当前位置:网站首页>Adb authorization process analysis
Adb authorization process analysis
2022-08-05 07:59:00 【Xiaoyuanzi 2016】
adbkey and adbkey.pub
adbkey and adbkey.pub_caibaihui's blog - CSDN blog _what is adbkey file
Experiments have shown that the public key on the mobile phone and the private key on the computer can be successfully paired, even if I modify the public key on the computer later, it will not affect the previous authorization
For example, the mobile phone has a built-in public key, and the paired private key is generated on my computer to complete the authorization
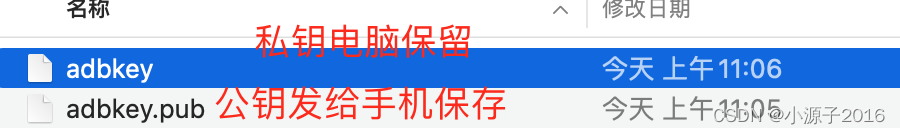
adb pull /data/misc/adb/adb_keys . The public key is stored in it
The authorization pop-up window shows that the RSA key fingerprint should be based on the public key. I don't know how to calculate it.
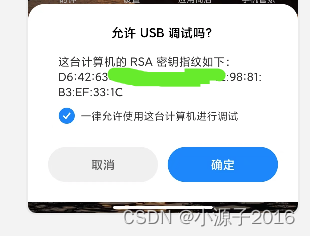
adb keygen cc can be used to generate RSA public and private keys
This information box will typically display the fingerprint (MD5) of the host's public key, not the host's
public key itself
