当前位置:网站首页>Vulnerability mining | routine in password retrieval
Vulnerability mining | routine in password retrieval
2022-06-29 01:09:00 【zkzq】
Zero basic hacker , Search official account : White hat left
author : The prophet community - I love cat's free fish
Original address :https://xz.aliyun.com/t/7977
Preface
First of all, this is not a concluding post , After all, there is a comprehensive summary of the test methods for password retrieval on the network
Such as brute force cracking of user credentials , The system returns important vouchers , Email phone weak token,token Universal ,session Cover , The validity period of the user voucher , The credential algorithm has been cracked , A series of vulnerabilities such as front-end verification .
Here is the brain map summarized by the elder , The summary is also quite detailed .

In the daily authorization test and forum wandering , Found some interesting password retrieval operations for individuals , It is much joyful to share the joy than enjoy alone. , I hope I can help you master .
Host Header cheating
Some people think that HTTP The online of depends on what is in the bag HOST header To connect , So I think that if you modify the HOST, Then you cannot connect to the target server , So it is uncontrollable .
Actually HTTP Online and in the bag HOST It doesn't matter , HTTP Is online TCP/IP The establishment of a , So I modified HOST HEADER It doesn't drop the package on another server .
So when the application uses $_SERVER[‘HTTP_HOST’] Get website URL And spliced into the link to retrieve the password, there will be a vulnerability .
When you use the website password reset function , Website URL May change in the future , Therefore, it is necessary to dynamically generate a link to retrieve the password from the mailbox to match the server URL.
It may be used at this time $_SERVER[‘HTTP_HOST’],Host header It is provided by the client , This means that attackers can write their own web address to the password reset email , Threaten the security of any user's account .
adopt X-Forwarded-Host To splice and retrieve the domain name in the password link , In this way, you can write the domain name you control , Then find the link to retrieve the password by visiting the record , Reset any user password after splicing back the correct domain name .
The use condition is that the victim must click the reset link , You can view the reset link from the website you control through the access record .
Take up a kackerone Example :
Mavenlink Allow users to register for a mavenlink.com To display their content , So they need a way to dynamically determine the subdomain name of the company .
host header It can be set to mavenlink.com Any subdomain of , But from mavenlink.com Changing the domain name will return an error , Instead of sending an email .
Add a random mavenlink.com Subdomain , But this will be directed to the right page , I can't insert my own domain name .
Test special characters .
Server accept host header A question mark in , Generate the following link
Host: example.com?.mavenlink.com
In this way, password reset can be stolen from user email token
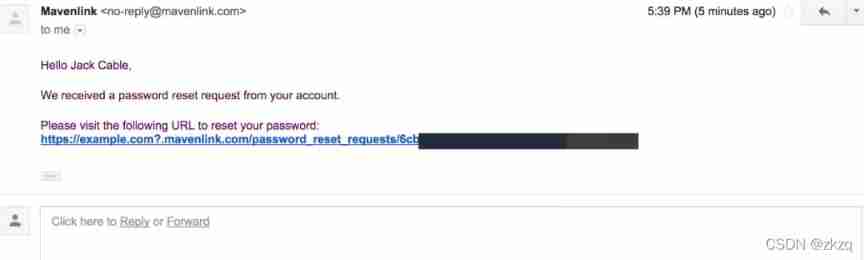
Of course, this also involves the problem of bypassing domain name detection , Once the user clicks the link , We are example.com You can get the reset link information
Verify link batch sending
When passing the email or mobile number to send the verification link to the backend , It can deliver a collection of mailboxes or mobile phones
Then as long as the first email or mobile number is the email or mobile number existing in the database , that The same link information will be sent to these mobile phone numbers or mailboxes
Examples encountered in team testing :


stay hackerone There are also such examples in the disclosed loopholes
By sending two mailboxes , A mailbox for the victim , A mailbox controlled by oneself , In this way, you can steal the link to reset the password in the victim's mailbox , To achieve the purpose of any user password reset .

Because I haven't seen the source code that triggers the vulnerability , Guess verification allows you to get something similar to a collection , Iterate over whether the value exists in the database
Release the set if it exists , The logic that then sends validation information also allows you to pass in a collection and then iterate over each value in the collection ,
Send the same validation link for each value
In the mobile phone number sql Inject
because sql The problem of sentence splicing leads to the existence of... At the mobile phone number sql Injection problem , In fact, this also tells us that sql As long as the splicing problem is involved in the execution of statements, there may be loopholes
In the test authorized by the team, we have also encountered the problem that exists at the change date sql Examples of Injection , It was fun anyway .
Here's one sqrt function ,sqrt Calculate a function for a square root , When the square root is calculated, it is spliced with the previous number , If the mobile phone number exists in the database, the verification code will be sent

If the mobile phone number after calculation and the previous digital splicing does not exist in the database, the verification code sending failure will be displayed

In this way, you can guess the relevant information of the database

summary
This logic loophole is always advancing in the struggle between attack and defense , There are bound to be people with big brain holes who will find more tricks , This is the operation of several interesting arbitrary user password reset vulnerabilities encountered in the test , Those who can find examples on the Internet try to use Internet examples , Please let us know if there is any infringement

边栏推荐
- What is the difference between immunohistochemistry and immunohistochemistry?
- Precautions for installation and use of rotary joint
- be based on. NETCORE development blog project starblog - (13) add friendship link function
- [eight part essay] MySQL
- 【Proteus仿真】4x4矩阵键盘中断方式扫描 +数码管显示
- QT is based on RFID Management System (applicable to most RFID Management Systems)
- Day 8 script and audio
- 滑环电机是如何工作的
- XML and other file contents in idea cannot be highlighted, and the file becomes gray
- UI highly adaptive modification scheme
猜你喜欢

旋转接头安装使用注意事项

Comparison between winding process and lamination process

狼人杀休闲游戏微信小程序模板源码/微信小游戏源码

BMFONT制作位图字体并在CocosCreator中使用

【leetcode】17. Letter combination of telephone number

Browser cache library design summary (localstorage/indexeddb)

Analysis of basic structure and working principle of slip ring

EasyCVR服务private.pem文件被清空,导致无法正常启动该如何处理?

PR 2021 quick start tutorial, how to use audio editing in PR?

How can multidimensional analysis pre summary work?
随机推荐
成功解决(机器学习分割数据问题):ModuleNotFoundError: No module named ‘sklearn.cross_validation‘
Précautions d'installation et d'utilisation des joints rotatifs
用户登录(记住用户)&用户注册(验证码) [运用Cookie Session技术]
第八天 脚本与音频
最新Justnews主题源码6.0.1开心版+社交问答插件2.3.1+附教程
Mask wearing face data set and mask wearing face generation method
统计字符串中不同回文子序列的个数
【温度检测】基于matlab GUI热红外图像温度检测系统【含Matlab源码 1920期】
[proteus simulation] 4x4 matrix keyboard interrupt mode scanning + nixie tube display
流媒体集群应用与配置:如何在一台服务器部署多个EasyCVR?
cocoscreator动态切换SkeletonData实现骨骼更新
卷绕工艺与叠片工艺的对比
企业和IT领导者对创新的误解
Is it safe and reliable for qiniu school to help open a securities account? How to drive
《Reinforcement learning based parameters adaption method for particleswarm optimization》代码复现
674. longest continuous increasing sequence
Drawing ECG curve with WPF
[agile 5.1] core of planning: user stories
EasyCVR服务private.pem文件被清空,导致无法正常启动该如何处理?
sql入门