当前位置:网站首页>Web container and IIS --- Middleware penetration method 1
Web container and IIS --- Middleware penetration method 1
2022-07-31 03:13:00 【GSflyy】
Common web containers
The web container is a service program, and a server port has a program that provides corresponding services. TOMCAT in java and IIS in ASP are all such containers.A server can have multiple containers
Common web containers:
IIS, Apache, Nginx, Tomcat, Jboss, Web Logic
Glossary
Middleware: Software that provides connection between system software and application software to facilitate communication between software.Between the middleware store and the operating system and higher-level applications.
Container: Provide an environment for the application components (JSP, PHP, ASP) in it, so that the application components in the container directly interact with the environment variable interface in the container, without paying attention to other system problems.
ps: Sometimes middleware and containers are common, that is, a piece of software can function as both middleware and container
Server: www server or http server, that is, the program that provides services to the browser
Introduction to IIS
What is IIS?
The full name is Internet Information Services (Internet Information Services), a basic Internet service based on Microsoft Windows provided by Microsoft Corporation.IIS includes services such as FTP/FTPS, NNTP, https/http, and smtp.
.net framework is the basic class library and the basic framework for program running
ASP.net is a collection of technologies used by .net to make websites.
IIs assumes that the web server is used to provide web browsing services and belongs to the system environment.
Generally use ASP.net to develop software, and then rely on IIS to provide services to the public network, the bottom layer of the software is .net framework
What is file parsing?
The server receives an http request, and IIS first decides how to process the request. What does IIS do based on it?According to the file extension.
The server obtains the suffix of the requested page, and then searches the server for an application that processes such a suffix. If no application that can process such a file is found, IIS returns the file directly to the client
IIS file parsing vulnerability
Reproduce the IIS6.0 file parsing vulnerability
First open the IIS service, open the Internet Information Services (IIS) Manager in the management tool

Open the following directory. The three buttons at the top of the middle represent the opening, suspension and suspension of the service
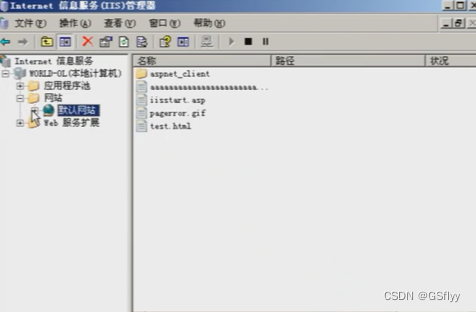
You can test whether the service is open by visiting 192.168.237.157/iisstart.asp
Exploitation
File parsing vulnerabilities are generally used in various upload vulnerabilities, and the suffix name of the file that users can upload is generally limited in the place where the file is uploaded.
In the actual vulnerability environment, IIS is generally matched with asp. If the uploading place restricts the .asp suffix, then the first thing that comes to mind should be to use other file suffixes supported by IIS. IIS parses asp scripts in addition to the .asp suffix.Has .cer and .asa
If the website says asp, cer, and asa are all filtered, it can only be bypassed by other methods, such as file parsing vulnerabilities.
IIS6.0 will have a logic error when processing file paths containing special symbols, which has long been a file parsing vulnerability.This vulnerability can be exploited in two completely different ways:
1. Create a new directory of test.asp, any file in this directory will be executed by IIS as asp
2. Upload a file named "test.asp;jpg", although the real suffix is jpg, but because there is a; number, the file will still be executed as an asp program
ps: Upgrading the IIS version can solve the problem
Apache file parsing
Introduction
Apache file parsing vulnerability is closely related to user configuration
Strictly speaking, this is a matter of user configuration.Here we will talk about the reasons for configuration errors and how to fix them, so you need to prepare your own environment.
Using Ubuntu's docker, then run the following command:
apt-get install apache2
apt-get install php7.0
apt-get install libapache2-mod-php7.0
Use docker ps to view the docker id in ubuntu and find the dockerid of apachephp
Use docker run -it -d -p 80:80 dockerid to start the container
docker ps to see if the container is started
docker exec -it dockerid bash set the container environment
Use the above three commands to configure the container environment
After configuring the environment, start the apache service
service apache2 start
Then access the container ip, and the apache page logo service appears normally open
Apache file parsing
Three ways to combine apache and php
CGI
FastCGI
Module
View the combination of Apache and php:
/usr/sbin/apachectl -M | grep php
边栏推荐
猜你喜欢

Addition and Subtraction of Scores in LeetCode Medium Questions

LeetCode简单题之找到和最大的长度为 K 的子序列
递归查询单表-单表树结构-(自用)
C#远程调试

YOLOV5 study notes (3) - detailed explanation of network module
MultipartFile文件上传

SQL injection Less54 (limited number of SQL injection + union injection)

TCP详解(三)

With 7 years of experience, how can functional test engineers improve their abilities step by step?
![[C language] Preprocessing operation](/img/69/0aef065ae4061edaf0d96b89846bf2.png)
[C language] Preprocessing operation
随机推荐
2022牛客多校联赛第四场 题解
Automation strategies for legacy systems
5. SAP ABAP OData 服务如何支持 $filter (过滤)操作
【HCIP】ISIS
The els block moves the boundary to the right, and accelerates downward.
The distance value between two arrays of LeetCode simple questions
12 Disk related commands
Annotation usage meaning
SIP协议标准和实现机制
QML的使用
Moxa NPort device flaw could expose critical infrastructure to devastating attack
【CocosCreator 3.5】CocosCreator get network status
YOLOV5 study notes (2) - environment installation + operation + training
Is interprofessional examination difficult?Low success rate of "going ashore"?Please accept this practical guide!
注解用法含义
TCP详解(三)
【Cocos Creator 3.5】缓动系统停止所有动画
STM32 problem collection
【Exception】The field file exceeds its maximum permitted size of 1048576 bytes.
学习DAVID数据库(1)