当前位置:网站首页>Wireshark packet capturing TLS protocol bar displays version inconsistency
Wireshark packet capturing TLS protocol bar displays version inconsistency
2022-07-04 18:39:00 【Dejavu_^_^】
problem
Conduct APP There was a problem during the security test , In the agreement display column, a pile of TLS1.2 Version of the package ** There are several TLSv1, And are client hello package ,** We know TLSv1 It's not safe , Is this a security vulnerability ?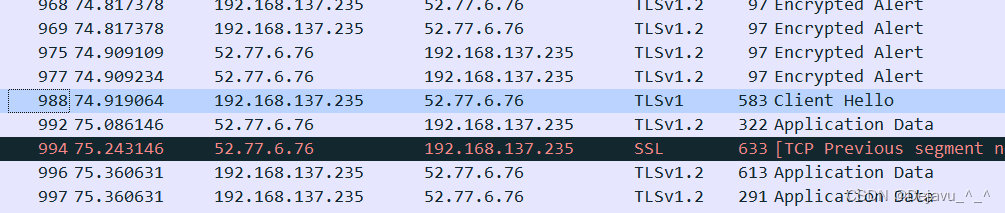
analysis
The following is TLS The negotiation process :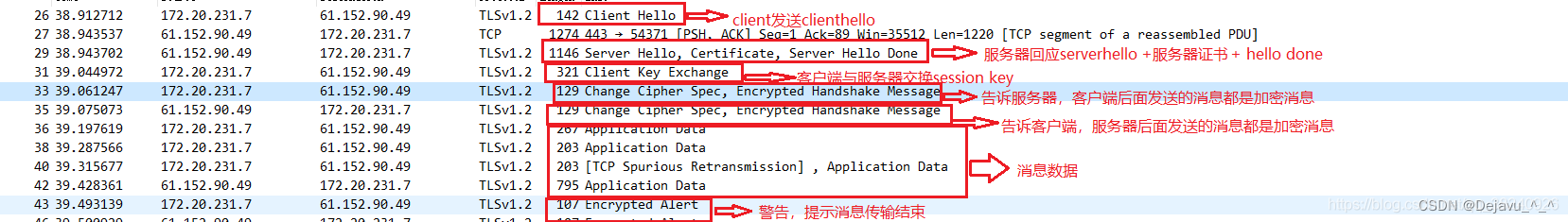
1. The client sends Generate random number (client random) And supported encryption methods to The server
