当前位置:网站首页>How to improve data security by renting servers in Hong Kong
How to improve data security by renting servers in Hong Kong
2022-07-03 19:42:00 【Yisuyun Q & A】
How to rent Hong Kong servers to improve data security :1、 We need to maintain the database of Hong Kong server , Prevent data leakage ;2、 The software program of Hong Kong server needs to be updated regularly , Prevent hackers from exploiting vulnerabilities ;3、 You need to back up the data of the Hong Kong server , Prevent data loss and cannot be recovered ;4、 Build a perfect disaster recovery mechanism for Hong Kong servers , Improve server data security .

The details are as follows :
1、 Maintain your database
Take some time to make sure your database is well maintained , And can be updated as needed , This is important . To be specific , You should ensure that your database is protected by SQL Injection protection . You may also need to delete any unwanted data , At the same time, manage the access rights of others to the database . If your customers need to pay on your website , So how to place your customer sensitive information ( Such as payment information ) By malicious mobile phone , This is especially important . You can use some database management tools to help you maintain .
2、 Update the software regularly
In terms of server security in Hong Kong , One of the biggest mistakes you can make is not keeping your software up to date . When you use outdated software , It may not have security updates 、 Patches and other protective measures to protect your information . When you receive a safety reminder , Point out that there is a new version of security software on your Hong Kong server , Please install now , This will effectively reduce the risk of your server software vulnerabilities being exploited by hackers . If you turn off the software version automatic update and other functions , Then you may completely forget the work of version update , So that your Hong Kong server is in danger .
3、 Backup of retained data
No one can predict how much important data you will lose as a result of a security vulnerability or attack , But this situation happens to a large number of large and small enterprises every day . So please make sure you set up regular data backup for your Hong Kong server , Don't give the backers any chance in this respect . You can make a copy backup of important data , Save in local or other server location , And ensure that in the event of an attack or security hazard , You can quickly find and use this data instead of losing it completely .
4、 Establish a perfect disaster recovery mechanism
Last , Now is also a good time to establish a perfect disaster recovery mechanism in your business , This includes developing agreements to deal with data breaches or other types of security risks . say concretely , You should know who to contact 、 How to reset the password and what other steps need to be followed . If any data is leaked , You may also want someone to prepare a statement for the customer .
边栏推荐
- 第一章:三位阶乘和数,图形点扫描
- Point cloud data denoising
- Merge K ascending linked lists
- Xctf attack and defense world crypto advanced area best_ rsa
- 5. MVVM model
- The space of C disk is insufficient, and the computer becomes stuck. Quickly expand the capacity of C disk to make the system more smooth
- 2022-07-02 advanced network engineering (XV) routing policy - route policy feature, policy based routing, MQC (modular QoS command line)
- BOC protected phenylalanine zinc porphyrin (Zn · TAPP Phe BOC) / iron porphyrin (Fe · TAPP Phe BOC) / nickel porphyrin (Ni · TAPP Phe BOC) / manganese porphyrin (Mn · TAPP Phe BOC) Qiyue Keke
- Day11 ---- 我的页面, 用户信息获取修改与频道接口
- Pecan - route
猜你喜欢

