当前位置:网站首页>CS kill-free pose
CS kill-free pose
2022-08-03 19:12:00 【Antview Network Security】
Foreword
The red team generally uses fishing to break through the boundary in HVV, and the blue team uses fishing to achieve traceability and countermeasures, but they are all inseparable from a good kill-free horse., Windows Defender and Symantec and other mainstream anti-software are no problem.
The working principle of anti-software
There are many ways to detect and kill software, such as feature recognition, which is based on virus samples collected by various manufacturers and the virus characteristics extracted from virus samples, so the ability to kill software also depends on the size of the virus database to a certain extent., this feature-based recognition is generally based on static.The working principle of heuristic can basically be defined as dynamic killing or a killing method of machine learning method.
How to avoid killing
•By modifying the signature code, the virus sample features that trigger the anti-software rules can be located according to the method of taint detection. Modifying the obvious features can avoid killing to a certain extent.
•To avoid killing the flower instructions, add garbage instructions in the program shellcode or feature code area, the added garbage instructions will not affect the file execution, and the verification will be inconsistent in dynamic killing or file hash comparison.
•Packers, such as upx packers, etc. After the general file is landed, the hash value can also be bypassed.
•Secondary compilation, generally used for secondary compilation of shellcode to bypass anti-software.
• Poweshell is free from killing, but general protection software or the system itself will generate an alarm when the powershell application is normally invoked. General security devices cannot pass through, and you need to use commands to bypass security device monitoring.
Don't kill
CS generates payload
Add listener to generate payload
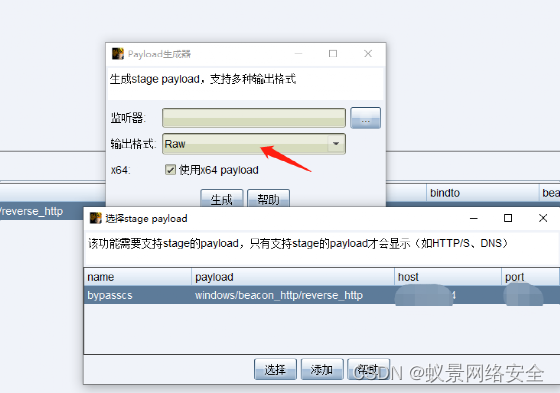
Download go-strip.exe and obfuscate the binary go compilation information
download link
https://cdn.githubjs.cf/boy-hack/go-strip/releases/download/v3.0/go-strip_0.3.4_windows_amd64.zip
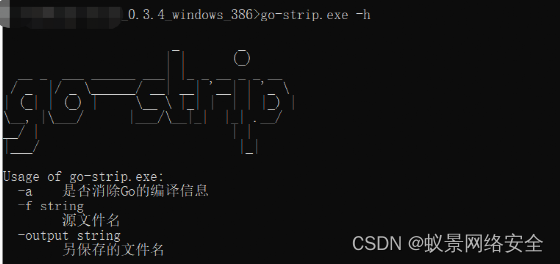
Run script bypass
go run main.go

The core content is the encryption method
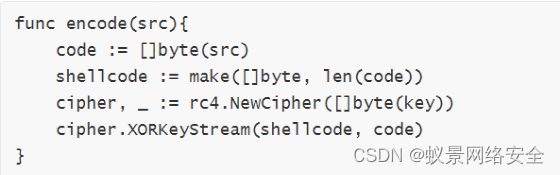
The shellcode is encrypted at two layers.
The source code is not directly put here, because I am worried that the sample will be tagged, here are a few projects recommended, try to use go here instead of python
https://github.com/TideSec/BypassAntiVirus
https://github.com/admin360bug/bypass
https://github.com/hack2fun/BypassAV/blob/master/bypass.cna
Here I modified the generated exe.Install tinder, check and kill
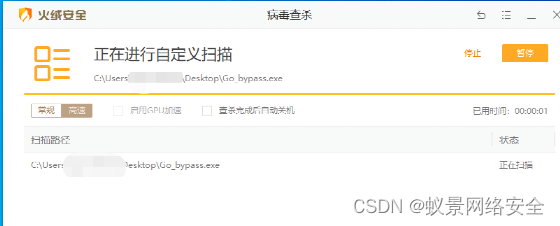
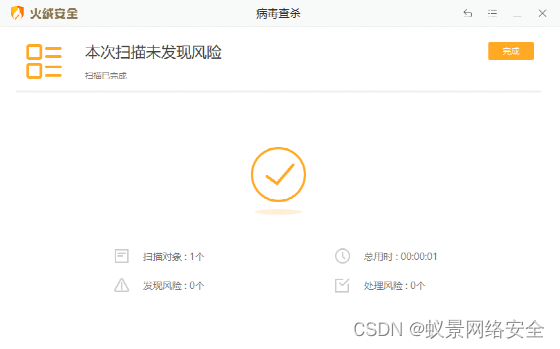
CS Online
Packer
Add another shell test.Address
https://upx.en.softonic.com/
Simple Compression Shell
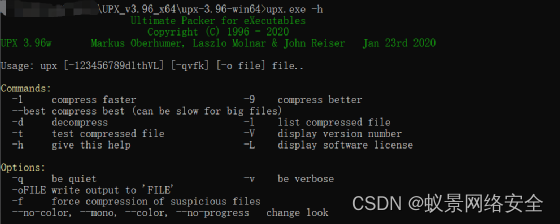
upx.exe -f Go_bypass.exe
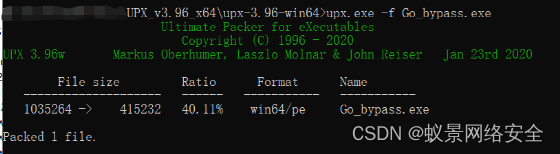
The size of the exe file of the birthday after packing is 406KB
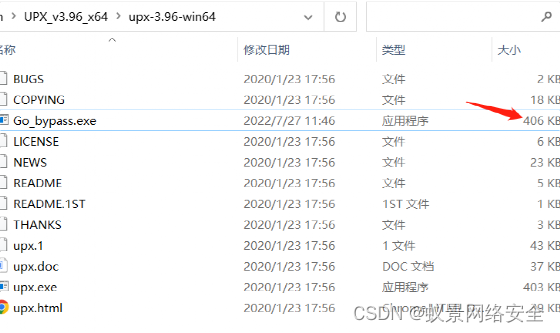
You can see that the file size before packing is 1011kb
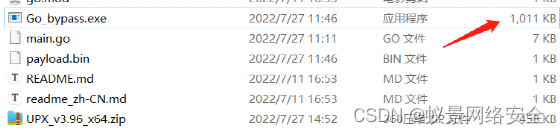
Modify the file name after packing to upx_Go_bypass to confirm the online status