ADB public key and private key authentication mechanism Use the following command to generate the host public key fingerprint: $ awk "{print $1}" < adbkey.pub | openssl base64 -A -d -a | openssl md5 -c | awk "{print $2}" | tr "[:lower:]" "[:upper:]" Actually, I used this command to find that the generated pop-up window is different from the one I saw, I am ready to give up and find new articles In general, it is necessary to process base64 and md5 separately For this, I need to know that the actual key in the file is the base64 encoded part, i.e. long cryptic string of characters.In my case the key field was always followed by the user-host field, i.e. something like In the latter case, I need to filter on the second field.In Windows, apparently, this is done using a Extract the key in the second field of 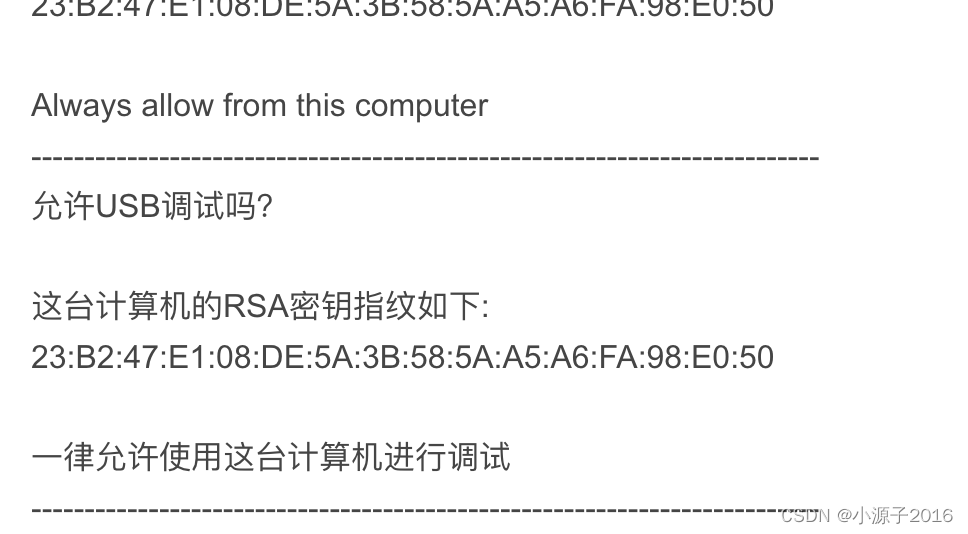
23:B2:47:E1:08:DE:5A:3B:58:5A:A5:A6:FA:98:E0:50[email protected] (also [email protected]), in some strings the case is preceded by a field containing ssh-rsa.for loop.I also send the output to a file for certUtil to do subsequent digestion, the output of which goes into the file again - containing the key which is no longer base64 encoded but in bytes - and finally hashed with MD5.id_rsa.pub into a file named tmp.key_base64:
