当前位置:网站首页>Ctfshow web entry explosion
Ctfshow web entry explosion
2022-07-05 14:58:00 【Cwxh0125】
web21
First, enter an account password casually
Grab the bag
The account name and password entered are base64 Encrypted , Decoding found that its form is ——admin: password , Next, construct payload
Using a custom iterator The first paragraph is admin The second paragraph is “:” The third paragraph is the password for downloading the title attachment Conduct base64 After encryption, it can be exploded
web22

web23
Open to see php Code , First analyze the code , You can know token By md5 encryption , And its first = Fourteenth = 17th ,( first place + Fourteenth + 17th )/ first place = 31st place
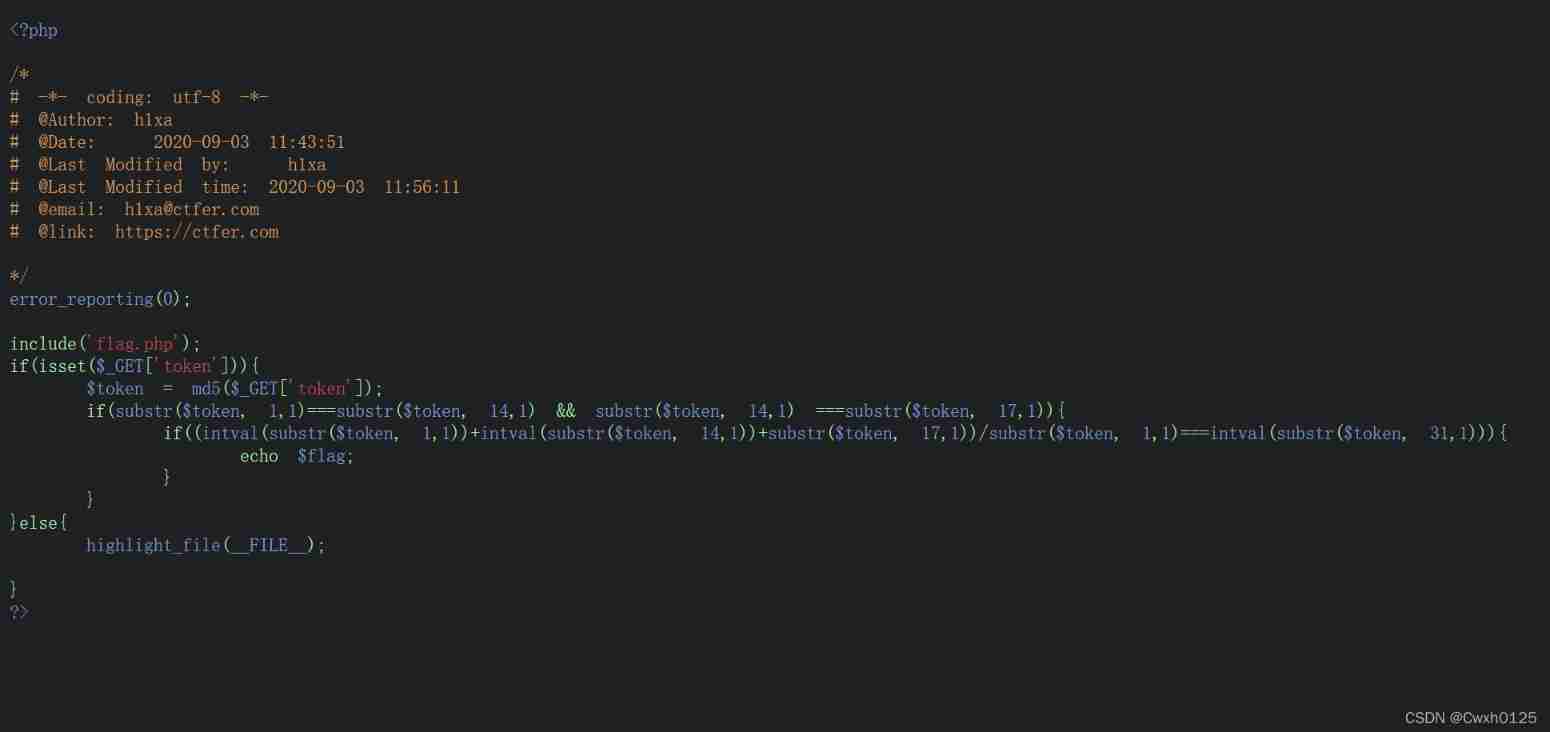
php Script
<?php
error_reporting(0);
$a="asdfghjklqwertyuiopzxcvbnm1234567890";
for($i=0;$i<36;$i++){
for($j=0;$j<36;$j++){
$token=$a[$i].$a[$j];
$token = md5($token);
if(substr($token, 1,1)===substr($token, 14,1) && substr($token, 14,1) ===substr($token, 17,1)){
if((intval(substr($token, 1,1))+intval(substr($token, 14,1))+substr($token, 17,1))/substr($token, 1,1)===intval(substr($token, 31,1))){
echo $a[$i].$a[$j];
exit(0);
}
}
}
}
?>
After running, get 3j The ginseng token=3j
web24
