当前位置:网站首页>The memorandum model of behavior model
The memorandum model of behavior model
2020-11-06 21:35:00 【Irving the procedural ape】
Catalog
- Definition and characteristics
- Structure and Implementation
- The structure of the pattern
- The realization of pattern
- Application scenarios
- Expand : Mixed with prototype patterns
Everyone makes mistakes sometimes , I hope there is a kind of “ Regret ” Make up for your own mistakes , Let yourself start over , But the reality is brutal . In computer applications , Customers also make mistakes often , Can you provide “ Regret ” Give it to them ? Of course you can , And it's necessary . This function consists of “ Memo mode ” To achieve .
In fact, many applications provide this function , Such as Word、 Notepad 、Photoshop、Eclipse Wait for the software to press when editing Ctrl+Z Key combination can undo the current operation , Restore the document to its previous state ; And in IE Back key in 、 Rollback operation in database transaction management 、 Save intermediate results when playing games 、 Database and operating system backup operation 、 The repentance function in chess games belongs to this kind of game .
Memo mode can record the internal state of an object , When the user regrets, the current operation can be undone , Restore data to its original state .
Definition and characteristics
Memorandum (Memento) Pattern The definition of : Without breaking encapsulation , Capture the internal state of an object , And save the state outside the object , So that the object can be restored to the original saved state when needed later , This mode is also called snapshot mode .
Memo mode is an object behavior pattern , Its main advantages are as follows :
- Provides a mechanism for restoring state : When the user needs to be able to more easily restore the data to a historical state .
- Realize the encapsulation of internal state : In addition to the founders who created it , No other object can access this state information .
- Simplified the originator : Initiators do not need to manage and save individual backups of their internal state , All status information is stored in the memo , And managed by the manager , This is in line with the principle of single responsibility .
Its main drawback is : High resource consumption , If the internal state information to be saved is too much or too frequent , It will occupy a large amount of memory resources .
Structure and Implementation
The core of the memo pattern is to design the memo class and the manager class for managing the memo , Now let's learn about its structure and implementation .
The structure of the pattern
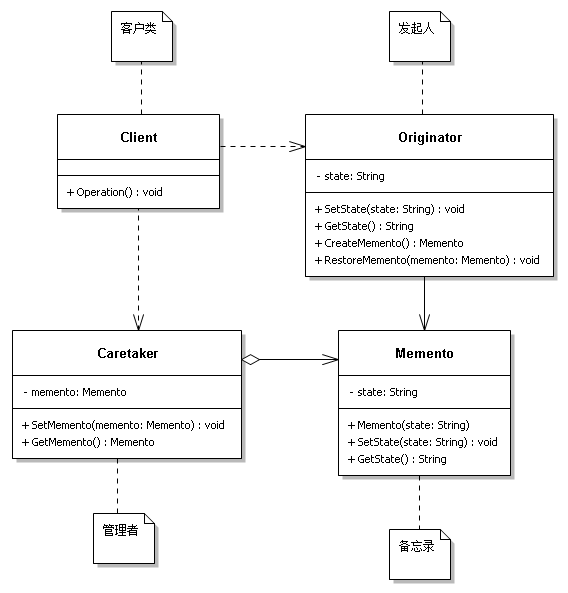
The main roles of the memo model are as follows :
- Originator (Originator) role : Record the internal status information of the current time , Provides the ability to create and recover memo data , Implement other business functions , It has access to all the information in the memo .
- Memorandum (Memento) role : Responsible for storing the internal state of the initiator , Provide these internal states to the originator when needed .
- managers (Caretaker) role : Manage memos , Provides the ability to save and retrieve memos , But it cannot access and modify the contents of the memorandum .
The structure of the memo mode is shown in the figure :
The realization of pattern
The implementation code of memo mode is as follows :
class Program{ static void Main(string[] args) { Originator or = new Originator(); Caretaker cr = new Caretaker(); or.SetState("S0"); Console.WriteLine(" The initial state :" + or.GetState()); cr.SetMemento(or.CreateMemento()); // Save state or.SetState("S1"); Console.WriteLine(" New status :" + or.GetState()); or.RestoreMemento(cr.GetMemento()); // Restore the state Console.WriteLine(" Restore the state :" + or.GetState()); Console.Read(); }}// Memorandum public class Memento{ private String state; public Memento(String state) { this.state=s.........版权声明
本文为[Irving the procedural ape]所创,转载请带上原文链接,感谢
边栏推荐
- Understanding formatting principles
- With this artifact, quickly say goodbye to spam messages
- From overseas to China, rancher wants to do research on container cloud market
- Top 5 Chinese cloud manufacturers in 2018: Alibaba cloud, Tencent cloud, AWS, telecom, Unicom
- 【涂鸦物联网足迹】物联网基础介绍篇
- To Lianyun analysis: why is IPFs / filecoin mining so difficult?
- ES6 learning notes (5): easy to understand ES6's built-in extension objects
- What is the purchasing supplier system? Solution of purchasing supplier management platform
- ado.net和asp.net的关系
- Exclusive interview of guests at | 2020 PostgreSQL Asia Conference: Wang Tao
猜你喜欢

An article will take you to understand CSS3 fillet knowledge

小熊派开发板实践:智慧路灯沙箱实验之真实设备接入

The role of theme music in games

Axios learning notes (2): easy to understand the use of XHR and how to package simple Axios

Exclusive interview of guests at | 2020 PostgreSQL Asia Conference: Wang Tao

嘉宾专访|2020 PostgreSQL亚洲大会阿里云数据库专场:曾文旌

实用工具类函数(持续更新)

检测证书过期脚本

An article will introduce you to HTML tables and their main attributes

Code generator plug-in and creator preform file analysis
随机推荐
Why is quicksort so fast?
An article taught you to download cool dog music using Python web crawler
[learning] interface test case writing and testing concerns
How does cglib implement multiple agents?
[forward] how to view UserData in Lua
Using an example to understand the underlying processing mechanism of JS function
File download manager realized by electron
行为型模式之解释器模式
Open source a set of minimalist front and rear end separation project scaffold
How to prepare for the system design interview
What is the tensor in tensorflow?
An article takes you to understand CSS pagination examples
意派Epub360丨你想要的H5模板都在这里,电子书、大转盘、红包雨、问卷调查……
2020-09-03:裸写算法:回形矩阵遍历。
Zero basis to build a web search engine of its own
事务的本质和死锁的原理
The legality of IPFs / filecoin: protecting personal privacy from disclosure
Tron smart wallet PHP development kit [zero TRX collection]
The 4th China BIM (digital construction) manager Summit Forum will be held in Hangzhou in 2020
Call analysis of start method in JNI thread and callback analysis of run method