当前位置:网站首页>Data communication foundation ACL access control list
Data communication foundation ACL access control list
2022-07-05 15:37:00 【GALi_ two hundred and thirty-three】
ACL Access control list
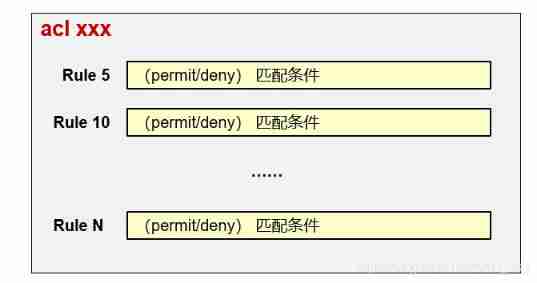
Access control list ACL(Access Control List) A series of permit or deny The sentences make up 、 A list of ordered rules , It realizes the classification of messages by matching the relevant information of messages ;
ACL It can only be used for message matching and distinguishing , It cannot realize the filtering function of messages , in the light of ACL The filtering function of the matched message , Specific mechanisms are needed to implement ( For example, it is used on the interface of the switch traffic-filter Command invocation ACL To filter messages ),ACL Just a matching tool ;
ACL In addition to being able to match messages , It can also be used to match routes ;
ACL It is a very widely used basic tool , Can be called by various applications or commands .
ACL Application
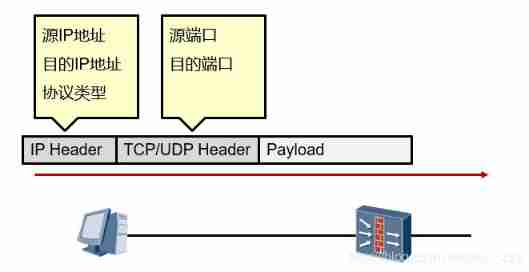
matching IP Traffic ( Source based 、 Objective IP Address 、 Protocol type 、 Port number and other elements )
stay Traffic-filter In the called
stay NAT In the called
Called in routing policy
stay IPSec VPN In the called
Called in the policy deployment of firewall
stay QoS In the called
ACL Can match one IP Source in packet IP Address 、 Purpose IP Address 、 Protocol type 、 Basic tools for elements such as source and destination ports ;ACL It can also be used to match routing entries .
identification ACL
Use digital identification ACL.
Use the name to identify ACL.
| Type of list | Scope of digital identification |
|---|---|
| Basic ACL | 2000-2999 |
| Advanced ACL | 3000-3999 |
ACL The classification of
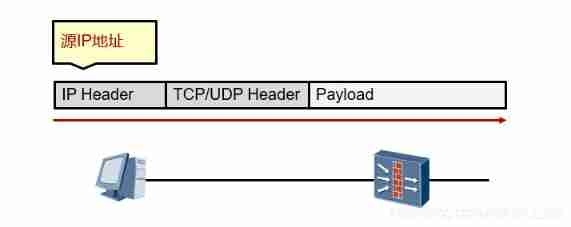
Basic access control list
- Only to IP The source in the head IP Address matching .
Advanced access control list
- Be able to target the source of the packet 、 Purpose IP Address 、 Protocol type 、 Source destination port number and other elements .
ACL Match order
Basic configuration
• Use numbers to create a basic ACL, And enter ACL View :
[Huawei] acl num
[Huawei-acl-basic-num]
basic ACL The range of numbers is 2000~2999.
• Create a rule (rule):
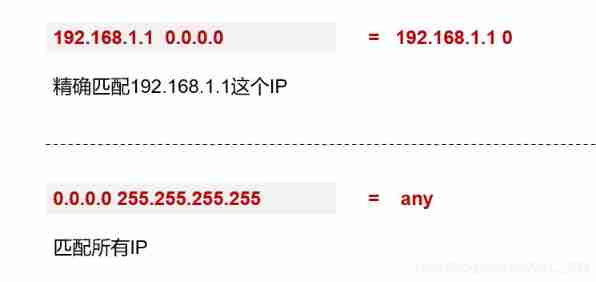
[Huawei-acl-basic-num] rule 5 {permit/deny} source src-address wildcard
notes : In a ACL You can create one or more rule, This is also ACL List in name (List) The origin of . Every one of them rule There is one. ID, The ID It can be automatically assigned by the system , It can also be allocated manually ,rule Press ID Order from small to large .
