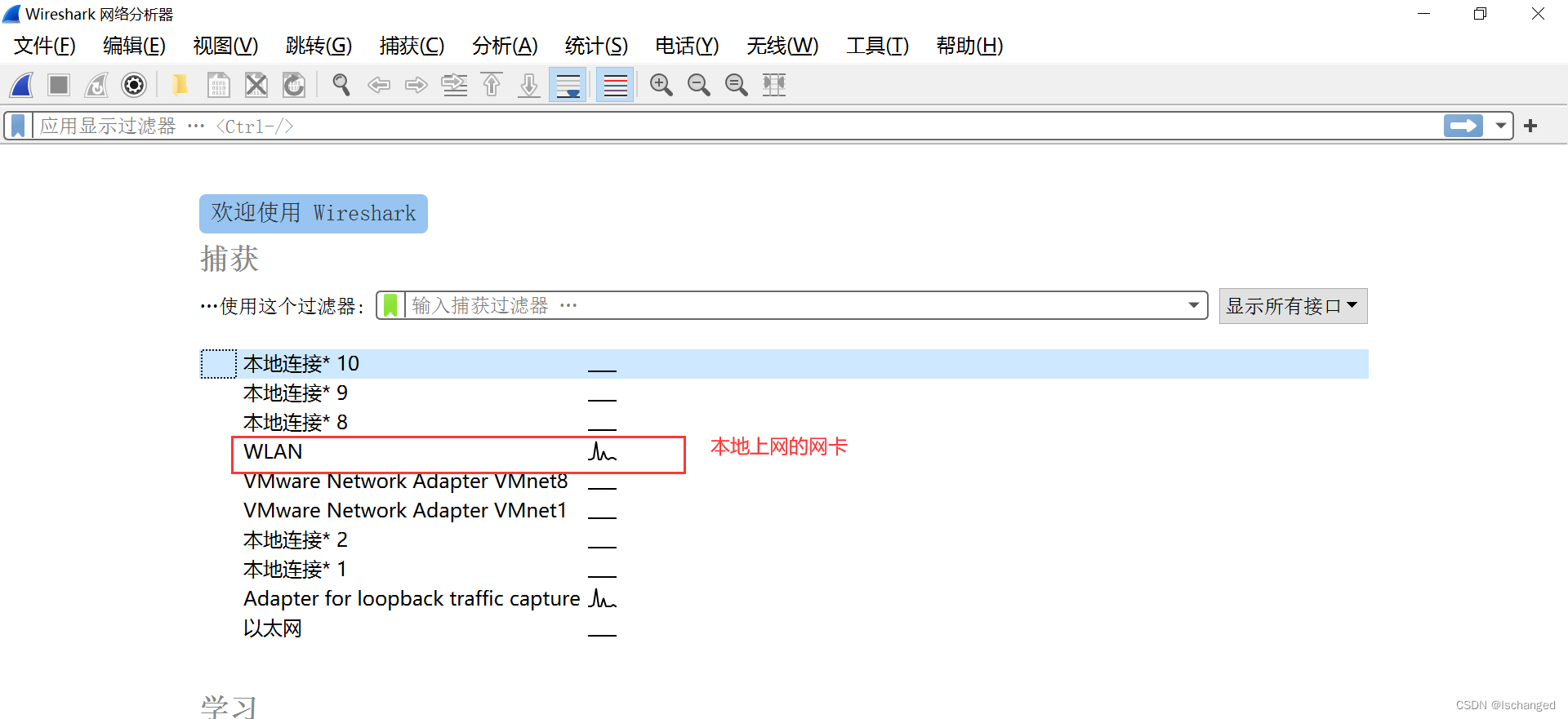
I grab LeetCode For example, website , First of all, I'm in dos window , adopt ping command , To get LeetCode Website ip After the address, it is used in wireshark It is used for data filtering and analysis .
open wireshark Click on the blue shark fin , Start capturing new groups and emptying previous groups , Start Bo capture 
Then quickly access in the browser LeetCode Website , After the wireshark Stop capturing packets for data analysis , Stop capturing groups and click the square on the right of the start capturing group , It is red before the capture is stopped , After stopping capturing, it will be gray . Then filter the data , Because our host may transmit data between many processes of different hosts at the same time, and also interact with different processes of the same host , Filtering data is helpful for data analysis .
