当前位置:网站首页>[exercise 6] [Database Principle]
[exercise 6] [Database Principle]
2022-07-03 12:46:00 【Laughing cold faced ghost】
List of articles
One 、 Single topic selection
1. View mechanism improves the efficiency of database system ().
A) integrity
B) Security
C) Uniformity
D) concurrency control
answer :B
2. The prevention object of integrity control is ().
A) Illegal users
B) Non semantic data
C) Illegal operation
D) Incorrect data structure
answer :B
3. The main objects of security control are ().
A) Legal users
B) Non semantic data
C) Illegal operation
D) Incorrect data
answer :C
4. When a transaction is executed , Should abide by “ Don't do either , Or do it all ” Principles , This is a matter of ().
A) Atomicity
B) Uniformity
C) Isolation,
D) persistence
answer :A
5. The statement to realize transaction rollback is ().
A)GRANT
B)COMMIT
C)ROLLBACK
D)REVOKE
answer :C
6. The role of backup copy is ().
A) Security
B) Integrity control
C) concurrency control
D) Database recovery
answer :D
7. The commonly used technology to solve the problem of data inconsistency caused by concurrency control is ().
A) The blockade
B) Access control
C) recovery
D) negotiation
answer :A
8. Such as business T For data objects R Realization X The blockade , be T Yes R().
A) Can only read but not write
B) Can only write, can't read
C) It's both readable and writable
D) Can't read or write
answer :C
9. In database technology ,“ Dirty data ” Refer to ().
A) Data not backed back
B) Uncommitted data
C) Fallback data
D) Data not submitted and subsequently withdrawn
answer :D
10.“ journal ” Files are used to save ().
A) The process of running the program
B) Data manipulation
C) Program execution result
D) Update the database
answer :D
12. In the transaction dependency graph , If the dependencies of two transactions form a loop , Then it will ().
A) There is a live lock phenomenon
B) Deadlock occurs
C) Transaction executed successfully
D) Transaction execution failed
answer :B
14. Consistency of transactions means ().
A) All operations included in the transaction are either done , Either not
B) Once the transaction is committed , Changes to the database are permanent
C) The operations and data used within a transaction are isolated from other concurrent transactions
D) The transaction must be to change the database from one consistency state to another
answer :D
15. Protect the database , Prevent data leakage caused by unauthorized or illegal use 、 Change destroys . This refers to the of data ().
A) Security
B) integrity
C) concurrency control
D) recovery
answer :A
16.SQL Use () Statement grants system permission or object permission to the user .
A)SELECT
B)CREATE
C)GRANT
D)REVOKE
right key :C
17. In the following description of views , What's not right is ().
A) Views are out of mode
B) Using views can speed up the execution of query statements
C) Views are virtual tables
D) Using views can speed up the writing of query statements
right key :B
Two 、 Completion
1.DBMS The security protection function of the database is through ____ control 、____ control 、____ Control and ____ Realized in four aspects .
answer : Security 、 integrity 、 concurrency 、 Data recovery
2. Two important indicators to measure the authorization mechanism are ____ and ____.
answer : Data objects 、 Operation type
3. It is a working unit executed in the database system , It is a user-defined sequence of operations . It has ____、____、____ and ____ Four characteristics .
answer : Business 、 Atomicity 、 Uniformity 、 Isolation, 、 persistence
4. The database inconsistencies caused by concurrent operations mainly include ____、____ and ____ Three .
answer : Lost update 、 Read dirty data 、 It can't be read repeatedly
5. The main methods to realize concurrency control are ____ technology , The basic types of blockade are ____ and ____ Two kinds of .
answer : The blockade 、 Exclusive lock 、 Shared lock
6. During the operation of the database ____ fault 、____ Faults and ____ Fault category III .
answer : Business 、 System 、 medium
7. Rules and defaults are used to help users realize data ____.
answer : integrity
8. according to SQL Server Safety requirements for , When a user wants to access SQL Server Database in , Must be in SQL Server To create a ____ and ____.
answer : Login account 、 The user account
9. Record the storage location according to the index , The index can be divided into ____ Index and ____ Indexes .
answer : Gather 、 Non aggregation
10. Views are virtual tables , Its data is not stored , Only store it in the database ____.
answer : Definition
边栏推荐
- Do you feel like you've learned something and forgotten it?
- 剑指Offer04. 二维数组中的查找【中等】
- Tianyi ty1208-z brush machine detailed tutorial (free to remove)
- 1-2 project technology selection and structure
- 4. 无线体内纳米网:电磁传播模型和传感器部署要点
- ORM use of node -serialize
- 双链笔记·思源笔记综合评测:优点、缺点、评价
- Sword finger offer09 Implementing queues with two stacks
- Prompt unread messages and quantity before opening chat group
- 自抗扰控制器七-二阶 LADRC-PLL 结构设计
猜你喜欢
Sword finger offer09 Implementing queues with two stacks

