当前位置:网站首页>Dry goods | summarize the linkage use of those vulnerability tools
Dry goods | summarize the linkage use of those vulnerability tools
2022-07-07 13:46:00 【Network security self-study room】
0x00 Introduction to missed scanning
Introduction for web Level vulnerability scanning , And the linkage use of some tools to improve efficiency , Because different objects need to use different types of scanning , for example awvs For domestic cms The framework may not scan so efficiently , Compare awvs It is a foreign maintenance update , So in this case, not a missed scan can solve all the problems , This is also an easy problem for novice Xiaobai to talk about in the test .
0x01 Burpsuite linkage xray Leakage and app 0x02 AWVS linkage Xray At the same time, missed scanning detection 0x03 awvs linkage bp linkage xray 0x04 afrog Leakage and 0x05 vulmap,pocassist Leakage and 0x06 Goby linkage awvs&xray&fofa 0x07 Single point tool
0x01 Burpsuite linkage xray Leakage and app
Flow trend : Simulator app data (192.168.181.1:8888)–>Burpsuite( monitor 192.168.181.1:8888, Forwarding traffic 127.0.0.1:8888)–>Xray( monitor 127.0.0.1:8888)
Project address :xray:https://github.com/chaitin/xray/releases
Use : Burpsuite monitor app Traffic :  Burpsuite Forwarding traffic :
Burpsuite Forwarding traffic : 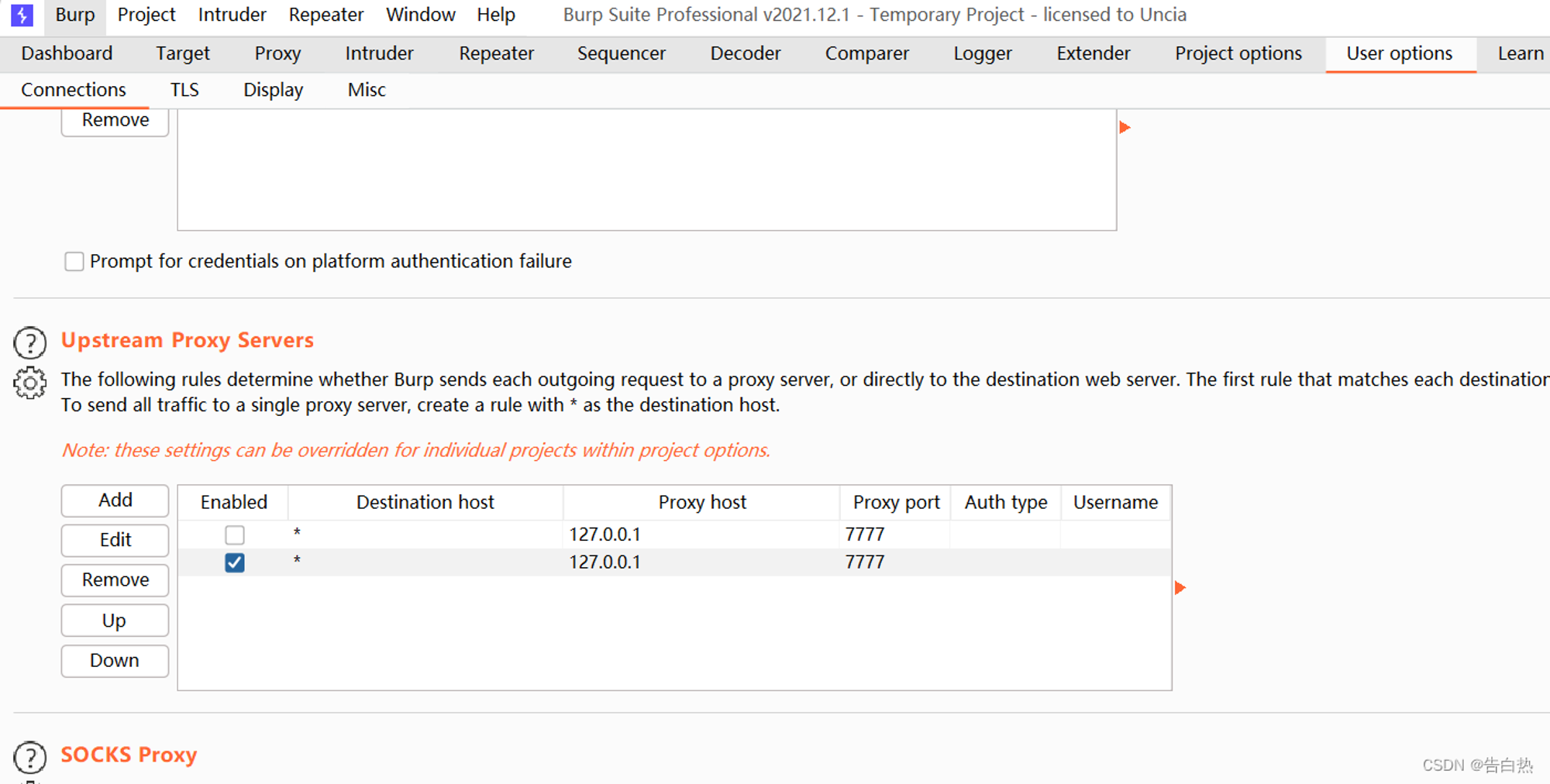
