当前位置:网站首页>SQL Server(2)
SQL Server(2)
2022-07-05 17:29:00 【Game programming】
1. Create modification table ( Do not delete the original table , Make changes )
Add new column :alter table tb_student add Gender bit null
Delete old columns :alter table tb_student drop column Gender
Change column names :alter table tb_student alter column Gender bit null
Change column names : exec sp_rename 'tb_student.ClassNo','No','Column'
2. Create constraints
( Do not delete the original table , Create constraints )
alter table Table name add constraint PK_tb_student primary key ( Name )
alter table Table name add constraint FK_ Table name foreign key ( Name 1) references surface 2 name ( Name 2)
alter table Table name add constraint UK_ Table name _ Name unique( Name 1, Name 2)
alter table Table name add constraint CK_ Table name _ Name check( Conditional expression )
alter table Table name add constraint DK_ Table name default(0)for Name
3. insert data
A single piece of data is listed
insert (into) Table name ( Name 1, Name 2)values ( value 1, value 2,...)
insert (into) Table name ( Name 1, Name 2)select value 1, value 2....
union( be used for select Concatenation of insert statements )union all Allowing repetition is efficient
Multiple data listed
insert (into) Table name ( Name 1, Name 2)values ( value 1, value 2,...),( value 3, value 4,...),( value 5, value 6,...)
Clone data ( Copy data from one table to another )
1):insert Target table ( Name 1)select Name 2 from The original table
2):select Name 2 into surface 1 from surface 2
4. Update data
update Table name set Name 1= value where Name 2= value
( If not where Words , The data of the whole table has been modified )
5. Delete data
1):delete from Table name where Name = value
( Cause the value of the identification column to be discontinuous )
2):truncate table Table name ( Table data is cleared , Restore to initialization , The identity column is also restored )
truncate Efficient than delete high ,delete No data is deleted , Will be recorded in the log ,
,truncate No logging , Do not activate the trigger ,drop truncate It's instant operation
author : Late boat •
Game programming , A game development favorite ~
If the picture is not displayed for a long time , Please use Chrome Kernel browser .
边栏推荐
- ICML 2022 | meta proposes a robust multi-objective Bayesian optimization method to effectively deal with input noise
- Cartoon: how to multiply large integers? (integrated version)
- Embedded UC (UNIX System Advanced Programming) -1
- [binary tree] insufficient nodes on the root to leaf path
- 漫画:如何实现大整数相乘?(下)
- Little knowledge about C language (array and string)
- 独立开发,不失为程序员的一条出路
- WR | Jufeng group of West Lake University revealed the impact of microplastics pollution on the flora and denitrification function of constructed wetlands
- ICML 2022 | Meta提出魯棒的多目標貝葉斯優化方法,有效應對輸入噪聲
- Read the basic grammar of C language in one article
猜你喜欢
随机推荐
Use JDBC technology and MySQL database management system to realize the function of course management, including adding, modifying, querying and deleting course information.
域名解析,反向域名解析nbtstat
独立开发,不失为程序员的一条出路
flask解决CORS ERR 问题
ClickHouse(03)ClickHouse怎么安装和部署
URP下Alpha从Gamma空间到Linner空间转换(二)——多Alpha贴图叠加
华为云云原生容器综合竞争力,中国第一!
Winedt common shortcut key modify shortcut key latex compile button
BigDecimal除法的精度问题
Function sub file writing
7.Scala类
Tips for extracting JSON fields from MySQL
C#(Winform) 当前线程不在单线程单元中,因此无法实例化 ActiveX 控件
WR | 西湖大学鞠峰组揭示微塑料污染对人工湿地菌群与脱氮功能的影响
Debug kernel code through proc interface
Example tutorial of SQL deduplication
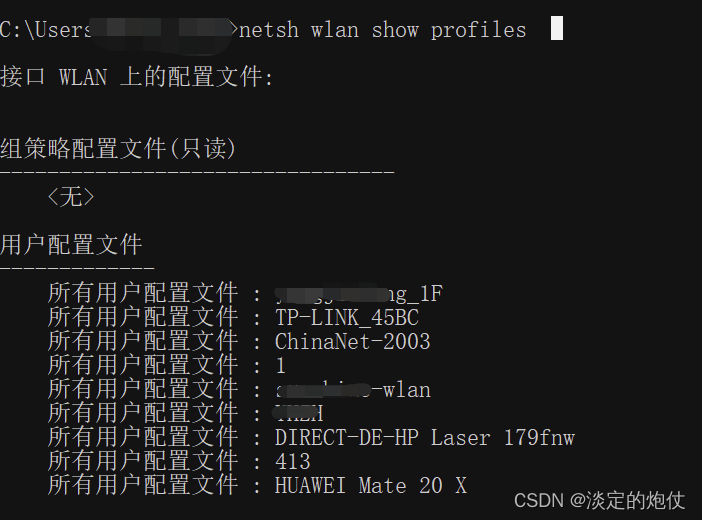
Check the WiFi password connected to your computer
【7.7直播预告】《SaaS云原生应用典型架构》大咖讲师教你轻松构建云原生SaaS化应用,难题一一击破,更有华为周边好礼等你领!
普通程序员看代码,顶级程序员看趋势
Flow characteristics of kitchen knife, ant sword, ice scorpion and Godzilla