当前位置:网站首页>Introduction and use of redis
Introduction and use of redis
2022-07-06 13:08:00 【Geometer】
redis summary
redis It's a non relational database , The key value database deployed in the slave , Its value There are five types , Respectively string,set,hash,list,zset
STRING: You can store strings , Integer or floating point , You can operate on the whole string or strings in the string , When it is an integer or floating-point number , Self increase or self decrease operation can be carried out
LIST: Main storage list . Press or eject both ends , You can trim multiple elements , Keep only the elements in one range
SET : You can add, get, and remove individual elements , Calculate and hand in , and , Difference set , Get elements randomly from the collection
HASH: You can add, get, and remove individual elements , Check if the element exists , Get all key value pairs
ZSET: Add get delete element , Get the element according to the score range or member , Calculate the rank of a key
The underlying implementation of data structure
string:
struct sdshdr{
int len;// Length of occupied space
int free;// Length of remaining space
char buf[];// Data space
}
Compared to calling directly c The advantage of string is that it can directly save the length without traversal . In addition, it can also reduce the problem of buffer overflow , Because the remaining length will be checked before use .
list:
Double linked list , But more about it
typedef struct listNode{
struct listNode *prev;
struct listNode * next;
void * value;
}
hash:
typedef struct dictht {
// Hash table array
dictEntry **table;
// Hash table size
unsigned long size;
// Hash table size mask , Used to calculate index values
unsigned long sizemask;
// The number of existing nodes in the hash table
unsigned long used;
}
typeof struct dictEntry{
// key
void *key;
// value
// Different key values may correspond to different types ,
// Therefore use union To solve this problem
union{
void *val;
uint64_tu64;
int64_ts64;
}
struct dictEntry *next;