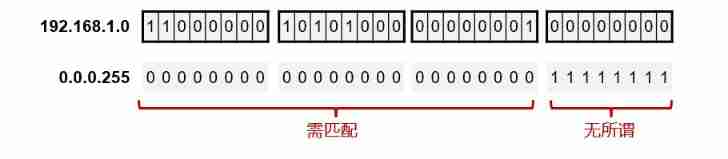
Wildcard( wildcard )
Wildcard is a 32 The value of the bit length , Used to indicate IP In the address , Which bits need to be strictly matched , It doesn't matter which bits .
Wildcards are usually expressed in dotted decimal form similar to netmask , But the meaning is completely different from netmask .
| Network mask | wildcard |
|---|---|
| for example 255.255.255.0 | for example 0.0.0.255 |
| Used to indicate IP In the address , Which bits are part of the network , What is the host part . | Used to indicate IP In the address , Which bits need to be strictly matched , It doesn't matter which bits . |
| In the netmask 1 The bit of represents the network part . | Wildcards are 1 The bit of indicates that no match is required . |
| In the netmask 0 The bit of indicates the host part . | Wildcards are 0 The bit representation of must be strictly matched . |
special wildcard
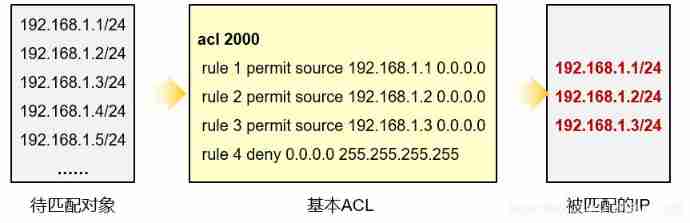
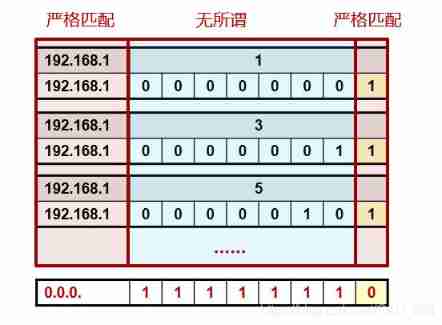
Example : matching 192.168.1.0/24 The last one in this subnet 8 Bit group based IP Address , for example 192.168.1.1、192.168.1.3、192.168.1.5 etc. .
basic ACL To configure
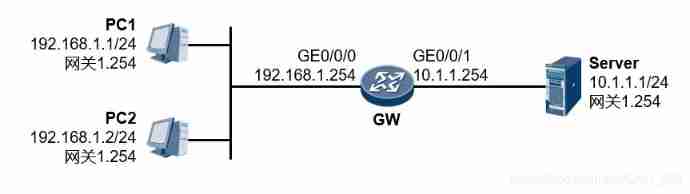
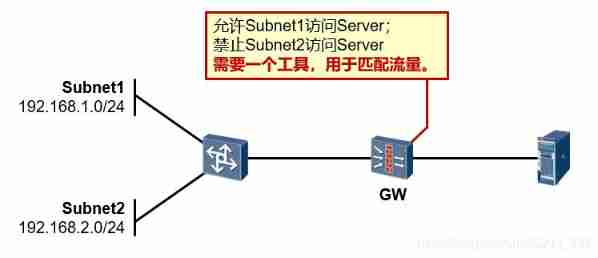
The experimental requirements :
In the initial case PC1 And PC2 Can access Server.
Now in GW Application on the interface of ACL, bring PC2 cannot access Server, Other users in the same network segment can access Server.
[GW]acl 2000
[GW-acl-basic-2000]rule deny source 192.168.1.2 0
[GW-acl-basic-2000]rule permit
[GW-acl-basic-2000]quit
[GW]interface GigabitEthernet 0/0/0
# traffic-filter be based on acl Packet filtering
[GW-GigabitEthernet0/0/0]traffic-filter inbound acl 2000
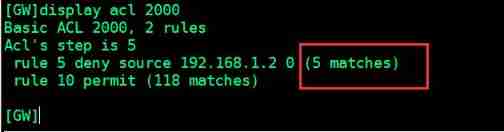
Rule permit The meaning of this rule is to match all , That is to say “permit any” It means . In fact, I was deceived ACL By interface level commands traffic-filter Invocation time , Has not been ACL Of rule The matched traffic is released by default , So in this case ,rule permit It's optional . But configure this rule after , stay display acl Is to be able to explicitly see being ACL The number of messages released by this rule .
