当前位置:网站首页>Solution to long waiting time of SSH connection to remote host
Solution to long waiting time of SSH connection to remote host
2022-07-03 16:59:00 【Brother Xing plays with the clouds】
Recently in use SSH When connecting to the remote host, I found that I was inputting SSH After the command, it will take a long time before the prompt for entering the password appears , On other machines, the prompt for entering the password can be displayed immediately . It makes me very unhappy . Who calls me a jerk ! So I don't want to just wait , Simply find a solution . finally , Our machine can also be connected to the remote host in seconds !
The solution is as follows :
1. First find /etc/ssh/ssh_config file
2. use vim Use root Permission to open the file and edit
3. take 27 Yes #GSSAPIAuthentication no Ahead ‘#’ Get rid of .
边栏推荐
- Web crawler knowledge day03
- [combinatorics] recursive equation (characteristic equation and characteristic root | example of characteristic equation | root formula of monadic quadratic equation)
- Kotlin学习快速入门(7)——扩展的妙用
- [combinatorics] polynomial theorem (polynomial coefficients | full arrangement of multiple sets | number of schemes corresponding to the ball sub model | polynomial coefficient correlation identity)
- 远程办公之如何推进跨部门项目协作 | 社区征文
- Idea configuration plug-in
- word 退格键删除不了选中文本,只能按delete
- [combinatorics] polynomial theorem (polynomial theorem | polynomial theorem proof | polynomial theorem inference 1 item number is the number of non negative integer solutions | polynomial theorem infe
- RedHat 6.2 配置 Zabbix
- C language string inversion
猜你喜欢

手把手带你入门 API 开发

線程池:業務代碼最常用也最容易犯錯的組件

Build your own website (23)
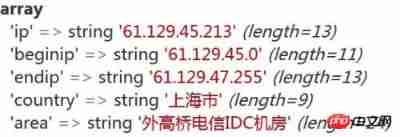
utfwry. Dat PHP, about ThinkPHP's method of IP location using utfwry address Library

What is the pledge pool and how to pledge?
Atom QT 16_ audiorecorder
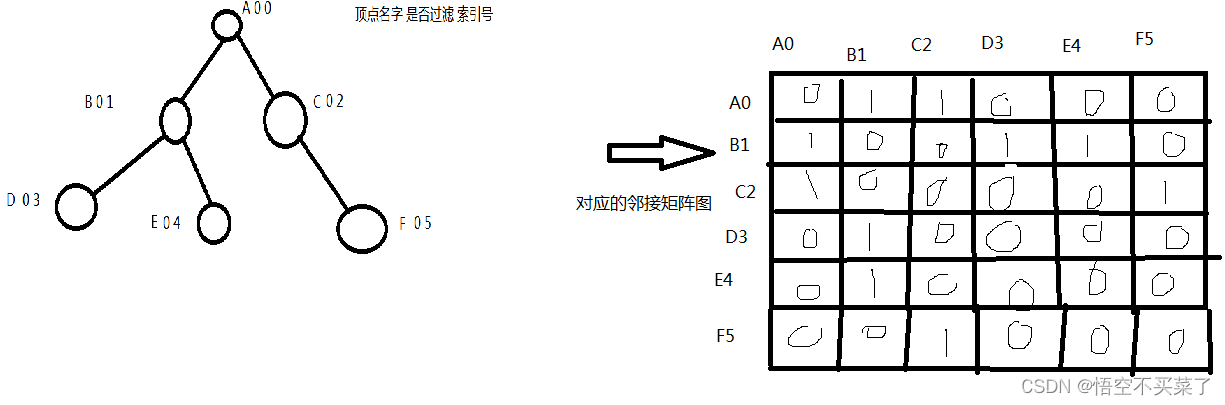
图之深度优先搜索
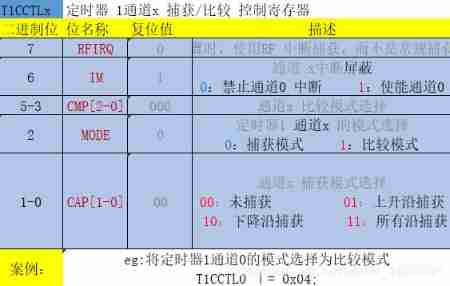
CC2530 common registers for timer 1

CC2530 common registers for ADC single channel conversion

What is the material of sa302grc? American standard container plate sa302grc chemical composition
随机推荐
Why is WPA3 security of enterprise business so important?
HP 阵列卡排障一例
[combinatorial mathematics] recursive equation (example of recursive equation 2 Hanoi Tower | example of recursive equation 3 insertion sequencing)
[combinatorics] recursive equation (example 1 of recursive equation | list recursive equation)
Build your own website (23)
MySQL single table field duplicate data takes the latest SQL statement
utfwry. Dat PHP, about ThinkPHP's method of IP location using utfwry address Library
手把手带你入门 API 开发
Meituan side: why does thread crash not cause JVM crash
C language string inversion
C语言字符串练习
Take you to API development by hand
13mnnimo5-4 German standard steel plate 13MnNiMo54 boiler steel 13MnNiMo54 chemical properties
[combinatorics] polynomial theorem (polynomial theorem | polynomial theorem proof | polynomial theorem inference 1 item number is the number of non negative integer solutions | polynomial theorem infe
PHP converts a one-dimensional array into a two-dimensional array
What material is sa537cl1? Sa537cl1 corresponds to the national standard material
浅谈拉格朗日插值及其应用
Necessary ability of data analysis
visual studio “通常每个套接字地址(协议/网络地址/端口)只允许使用一次“
汇编实例解析--实模式下屏幕显示