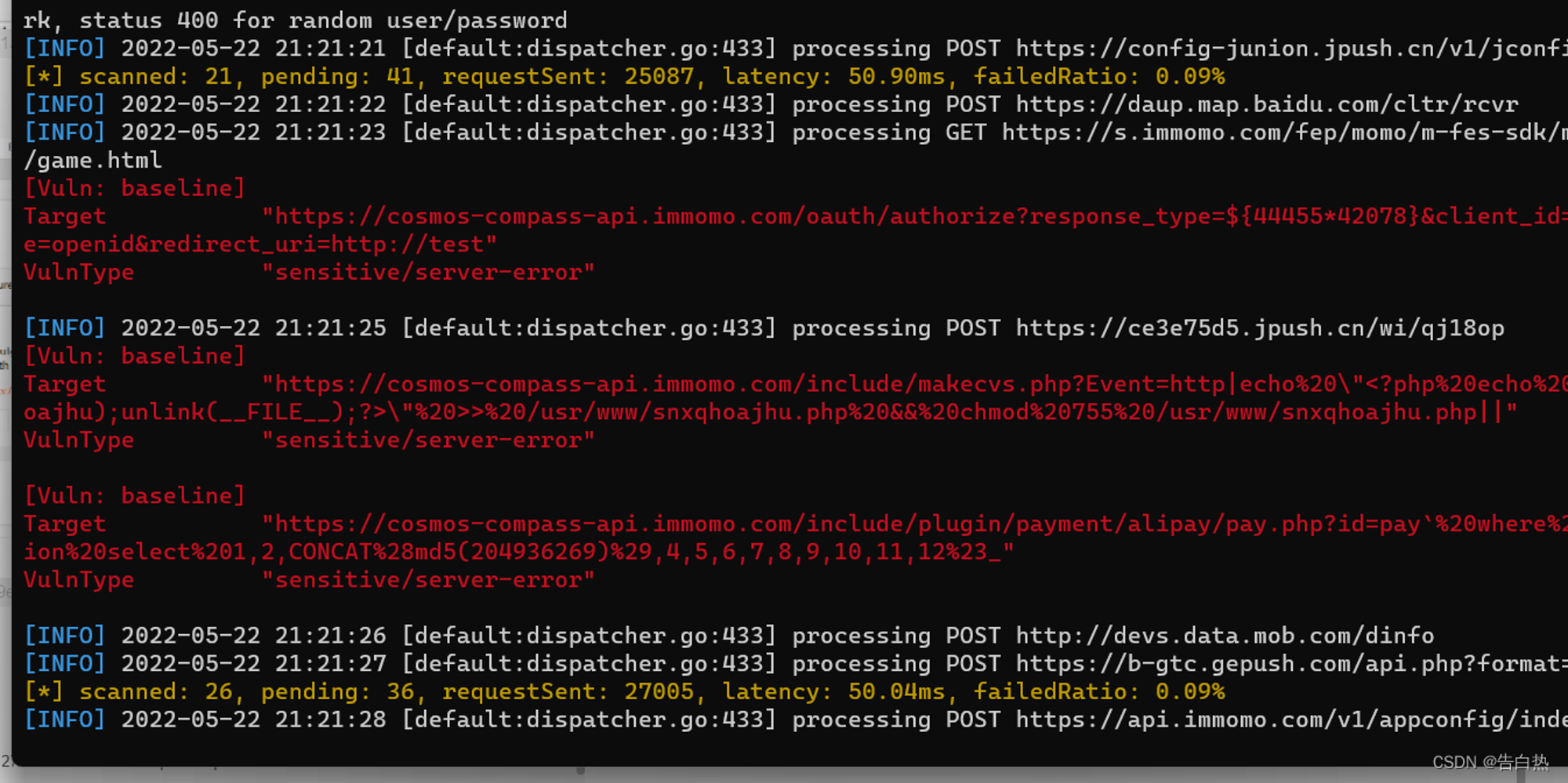
xray Detect traffic packets :
.\xray_windows_amd64.exe webscan --listen 127.0.0.1:7777 --html-output mniqi.html
0x02 AWVS linkage Xray At the same time, missed scanning detection
Flow trend : awvs Test object ( And send the traffic to IP1)–>Xray Monitor any traffic (0.0.0.0 Test flow leakage scanning )
Project address : awvs:https://www.ddosi.org/awvs14-6-log4j-rce/ Use : awvs After setting the scanning object, forward the traffic to 127.0.0.1:1111: 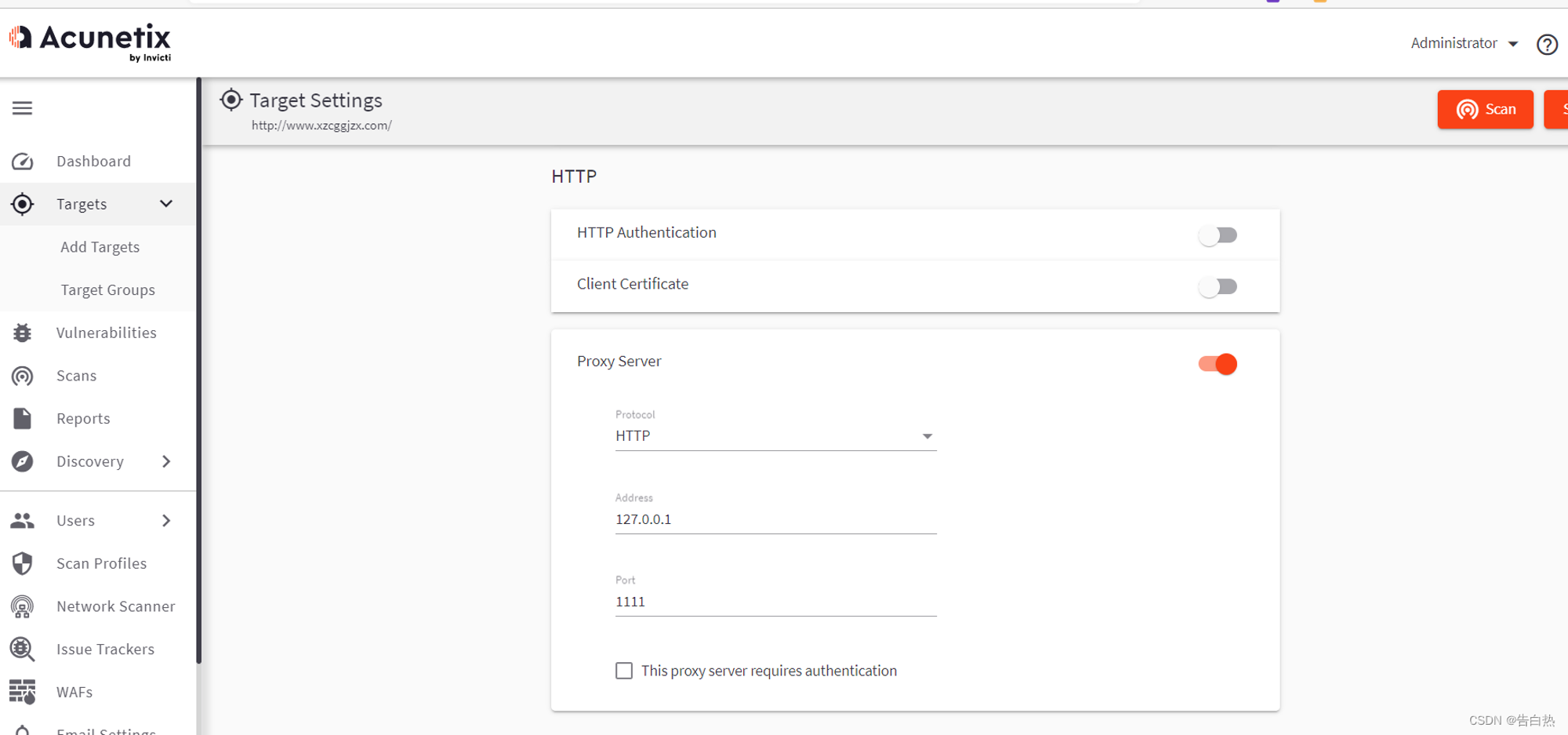 xray monitor 127.0.0.1:1111 Flow and scan :
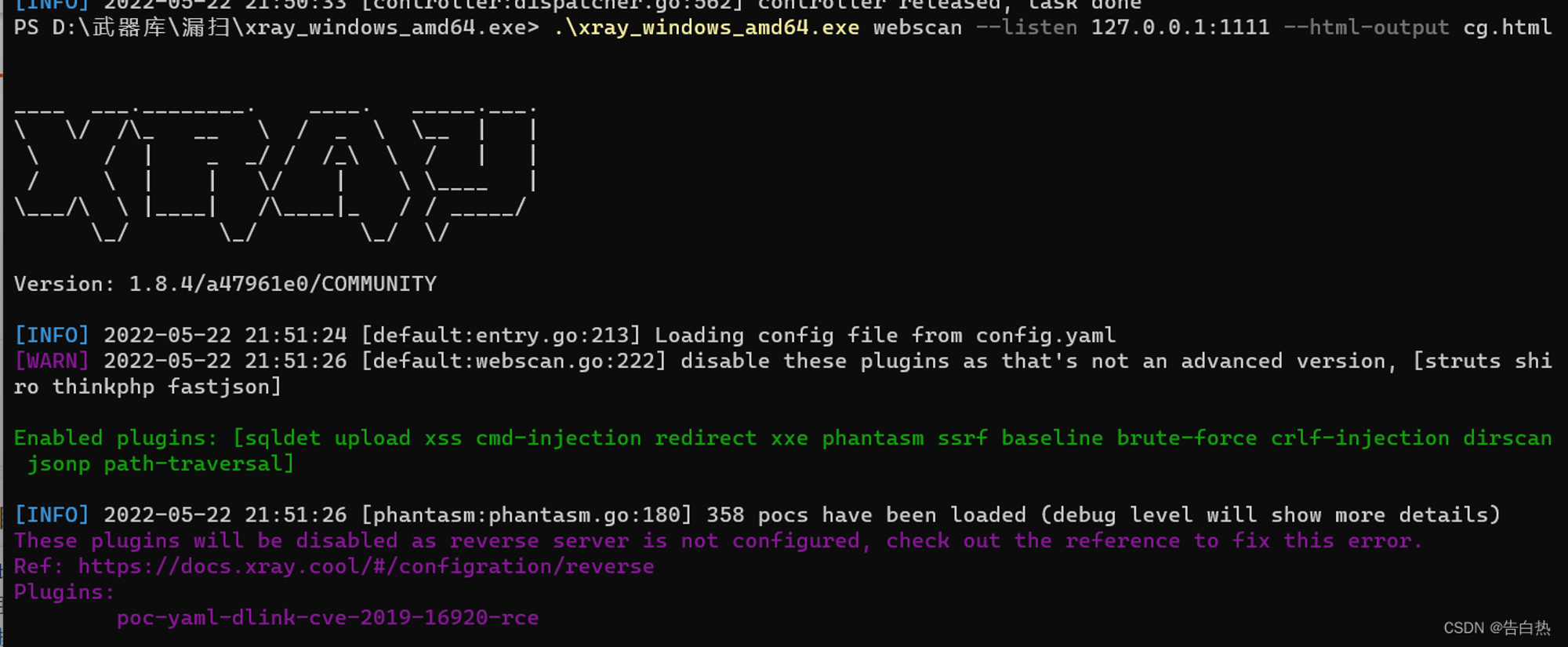
xray monitor 127.0.0.1:1111 Flow and scan :
.\xray_windows_amd64.exe webscan --listen 127.0.0.1:1111 --html-output cg.html
 Linkage scanning :
Linkage scanning : 
0x03 awvs linkage bp linkage xray
Flow trend :awvs Traffic –>Burpsuite–>Xray Test flow
Same as above , The effect is almost the same , Just forward the traffic in several layers
0x04 afrog Leakage and
afrog It is a high-performance 、 Fast and steady 、PoC Customizable vulnerability scanning ( Dig a hole ) Tools ,PoC involve CVE、CNVD、 Default password 、 Information disclosure 、 fingerprint identification 、 Unauthorized access 、 Arbitrary file reading 、 Command execution and other vulnerability types , Help network security practitioners quickly verify and repair vulnerabilities in time .