mt_scrand(seed) This function means , By distributing seed seeds , Then the seeds have , by mt_rand() Generate random Count 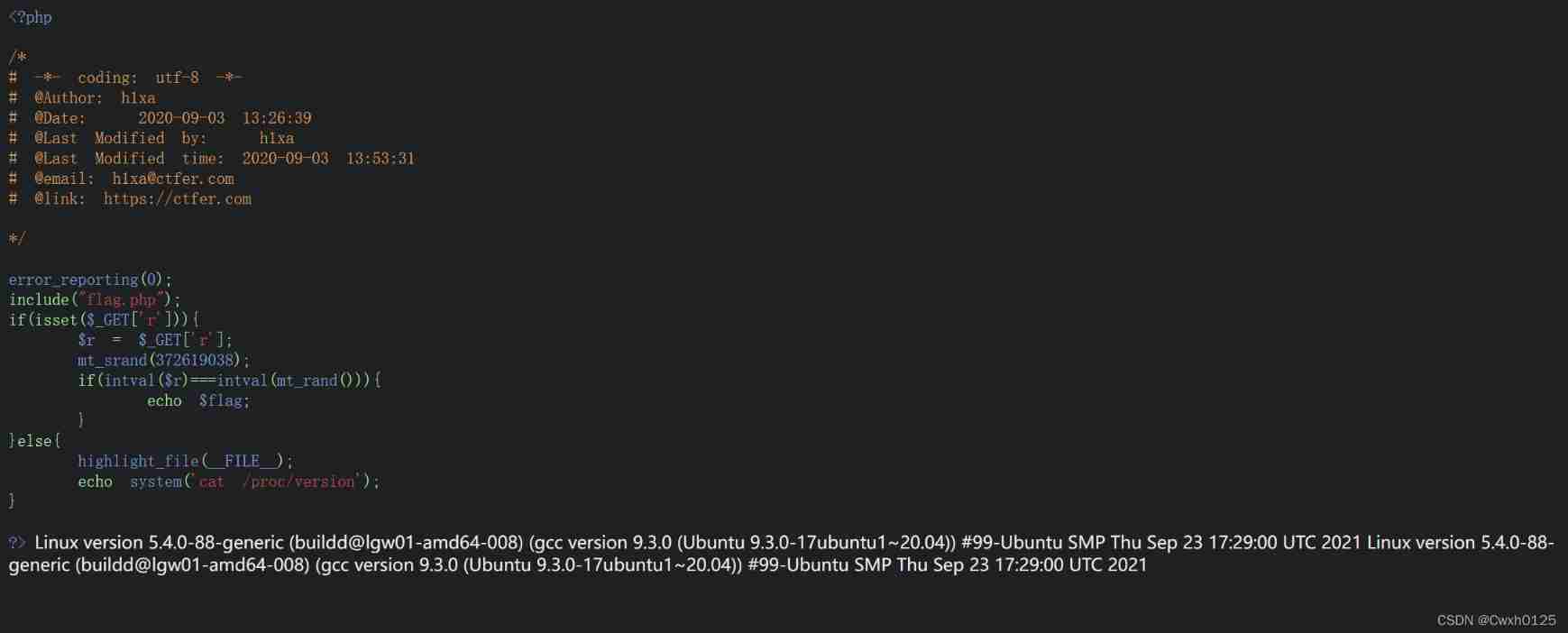
stay kali Run on Or by php Script ![]()
Run a pseudo-random number 1155388967 Pass on ?r=1155388967 Can get flag
web25
web26
Direct input I can't find out
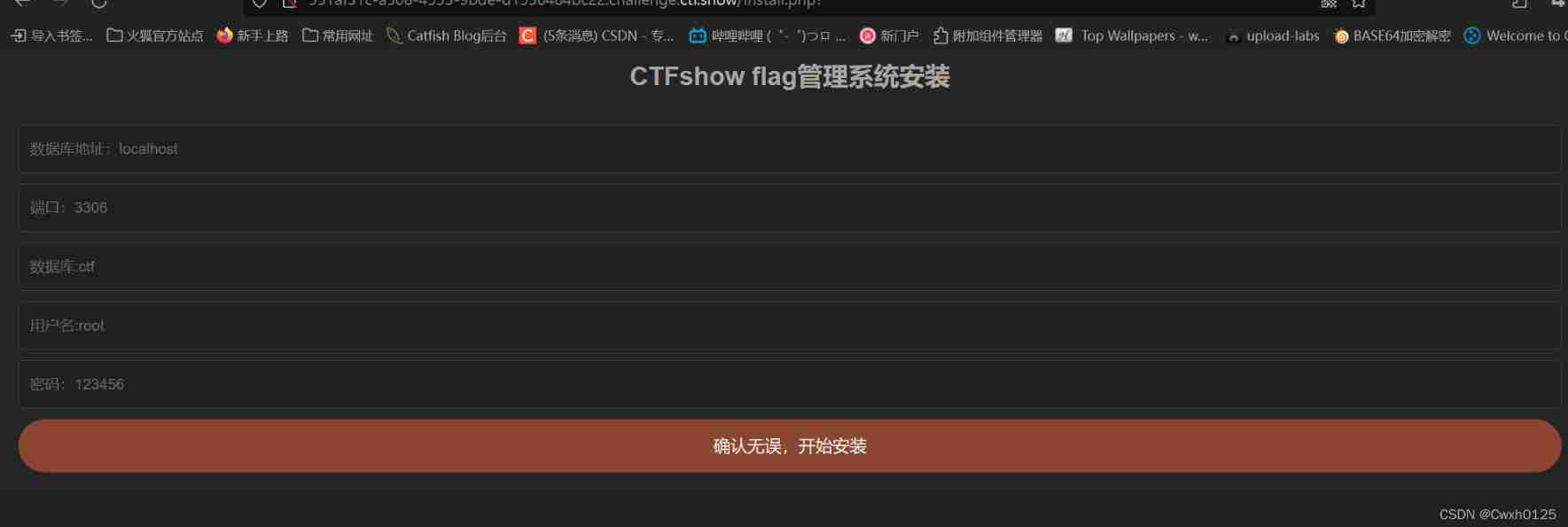
Blow up the password 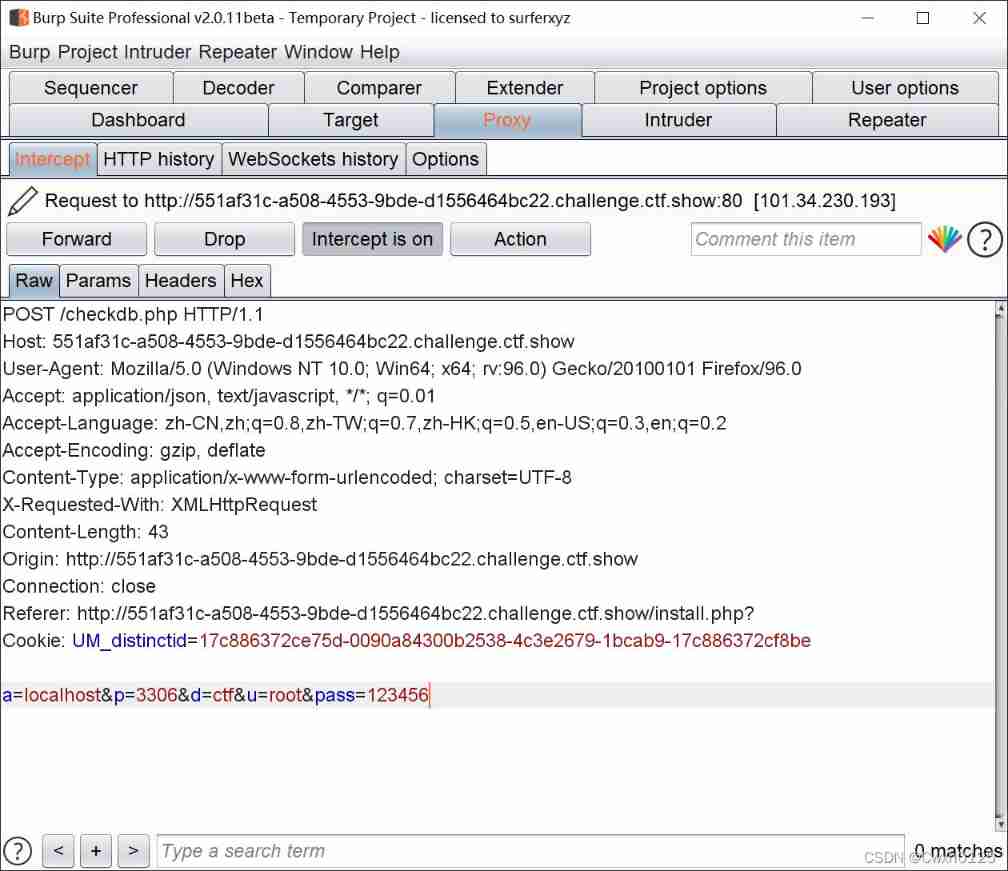
After blasting
边栏推荐
- FR练习题目---综合题
- 黑马程序员-软件测试-10阶段2-linux和数据库-44-57为什么学习数据库,数据库分类关系型数据库的说明Navicat操作数据的说明,Navicat操作数据库连接说明,Navicat的基本使用,
- 实现一个博客系统----使用模板引擎技术
- PyTorch二分类时BCELoss,CrossEntropyLoss,Sigmoid等的选择和使用
- Isn't it right to put money into the external market? How can we ensure safety?
