当前位置:网站首页>Ten minutes to thoroughly master cache breakdown, cache penetration, cache avalanche
Ten minutes to thoroughly master cache breakdown, cache penetration, cache avalanche
2022-07-06 13:02:00 【Java misty rain】
Write an article to slow down , Share the old stereotype : Cache breakdown 、 Cache penetration 、 Cache avalanche .
Before we understand these three problems , We need to understand , Commonly used distributed cache Redis The amount of single machine concurrency can reach 10000 , Common relational databases MySQL The general concurrency is 1000 , The amount of concurrency they support may be ten times worse , Therefore, the traffic should be intercepted in the cache layer as much as possible .
Why? ? It's like draining more water in a big lake , It may wash out the small river , I don't know if you've heard of —— The water of the Yangtze River comes up from the sky , Baiyangdian can't hold .
Contents of this article :
Cache breakdown
What is cache breakdown
How to solve
Cache penetration
What is cache penetration
How to solve cache penetration
Cache avalanche
What is a cache avalanche
How to solve the cache avalanche
Text :
What is cache breakdown
Start with cache breakdown .
Cache breakdown : A large number of concurrent visits key Expire at a certain time , Cause all requests to be typed directly in DB On .

Cache breakdown
Cache breakdown will increase the load on the database , Let's see how to alleviate .
How to solve
Lock update
The query cache , It is found that there is no... In the cache , Lock , Let other threads wait , Let only one thread update the cache .

Lock update
Asynchronous update
Another possible solution is to set the cache to never expire . How to update the cache ? Update the cache asynchronously .
For example, a daemon thread is set in the background to update the cache regularly , But this timing is difficult to grasp .
Asynchronous update mechanism is actually more suitable for cache preheating .
Cache penetration
What is cache penetration
Cache penetration : Cache penetration refers to data that does not exist in both the query cache and the database , In this way, each request is directly called to the database , It's like the cache doesn't exist .
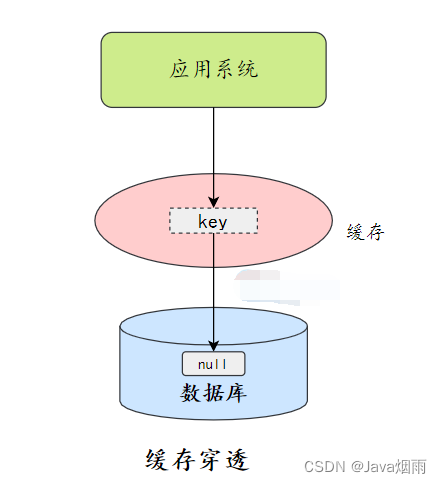
Cache penetration
Cache penetration will cause non-existent data to be queried in the storage layer every time it is requested , Lost the significance of cache protection back-end storage .
Cache penetration may increase the back-end storage load , If a large number of storage layer null hits are found , Maybe there is a cache penetration problem .
Cache penetration can occur for two reasons :
Own business code problem
A malicious attack , Reptiles cause empty hits
Let's see how to solve .
How to solve cache penetration
Cache null / The default value is
One way is after a database miss , Save an empty object or default value to the cache , Then access the data , It gets it from the cache , This protects the database .
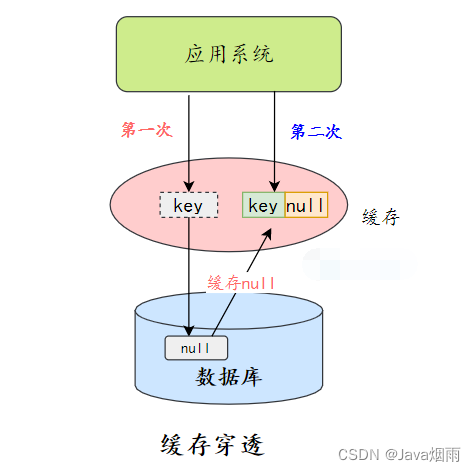
Cache null
There are two major problems with caching null values :
Null values are cached , It means that there are more keys in the cache layer , Need more memory space ( If it's an attack , The problem is more serious ), More effective
The method is to set a shorter expiration time for this kind of data , Let it automatically remove .
