当前位置:网站首页>How to protect user privacy without password authentication?
How to protect user privacy without password authentication?
2022-07-05 11:30:00 【Huawei mobile services】
In the Internet world , Verifying user identity is a common and important scenario , The most widely used method is account password verification . As developers' requirements for authentication security continue to improve , In addition, users pay more attention to privacy and convenience in the process , Authentication methods are gradually diversified , With dynamic token 、 SMS verification code 、 Biometric authentication and other methods . This article mainly from the perspective of security , Discuss the security vulnerabilities of several common authentication methods , Provide more advantageous solutions for developers .
The security risks of common authentication methods are as follows :

Since both static and dynamic password authentication methods have vulnerabilities , Then whether authentication can be independent of passwords ?
Actually , Long ago , Someone began to imagine “ Password-free login ”. Of course ,“ Password-free login ” It does not mean that there is no password , Instead, use a new authentication method , To replace the existing password authentication system .HMS Core Online Fast Authentication Service (HMS Core FIDO) Based on this starting point , It provides a more advantageous solution for developers : User authentication without password , Provide local biometric authentication and online fast authentication capabilities , It can be used for user login 、 Purchase payment and other scenarios , meanwhile , Through system integrity detection and key verification mechanism , To ensure that the verification results are safe and reliable . The implementation process is as follows .
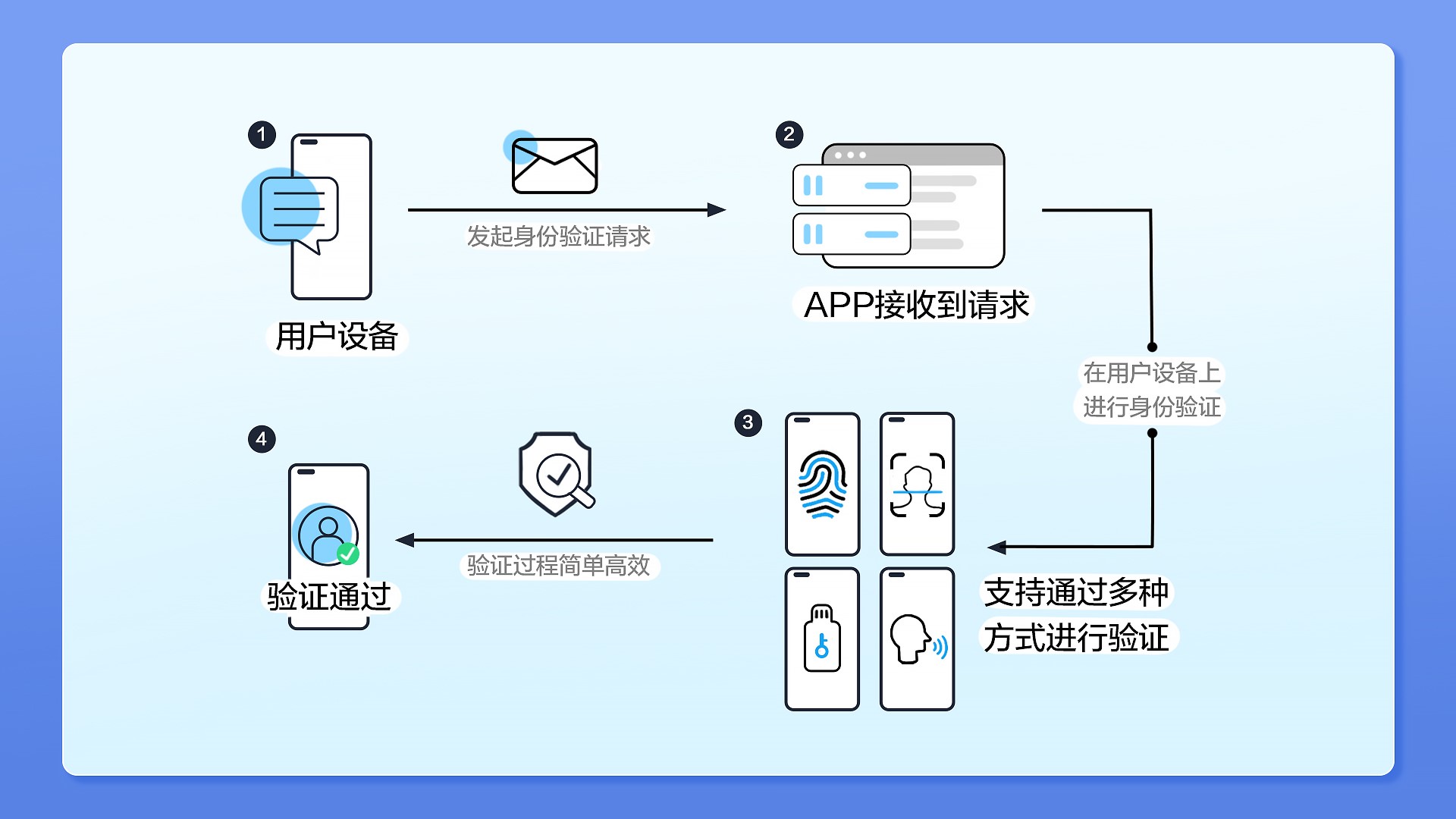
In terms of security , First ,HMS Core FIDO It avoids the user entering the account password manually , Therefore, there is no need to worry about the risk of account password disclosure .