The first handshake bag , Because it's a handshake process , This message contains a random number generated by the client Random1、 Encryption suite supported by client (Support Ciphers) and SSL Version Etc , Because the key has not been negotiated , Plaintext transmission is still used here , Note the plaintext transmission , The data carrier of the recording protocol is plaintext SSL handshake protocol . You may be confused here , Why is plaintext transmission wireshark The agreement column will write TLS edition ? Explain later ~~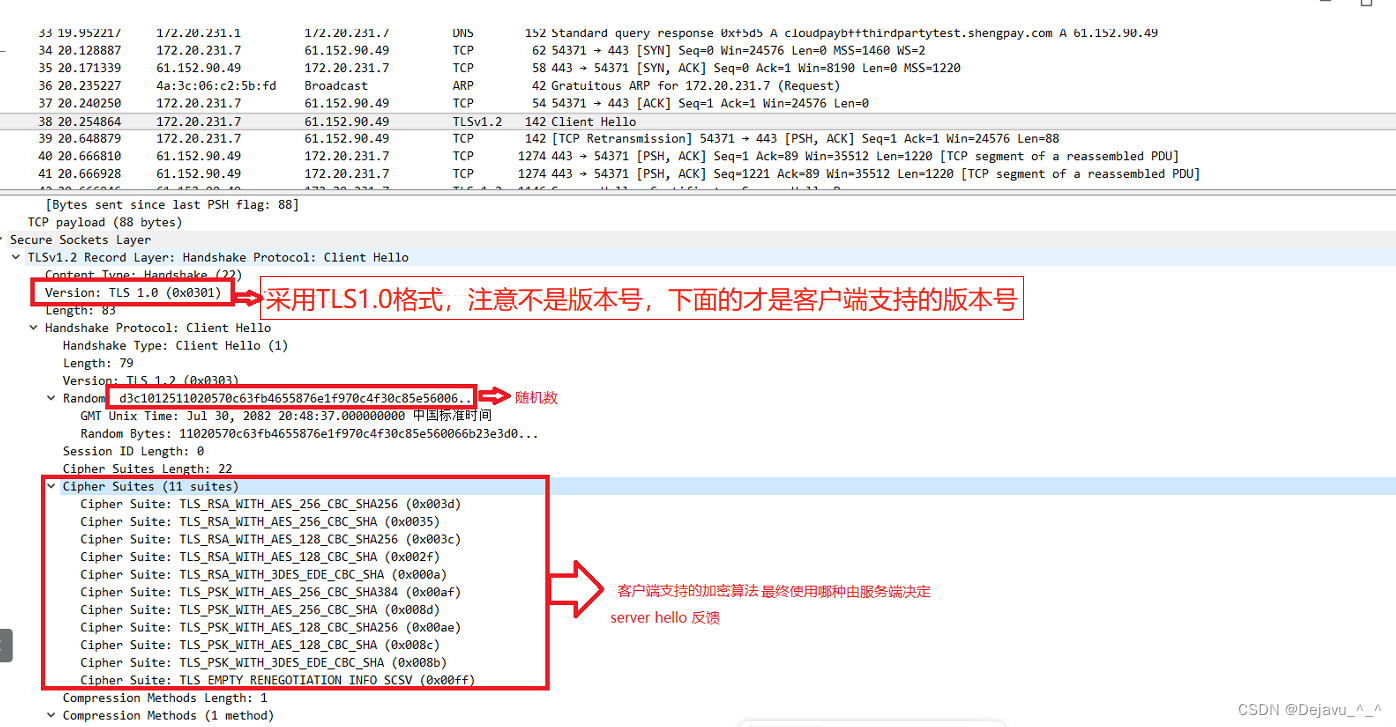
