当前位置:网站首页>Process of manually encrypt the mass-producing firmware and programming ESP devices
Process of manually encrypt the mass-producing firmware and programming ESP devices
2022-07-04 20:04:00 【25March】
The requirements are as follows
Encrypting the mass-produced firmware, after encryption you can use the tool to erase the old firmware, and it support repeated flashing the firmware.
Required tools:
- esptool , you can refer to Introduction and use of esptool.py
- Flash download tool
Reference Documentation:
solution
Specify the Flash encryption key (
key.bin), i.e. each module uses the same Flash encryption key (key.bin). Firstly using the Flash encryption key (key.bin) to encrypt the separate binary plaintext firmware that compiled by project, then you can flash the encrypted ciphertext firmware directly using the Flash Download Tool. After the ciphertext firmware flashed, you need to use esptool to falsh the Flash encryption key (key.bin) to the Efuse, then turn on the Control Bit of Flash Encryption in Efuse to make sure the encrypted firmware boots properly. The steps are as follows:
1 Use the esptool tool to generate a Flash encryption key (key.bin) for production firmware, for example, the generated encryption key is key.bin:
espsecure.py generate_flash_encryption_key key.bin
2 Encrypt each firmware (bin file) to be flashed, using the hello-world as an example
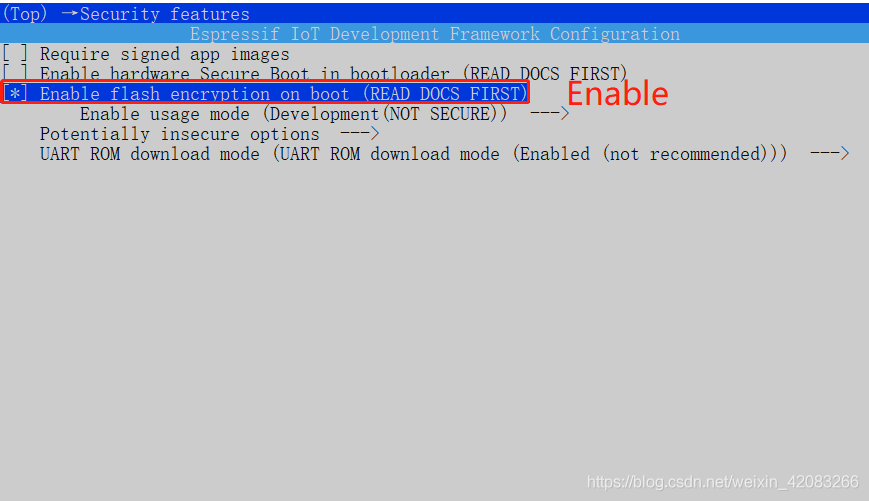
- **Turned on the Flash encryption option in menuconfig, as follows: **
menuconfig -> Security features -> Enable flash encryption on boot
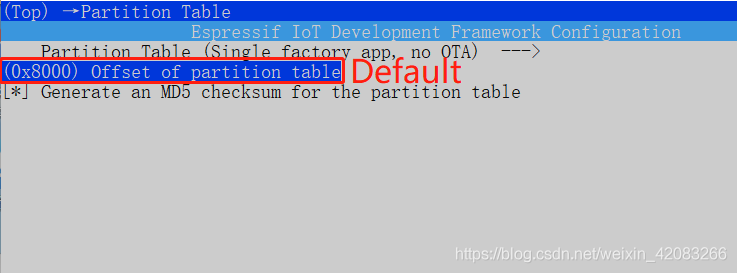
- **Since Flash encryption increases the size of the bootloader .bin firmware, the offset of the default partition table needs to be adjusted, which is 0x8000, can be adjusted to 0xa000. You can modify the settings for partition_table in menuconfig. As follows: **
menuconfig -> Partition Table -> Offset of partition table
- Then compile the project and check the firmware download address corresponding to the compiled firmware. You can find that the download address of hello-world.bin becomes 0x20000
Project build complete. To flash, run this command:
E:.espressif\python_env\idf4.3_py3.8_env\Scripts\python.exe …\components\esptool_py\esptool\esptool.py -p (PORT) -b 460800 --before default_reset --after no_reset --chip esp32c3 write_flash --flash_mode dio --flash_size detect --flash_freq 80m 0x0 build\bootloader\bootloader.bin 0xa000 build\partition_table\partition-table.bin 0x20000 build\hello-world.bin
