当前位置:网站首页>Maximum entropy model
Maximum entropy model
2022-07-04 01:26:00 【YaoHa_】
The principle of maximum entropy
principle : Select the model with the maximum entropy from the model set that meets the constraint conditions .
Ideas : From training data T Extract several features from , These characteristics are in T on Expectations of empirical distribution With them in the model p(x,y) The mathematical expectation of is equal , such , A feature corresponds to a constraint .
Suppose the classification model is a conditional probability distribution 𝑃(𝑌|𝑋), 𝑋 ∈ 𝒳 ⊆ 𝑅𝑛 Indicates input ,𝑌 ∈ 𝒴 Table condition overview
rate 𝑃(𝑌|𝑋) Output 𝑌. Given a training data set 𝑇 = {(𝑥1,𝑦1), (𝑥2,𝑦2), ⋯ , (𝑥𝑁,𝑦𝑁)}.
1. Consider the conditions that the model satisfies .
Joint distribution 𝑃(𝑋,𝑌) Empirical distribution and marginal distribution 𝑃(𝑋) The distribution of experience .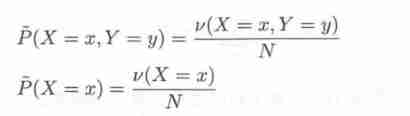
ν(𝑋 = 𝑥,𝑌 = 𝑦) Represents the sample in the training data (𝑥,𝑦) Frequency of occurrence ,
ν(𝑋 = 𝑥) Indicates that... Is entered in the training data 𝑥 Frequency of occurrence ,
𝑁 Represents the training sample size .
2. The characteristic function (feature function)𝑓(𝑥,𝑦) Description input 𝑥 And the output 𝑦 A fact between .
3. The characteristic function 𝑓(𝑥,𝑦) About the distribution of experience 𝑃̃(𝑋,𝑌) The expected value of is expressed as :
The characteristic function 𝑓(𝑥, 𝑦) About the model 𝑃(𝑌|𝑋) And experience distribution 𝑃̃(𝑋) The expected value of is expressed as :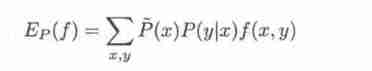
If the model can capture the information in the training data , Then we can assume that the two expectations are equal . namely 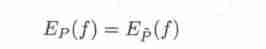
or 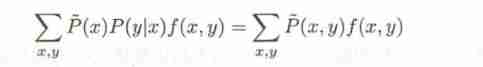
Definition : Suppose that the set of models satisfying all the constraints is 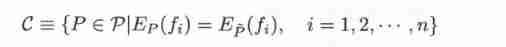
Defined in conditional probability distribution 𝑃(𝑌|𝑋) The conditional entropy on is 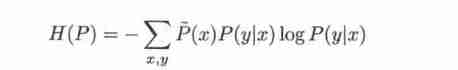
Then the model set C Intermediate conditional entropy H ( P ) H(P) H(P) The largest model is called the largest direct model . The logarithm in the formula is the natural logarithm .
For a given set of training data 𝑇 = {(𝑥1, 𝑦1), (𝑥2, 𝑦2), ⋯ , (𝑥𝑁, 𝑦𝑁)} And the characteristic function 𝑓𝑖(𝑥, 𝑦), 𝑖 = 1,2, ⋯ , 𝑛,
The maximum problem is rewritten as an equivalent minimum problem :
Using Lagrange multiplier method, the maximum entropy model is transformed from a constrained optimization problem into an equivalent unconstrained optimization problem . Solve the original problem by solving the dual problem .
Derivation process :
边栏推荐
- Cesiumjs 2022^ source code interpretation [8] - resource encapsulation and multithreading
- Oracle database knowledge points that cannot be learned (III)
- 中电资讯-信贷业务数字化转型如何从星空到指尖?
- Solution of cursor thickening
- C import Xls data method summary IV (upload file de duplication and database data De duplication)
- 7.1 学习内容
- Hbuilder link Xiaoyao simulator
- Introduction to A-frame virtual reality development
- Long article review: entropy, free energy, symmetry and dynamics in the brain
- MySQL uses the view to report an error, explain/show can not be issued; lacking privileges for underlying table
猜你喜欢

0 basic learning C language - nixie tube dynamic scanning display
Function: find the approximate value of the limit of the ratio of the former term to the latter term of Fibonacci sequence. For example, when the error is 0.0001, the function value is 0.618056.
Long article review: entropy, free energy, symmetry and dynamics in the brain

Technical practice online fault analysis and solutions (Part 1)
![Cesiumjs 2022^ source code interpretation [8] - resource encapsulation and multithreading](/img/d2/99932660298b4a4cddd7e5e69faca1.png)
Cesiumjs 2022^ source code interpretation [8] - resource encapsulation and multithreading
MySQL deadly serial question 2 -- are you familiar with MySQL index?
Luogu p1309 Swiss wheel
Thinkphp6 integrated JWT method and detailed explanation of generation, removal and destruction
查询效率提升10倍!3种优化方案,帮你解决MySQL深分页问题

Introduction to Tianchi news recommendation: 4 Characteristic Engineering
随机推荐
7.1 learning content
Future source code view -juc series
Fundamentals of machine learning: feature selection with lasso
51 MCU external interrupt
Lightweight Pyramid Networks for Image Deraining
Function: find the approximate value of the limit of the ratio of the former term to the latter term of Fibonacci sequence. For example, when the error is 0.0001, the function value is 0.618056.
[common error] UART cannot receive data error
Openbionics robot project introduction | bciduino community finishing
GUI application: socket network chat room
MySQL -- Introduction and use of single line functions
[dynamic programming] leetcode 53: maximum subarray sum
I don't care about you. OKR or KPI, PPT is easy for you
How to delete MySQL components using xshell7?
How to set the response description information when the response parameter in swagger is Boolean or integer
MPLS experiment
“疫”起坚守 保障数据中台服务“不打烊”
Luogu p1309 Swiss wheel
Sequence list and linked list
Hash table, string hash (special KMP)
Audio resource settings for U3D resource management