secondly , Use HMS Core FIDO There is no need for users to carry additional second authentication devices .App The user's identity can be verified through the built-in components of the user's mobile phone , Such as fingerprint verifier 、3D Face sensor 、 Iris verifier, etc . If App Hope to strengthen the verification , In addition to using or inserting the second device , Users' mobile phones can be directly used as security key hardware , Complete authentication . A cell phone , Support multiple verification scenarios , Users do not need to carry additional equipment ,HMS Core FIDO It not only improves the user experience , At the same time, it also reduces the deployment cost of Internet service providers .
Last , The user biometric information used in the verification process will never leave the user's device , It can only be used after unlocking locally , Therefore, there is no need to worry about leaking user data from the server .
In addition to providing secure authentication ,HMS Core FIDO It can also help developers optimize the user experience .
HMS Core FIDO The protocol is always designed around protecting users' privacy , These protocols do not provide information that can be used to track users on Internet platforms , If biometric technology is adopted , User biometric information will never leave the user device . This is compared with the traditional biometric authentication , Great improvements have been made in security and privacy protection , Because traditional biometric authentication will collect user data to the server , Once the server data leaks , There will be serious consequences . From the user's point of view , The privacy experience has been greatly improved .
During authentication , The user operation is simple , The process is smooth and uninterrupted , Don't spend too much time waiting , For example, accept the verification code 、 Enter the password, etc .
HMS Core FIDO Application scenarios of
at present ,FIDO Technology has been developed by global equipment manufacturers 、 Widespread recognition of Internet service providers , Including some large banks and other financial institutions 、 Government network platform, etc , Mature application in high security scenarios involving capital changes , Such as : Shopping websites or App Purchase payment 、 Digital currency transfer 、 Mobile Banking ( Online Banking Service ) Large transactions in , wait . Take the use process for example ,App Check whether the device supports when the user logs in HMS Core FIDO, If the support ,App It can guide users to open fingerprints or 3D Face login , Users only need to verify their fingerprints or 3D Face can be .
HMS Core FIDO Is based on FIDO Standardize the open capabilities for developers at home and abroad , It can help Internet service providers to make the authentication process more secure 、 It's simpler , At the same time, it can also gain a better user experience .FIDO Its full name is Fast Identity Online standard , By FIDO The alliance has launched and continues to maintain a set of authentication framework protocols , It uses standard public key cryptography , Provide a more powerful authentication method .
Click to enter HMS Core FIDO Official website , obtain Development guidance document , Experience high-quality authentication capabilities .
Learn more >>
visit Official website of Huawei developer Alliance
obtain Development guidance document
Huawei mobile service open source warehouse address :GitHub、Gitee
Pay attention to our , The first time to understand HMS Core Latest technical information ~
边栏推荐
- C # implements WinForm DataGridView control to support overlay data binding
- 使用GBase 8c数据库过程中报错:80000305,Host ips belong to different cluster ,怎么解决?