Pay attention here , Packets use TLS The version must be in the message Handshake Protocol Under the version To judge , This field really represents the maximum version supported by the client TLS agreement . As you can see below ,Protocol Column , Whether it's client hello still server Of response Are shown as TLSv1.2, In fact, if you look at client Detailed version of , You will find that the inside is TLSv1.0. If you don't look carefully , It may come to the wrong conclusion .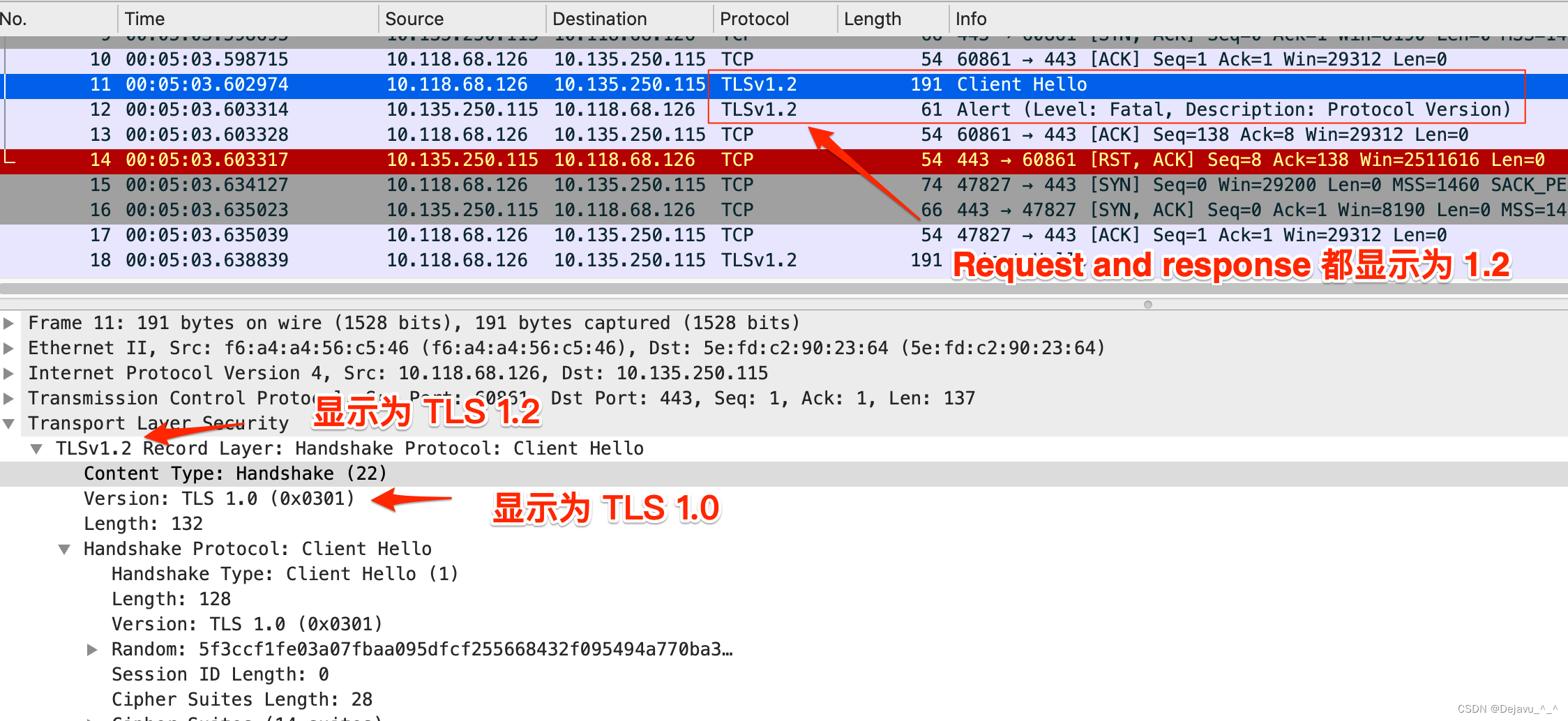
2. The server return server hello, contain
Encryption method used by both parties 、 The use of tls Version number and a random number
Encryption suite (cipher suite):TLS+ Key exchange algorithm + encryption algorithm + Authentication algorithm
