当前位置:网站首页>mysql数据库的存储
mysql数据库的存储
2022-07-04 03:35:00 【CSDN问答】
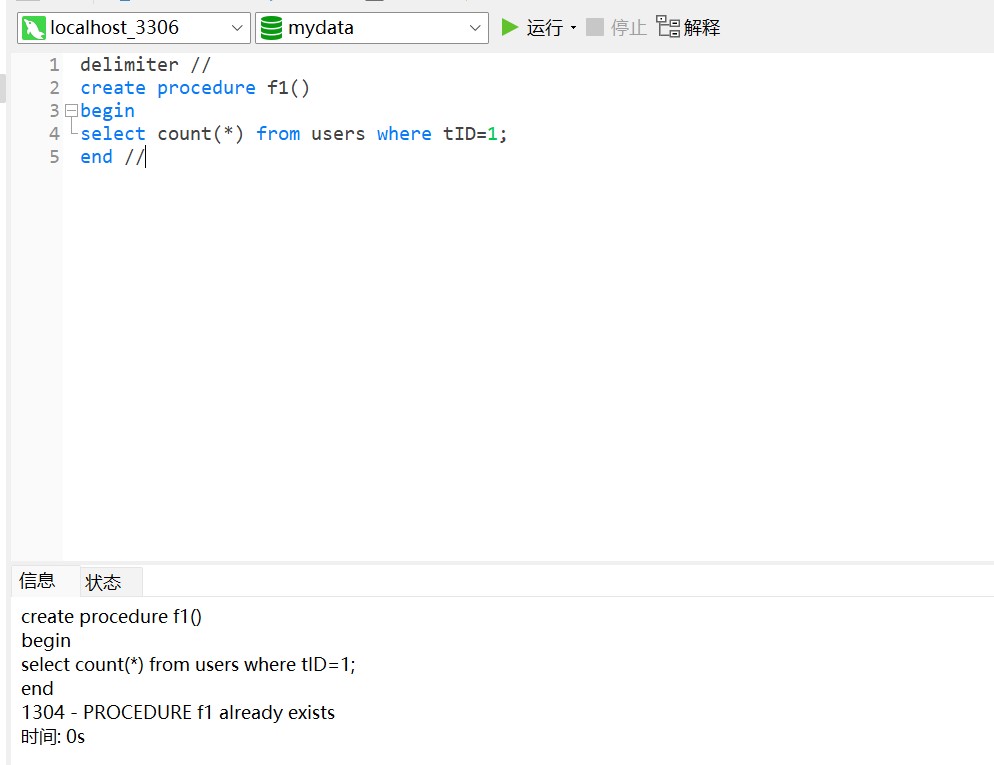
创建存储过程中,说我的语句有错

sql语句也没错,提示此存储已存在,无论创建什么名字都提示已存在,这个怎么解决?
边栏推荐
- Sword finger offer:55 - I. depth of binary tree
- Future源碼一觀-JUC系列
- SQL語句加强練習(MySQL8.0為例)
- what does ctrl + d do?
- System integration meets the three business needs of enterprises
- Zhihu million hot discussion: why can we only rely on job hopping for salary increase? Bosses would rather hire outsiders with a high salary than get a raise?
- Katalon框架测试web(二十六)自动发邮件
- Jenkins configures IP address access
- [PaddleSeg 源码阅读] PaddleSeg计算 mIoU
- Constantly changing harmonyos custom JS components during the Spring Festival - Smart Koi
猜你喜欢

Webhook triggers Jenkins for sonar detection

Cache general management class + cache httpcontext Current. Cache and httpruntime Differences between caches

MySQL one master multiple slaves + linear replication
用于TCP协议交互的TCPClientDemo
The 37 year old programmer was laid off, and he didn't find a job for 120 days. He had no choice but to go to a small company. As a result, he was confused
Es network layer
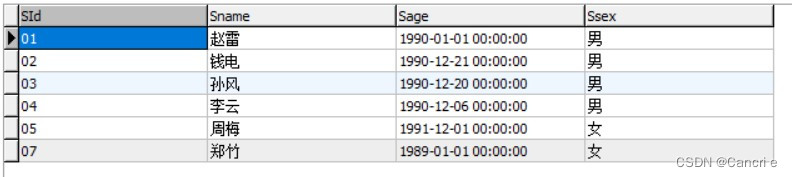
SQL语句加强练习(MySQL8.0为例)

What is cloud primordial?
![[Wu Enda deep learning] beginner learning record 3 (regularization / error reduction)](/img/e9/818bdfeae766dca7d2318b52b4424d.jpg)
[Wu Enda deep learning] beginner learning record 3 (regularization / error reduction)
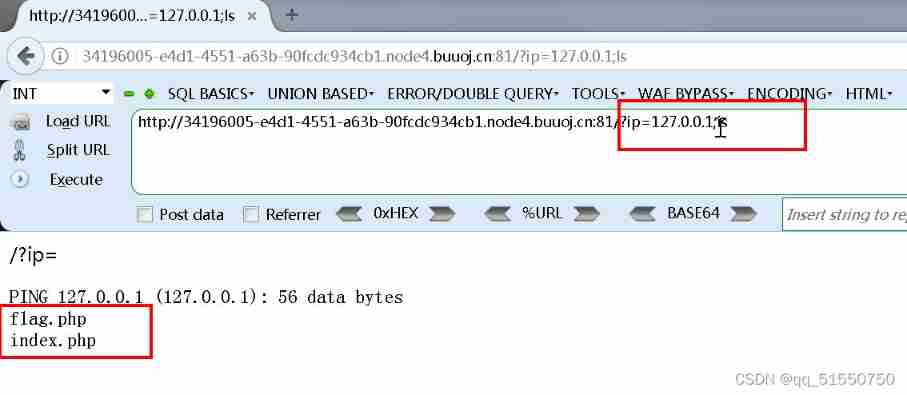
Command Execution Vulnerability - command execution - vulnerability sites - code injection - vulnerability exploitation - joint execution - bypass (spaces, keyword filtering, variable bypass) - two ex
随机推荐
Nbear introduction and use diagram
super_ Subclass object memory structure_ Inheritance tree traceability
JSON string conversion in unity
2022 Guangxi provincial safety officer a certificate examination materials and Guangxi provincial safety officer a certificate simulation test questions
Dare to climb here, you're not far from prison, reptile reverse actual combat case
JVM family -- heap analysis
[source code analysis] model parallel distributed training Megatron (5) -- pipestream flush
Jenkins configures IP address access
数据库SQL语句汇总,持续更新......
Objective-C member variable permissions
Command Execution Vulnerability - command execution - vulnerability sites - code injection - vulnerability exploitation - joint execution - bypass (spaces, keyword filtering, variable bypass) - two ex
渗透实战-guest账户-mimikatz-向日葵-sql提权-离线解密
Ningde times and BYD have refuted rumors one after another. Why does someone always want to harm domestic brands?
Recent learning fragmentation (14)
If you have just joined a new company, don't be fired because of your mistakes
Typical applications of minimum spanning tree
MySQL is dirty
Future源碼一觀-JUC系列
How to use websocket to realize simple chat function in C #
CSP drawing