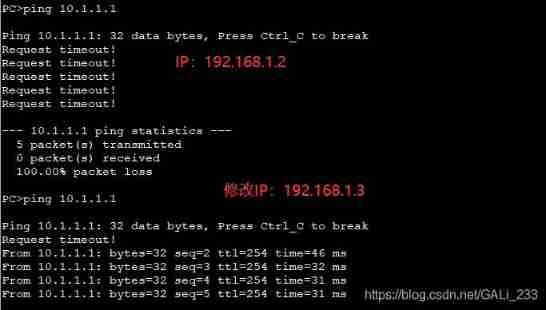
192.168.1.2 Traffic will be rejected , By this IP You can release
senior ACL To configure
Use numbers to create an advanced ACL, And enter ACL View :
[Huawei] acl num
[Huawei-acl-adv-num]
# senior ACL The range of numbers is 3000~3999.
according to IP Configure advanced ACL The rules :
[Huawei-acl-adv-num] rule 5 {permit/deny} ip source src-address wildcard destination dst-address wildcard
except IP agreement , senior ACL According to IP Match the upper layer protocol information carried , for example TCP、UDP、ICMP wait .

After configuration ,PC2 Will not be able to Telnet Server2, But it can. ping through Server2, In addition, other flows are allowed .
because ensp in PC Out-of-service Telnet, So they all use routers instead
[GW]acl 3000
[GW-acl-adv-3000]rule 5 deny tcp source 192.168.1.2 0 destination 10.1.1.2 0 des
tination-port eq 23 # eq 23 Or you could write it as eq telnet
[GW-acl-adv-3000]rule 10 permit ip # Allow others ip Flow through ( Optional )
[GW-acl-adv-3000]quit
[GW]int GigabitEthernet 0/0/0
[GW-GigabitEthernet0/0/0]traffic-filter inbound acl 3000
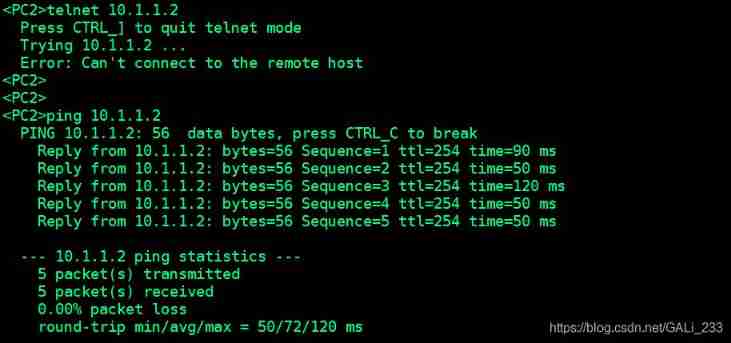
pc1 Sure telnet Server2
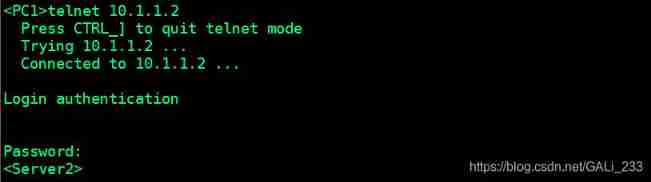
pc2 You can't Telnet Server2, But it can ping through
Add :
| Operators and syntax | meaning |
|---|---|
| equalportnumber | Equal to port number portnumber |
| greater-thanportnumber | Greater than port number portnumber |
| less-thanportnumber | Less than port number portnumber |
| not-equalportnumber | Not equal to port number portnumber |
| rangeportnumber1 portnumber2 | Between port number portnumber1 and portnumber2 Between |
establish acl name
Create a base with a name ACL:
[GW] acl name xxx basic
Create advanced with name ACL:
[GW] acl name xxx advance
边栏推荐
- Thymeleaf uses background custom tool classes to process text
- wxml2canvas
- 【 note 】 résoudre l'erreur de code IDE golang
- Basic JSON operations of MySQL 5.7
- 六种常用事务解决方案,你方唱罢,我登场(没有最好只有更好)
- wyt 。。
- Bugku's Ah Da
- swiper. JS to achieve barrage effect
- Coding devsecops helps financial enterprises run out of digital acceleration
- How to introduce devsecops into enterprises?