The data of cache layer and storage layer will be inconsistent for a period of time , It may have some impact on the business .
For example, the expiration time is set to 5 minute , If the storage layer adds this data at this time , Then there will be inconsistencies between the cache layer and the storage layer data in this period of time .
At this time, you can use message queue or other asynchronous methods to clean up the empty objects in the cache .
The bloon filter
In addition to caching empty objects , We can also store and cache before , Add a bloom filter , Do a layer of filtering .
The bloom filter will store whether the data exists , If you judge that the data is not, you can no longer , No access to storage .
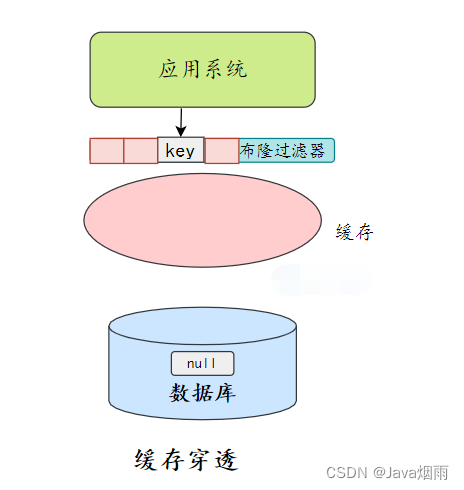
The bloom filter filters
What's the bloom filter ? Find out if it will be slow ?
What is a bloon filter ?
I don't know how much you know about hash tables , The bloom filter is a similar thing .
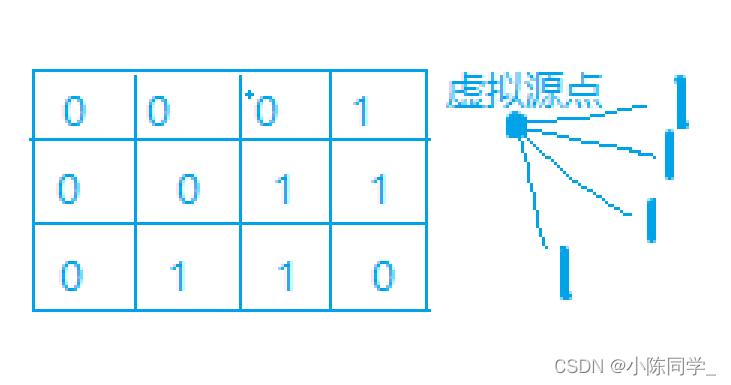
It is a continuous data structure , Each storage bit is a bit, namely 0 perhaps 1, To identify whether the data exists .
When storing data , Use K A different hash function maps this variable to bit Of the list K A little bit , Set them as 1.
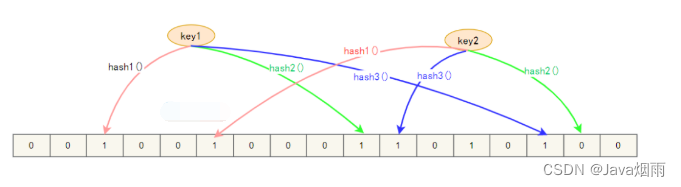
Bulon filter structure
We judge the cache key Whether there is , Again ,K Hash functions , Mapping to bit On the list K A little bit , Judgment is not 1:
If it's not 1, that key non-existent ;
If it's all 1, It just means key Possible .
As for why ? Because hash functions may collide .
There are two main solutions for cache penetration , Let's make a simple comparison :
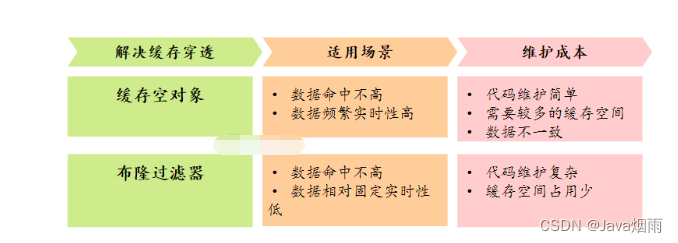
Cache empty object core bloom filter scheme comparison
Cache avalanche
Next, let's look at the most serious situation , Cache avalanche .
