当前位置:网站首页>Privacy violation and null dereference of fortify vulnerability
Privacy violation and null dereference of fortify vulnerability
2020-11-07 21:43:00 【Rich in starch】
Fortify Loopholes Privacy Violation( Privacy leaks ) and Null Dereference( Null pointer exception )
Reference article :
(2)https://www.cnblogs.com/meInfo/p/9037784.html
Just remember .
版权声明
本文为[Rich in starch]所创,转载请带上原文链接,感谢
边栏推荐
- go wire 依赖注入入门
- Insight -- the application of sanet in arbitrary style transfer
- Adobe media encoder / me 2021 software installation package (with installation tutorial)
- Jingtao project day09
- ROS学习---远程启动ROS节点
- Download, installation and configuration of Sogou input method in Ubuntu
- Thinkphp6中where条件中字段与字段比较条件的写法
- About the promotion of the whole stack of engineers, from the introduction to give up the secret arts, do not click in to have a look?
- Android 9.0/P WebView 多进程使用的问题
- delphi10的rest.json与system.json的踩坑
猜你喜欢
Analysis of kubernetes service types: from concept to practice

【解决方案】分布式定时任务解决方案

Ubuntu下搜狗输入法的下载安装及配置

Everything is 2020, LINQ query you are still using expression tree
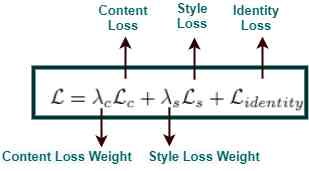
洞察——风格注意力网络(SANet)在任意风格迁移中的应用

关于晋升全栈工程师,从入门到放弃的神功秘籍,不点进来看一看?
Code Review Best Practices

什么都2020了,LINQ查询你还在用表达式树
websocket+probuf.原理篇

laravel8更新之维护模式改进
随机推荐
爆一个VS2015 Update1更新带来的编译BUG【已有解决方案】
About the promotion of the whole stack of engineers, from the introduction to give up the secret arts, do not click in to have a look?
Data transmission of asynchronous serial communication controlled by group bus communication
Web Security (3) -- CSRF attack
Ladongo open source full platform penetration scanner framework
The instanceof operator in ecmascript7 specification
看一遍就理解,图解单链表反转
Web安全(四)---XSS攻击
[original] the influence of arm platform memory and cache on the real-time performance of xenomai
Sentry 安装
ngnix集群高并发
Get started, GIT
When tidb and Flink are combined: efficient and easy to use real-time data warehouse
ECMAScript7规范中的instanceof操作符
[solution] distributed timing task solution
The emergence and significance of micro service
leetcode之判断路径是否相交
It's time to end bertology
More than 50 object detection datasets from different industries
Idea - the. IML file was not automatically generated by the project