Chapter 1: extend the same code decimal sum s (D, n)
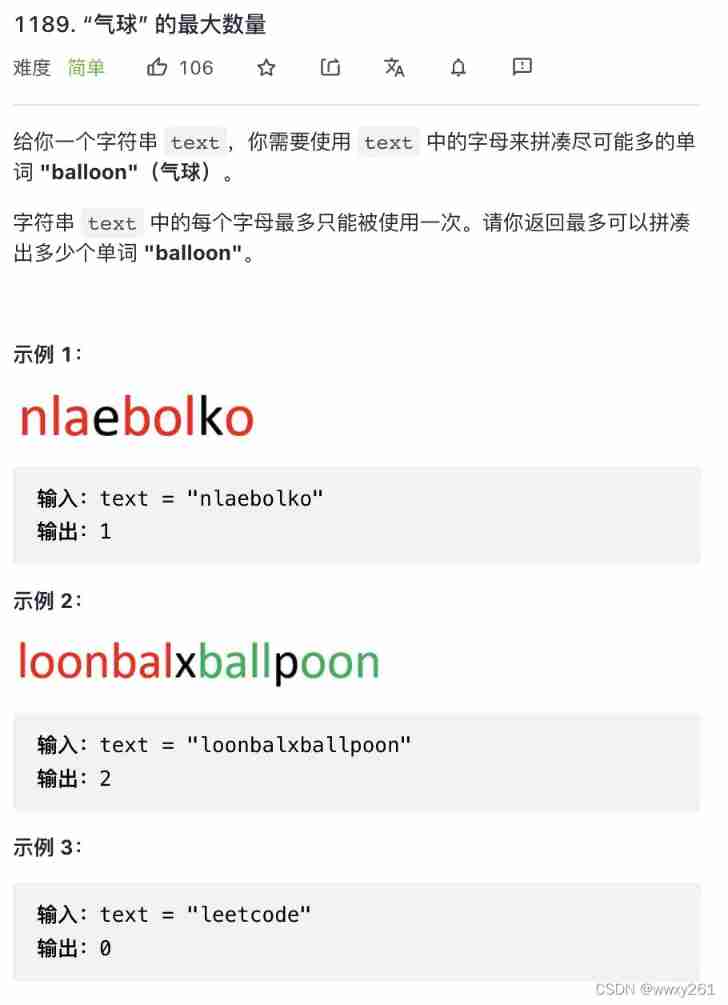
Leetcode 1189. Maximum number of balloons (special character count)
2022 Xinjiang latest construction eight members (standard members) simulated examination questions and answers

If the warehouse management communication is not in place, what problems will occur?
第一章:求奇因数代数和,求同吗小数和s(d, n),简化同码小数和s(d, n),拓广同码小数和s(d, n)

Day18 - basis of interface testing

The necessity of lean production and management in sheet metal industry
BOC protected alanine zinc porphyrin Zn · TAPP ala BOC / alanine zinc porphyrin Zn · TAPP ala BOC / alanine zinc porphyrin Zn · TAPP ala BOC / alanine zinc porphyrin Zn · TAPP ala BOC supplied by Qiyu
FPGA 学习笔记:Vivado 2019.1 工程创建
![Meso tetra [P - (p-n-carbazole benzylidene imino)] phenylporphyrin (tcipp) /eu (tcipp) [pc( α- 2-oc8h17) 4] and euh (tcipp) [pc (a-2-oc8h17) 4] supplied by Qiyue](/img/5b/fc776a1982e24b82984d82be6a016f.jpg)
Meso tetra [P - (p-n-carbazole benzylidene imino)] phenylporphyrin (tcipp) /eu (tcipp) [pc( α- 2-oc8h17) 4] and euh (tcipp) [pc (a-2-oc8h17) 4] supplied by Qiyue
随机推荐
Octopus online ecological chain tour Atocha protocol received near grant worth $50000
Meso tetra [P - (p-n-carbazole benzylidene imino)] phenylporphyrin (tcipp) /eu (tcipp) [pc( α- 2-oc8h17) 4] and euh (tcipp) [pc (a-2-oc8h17) 4] supplied by Qiyue
Floating source code comment (38) parallel job processor
BUUCTF
Today I am filled with emotion
IPv6 experiment
OSPF - detailed explanation of stub area and full stub area
Luogu-p1107 [bjwc2008] Lei Tao's kitten
Chapter 1: drinking soft drinks, step tariff calculation, step tariff calculation function, personal income tax, solving square root inequality, simplifying solving square root inequality, solving dem
Phpstudy set LAN access
2. Template syntax
Compared with 4G, what are the advantages of 5g to meet the technical requirements of industry 4.0
05 -- QT OpenGL draw cube uniform
2022-06-25 网工进阶(十一)IS-IS-三大表(邻居表、路由表、链路状态数据库表)、LSP、CSNP、PSNP、LSP的同步过程
Utilisation de base du cadre unitest
Pecan — Overview
02 -- QT OpenGL drawing triangle
Chapter 2: find the number of daffodils based on decomposition, find the number of daffodils based on combination, find the conformal number in [x, y], explore the n-bit conformal number, recursively
04 -- QT OpenGL two sets of shaders draw two triangles
Cross compile opencv with contrib