- Microframe technology won the "cloud tripod Award" at the global Cloud Computing Conference!
- CPU设计实战-第四章实践任务二用阻塞技术解决相关引发的冲突
- Un week - end heureux
- Explain Vue's plan to clean up keepalive cache in time
- Interpretation of Apache linkage parameters in computing middleware
猜你喜欢

Dark horse programmer - software testing -10 stage 2-linux and database -44-57 why learn database, description of database classification relational database, description of Navicat operation data, de
想进阿里必须啃透的12道MySQL面试题
Crud of MySQL

Visual task scheduling & drag and drop | scalph data integration based on Apache seatunnel

12 MySQL interview questions that you must chew through to enter Alibaba

Differences between IPv6 and IPv4 three departments including the office of network information technology promote IPv6 scale deployment
Talking about how dataset and dataloader call when loading data__ getitem__ () function
Photoshop插件-动作相关概念-ActionList-ActionDescriptor-ActionList-动作执行加载调用删除-PS插件开发
APR protocol and defense
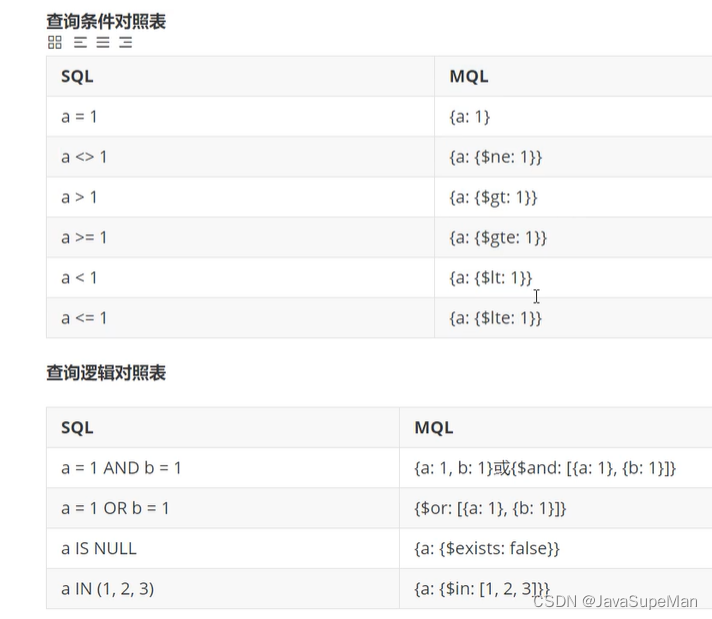
Mongdb learning notes
随机推荐
I collect multiple Oracle tables at the same time. After collecting for a while, I will report that Oracle's OGA memory is exceeded. Have you encountered it?
Long list optimized virtual scrolling
百亿按摩仪蓝海,难出巨头
两个BI开发,3000多张报表?如何做的到?
Crud de MySQL
[detailed explanation of Huawei machine test] character statistics and rearrangement
【NVMe2.0b 14-9】NVMe SR-IOV
FR练习题目---简单题
MySQL之CRUD
【招聘岗位】基础设施软件开发人员
Photoshop插件-动作相关概念-非加载执行动作文件中动作-PS插件开发
Visual task scheduling & drag and drop | scalph data integration based on Apache seatunnel
【招聘岗位】软件工程师(全栈)- 公共安全方向
想进阿里必须啃透的12道MySQL面试题
webRTC SDP mslabel lable
裁员下的上海
Topology可视化绘图引擎
Differences between IPv6 and IPv4 three departments including the office of network information technology promote IPv6 scale deployment
B站做短视频,学抖音死,学YouTube生?
webRTC SDP mslabel lable