Digital certificate and parameters generated by itself through some algorithm 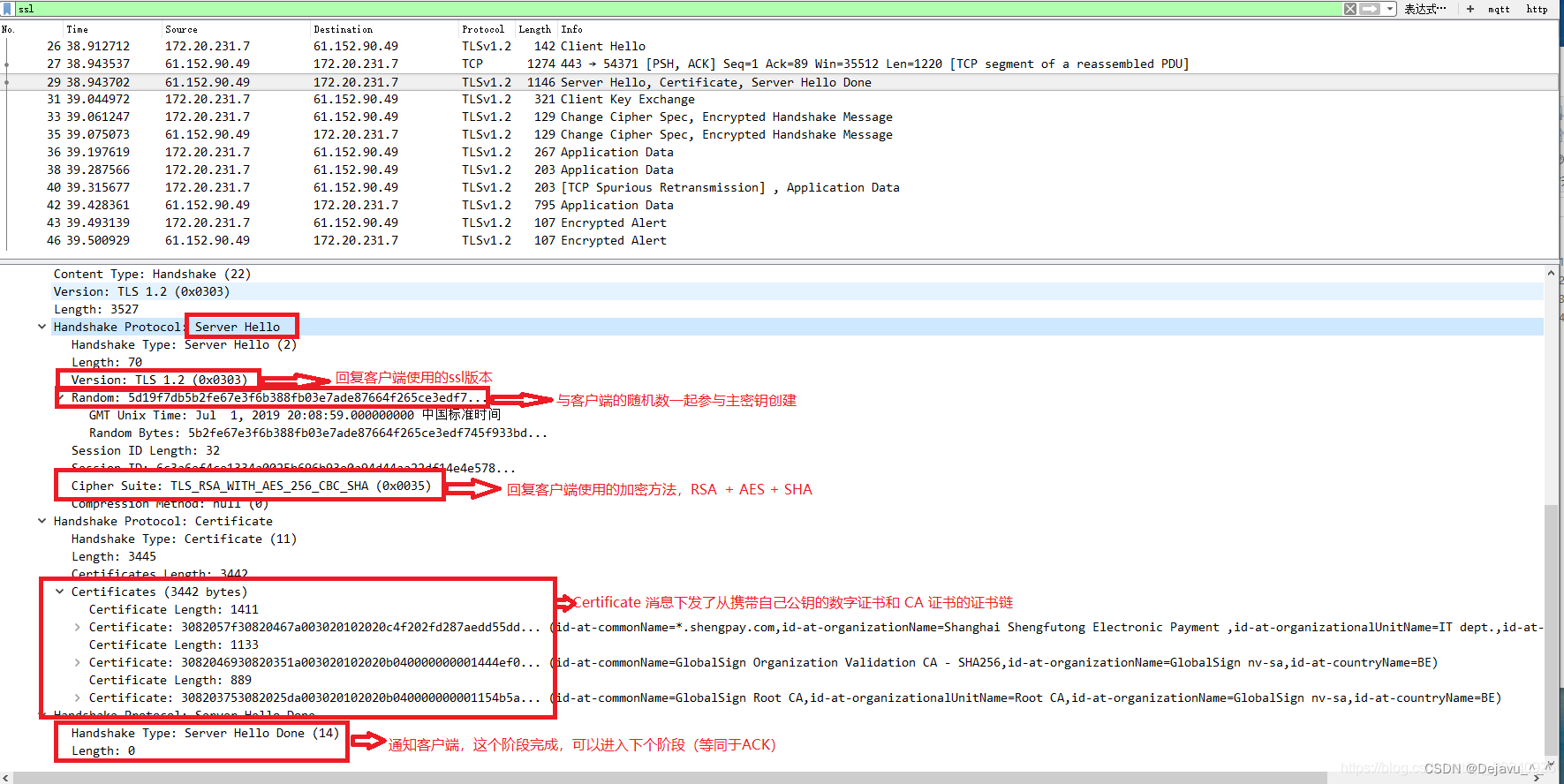
3.client according to server Return value ( random number , Encryption suite ) Exchange key 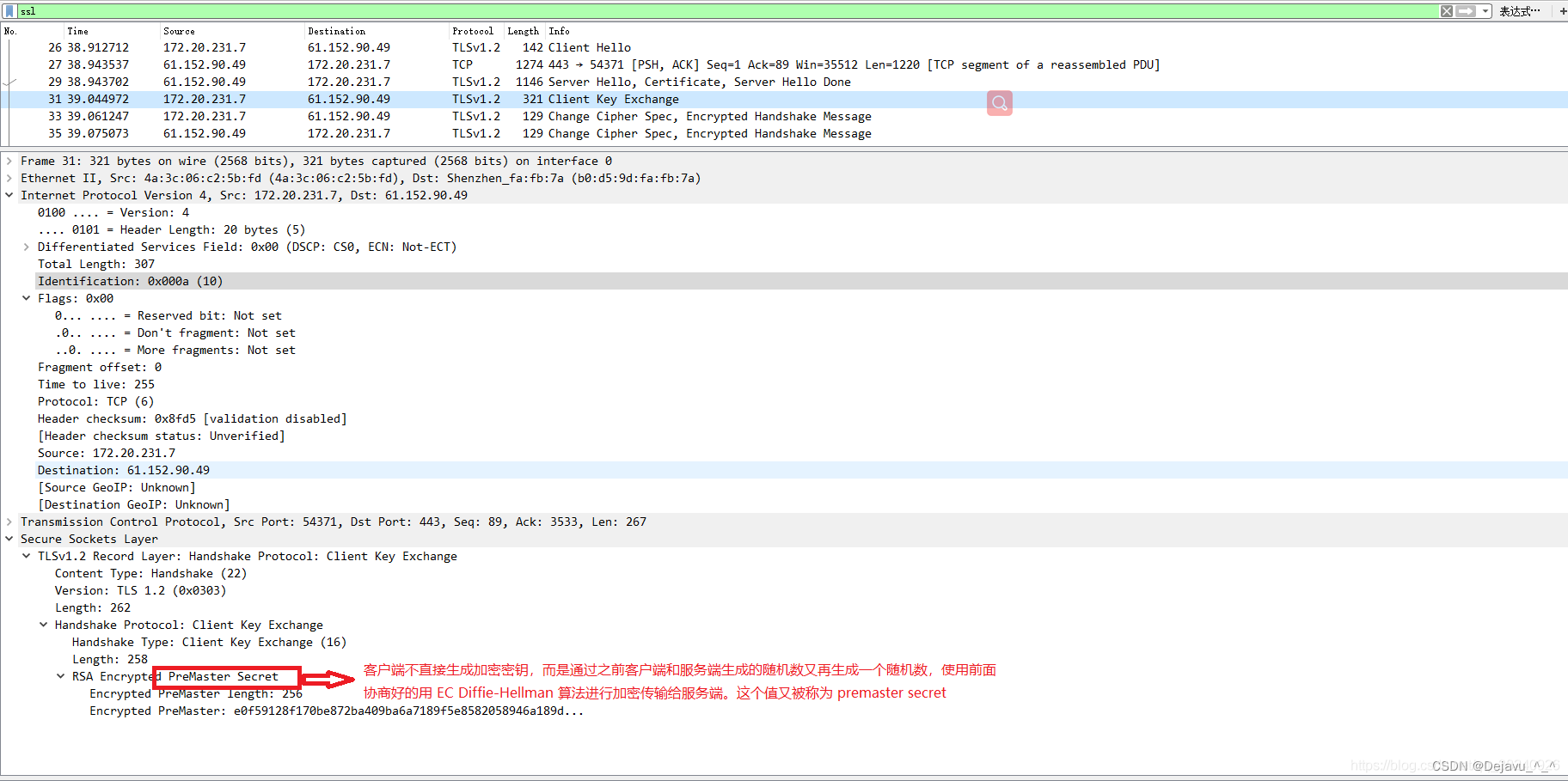
After the server receives this message , I will use my private key to unlock this random number . After this stage , Both the server and the client have three random numbers : Client random number 、 Server random number and prepared master key . Received on the server Client Key Exchange After the news , Both sides generate the master key according to the corresponding algorithm , Encryption key exchange completed .