剑指Offer03. 数组中重复的数字【简单】

4. 无线体内纳米网:电磁传播模型和传感器部署要点
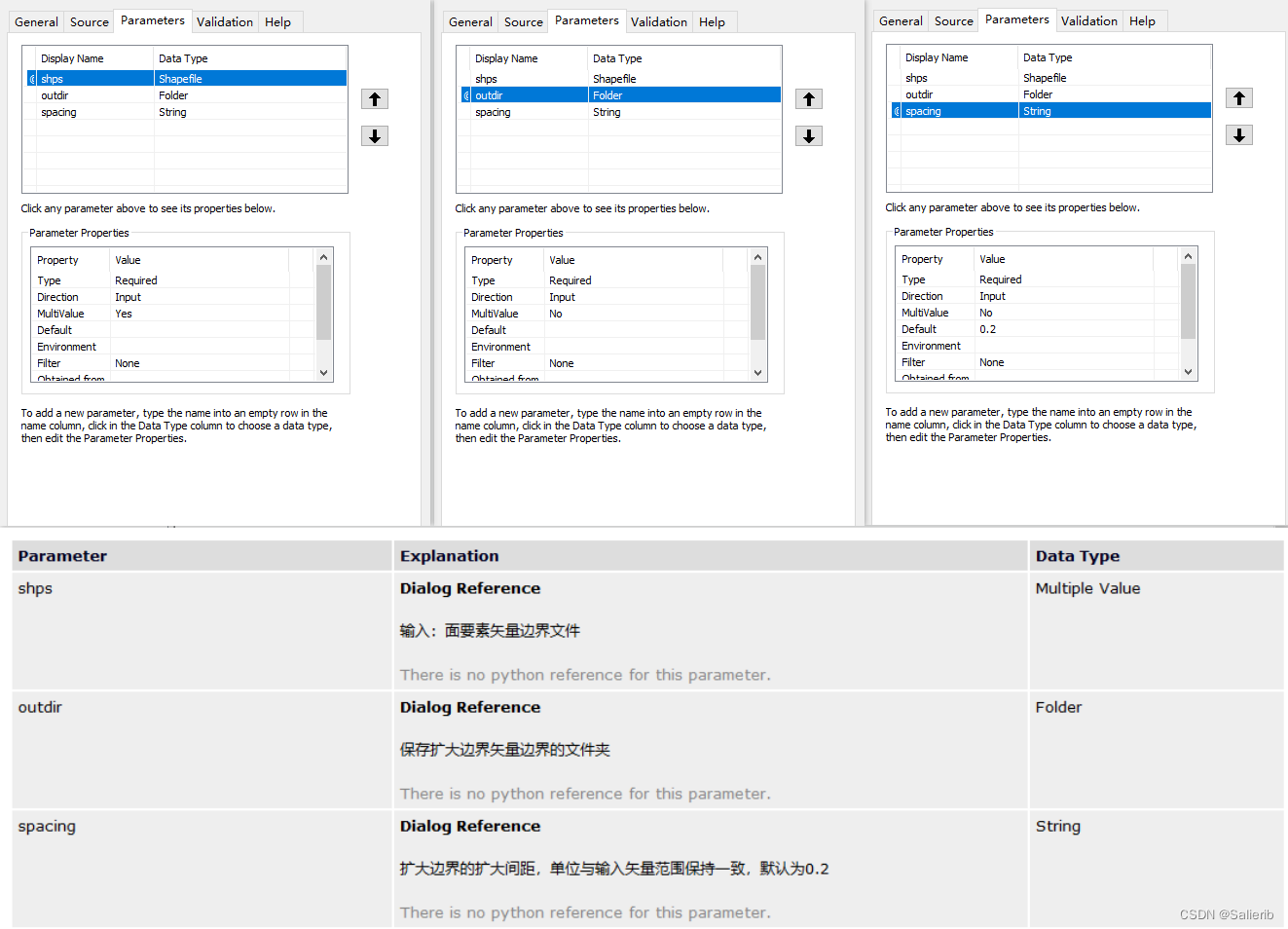
【ArcGIS自定义脚本工具】矢量文件生成扩大矩形面要素

基于同步坐标变换的谐波电流检测

ncnn神经网络计算框架在香橙派OrangePi 3 LTS开发板中的使用介绍

1-2 project technology selection and structure

Application of ncnn neural network computing framework in orange school orangepi 3 lts development board
剑指Offer07. 重建二叉树
![[ArcGIS user defined script tool] vector file generates expanded rectangular face elements](/img/39/0b31290798077cb8c355fbd058e4d3.png)
[ArcGIS user defined script tool] vector file generates expanded rectangular face elements
随机推荐
Idea packages the web project into a war package and deploys it to the server to run
elastic_ L01_ summary
lambda与匿名内部类的区别
【ArcGIS自定义脚本工具】矢量文件生成扩大矩形面要素
Project video based on Linu development
Take you to the installation and simple use tutorial of the deveco studio compiler of harmonyos to create and run Hello world?
Adult adult adult
Lambda表达式
Is it safe to open an account for online stock speculation? Who can answer
ImportError: No module named examples. tutorials. mnist
Apache Mina开发手册
Powerful avatar making artifact wechat applet
[download attached] password acquisition tool lazagne installation and use
剑指Offer05. 替换空格
低代码平台国际化多语言(i18n)技术方案
Keep learning swift
CNN MNIST handwriting recognition
Computer version wechat applet full screen display method, mobile phone horizontal screen method.
studio All flavors must now belong to a named flavor dimension. Learn more
(最新版) Wifi分销多开版+安装框架