What is a cache avalanche
Cache avalanche : When ⼀ All the time ⽣⼤ Large scale cache invalidation , For example, the cache service is down 、 A lot of key Expire at the same time , The result is ⼤ The quantity request comes in and calls directly to DB On , May cause the whole system to crash , It's called an avalanche .
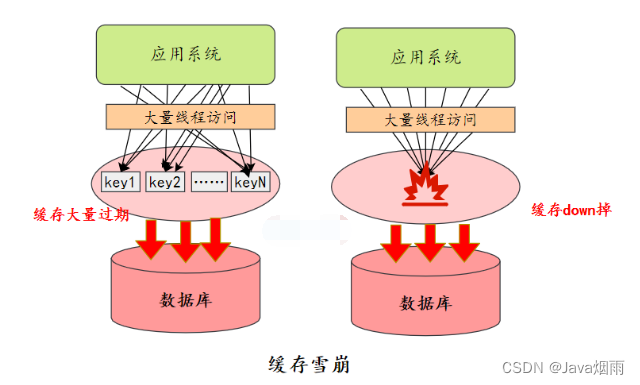
.... Bloggers are too lazy, too many words , I don't want to write. .... The article has been finished PDF, Friends in need can get it for free by private letter !
边栏推荐
- 《软件测试》习题答案:第一章
- [算法] 剑指offer2 golang 面试题9:乘积小于k的子数组
- 几道高频的JVM面试题
- Itext 7 生成PDF总结
- 记录:newInstance()过时的代替方法
- MySQL error warning: a long semaphore wait
- [Chongqing Guangdong education] reference materials for regional analysis and planning of Pingdingshan University
- KF UD decomposition pseudo code implementation advanced [2]
- The service robots that have been hyped by capital and the Winter Olympics are not just a flash in the pan
- [Chongqing Guangdong education] Shandong University College Physics reference materials
猜你喜欢
![[dry goods] cycle slip detection of suggestions to improve the fixed rate of RTK ambiguity](/img/9d/7284c1399964d3fb48886f12e4941c.jpg)
[dry goods] cycle slip detection of suggestions to improve the fixed rate of RTK ambiguity
![[algorithm] sword finger offer2 golang interview question 12: the sum of the left and right sub arrays is equal](/img/11/ee0628a68542236fc641966579a31a.png)
[algorithm] sword finger offer2 golang interview question 12: the sum of the left and right sub arrays is equal
![[算法] 劍指offer2 golang 面試題2:二進制加法](/img/c2/6f6c3bd4d70252ba73addad6a3a9c1.png)
[算法] 劍指offer2 golang 面試題2:二進制加法
地球围绕太阳转
编辑距离(多源BFS)
微信小程序开发心得
FairyGUI增益BUFF数值改变的显示
![[algorithm] sword finger offer2 golang interview question 6: sum of two numbers in the sorting array](/img/d5/4bda133498f71ae9fd7a64c6cba8f0.png)
[algorithm] sword finger offer2 golang interview question 6: sum of two numbers in the sorting array

121 distributed interview questions and answers
Unity3D基础入门之粒子系统(属性介绍+火焰粒子系统案例制作)
随机推荐
[算法] 剑指offer2 golang 面试题10:和为k的子数组
[algorithm] sword finger offer2 golang interview question 5: maximum product of word length
【GNSS】抗差估计(稳健估计)原理及程序实现
Fabrication of fairygui simple Backpack
错误: 找不到符号
Fairygui joystick
Fabrication d'un sac à dos simple fairygui
《软件测试》习题答案:第一章
[algorithme] swordfinger offer2 golang question d'entrevue 2: addition binaire
【干货】提升RTK模糊度固定率的建议之周跳探测
FairyGUI复选框与进度条的组合使用
Dark chain lock (lca+ difference on tree)
KF UD分解之UD分解基础篇【1】
PR 2021 quick start tutorial, first understanding the Premiere Pro working interface
Heap sort [handwritten small root heap]
Pride-pppar source code analysis
基于rtklib源码进行片上移植的思路分享
[算法] 剑指offer2 golang 面试题5:单词长度的最大乘积
[Yu Yue education] guide business reference materials of Wuxi Vocational and Technical College of Commerce
[算法] 剑指offer2 golang 面试题4:只出现一次的数字