Subsequently, inform the other party separately , Subsequent messages will be encrypted and sent .
The following explains why client hello Is shown as TLSv1
In addition to this , Two other interesting phenomena were found in the test , I saw client hello Package for TLSv1, But it disappeared after a while , Discover the original v1 Turned into 1.2.
Save the bag you caught , Open it again after a while , The original v1 It's gone again , Turned into 1.2.
Why does this happen ? It's going back to wireshark Of SSL dissector Source code , From source code , For this client hello Judgment of protocol version , Yes, according to client According to server Both sides make judgments . Under normal circumstances , Both ends are consistent , Or under normal negotiation , According to the server version . If the server does not respond , This is the time , In order to client Terminal client hello The version of is set . The problem we have here , The server responds , It's a different version , Lead to wireshark Is displayed as and client Real inconsistent problems .
The official website has such a problem : https://www.wireshark.org/lists/wireshark-users/201701/msg00004.html
Conclusion
- client hello It is plaintext transmission ,TLSv1 It's just wireshark On the basis of client According to server Result padding on both sides ;
- In use wireshark Grab Test SSL、TLS At version time , Main attention should be paid to application data Whether the package adopts TLS1.2 Above version , Because this is loaded with data .
Other knowledge complements
legacy version and supported_versions
stay TLS1.3 In the previous version ,legacy version For version negotiation , And represents the maximum version supported by the client . stay TLS1.3 The client in supported_versions Add the supported by the client to the extension TLS Version list , meanwhile ,legacy_version Must be set to 0x0303, namely TLS1.2 Version number of .
As shown in the figure , This is a TLS 1.3 Of client hello, Its version yes 0x0303, It has one supported_versions Extended fields for , The highest agreement supported inside is TLS1.3(0x0304).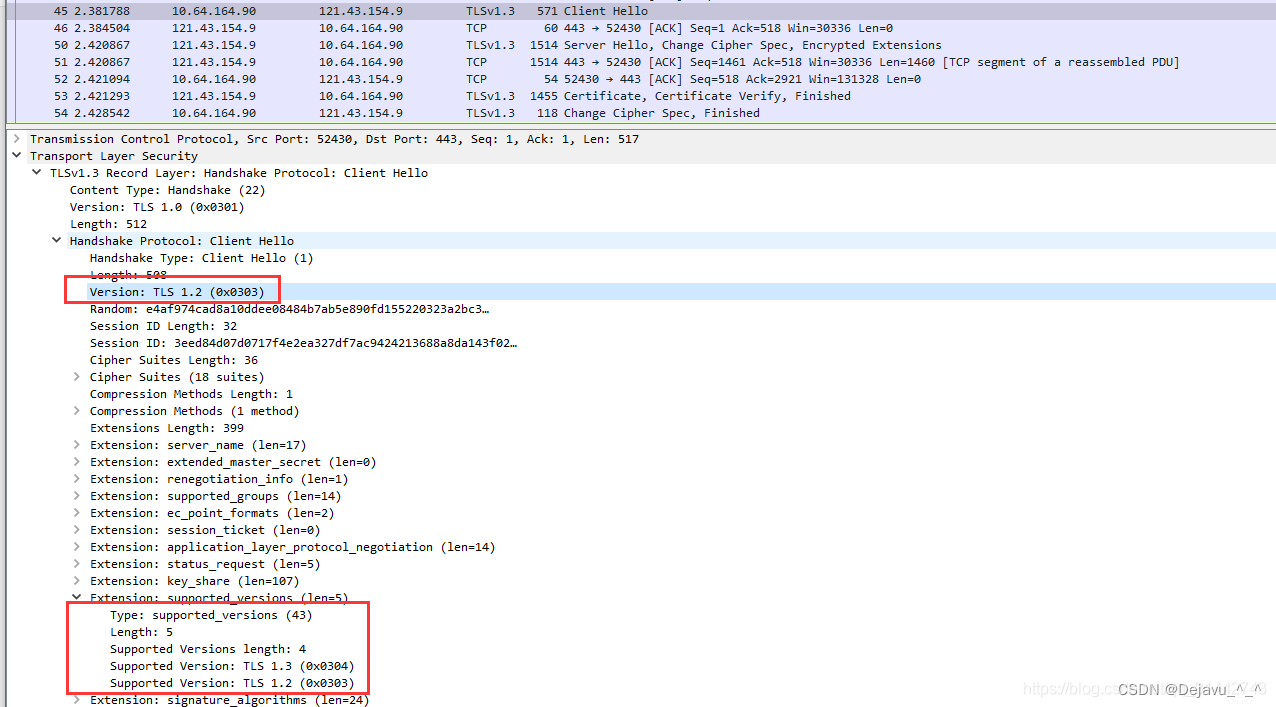
Reference material :
