当前位置:网站首页>Hash table acwing 840 Simulated hash table
Hash table acwing 840 Simulated hash table
2022-07-02 12:42:00 【T_ Y_ F666】
Hashtable AcWing 840. Simulation hash table
Original link
AcWing 840. Simulation hash table
Algorithm tags
Hashtable
Ideas

Zipper method
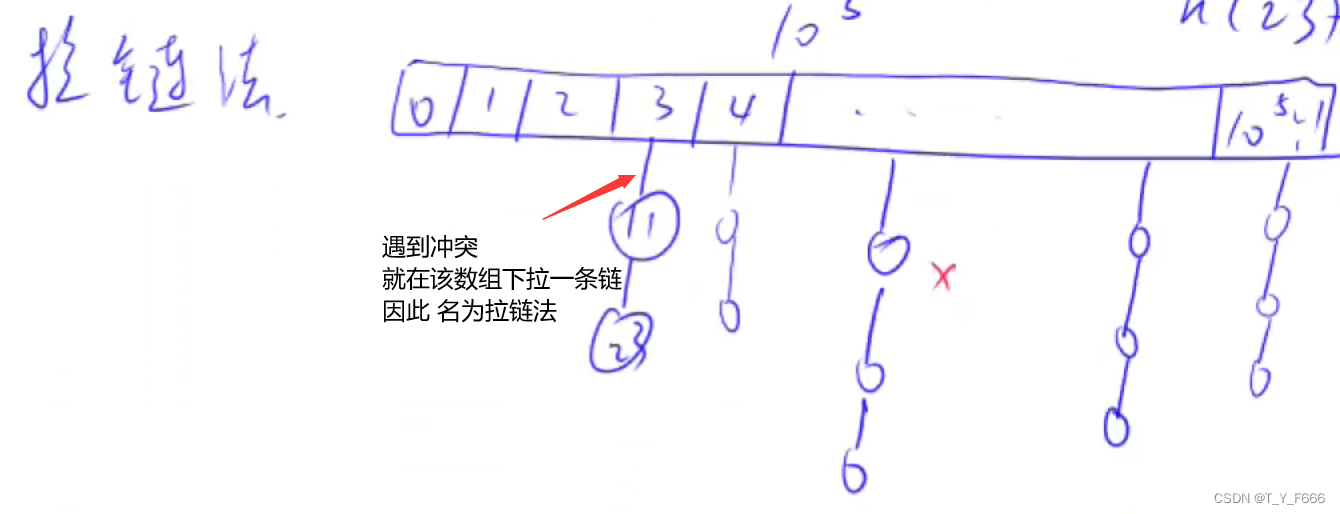
Open addressing
Code
#include<bits/stdc++.h>
#define int long long
#define rep(i, a, b) for(int i=a;i<b;++i)
#define Rep(i, a, b) for(int i=a;i>b;--i)
using namespace std;
const int N = 100003;
int a[N], e[N], h[N], ne[N], idx;
int s;
inline int read(){
int s=0,w=1;
char ch=getchar();
while(ch<'0'||ch>'9'){if(ch=='-')w=-1;ch=getchar();}
while(ch>='0'&&ch<='9') s=s*10+ch-'0',ch=getchar();
return s*w;
}
void put(int x) {
if(x<0) putchar('-'),x=-x;
if(x>=10) put(x/10);
putchar(x%10^48);
}
// Head insertion Insert the data into the corresponding hash The value is k Of hash In the table
void insert(int x){
// Ensure that negative numbers can also be mapped to hash In the table The modulo number is a prime number Conflicts can be minimized
int k=(x%N+N)%N;
e[idx]=x;
ne[idx]=h[k];
h[k]=idx++;
}
bool find(int x){
int k=(x%N+N)%N;
for(int i=h[k]; i!=-1; i=ne[i]){
if(e[i]==x){
return true;
}
}
return false;
}
signed main(){
ios::sync_with_stdio(false);
cin.tie(0);
cout.tie(0);
memset(h, -1, sizeof h);
int n=read();
while(n--){
char op[2];
scanf("%s", op);
int x=read();
if(op[0]=='I'){
insert(x);
}else{
if(find(x)){
puts("Yes");
}else{
puts("No");
}
}
}
return 0;
}
Originality is not easy.
Reprint please indicate the source
If it helps you Don't forget to praise and support 
边栏推荐
- Distributed machine learning framework and high-dimensional real-time recommendation system
- 怎样写一篇赏心悦目的英文数学论文
- Leetcode - < dynamic planning special> Jianzhi offer 19, 49, 60
- 中国交通标志检测数据集
- JSON序列化 与 解析
- js1day(输入输出语法,数据类型,数据类型转换,var和let区别)
- Interview with meituan, a 34 year old programmer, was rejected: only those under the age of 30 who work hard and earn little overtime
- Redis bloom filter
- 染色法判定二分图 AcWing 860. 染色法判定二分图
- JS6day(DOM结点的查找、增加、删除。实例化时间,时间戳,时间戳的案例,重绘和回流)
猜你喜欢
BOM DOM

What is the relationship between NFT and metauniverse? How to view the market? The future market trend of NFT
![[FFH] little bear driver calling process (take calling LED light driver as an example)](/img/e7/153ae9f1befc12825d277620049f9d.jpg)
[FFH] little bear driver calling process (take calling LED light driver as an example)

传感器 ADXL335BCPZ-RL7 3轴 加速度计 符合 RoHS/WEEE
线性DP AcWing 897. 最长公共子序列

模数转换器(ADC) ADE7913ARIZ 专为三相电能计量应用而设计

区间DP AcWing 282. 石子合并

Less than three months after the programmer was hired, the boss wanted to launch the app within one month. If he was dissatisfied, he was dismissed immediately

染色法判定二分图 AcWing 860. 染色法判定二分图

AI中台技术调研
随机推荐
[FFH] little bear driver calling process (take calling LED light driver as an example)
Redis sentinel mechanism and configuration
基于STM32的OLED 屏幕驱动
Direct control PTZ PTZ PTZ PTZ camera debugging (c)
线性DP AcWing 896. 最长上升子序列 II
Simple use of drools decision table
PR 2021 quick start tutorial, learn about the and functions of the timeline panel
About asp Net MVC project in local vs running response time is too long to access, the solution!
ASP. Net MVC default configuration, if any, jumps to the corresponding program in the specified area
通过反射执行任意类的任意方法
深拷貝 事件總線
Anti shake throttle
bellman-ford AcWing 853. 有边数限制的最短路
正确遍历EntryList方法
Window10 upgrade encountered a big hole error code: 0xc000000e perfect solution
JS10day(api 阶段性完结,正则表达式简介,自定义属性,过滤敏感词案例,注册模块验证案例)
Is the neural network (pinn) with embedded physical knowledge a pit?
线性DP AcWing 899. 编辑距离
Leetcode - Sword finger offer 59 - I, 59 - II
应用LNK306GN-TL 转换器、非隔离电源