After capture pause , I am here wireshark Enter ip.addr == 203.107.53.81 and tcp To filter , Filter out tcp agreement ,ip Address and 203.107.53.81 Related packets , Filter as shown in the figure .
As you can see from the picture ,TCP It seems that several handshakes have been established , But that's the different process of my host and LeetCode The server port number of the website is 443 Process to communicate , I only select one of the processes for analysis . Select port number 51175 Process analysis .TCP An important purpose of the triple handshake is to determine the good sending and receiving ability of the communication dual transmitter and to agree on some parameters , Such as the determination of the initial serial number , The explanation of serial number and confirmation serial number is in TCP The format of the protocol section is introduced there .
The first handshake :Seq=0, The initial serial number is 0, That is, the number of the first byte of the data to be transmitted is 0, In fact, it's not for 0, It's just wireshark This software helps us set the relative serial number , The client first sends a SYN Message segment requests to establish connection , Then the value of this field becomes 1, Then we can also wireshark Observe . For transmitted data , Fields in the data header SYN,ACK And value can also be in wireshark Seen inside , If the corresponding field is marked Set Indicates the value set , Otherwise, the value is not set . If you look at the first handshake SYN value , Click on tcp agreement , Click again Flags You can see .

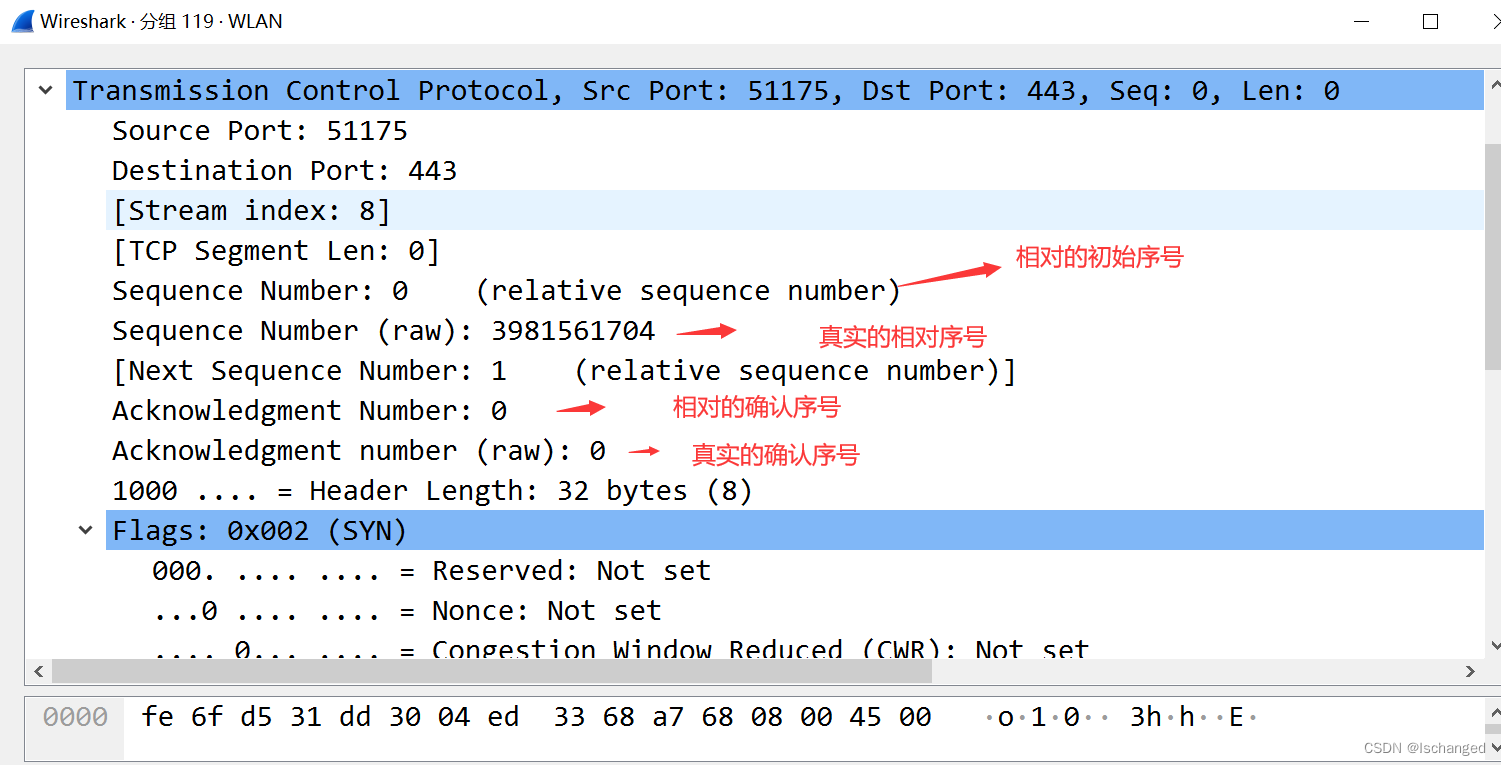
The second handshake : The server sends... To the client SYN( Synchronization segment ),ACK( Confirm message segment ) And the values are activated to 1, The synchronous message segment indicates that the server should establish a connection with the client , Confirm message segment , Indicates that the server has received a request from the client , Tell the client . So the initial sequence number of the second handshake Seq=0 It is also a relative serial number , The server returns a confirmation serial number Ack=0+1, Indicates that the data number sent by the client is 0 The data server of has received , And ask the client for the next packet .wireshark The screenshot analysis is as follows :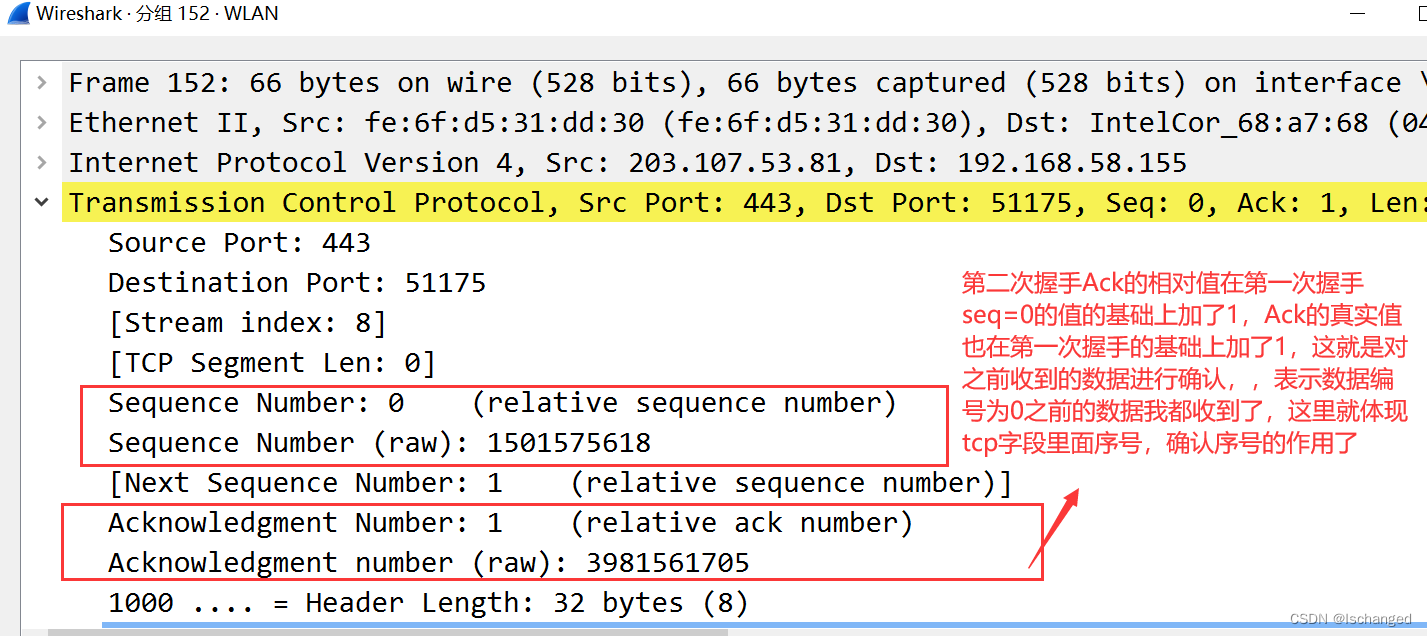
The third handshake , The client returns a ACK Confirm message segment , It means to confirm receiving the data sent by the client , The confirmation sequence inside Ack=0+1 The value of 1, Indicates that the serial number sent by the server is 0 The data of ,wireshark The data analysis diagram is as follows :