https://www.tianxiaohui.com/index.php/Linux%E7%9B%B8%E5%85%B3/wireshark-TSL-1-0-%E6%98%BE%E7%A4%BA%E5%8D%8F%E8%AE%AE%E5%88%97%E4%B8%BA-1-2-%E7%9A%84%E9%97%AE%E9%A2%98.html
https://blog.csdn.net/qq_38240926/article/details/94405011
https://blog.csdn.net/qq_31442743/article/details/111666786
边栏推荐
- 1、 Introduction to C language
- I wrote a learning and practice tutorial for beginners!
- 提升复杂场景三维重建精度 | 基于PaddleSeg分割无人机遥感影像
- [daily question] 556 Next bigger element III
- 表情包坑惨职场人
- Halcon template matching
- With an estimated value of 90billion, the IPO of super chip is coming
- 【210】PHP 定界符的用法
- Weima, which is going to be listed, still can't give Baidu confidence
- 如何提高开发质量
猜你喜欢
TCP waves twice, have you seen it? What about four handshakes?
![[go language question brushing chapter] go conclusion chapter | introduction to functions, structures, interfaces, and errors](/img/7a/16b481753d7d57f50dc8787eec8a1a.png)
[go language question brushing chapter] go conclusion chapter | introduction to functions, structures, interfaces, and errors
力扣刷题日记/day5/2022.6.27
同事悄悄告诉我,飞书通知还能这样玩
Tutorial on the use of Huawei cloud modelarts (with detailed illustrations)
基于NCF的多模块协同实例

Halcon模板匹配
Why are some online concerts always weird?
股价大跌、市值缩水,奈雪推出虚拟股票,深陷擦边球争议
删除二叉搜索树中的节点附图详解
随机推荐
[go language question brushing chapter] go conclusion chapter | introduction to functions, structures, interfaces, and errors
Tutorial on the use of Huawei cloud modelarts (with detailed illustrations)
mysql5.7安装教程图文详解
华为云ModelArts的使用教程(附详细图解)
Mysql5.7 installation tutorial graphic explanation
用于图数据库的开源 PostgreSQL 扩展 AGE被宣布为 Apache 软件基金会顶级项目
[HCIA continuous update] WAN technology
[daily question] 556 Next bigger element III
2022年DCMM认证全国各地补贴政策汇总
Russia arena data releases PostgreSQL based products
Halcon template matching
【Go语言刷题篇】Go完结篇|函数、结构体、接口、错误入门学习
字节跳动Dev Better技术沙龙成功举办,携手华泰分享Web研发效能提升经验
DB engines database ranking in July 2022: Microsoft SQL Server rose sharply, Oracle fell sharply
Large scale service exception log retrieval
Interpretation of SIGMOD '22 hiengine paper
DB-Engines 2022年7月数据库排行榜:Microsoft SQL Server 大涨,Oracle 大跌
celebrate! Kelan sundb and Zhongchuang software complete the compatibility adaptation of seven products
一直以为做报表只能用EXCEL和PPT,直到我看到了这套模板(附模板)
File processing examples of fopen, FREAD, fwrite, fseek