猜你喜欢
Bugku's eyes are not real
Detailed explanation of C language branch statements
Number protection AXB function! (essence)
Lesson 4 knowledge summary
Common MySQL interview questions
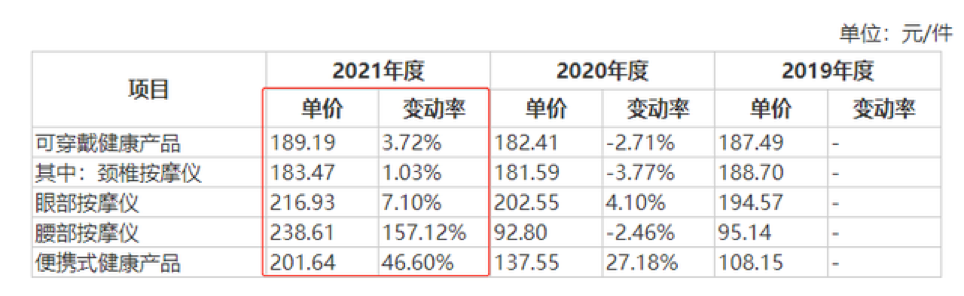
百亿按摩仪蓝海,难出巨头
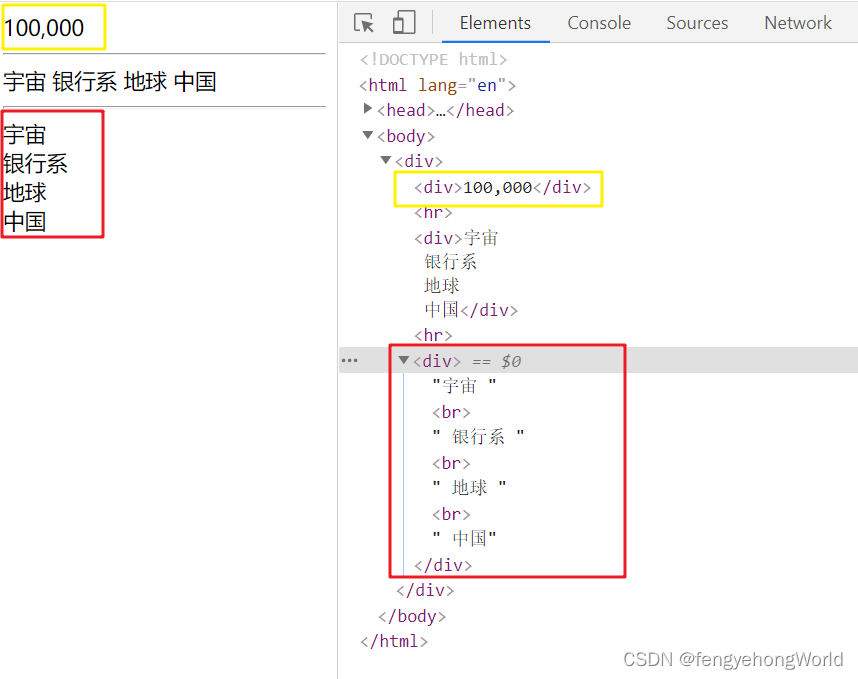
Thymeleaf uses background custom tool classes to process text
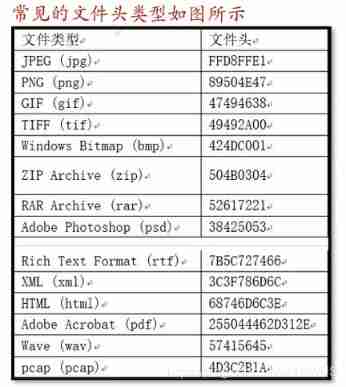
Misc Basic test method and knowledge points of CTF
Ctfshow web entry information collection
DVWA range clearance tutorial
随机推荐
How can I quickly check whether there is an error after FreeSurfer runs Recon all—— Core command tail redirection
Lesson 4 knowledge summary
Summary of the second lesson
[brief notes] solve the problem of IDE golang code red and error reporting
Thymeleaf uses background custom tool classes to process text
I'm fat, huh
The difference between SQL Server char nchar varchar and nvarchar
Object. defineProperty() - VS - new Proxy()
Redis' transaction mechanism
Garbage collection mechanism of PHP (theoretical questions of PHP interview)
Common PHP interview questions (1) (written PHP interview questions)
sql server学习笔记
Array sorting num ranking merge in ascending order
Bugku's eyes are not real
Brief introduction of machine learning framework
B站做短视频,学抖音死,学YouTube生?
I spring web upload
F. Min cost string problem solving Report
Bugku easy_ nbt
Value series solution report