}
When hash When the conflict , Using zippers to resolve conflicts
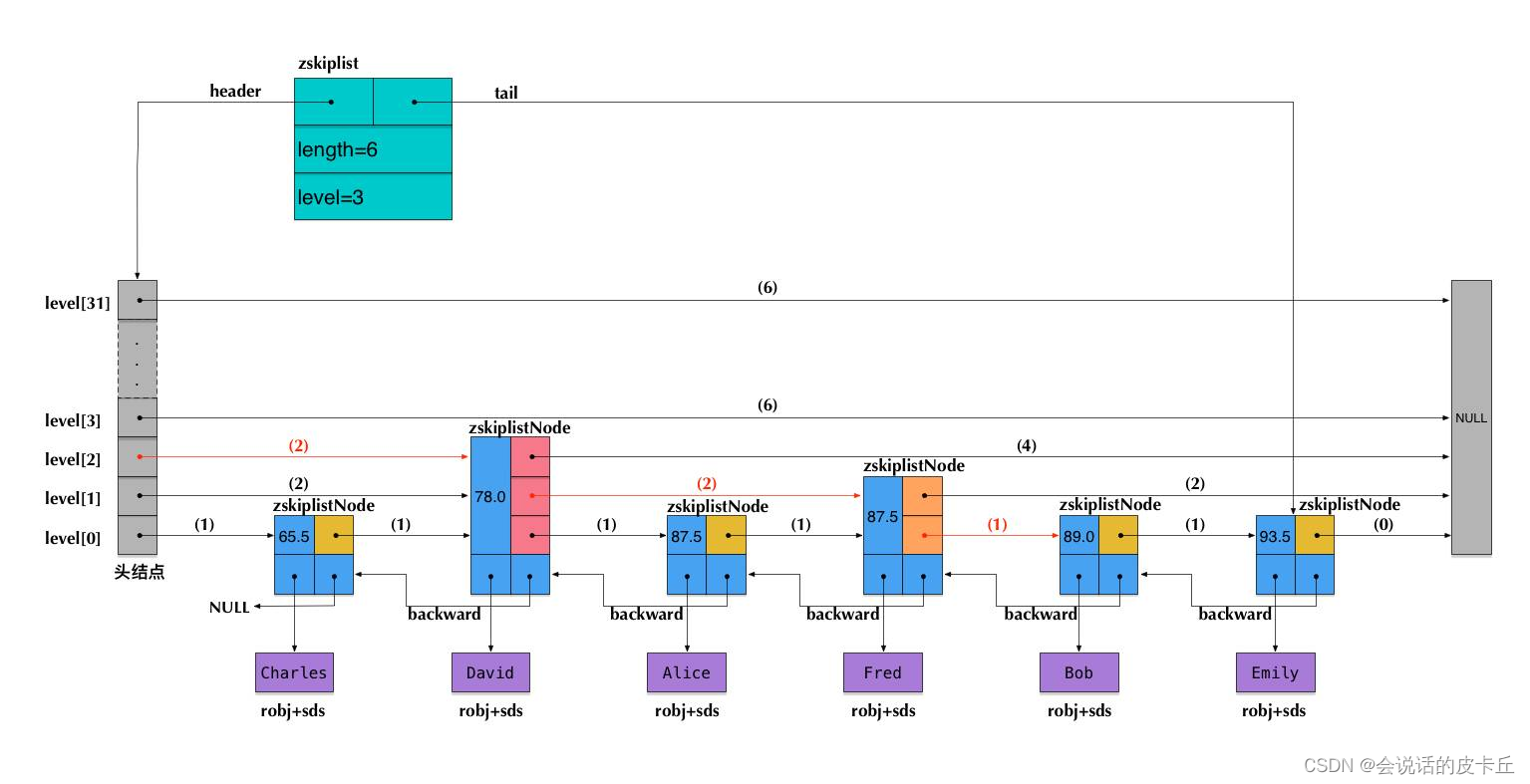
zset:
The bottom layer is realized by jumping table , It can be used to replace binary balanced tree
Skip list (skiplist) Is an ordered data structure , It maintains multiple pointers to other nodes in each node , So as to achieve the purpose of quickly finding access nodes . The jump table is a kind of randomized data , A jump table stores elements in a hierarchical linked list in an orderly manner , Efficiency is as good as the balance tree —— lookup 、 Delete 、 Add and other operations can be done in O(logn) Finish... In the expected time .
// Specific implementation of node
typedef struct zskiplistNode{
// layer
struct zskiplistLevel{
// Forward pointer
struct zskiplistNode *forward;
// span
unsigned int span;
} level[];
// Back pointer
struct zskiplistNode *backward;
// The score is
double score;
// member object
robj *obj;
}
typedef struct zskiplist {
// Header node and footer node
structz skiplistNode *header,*tail;
// The number of nodes in the table
unsigned long length;
// The number of layers of the node with the largest number of layers in the table
int level;
}zskiplist;
Friends who don't know about it can see the following post
Skip List– Jump watch ( There is no one of the most detailed jump table articles in the whole network )
set:
typedef struct intset{
// Encoding mode int16_t、int32_t、int64_t
uint32_t enconding;
// Number of elements contained in the collection
uint32_t length;
// Array to hold elements
int8_t contents[];
}
intset yes Redis One of the memory data structures , And before sds、 skiplist、dict、adlist
And other general data , It is Redis Peculiar , Used to implement Redis Of Set structure ( When the element is small and of numeric type ), Its characteristics are :Element type can only be numeric . There are three types of elements :int16_t、int32_t、int64_t. The elements are in order , Do not repeat .
intset and sds equally , Memory is continuous , It's like an array .