Project use :
Scanning a single target :
afrog -t http://127.0.0.1 -o result.html
Scan multiple targets :
afrog -T urls.txt -o result.html
for example :urls.txt
http://192.168.139.129:8080
http://127.0.0.1
Test individual PoC file :
afrog -t http://127.0.0.1 -P ./testing/poc-test.yaml -o result.html
Test multiple PoC file :
afrog -t http://127.0.0.1 -P ./testing/ -o result.html
Output after scanning html The report , You can intuitively see the existing vulnerabilities , Then test and use : 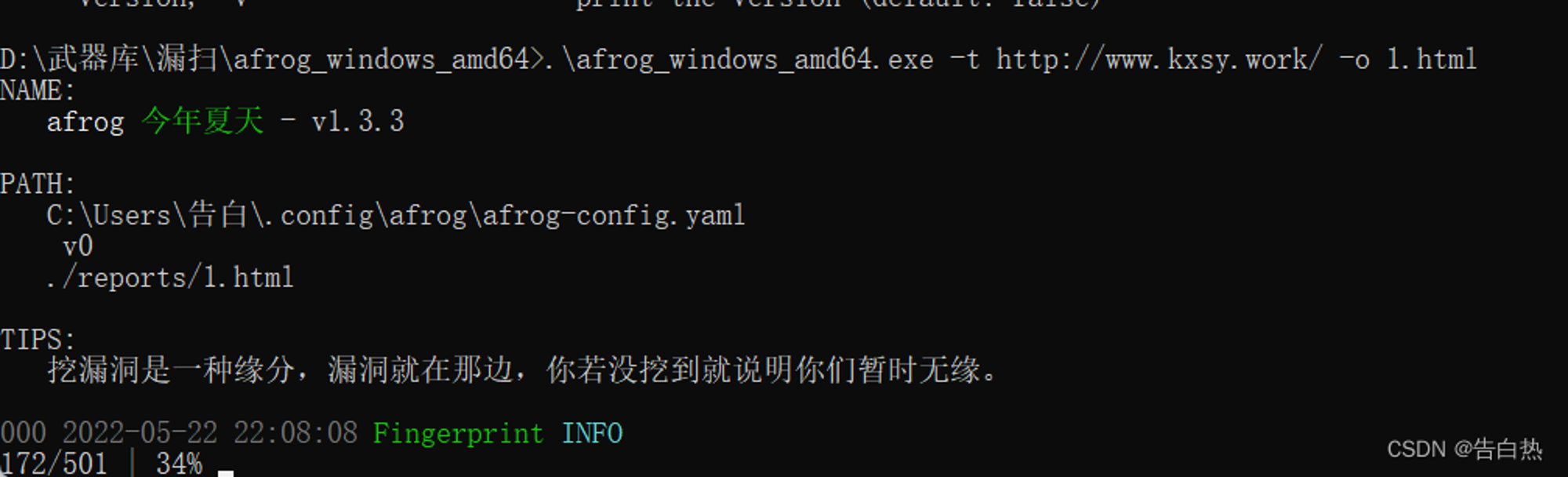
0x05 vulmap,pocassist Leakage and
The missed scan is in an un updated state , The project gives , You can't do the experiment yourself Project address : vulmap:https://github.com/zhzyker/vulmap/releases pocassist:https://github.com/jweny/pocassist/releases
0x06 Goby linkage awvs&xray&fofa
Goby It is a next-generation network security tool based on cyberspace mapping technology . It generates emergency response to network security incidents and vulnerabilities by establishing a comprehensive asset knowledge base for the target network . Goby Provide the most comprehensive asset identification .Goby Preset 100,000 Multiple rule recognition engines , It can automatically identify and classify hardware equipment and software business systems , And comprehensively analyze the business systems existing in the network .