or run ‘idf.py -p (PORT) flash’
3 Using the generated Flash encryption key (key.bin file) to encrypt each individual firmware (bin file) that compiled by project. As follows:
- ) to encrypt bootloader.bin, and the encrypted bootloader.bin becomes key_bootloader.bin**
espsecure.py encrypt_flash_data --keyfile key.bin --address 0x1000 -o key_bootloader.bin build/bootloader/bootloader.bin
- Using the generated Flash encryption key (
key.bin) to encrypt partition-table.bin, and the encrypted partition-table.bin becomes key_partition-table.bin
espsecure.py encrypt_flash_data --keyfile key.bin --address 0xa000 -o key_partition-table.bin build/partition_table/partition-table.bin
- Using the generated Flash encryption key (
key.bin) to encrypt hello_world.bin, and the encrypted hello_world.bin becomes key_hello-world.bin
espsecure.py encrypt_flash_data --keyfile key.bin --address 0x20000 -o key_hello-world.bin build/hello_world.bin
4 **According to the corresponding download address of the firmware compiled by project, program the encrypted firmware (encrypted bin file), use the esptool to download the encrypted firmware as follows: **
esptool.py -b 460800 --before default_reset --after no_reset --chip esp32 write_flash --flash_mode dio --flash_size detect --flash_freq 40m 0x1000 key_bootloader.bin 0xa000 key_partition-table.bin 0x20000 key_hello-world.bin
note:
This step to download the encryption firmware can also be downloaded directly using the Flash Download Tool as follows:
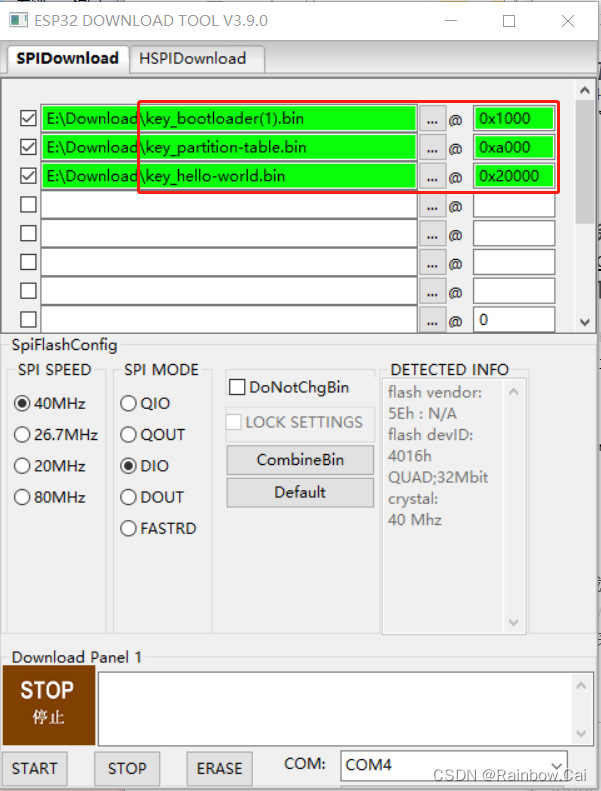
5 Program the Flash encryption key (key.bin) to Efuse:
espefuse.py burn_key flash_encryption key.bin
6 Use the esptool tool to turn on the Control Bits for Flash Encryption in Efuse:
espefuse.py burn_efuse FLASH_CRYPT_CONFIG 0xF FLASH_CRYPT_CNT 1
Instructions
If the Flash encryption key (
key.bin) is not written in Efuse or not turn on the Control Bits for Flash encryption in Efuse, the encrypted “firmware” (bin file) does not boot properly.After Flash encryption is enabled, the Flash Download Tool cannot be used to reprogram the firmware and erase the firmware, but the esptool tool is supported to reprogram the firmware and erase the firmware.