- Pytorch training process was interrupted
- [crawler] Charles unknown error
- uboot的启动流程:
- go语言学习笔记-初识Go语言
- Four departments: from now on to the end of October, carry out the "100 day action" on gas safety
- 7 themes and 9 technology masters! Dragon Dragon lecture hall hard core live broadcast preview in July, see you tomorrow
- 跨境电商是啥意思?主要是做什么的?业务模式有哪些?
- 数据库三大范式
猜你喜欢
COMSOL--建立几何模型---二维图形的建立

R3Live系列学习(四)R2Live源码阅读(2)
![[advertising system] parameter server distributed training](/img/8b/558c2fefbd16b580546003f3afeaf5.png)
[advertising system] parameter server distributed training
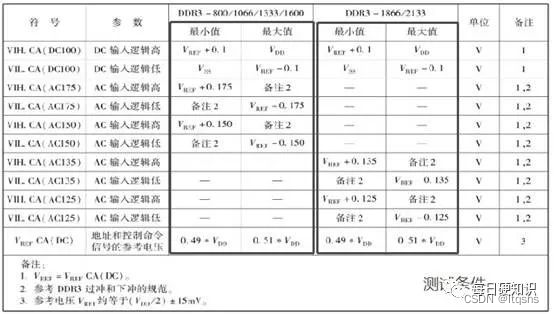
DDR4的特性与电气参数
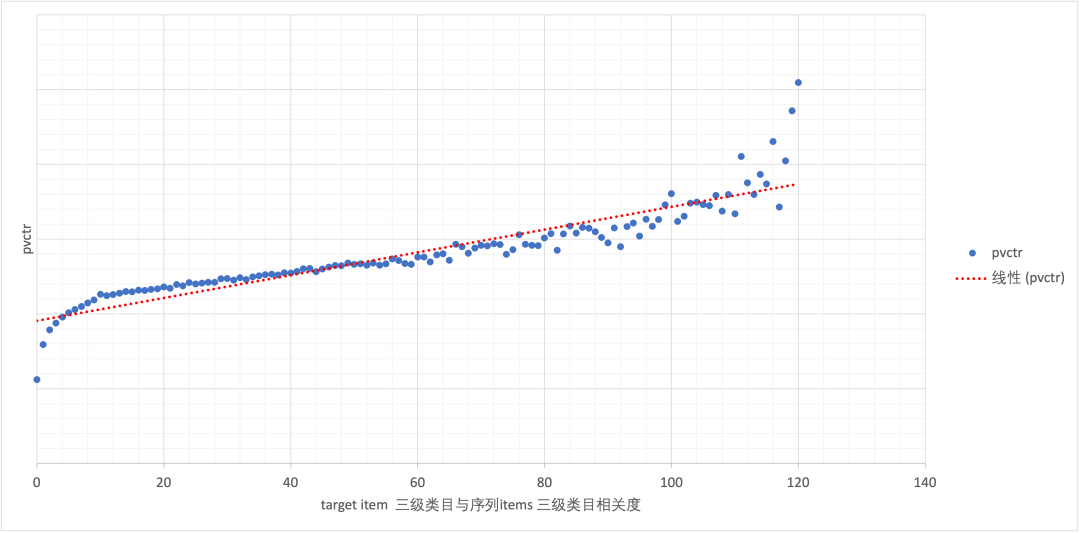
Evolution of multi-objective sorting model for classified tab commodity flow
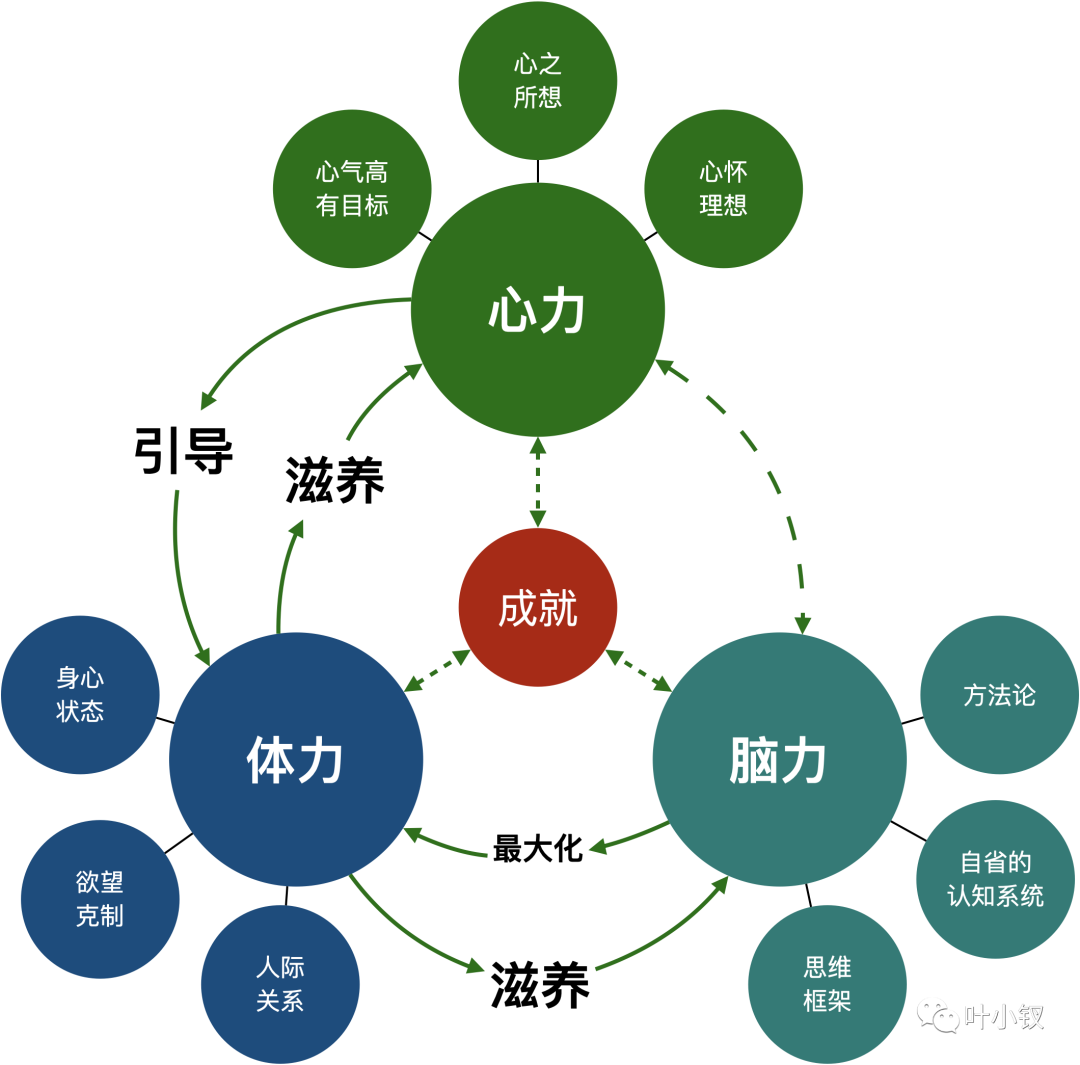
技术管理进阶——什么是管理者之体力、脑力、心力

The ninth Operation Committee meeting of dragon lizard community was successfully held

不要再说微服务可以解决一切问题了!
COMSOL -- three-dimensional graphics random drawing -- rotation
pytorch训练进程被中断了
随机推荐
Golang application topic - channel
COMSOL -- establishment of 3D graphics
技术分享 | 常见接口协议解析
SET XACT_ABORT ON
高校毕业求职难?“百日千万”网络招聘活动解决你的难题
Go language learning notes - first acquaintance with go language
阻止瀏覽器後退操作
7 themes and 9 technology masters! Dragon Dragon lecture hall hard core live broadcast preview in July, see you tomorrow
FFmpeg调用avformat_open_input时返回错误 -22(Invalid argument)
Basic part - basic project analysis
基于Lucene3.5.0怎样从TokenStream获得Token
Three paradigms of database
How did the situation that NFT trading market mainly uses eth standard for trading come into being?
Ffmpeg calls avformat_ open_ Error -22 returned during input (invalid argument)
How can edge computing be combined with the Internet of things?
Cdga | six principles that data governance has to adhere to
go语言学习笔记-初识Go语言
How can China Africa diamond accessory stones be inlaid to be safe and beautiful?
Intelligent metal detector based on openharmony
基础篇——基础项目解析