( Explain the above TCP In the figure of establishing connection ack And what I said here Ack In fact, it all refers to one thing , Is to confirm the serial number ,Ack This is a wireshark What's inside ,seq,Seq Is the initial data serial number , It just means different , Different materials , The article is different )
thus TCP Three handshakes completed , Subsequent data transmission is possible . Use the bag grabbing tool to grab tcp Three handshakes of , It can deepen our understanding of the protocol format , and tcp Understanding of some mechanisms .
边栏推荐
- 程序猿学英语-指令式编程
- Summary of one question per day: String article (continuously updated)
- Library function of C language
- Matlab - autres
- Array and string processing, common status codes, differences between PHP and JS (JS)
- 程序猿学英语-Learning C
- C语言实现XML生成解析库(XML扩展)
- Introduction to parameters of CarSim pavement 3D shape file
- Matlab mathematical modeling tool
- Carla-UE4Editor导入RoadRunner地图文件(保姆级教程)
猜你喜欢

Data reverse attack under federated learning -- gradinversion
On the back door of deep learning model

Animation synchronization of CarSim real-time simulation

2022 Heilongjiang's latest eight member (Safety Officer) simulated test question bank and answers
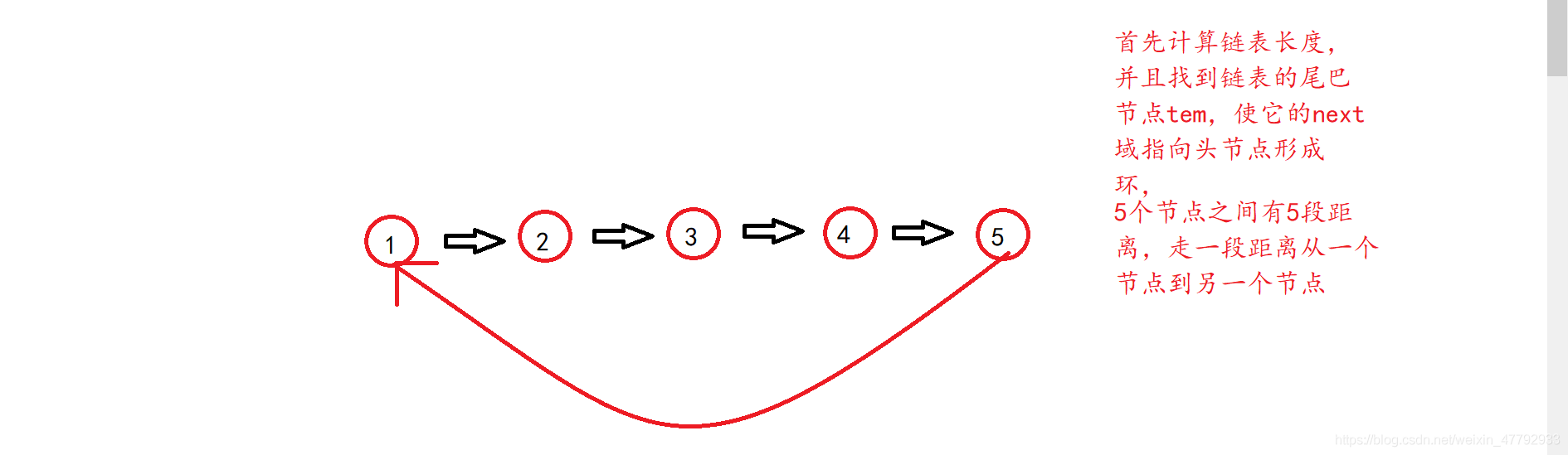
旋转链表(图解说明)
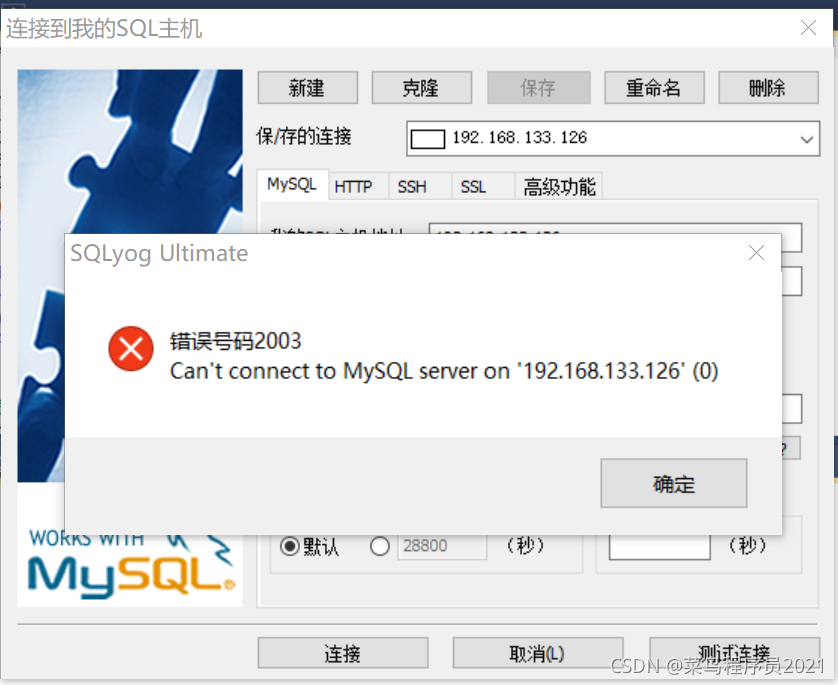
SQLyog远程连接centos7系统下的MySQL数据库

Fundamentals of music theory (brief introduction)

使用Matplotlib绘制图表初步
Carsim 学习心得-粗略翻译1

Sqlyog remote connection to MySQL database under centos7 system
随机推荐
On the confrontation samples and their generation methods in deep learning
Summary of one question per day: String article (continuously updated)
Introduction to parameters of CarSim pavement 3D shape file
常量指针和指针常量
c语言自定义类型枚举,联合(枚举的巧妙使用,联合体大小的计算)
学习写文章格式
MySQL优化
Introduction to anti interception technology of wechat domain name
Vscode下中文乱码问题
Generate database documents with one click, which can be called swagger in the database industry
How to wrap qstring strings
Global and Chinese market of electric cheese grinder 2022-2028: Research Report on technology, participants, trends, market size and share
Carsim-問題Failed to start Solver: PATH_ID_OBJ(X) was set to Y; no corresponding value of XXXXX?
Jumping | Blue Bridge Cup
STL速查手册
Implementation of bidirectional linked list (simple difference, connection and implementation between bidirectional linked list and unidirectional linked list)
OpenCV3 6.2 低通滤波器的使用
高中数学必修一
Carsim-问题Failed to start Solver: PATH_ID_OBJ(X) was set to Y; no corresponding value of XXXXX?
Causes of laptop jam