**For encrypted modules encrypted by Flash to reprogram firmware, the reprogram firmware requires to turn on the configuration option of “
Flash Encryption” in menuconfig, and use the same encryption key (key.bin) as the old firmware to encrypt and flash, so that the reprogram firmware can boot properly. ****Burning encryption keys in Efuse is non-erasable, so new keys cannot be reprogrammed. **
This solution meets the requirements that it can also use the esptool tool to
reprogram the firmware, erase, read Flashoperation on the module after the module production firmware is encrypted, but the read firmware is encrypted firmware. If the new module does not flash the key (key.bin) corresponding to the encryption firmware, only reprogram the encrypted firmware to the new module, it can’t boot properly.
边栏推荐
- Huawei Nova 10 series supports the application security detection function to build a strong mobile security firewall
- 数据集划分
- C# 使用StopWatch测量程序运行时间
- 项目中遇到的线上数据迁移方案1---总体思路整理和技术梳理
- Functional interface
- 公司要上监控,Zabbix 和 Prometheus 怎么选?这么选准没错!
- 1007 maximum subsequence sum (25 points) (PAT class a)
- 1009 Product of Polynomials(25 分)(PAT甲级)
- Niuke Xiaobai monthly race 7 I new Microsoft Office Word document
- Pythagorean number law (any three numbers can meet the conditions of Pythagorean theorem)
猜你喜欢
CANN算子:利用迭代器高效实现Tensor数据切割分块处理
牛客小白月赛7 谁是神箭手
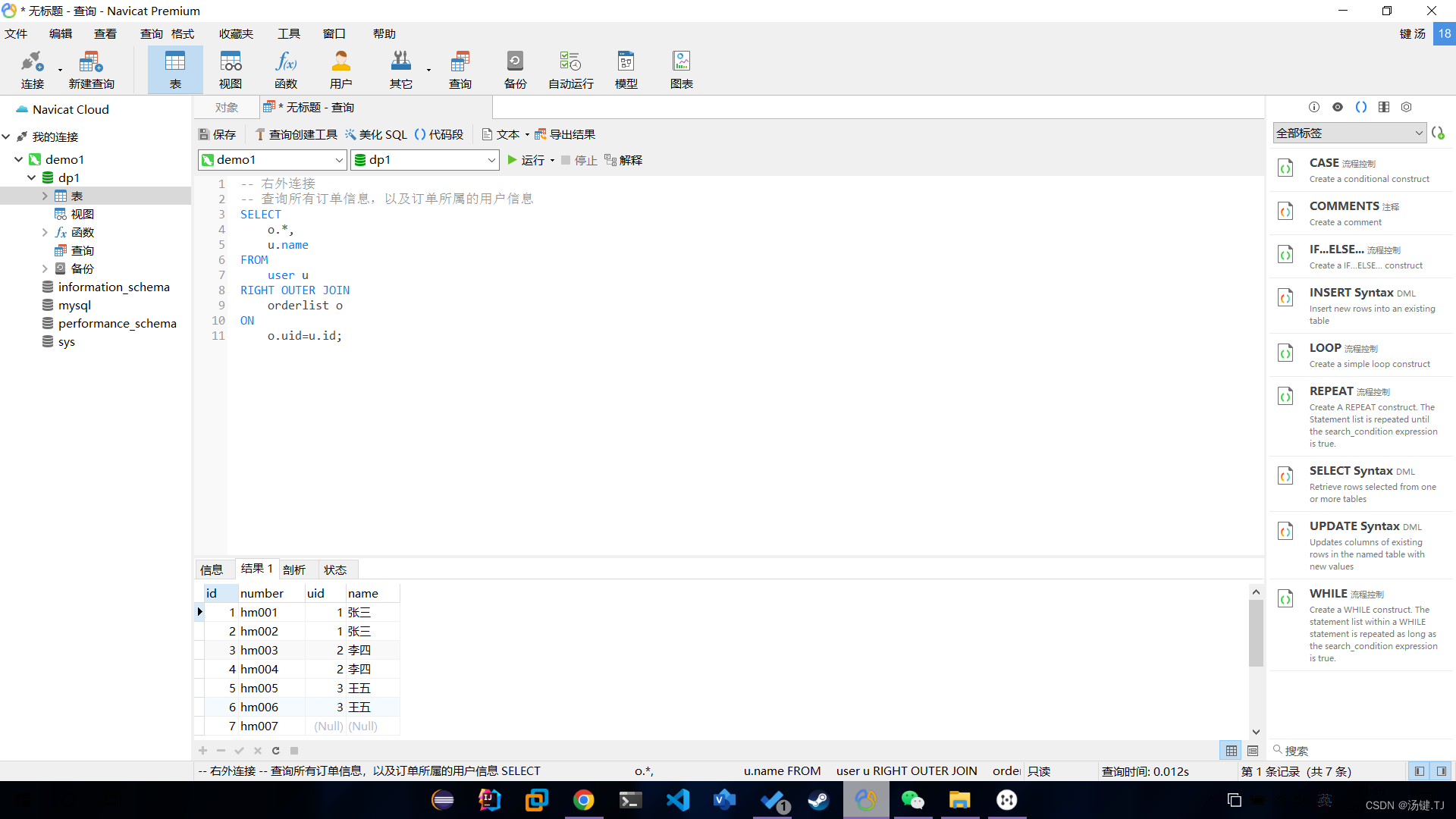
多表操作-外连接查询
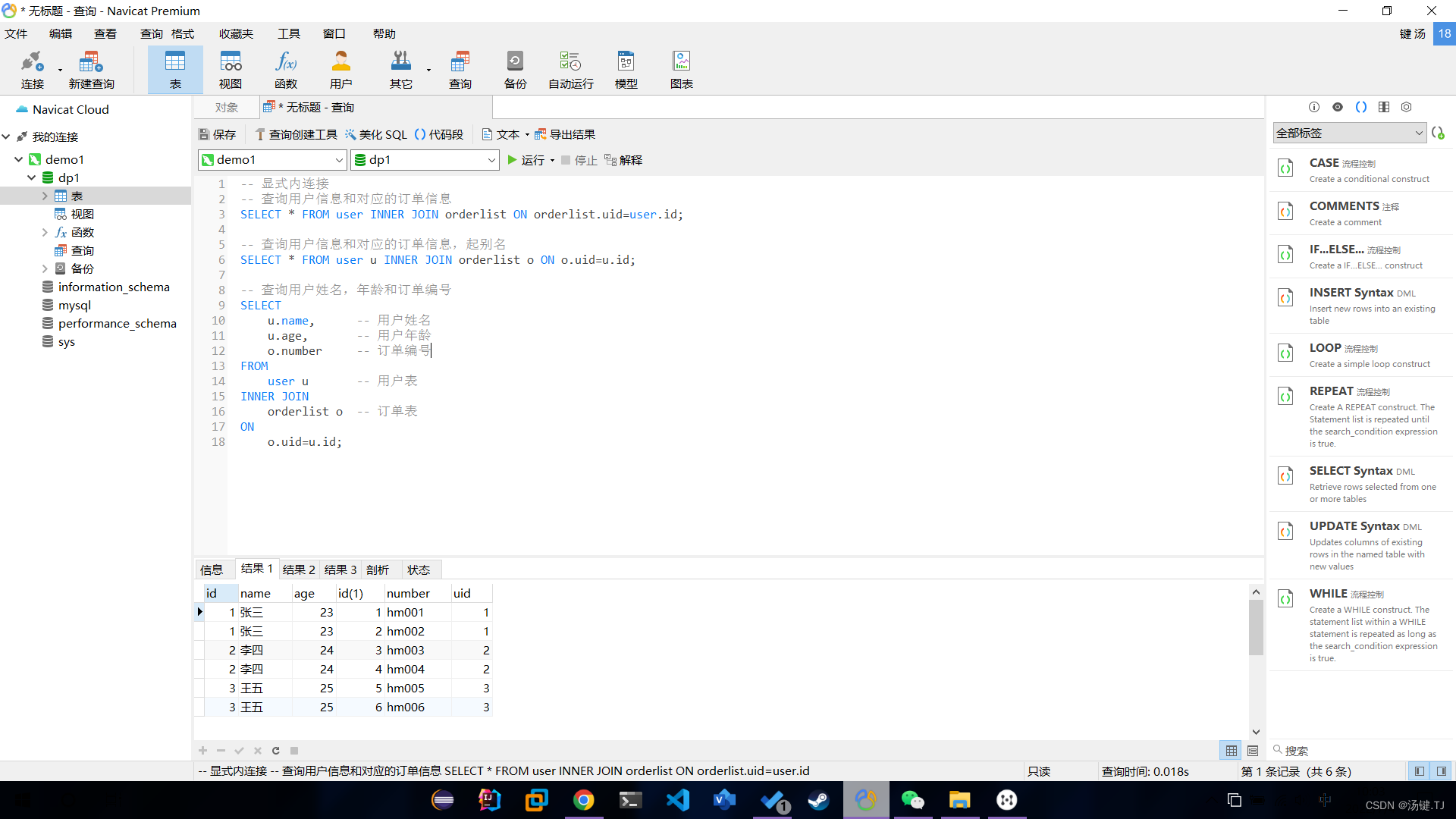
多表操作-内连接查询
Some thoughts on whether the judgment point is located in the contour