Project address :https://github.com/gobysec/Goby/releases
Plug in linkage : If there are too many, we won't make a demonstration ,goby It can play a good role in asset sorting , Very recommended 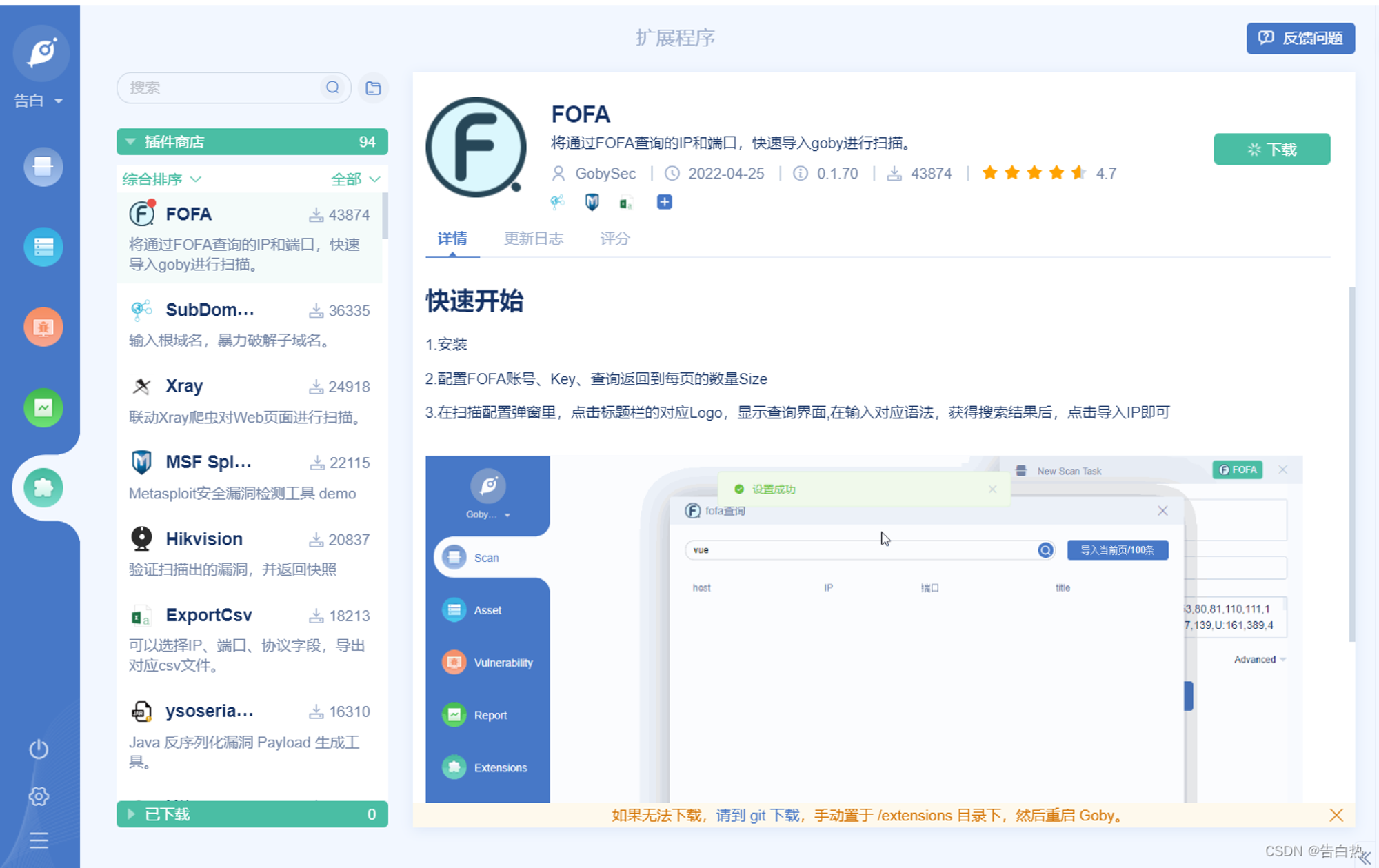
0x07 Single point tool
In general testing , Missed scan is to detect the whole target , But often when using a single weapon , It can have a very bad effect when penetrating , Here are some common individual weapons :
Graphical penetration Arsenal :GUI_TOOLS_V6.1_by Safety circle little prince –bugfixed 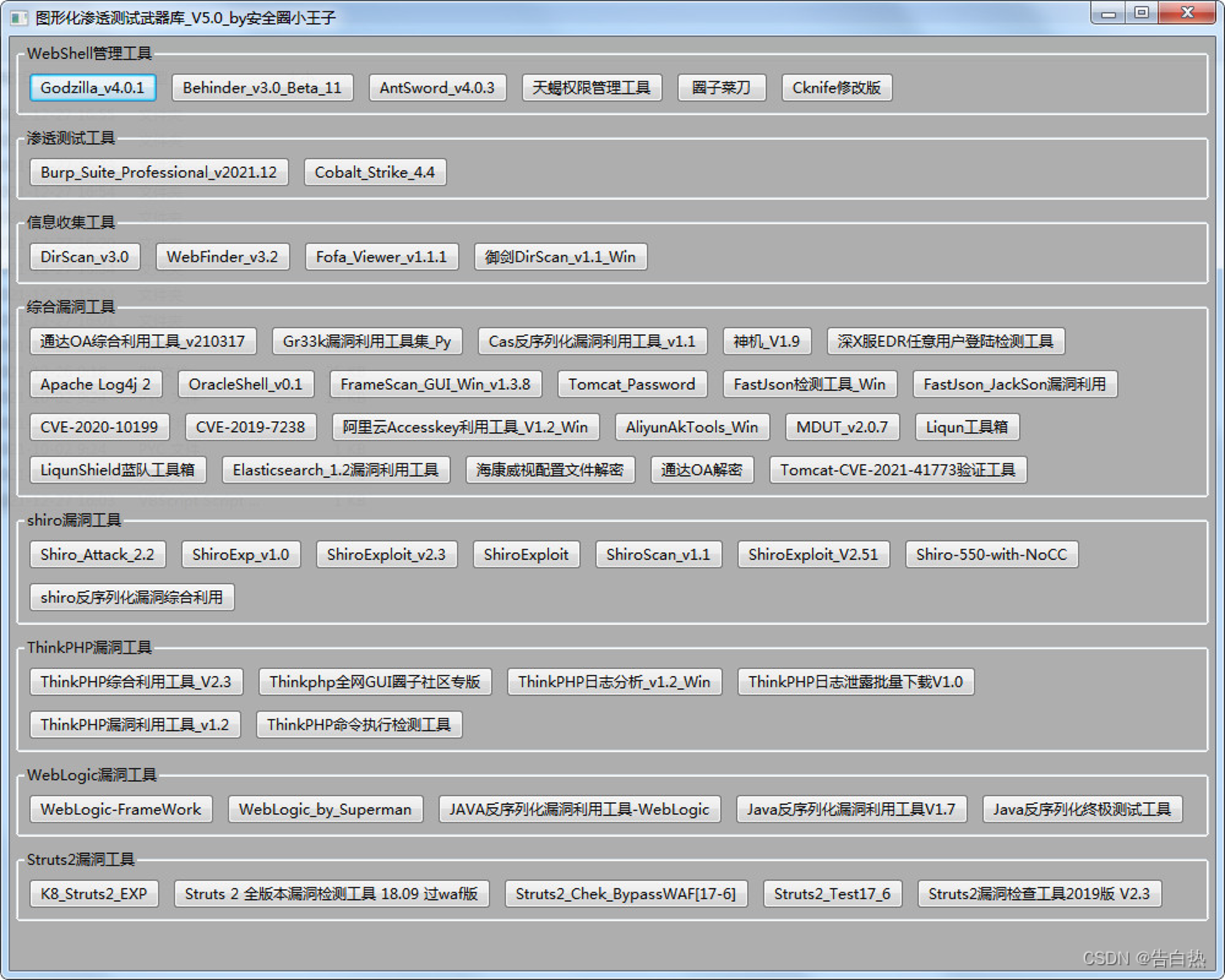
CMS Vulnerability scanner name Supported by CMS platform :
Droopescan WordPress,Joomla,Drupal,Moodle,SilverStripe
CMSmap WordPress,Joomla,Drupal,Moodle
CMSeeK WordPress,Joomla,Drupal etc.
WPXF WordPress
WPScan WordPress
WPSeku WordPress
WPForce WordPress
JoomScan Joomla
JoomlaVS Joomla
JScanner Joomla
Drupwn Drupal
Typo3Scan Typo3
Zhiyuan OA Comprehensive utilization tools https://github.com/Summer177/seeyon_exp
Accessible OA Comprehensive utilization tools https://github.com/xinyu2428/TDOA_RCE TDOA_RCE
Lan Ling OA Exploit tools / The front desk is unconditional RCE/ File is written to https://github.com/yuanhaiGreg/LandrayExploit
Pan Wei OA Vulnerability comprehensive utilization script https://github.com/z1un/weaver_exp weaver_exp
Ruijie network EG Easy gateway RCE Batch safety inspection https://github.com/Tas9er/EgGateWayGetShell EgGateWayGetShell
CMSmap For popular CMS Tools for security scanning https://github.com/Dionach/CMSmap CMSmap
Use Go Developed WordPress Vulnerability scanning tool https://github.com/blackbinn/wprecon wprecon
One Ruby frame , To help with WordPress Perform penetration test on the system https://github.com/rastating/wordpress-exploit-framework
WPScan WordPress Security scanners https://github.com/wpscanteam/wpscan wpscan
WPForce Wordpress Attack Suite https://github.com/n00py/WPForce WPForce
边栏推荐
- 2022-7-7 Leetcode 34. Find the first and last positions of elements in a sorted array
- 如何让join跑得更快?