Successfully launched, continue to check the kill-free effect after packing

At this time, the velvet does not report poison to the files before and after packing

Although the virus was reported before the package, but the virus was not reported after the package.

Symantec has not reported poisoning, and other anti-virus software will not be released.But be careful not to use cloud sandbox detection.
Summary
Multiple tests will always lead to new discoveries. It is relatively easy to practice, but it is important to pay attention to the effect of avoiding kills.
边栏推荐
- Confused!Ali was abused on the one hand, but was fortunate to be promoted to Huawei's technology, and successfully got the offer, with an annual salary of 40w
- 网络协议-TCP、UDP区别及TCP三次握手、四次挥手
- MySQL如何一劳永逸的永久支持输入中文
- MD5是对称加密还是非对称加密,有什么优缺点
- MySQL——增删改查进阶
- vulnhub pyexp: 1
- Shell编程之循环语句
- 【Azure 事件中心】使用Azure AD认证方式创建Event Hub Consume Client + 自定义Event Position
- 阿里巴巴政委体系-第五章、阿里政委体系建设
- MySQL基础
猜你喜欢
懵逼!阿里一面被虐了,幸获内推华为技术四面,成功拿到offer,年薪40w
OneNote 教程,如何在 OneNote 中设置页面格式?

要想成为黑客,离不开这十大基础知识
U-Net生物医学图像分割讲解(Convolutional Networks for BiomedicalImage Segmentation)
vulnhub pyexp: 1
Radondb mysql installation problems

图像超分——Real-ESRGAN快速上手
MySQL超详细安装教程 手把手教你安装MySQL到使用MySQL 最简单的MySQL安装方式,这种方式装,卸载也简单
![[Azure Event Hub] Create Event Hub Consume Client + Custom Event Position with Azure AD Authentication](/img/fe/db506853be08398f815f4e36beee76.png)
[Azure Event Hub] Create Event Hub Consume Client + Custom Event Position with Azure AD Authentication
Protobuf Grpc使用异常 类型有未导出的方法,并且是在不同的软件包中定义
随机推荐
POJ 2377 Bad Cowtractors(最大生成树)
InnoDB 中不同SQL语句设置的锁
201709-3 CCF jason查询 (满分题解)
WEB 渗透之RCE
flex布局
X86 function call model analysis
手把手教你定位线上MySQL慢查询问题,包教包会
MySQL【变量、流程控制与游标】
如何理解即时通讯开发移动网络的“弱”和“慢”
201712-3 CCF Crontab满分题解
The effective square of the test (one question of the day 7/29)
Shell编程之循环语句
[Azure Event Hub] Create Event Hub Consume Client + Custom Event Position with Azure AD Authentication
面试突击:什么是粘包和半包?怎么解决?
MySQL基础
【Azure 事件中心】使用Azure AD认证方式创建Event Hub Consume Client + 自定义Event Position
Power button brush the topic of merging two orderly array
力扣刷题之移动零
When does MySQL use table locks and when to use row locks?You should know this
Matlab论文插图绘制模板第42期—气泡矩阵图(相关系数矩阵图)