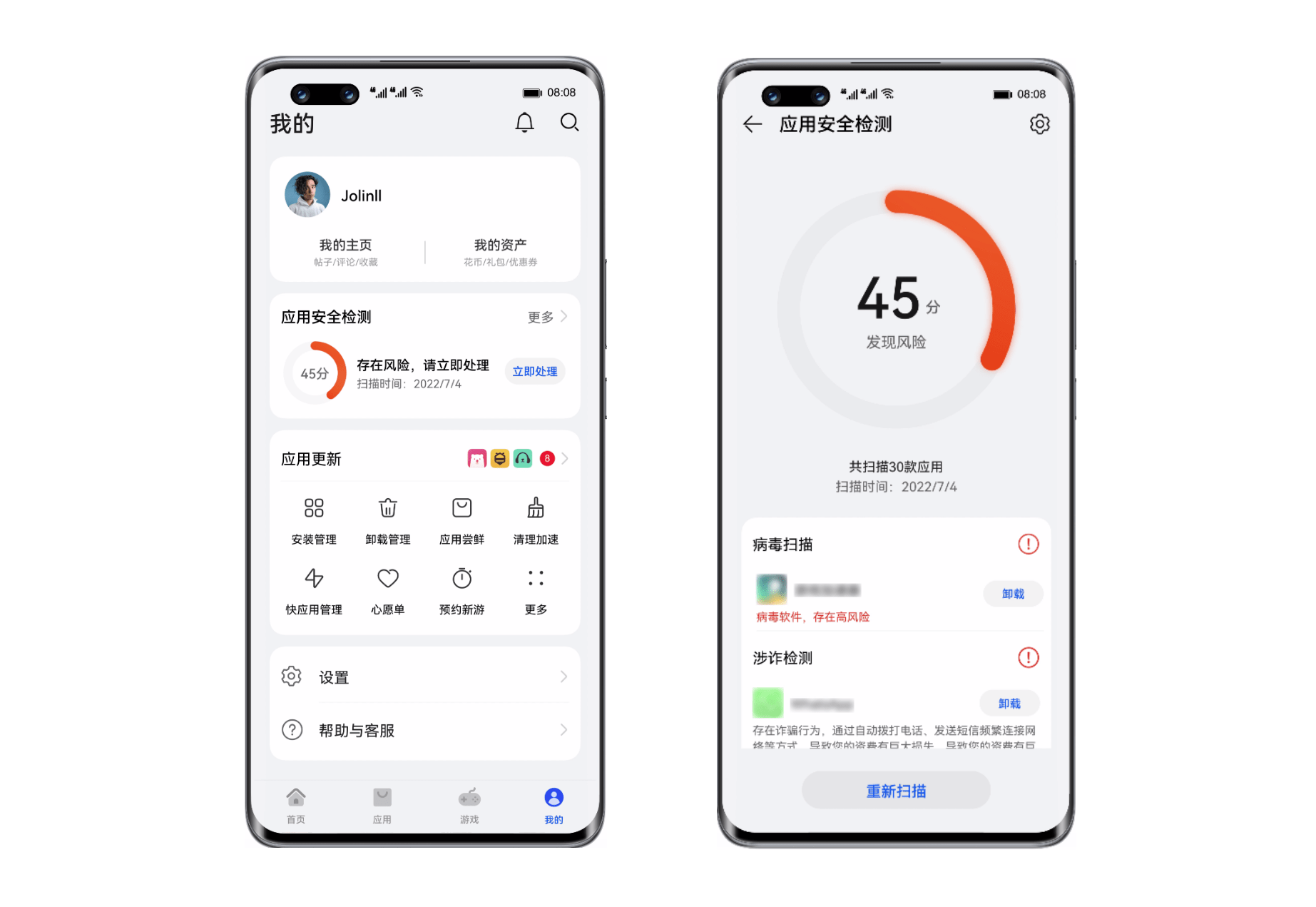
Huawei Nova 10 series supports the application security detection function to build a strong mobile security firewall

92. (cesium chapter) cesium building layering
记一次 .NET 某工控数据采集平台 线程数 爆高分析
Cbcgptabwnd control used by BCG (equivalent to MFC TabControl)

做社交媒体营销应该注意些什么?Shopline卖家的成功秘笈在这里!
随机推荐
"Only one trip", active recommendation and exploration of community installation and maintenance tasks
1007 Maximum Subsequence Sum(25 分)(PAT甲级)
How to use async Awati asynchronous task processing instead of backgroundworker?
In the first month of its launch, the tourist praise rate of this campsite was as high as 99.9%! How did he do it?
牛客小白月赛7 谁是神箭手
[QNX Hypervisor 2.2用户手册]6.3.1 工厂页和控制页
Niuke Xiaobai monthly race 7 I new Microsoft Office Word document
In operation (i.e. included in) usage of SSRs filter
Key rendering paths for performance optimization
Functional interface
Matrix flip (array simulation)
Detailed explanation of the binary processing function threshold() of opencv
Offset function and windowing function
BCG 使用之CBCGPProgressDlgCtrl進度條使用
1003 emergency (25 points) (PAT class a)
The company needs to be monitored. How do ZABBIX and Prometheus choose? That's the right choice!
2022 version of stronger jsonpath compatibility and performance test (snack3, fastjson2, jayway.jsonpath)
Specify the character set to output
Pythagorean number law (any three numbers can meet the conditions of Pythagorean theorem)
C # use stopwatch to measure the running time of the program