边栏推荐
- 闇の連鎖(LCA+树上差分)
- 【无标题】
- Employment of cashier [differential constraint]
- 一文搞定 UDP 和 TCP 高频面试题!
- PRIDE-PPPAR源码解析
- 图书管理系统小练习
- 10 minutes pour maîtriser complètement la rupture du cache, la pénétration du cache, l'avalanche du cache
- [algorithm] sword finger offer2 golang interview question 6: sum of two numbers in the sorting array
- 4.30 dynamic memory allocation notes
- [Chongqing Guangdong education] Shandong University College Physics reference materials
猜你喜欢
![[algorithm] sword finger offer2 golang interview question 5: maximum product of word length](/img/e0/cea31070d6365eb57013cdead4a175.png)
[algorithm] sword finger offer2 golang interview question 5: maximum product of word length

TYUT太原理工大学2022数据库大题之分解关系模式
2年经验总结,告诉你如何做好项目管理
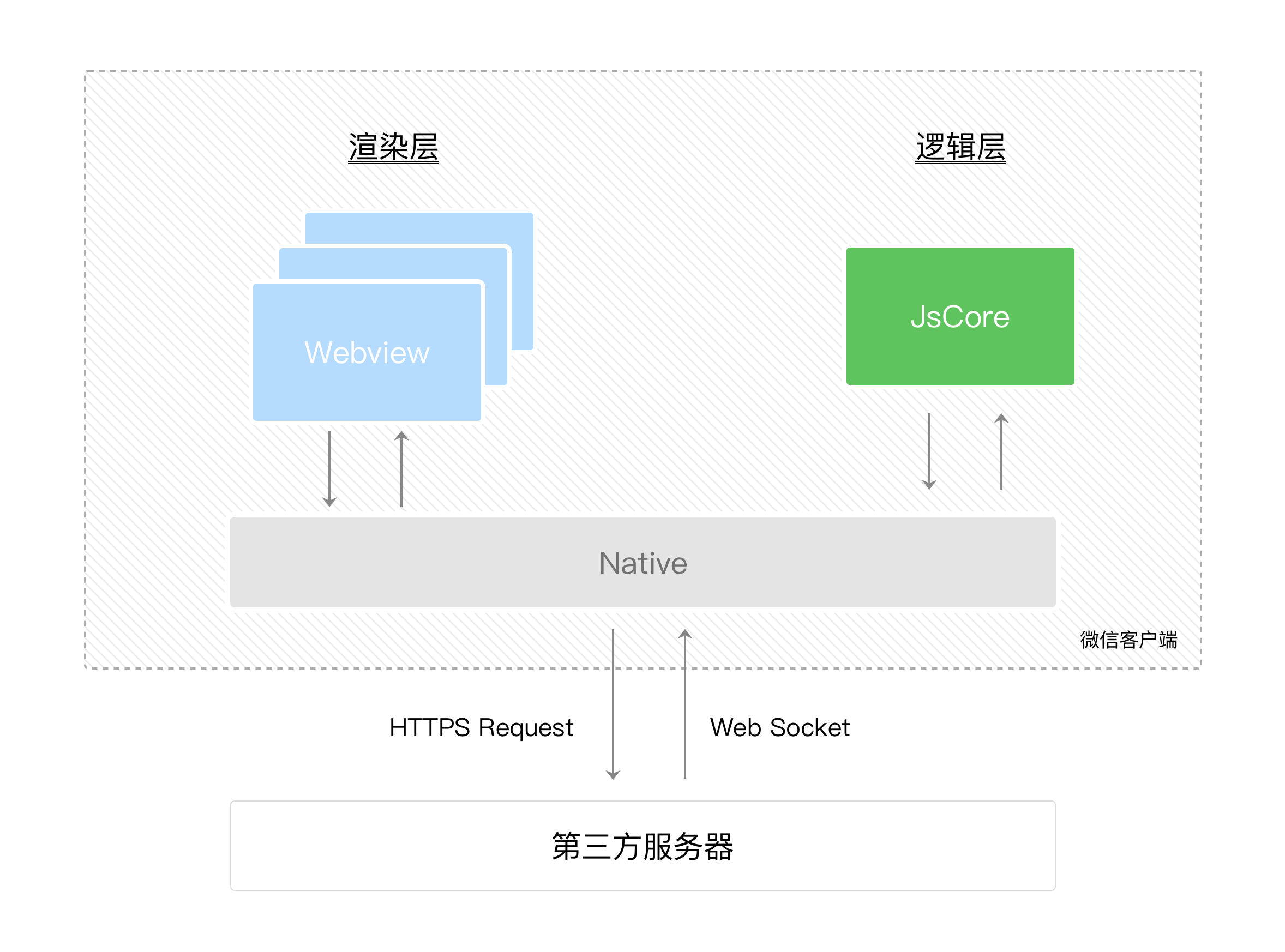
微信小程序开发心得

Experience summary of autumn recruitment of state-owned enterprises
TYUT太原理工大学2022软工导论大题汇总
![[算法] 剑指offer2 golang 面试题3:前n个数字二进制形式中1的个数](/img/64/0f352232359c7d44f12b20a64c7bb4.png)
[算法] 剑指offer2 golang 面试题3:前n个数字二进制形式中1的个数
十分鐘徹底掌握緩存擊穿、緩存穿透、緩存雪崩
On March 15, the official version of go 1.18 was released to learn about the latest features and usage
一文搞定 UDP 和 TCP 高频面试题!
随机推荐
Excel导入,导出功能实现
[算法] 剑指offer2 golang 面试题3:前n个数字二进制形式中1的个数
[algorithm] sword finger offer2 golang interview question 5: maximum product of word length
Itext 7 生成PDF总结
2022国赛Re1 baby_tree
[algorithm] sword finger offer2 golang interview question 2: binary addition
【GNSS】抗差估计(稳健估计)原理及程序实现
【GNSS数据处理】赫尔默特(helmert)方差分量估计解析及代码实现
TYUT太原理工大学2022数据库考试题型大纲
雇佣收银员【差分约束】
Pride-pppar source code analysis
Record: Navicat premium can't connect to MySQL for the first time
[算法] 剑指offer2 golang 面试题10:和为k的子数组
The port is occupied because the service is not shut down normally
使用rtknavi进行RT-PPP测试
系统设计学习(三)Design Amazon‘s sales rank by category feature
Tyut Taiyuan University of technology 2022 introduction to software engineering examination question outline
First acquaintance with C language (Part 1)
Redis介绍与使用
架构师怎样绘制系统架构蓝图?