- 简单好用的代码规范
- 供应链供需预估-[时间序列]
- . Net core about redis pipeline and transactions
- MySQL error 28 and solution
- [QNX Hypervisor 2.2用户手册]6.3.4 虚拟寄存器(guest_shm.h)
- Problems that cannot be accessed in MySQL LAN
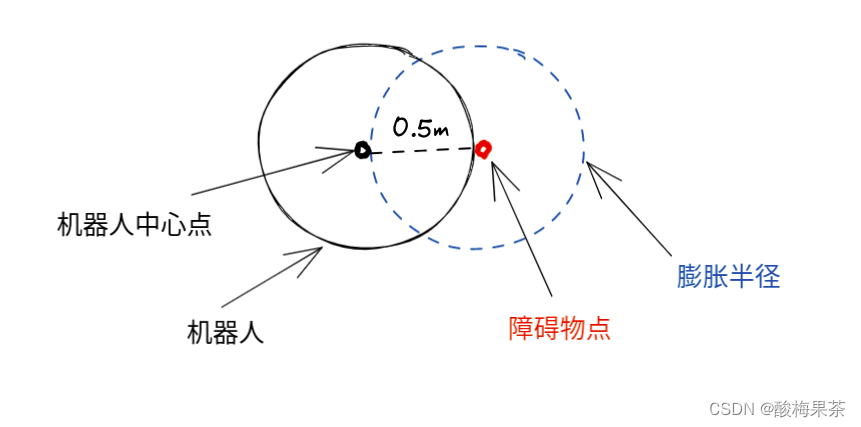
- 室内ROS机器人导航调试记录(膨胀半径的选取经验)
- Distributed transaction solution
猜你喜欢

高等数学---第八章多元函数微分学1
室內ROS機器人導航調試記錄(膨脹半徑的選取經驗)
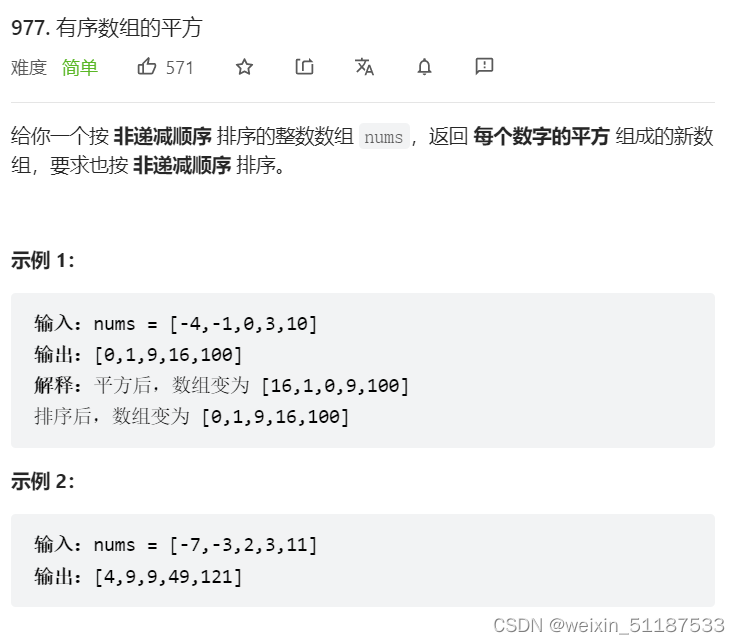
2022-7-6 Leetcode 977. Square of ordered array
Custom thread pool rejection policy
2022-7-6 使用SIGURG来接受外带数据,不知道为什么打印不出来
Use of polarscatter function in MATLAB

Help tenants
Navicat运行sql文件导入数据不全或导入失败
JS slow motion animation principle teaching (super detail)
2022-7-6 beginner redis (I) download, install and run redis under Linux
随机推荐
如何让join跑得更快?
C语言数组相关问题深度理解
供应链供需预估-[时间序列]
[dark horse morning post] Huawei refutes rumors about "military master" Chen Chunhua; Hengchi 5 has a pre-sale price of 179000 yuan; Jay Chou's new album MV has played more than 100 million in 3 hours
How did Guotai Junan Securities open an account? Is it safe to open an account?
Scrapy教程经典实战【新概念英语】
[QNX hypervisor 2.2 user manual]6.3.4 virtual register (guest_shm.h)
LeetCode简单题分享(20)
Write it down once Net a new energy system thread surge analysis
Redis只能做缓存?太out了!
10 pictures open the door of CPU cache consistency
648. 单词替换 : 字典树的经典运用
记一次 .NET 某新能源系统 线程疯涨 分析
《厌女:日本的女性嫌恶》摘录
Help tenants
MongoDB优化的几点原则
User management summary of mongodb
. Net core about redis pipeline and transactions
2022-7-6 Leetcode27. Remove the element - I haven't done the problem for a long time. It's such an embarrassing day for double pointers
"New red flag Cup" desktop application creativity competition 2022