边栏推荐
猜你喜欢

Redis 全套学习笔记.pdf,太全了
TRACE32——Break
双向循环带头链表

VXE-Table融合多语言
本地能ping通虚拟机,虚拟机ping不通本地
链表专项之环形链表
Ethernet Principle
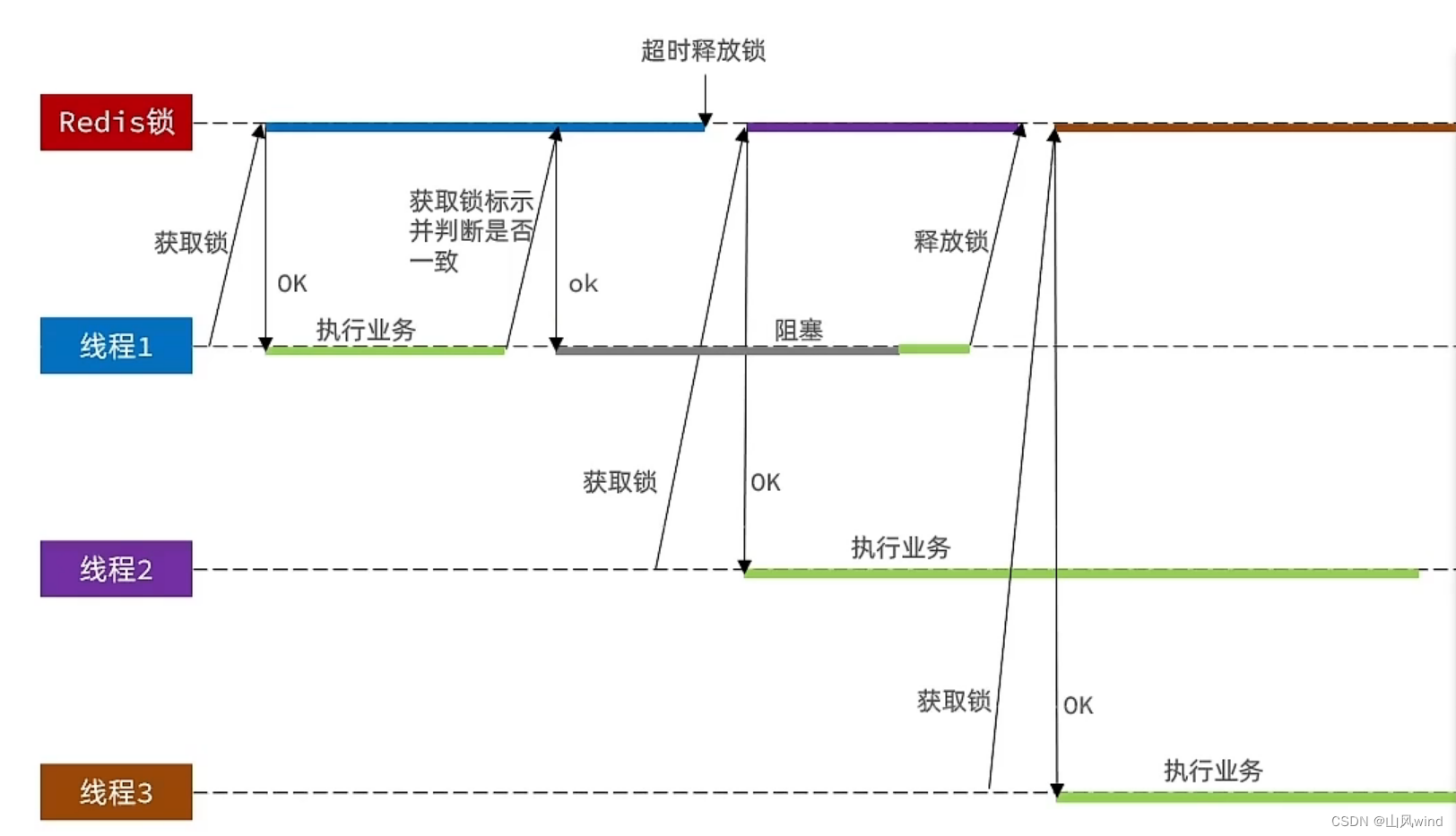
Redis implements distributed lock-principle-detailed explanation of the problem
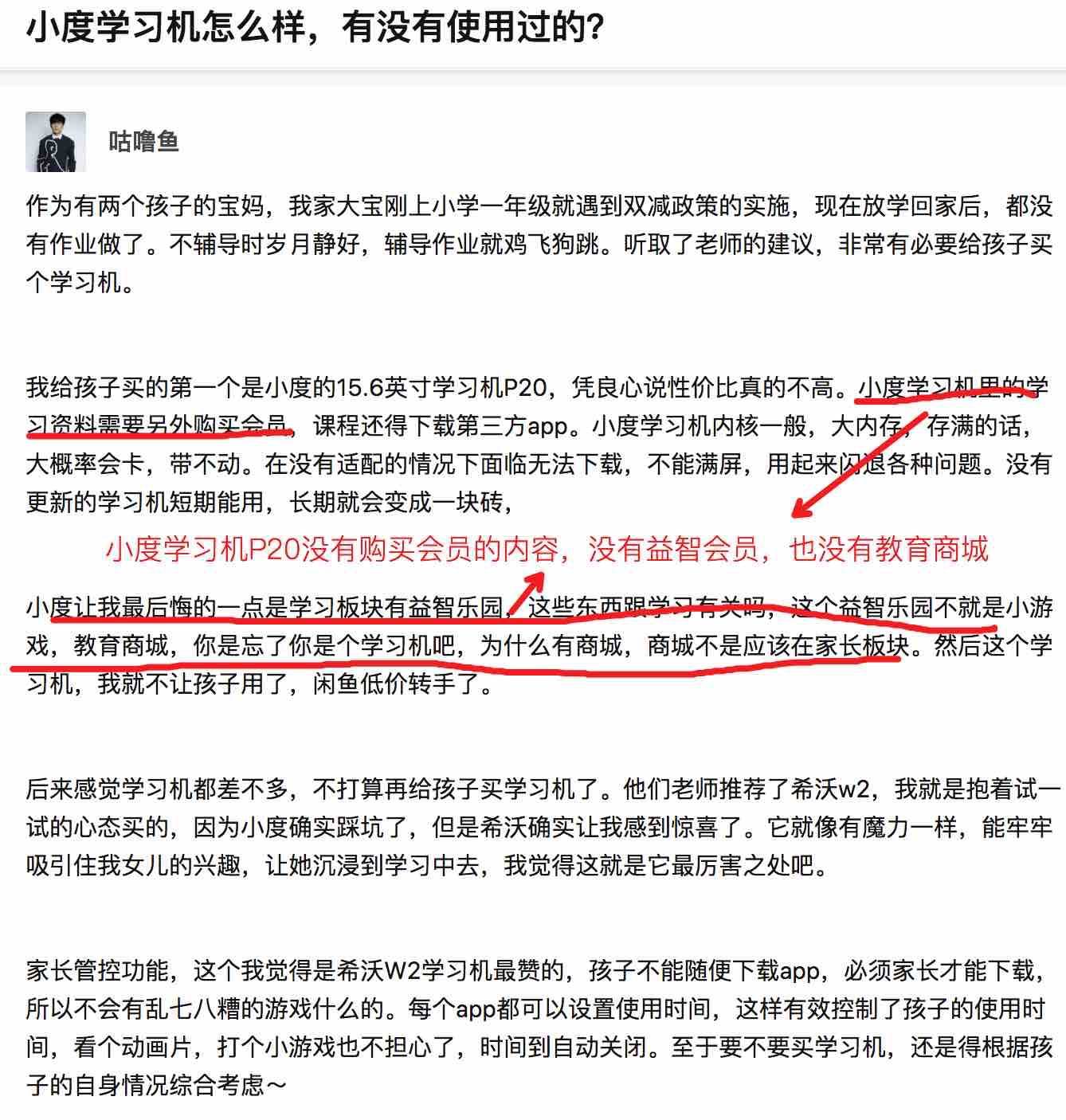
学习机赛道加速:请“卷”产品,不要“卷”营销
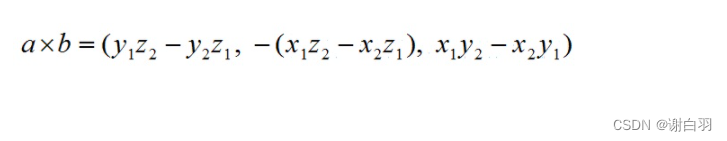
Game Thinking 19: Multi-dimensional calculation related to games: point product, cross product, point-line-surface distance calculation
随机推荐
ARM Cortex-M上的Trace跟踪方案
Redis数据库学习
[Structural Internal Power Cultivation] The Mystery of Enumeration and Union (3)
风控特征的优化分箱,看看这样教科书的操作
Version number naming convention
Qt writes custom controls: one of the text spotlight effects
DataFrame在指定位置插入行和列
爬虫之验证码
Nn. Unfold and nn. The fold
环网冗余式CAN/光纤转换器 CAN总线转光纤转换器中继集线器hub光端机
SVG Star Wars Style Toggle Toggle Button
C语言制作-QQ聊天室
创业者如何吸引风险投资商
版本号命名规则
P1103 书本整理
JVM运行流程,运行时数据区,类加载,垃圾回收,JMM解析
nn.unfold和nn.fold
Fiddler工具讲解
Re regular expressions
Mysql 死锁和死锁的解决方案